Ved Parkash
@v3d_bug
Curious to Learn
คุณอาจชื่นชอบ
Hey Everyone, do checkout how me and my brother @Zero2Infinity_ bag our 1st $$$$ bounty individually. v3d.medium.com/story-of-bount… #bugbounty #bugbountytips #bugbountytip #bughunter #hacker #cybersecurity #hackerone #bugcrowd

🔁 A good wordlist helps discover hidden content... but a custom one reveals what most other bug bounty hunters miss! Incorporating naming conventions, technology-specific and company-specific keywords (such as product names) is how you can craft your own custom wordlist. In…

I usually brute-force API paths with "Debug":true parameter and often it leads to reveal internal debug info to reverse proxies exposing API secrets and tokens.

We just dove into our shelf of archived bug bounty write-ups from the most notable hackers! 🤠 In this issue, we selected 5 compelling articles (that are still relevant today) to share with you, from which you can learn something new! 😎 🧵 👇

Javascript For bug hunters writeups, I hope you found it usefull medium.com/@mohammed0x04/… bitthebyte.medium.com/javascript-for… bitthebyte.medium.com/javascript-for… bitthebyte.medium.com/javascript-for…
A few months ago, @rootxharsh and I gave a talk, sharing the slides here in case they’re helpful to anyone.

As a homage to the work of @Blaklis_, our Security Researcher @softpoison_ debuts his first research post on reverse engineering a critical unauthenticated RCE in Magento (SessionReaper) CVE-2025-54236 at @SLCyberSec: slcyber.io/assetnote-secu…
Late last month, @SLCyberSec Security Researchers Adam Kues (@hashkitten) and Dylan Pindur presented on Finding Critical Vulnerabilities in Adobe Experience Manager at @BSidesCBR. Today, we’re releasing our research post and presentation slides: slcyber.io/assetnote-secu….
Found Algolia key in the DOM using my own Chrome extension. It searches the defined keywords in the DOM and JS files. github.com/dirtycoder0124… Exploit the key by following the steps given on hackwithsuryesh.medium.com/algolia-api-ke… #bugbounty #bugbountytips
Next.js Security Testing Guide for Bug Hunters and Pentesters deepstrike.io/blog/nextjs-se…
Built a JS secrets hunter for my testing workflow 🔍 Nothing new - just a more structured version of existing JS recon tools: ✅ Auto discovery ✅ 40+ patterns ✅ Multi-threaded ✅ Clean output github.com/Mah3Sec/JSHawk #bugbountytips #infosec #CyberSecurity #PenTest
🔥Quick tip: Don't miss any JS files changes! They contain a lot of juicy information about your target app.. * Real time JS monitoring, scraping and alerting with advanced MapperPlus engine with history of file.. (Even if the company accidentally exposed the JS file for a…

