𝖒𝖆𝖗𝖐𝖚𝖘
@wirehack7
Another #ITSec guy. Incident Response and RE | GREM | Plague doctor to malware and scums, curing the pest since 2013 w/ #MalwareMustDie
You might like
Hey #malware #moronz, here is a message for you: #MalwareMustDie /cc: @MalwareMustDie

Finding vulnerabilities in DJI drones: reverse engineering, firmware decryption, and dynamic analysis (fuzzing). 👨💻❯❯🛸🫨🪲 More details on: LinkedIn: linkedin.com/posts/dlaskov_… Substack: it4sec.substack.com/p/finding-vuln…

Just wondering how many of us are actually rebooting (turning off and on again) our mobile phone devices everyday? #MalwareMustDie #Poll
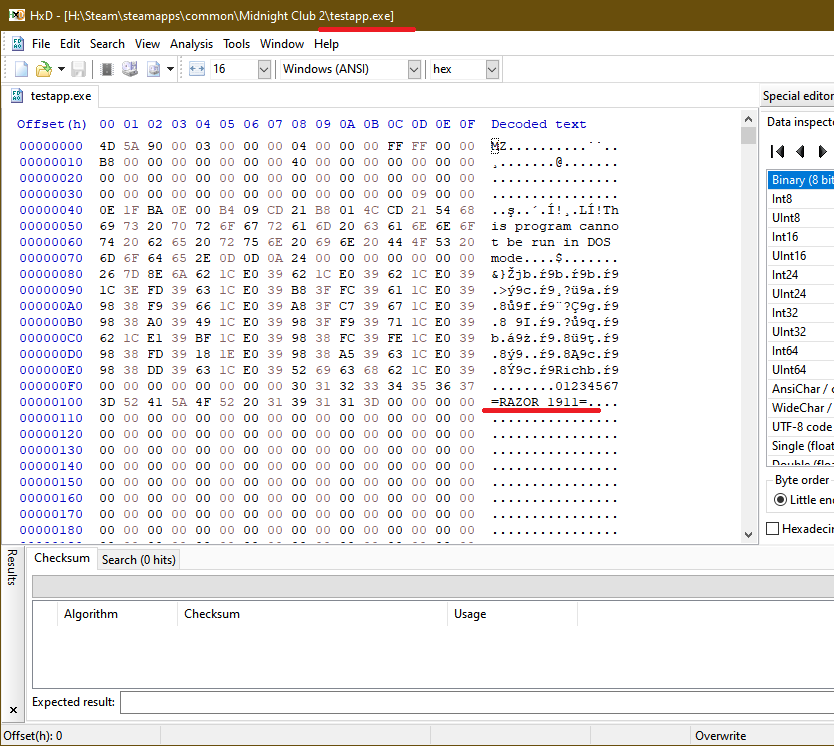
This strange tweet got >25k retweets. The author sounds confident, and he uses lots of hex and jargon. There are red flags though... like what's up with the DEI stuff, and who says "stack trace dump"? Let's take a closer look... 🧵1/n

Crowdstrike Analysis: It was a NULL pointer from the memory unsafe C++ language. Since I am a professional C++ programmer, let me decode this stack trace dump for you.

Nice learning material on real ELF malware. Thanks a lot! #infosec #reversing
#Blog: Back in 2015, where #Linux #Ransomware was started to came up to the surface, I posted an analysis that I forgot to post it in #MMD blog in English until just now.. So, I am sorry, better late than never. Here it is: blog.malwaremustdie.org/2024/06/mmd-06… #MalwareMustDie!
#Blog: I re-posted my older #APT #PoisonIvy analysis in #MMD blog before it becomes /dev/null :) blog.malwaremustdie.org/2024/06/mmd-06… #MalwareMustDie!
As a tweet poster the likes to the tweet are not anonymous, the poster sees who is liking the tweet. That's as expected @XEng?
it's 2024 and websites like wordpress.org @WordPress still don't support ipv6. AAAA record missing. Is it rocket science to also offer ipv6? Or is ipv6 too new? #wordpress #IPv6
Dieses Jahr waren wir wie immer beim #CCC Kongress, #37c3, dabei 😎👾 Es gab interessante Einblicke und Spaß 👌 Die Telnet Challenge hat #iSecNG gerockt, denn wir sprechen Klartext. Bis zum nächsten Mal und einen guten Rutsch 🎉 Das iSecNG Team