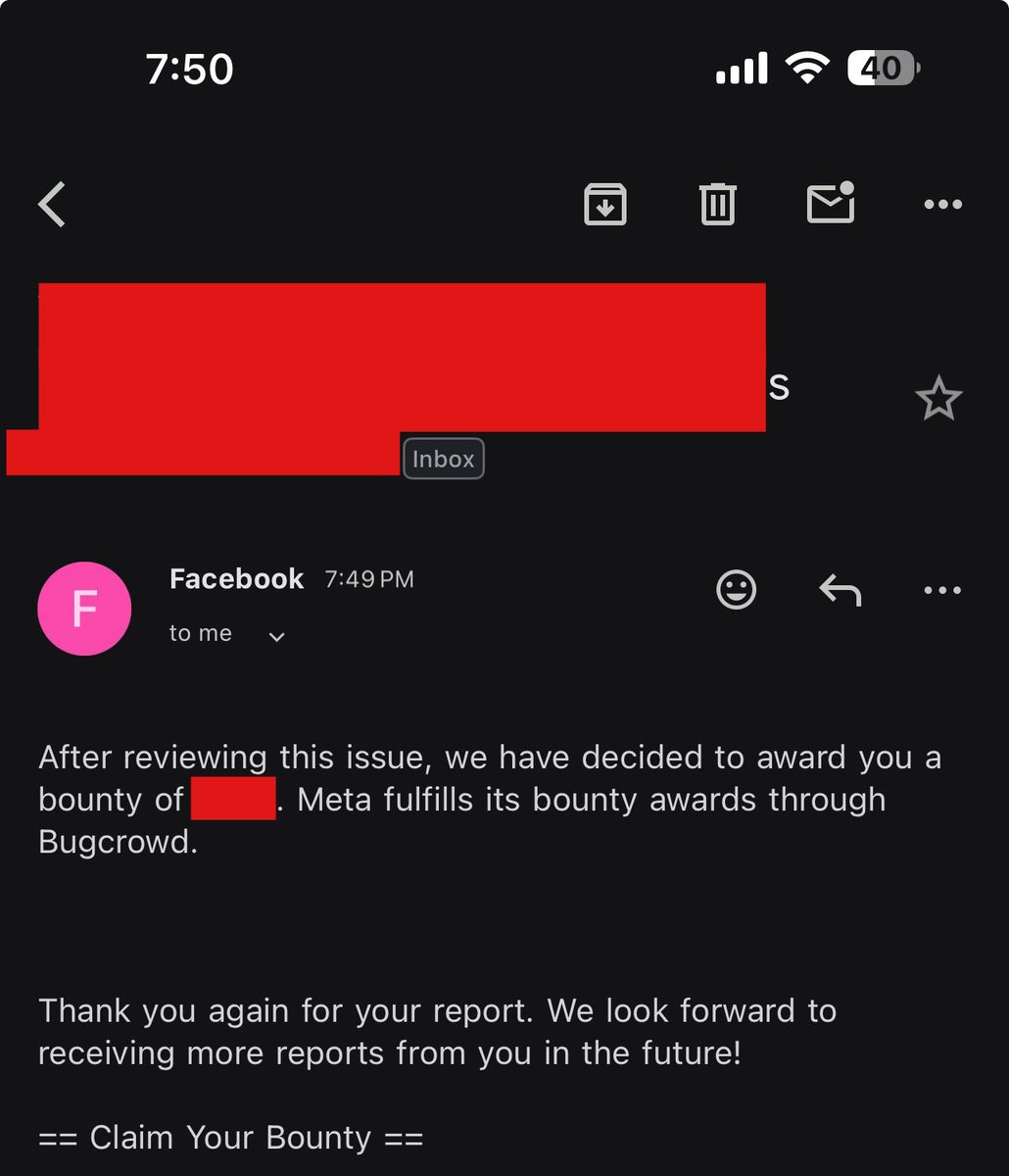
Jai Shri Ram 🙏🏻...Happy to secure @WhatsApp and received a bounty from @Meta ...WhatsApp is known for being a highly secure application, so finding and reporting a valid bug here means a lot. #bugbounty #bughunter #bughunting #CyberSecurity #hacker #meta #hackerone #bugcrowd
FINALLY! I overcame the procrastination wall and published my full breakdown on Dependency Confusion. This post covers my strategy for turning existing research into a 24/7 automated engine. Check out here: sl4x0.medium.com/turning-depend… #bugbountytips #supplychains
This is an interesting write-up on turning a limited path traversal into $40K. If you fuzz the target enough, there's always something interesting: medium.com/@HX007/a-journ…
Happy Friday! Enjoy our analysis of CVE-2025-36604, a pre-auth Command Inj in Dell's UnityVSA that we discovered and reported in March. labs.watchtowr.com/its-never-simp…
If you’re hunting for IDORs or dealing with messy, ID-heavy applications, you need Logger++ in your toolkit. Logger++ is a Burp Suite extension that helps you track, search, and filter requests. It’s particularly powerful when working with large volumes of API traffic and…

We just released a new article on how we hacked with @adnanthekhan the npm Supply Chain of 36 Million Weekly Installs 🔥 🔗Link: landh.tech/blog/20251003-…

Just getting started with bug bounty? Learn 4 vulnerability types in 400 seconds! 🤠 A thread! 🧵 👇

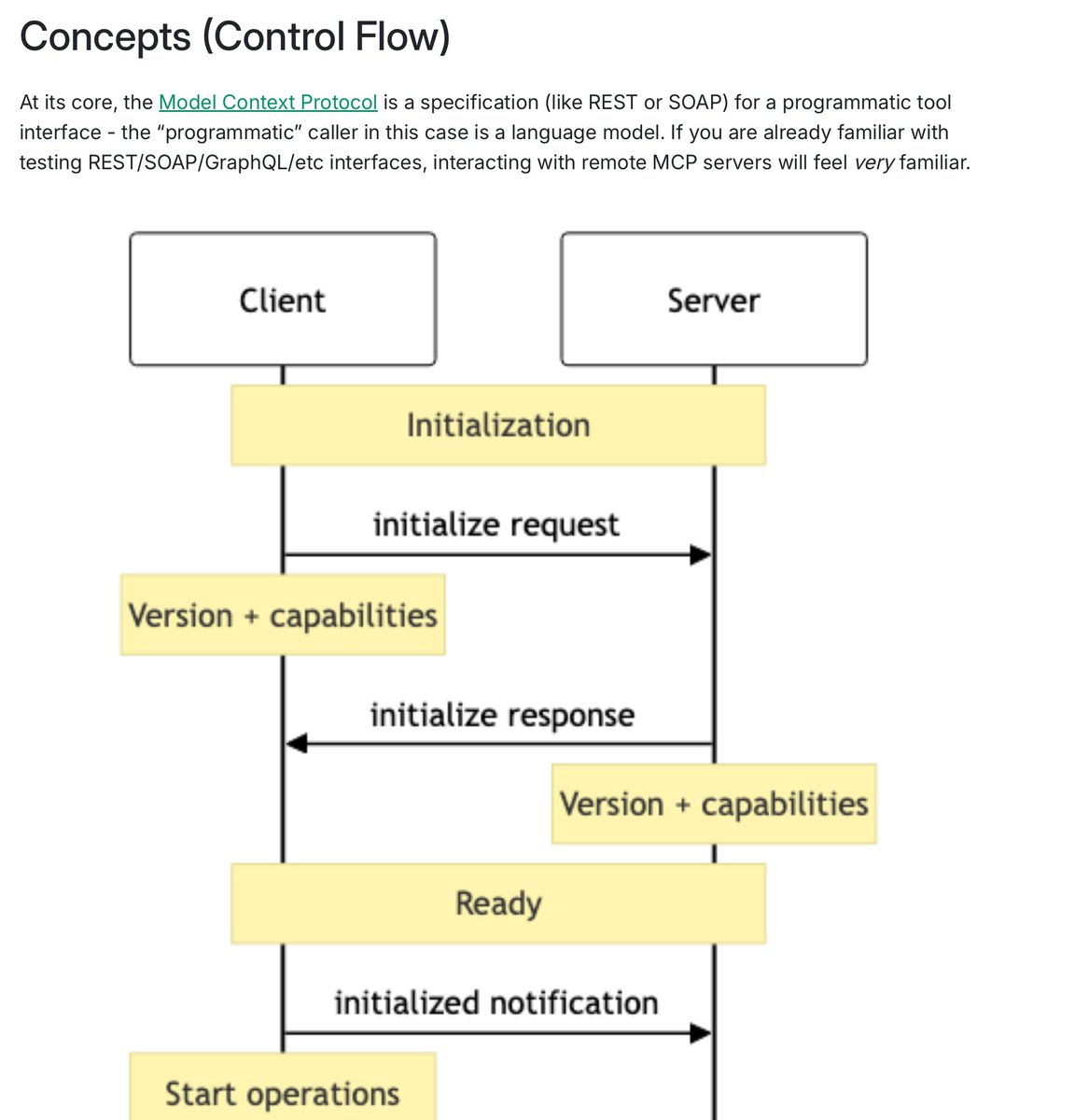
If you're interested in MCP my colleague Kurt has just put up a really good intro to MCP for security engineers that covers what they are and how they work as well as what vulnerabilities they have, plus tools to test them, check it out



United States เทรนด์
- 1. Cowboys 53.1K posts
- 2. #WWERaw 51.9K posts
- 3. Cardinals 24.1K posts
- 4. Logan Paul 7,670 posts
- 5. Koa Peat 5,218 posts
- 6. Jerry 40.5K posts
- 7. Bland 10.7K posts
- 8. Jacoby Brissett 3,105 posts
- 9. Kyler 5,988 posts
- 10. Arizona 41K posts
- 11. Cuomo 151K posts
- 12. Bethune 3,716 posts
- 13. Monday Night Football 16.7K posts
- 14. Steele 5,794 posts
- 15. Eberflus 1,737 posts
- 16. Pacers 9,700 posts
- 17. Javonte Williams 1,554 posts
- 18. CeeDee 6,460 posts
- 19. #RawOnNetflix 1,866 posts
- 20. Marvin Harrison Jr 5,437 posts
คุณอาจชื่นชอบ
-
 moSec
moSec
@moe1n1 -
 Basavaraj Banakar🇮🇳
Basavaraj Banakar🇮🇳
@basu_banakar -
 Nihad
Nihad
@nihad_rekany -
 Atharv Shejwal
Atharv Shejwal
@AtharvShejwal -
 Sunil Yedla
Sunil Yedla
@sunilyedla2 -
 Deepak Dhiman🇮🇳
Deepak Dhiman🇮🇳
@Virdoex_hunter -
 sushant dhopat
sushant dhopat
@sushantdhopat -
 Dani | Vulnerable 💔❤️🩹
Dani | Vulnerable 💔❤️🩹
@my_r3in3 -
 ɴɪᴛɪɴ ɢᴀᴠʜᴀɴᴇ
ɴɪᴛɪɴ ɢᴀᴠʜᴀɴᴇ
@NitinGavhane_ -
 Sachin Pandey
Sachin Pandey
@sachin_pandey98 -
 Syed Mushfik Hasan Tahsin
Syed Mushfik Hasan Tahsin
@SMHTahsin33 -
 Debangshu 🇮🇳🥷
Debangshu 🇮🇳🥷
@ThisIsDK999 -
 Burhan Chhotaudepur
Burhan Chhotaudepur
@burhan__xd -
 Mahendra Purbia
Mahendra Purbia
@Mah3Sec -
 Aman Mahendra
Aman Mahendra
@amanmahendra_
Something went wrong.
Something went wrong.