Vote and maybe reply here for non listed sandboxes. Would be also to share why. #infosec #sandbox #malware pls help to RT if you want. Sharing the love, thanks! ❤️
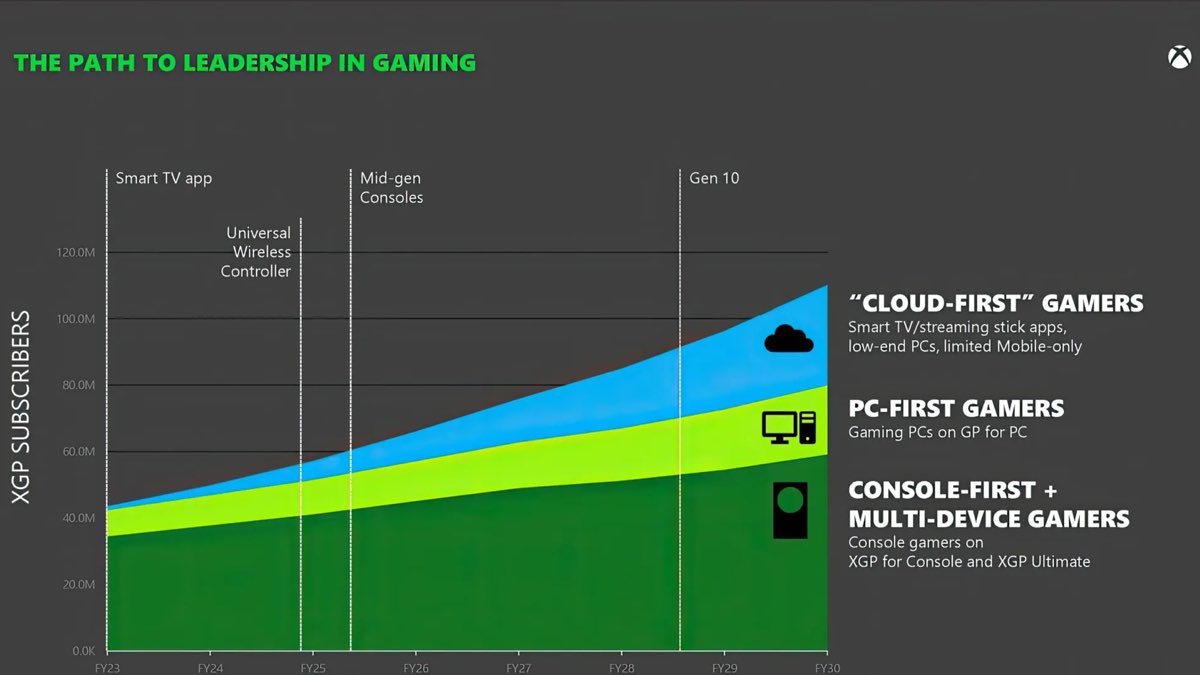
#Xbox isn’t abandoning consoles anytime soon. In a graph @Microsoft Gaming’s CEO, Phil Spencer, used in the FTC hearing relating to the acquisition of Activision Blizzard King, they showed the potential growth of the Microsoft Gaming brand from 2023 to 2030. This chart showed a…
Thank you for all of friends for the amazing support along these 11years+. If you are following our #malwaremustdie/#MMD's twitter/x account @malwaremustdie up to now & got disconnected please follow this official account to keep in touch. -- MMD
Want to download faster juicy leaks from #TOR network? Try out this: github.com/sn0b4ll/aria2-… Speed it up, waste less time. made by @sn0b4ll #infosec
Rockstar is selling cracked game copies on Steam
"HHHash: HTTP Headers Hashing (HHHash) is a technique used to create a fingerprint of an HTTP server based on the headers it returns." #infosec #pentest #redteam github.com/adulau/HHHash

The Forum of Incident Response and Security Teams (#FIRST) is proud to announce the official release of #CVSS v4.0 #ThePublicPreview. The latest information on CVSS v4.0 can be found at first.org/cvss/v4-0/ #FIRSTCON23

United States Trends
- 1. Bills 123K posts
- 2. Josh Allen 11.7K posts
- 3. Dolphins 26.3K posts
- 4. Giants 51.2K posts
- 5. Henderson 12.2K posts
- 6. Bears 47.1K posts
- 7. Browns 29.4K posts
- 8. Dart 19.8K posts
- 9. Drake Maye 11.2K posts
- 10. Ravens 29.7K posts
- 11. Bryce 13.3K posts
- 12. Patriots 83.5K posts
- 13. Caleb 34.9K posts
- 14. Saints 30.2K posts
- 15. Vikings 25.2K posts
- 16. JJ McCarthy 3,237 posts
- 17. Daboll 3,142 posts
- 18. Pats 10.7K posts
- 19. Jonathan Taylor 22.7K posts
- 20. Jefferson 7,793 posts
You might like
-
 Seongsu Park
Seongsu Park
@unpacker -
 Danny Quist
Danny Quist
@OpenMalware -
 Evilcry_
Evilcry_
@Blackmond_ -
 Santiago Pontiroli
Santiago Pontiroli
@spontiroli -
 Michael Ligh (MHL)
Michael Ligh (MHL)
@iMHLv2 -
 JaromirHorejsi
JaromirHorejsi
@JaromirHorejsi -
 marc ochsenmeier
marc ochsenmeier
@ochsenmeier -
 Giuseppe `N3mes1s`
Giuseppe `N3mes1s`
@gN3mes1s -
 Fafner [_KeyZee_]
Fafner [_KeyZee_]
@F_kZ_ -
 Antelox
Antelox
@Antelox -
 Malekal's site
Malekal's site
@malekal_morte -
 🅰🅳🅼
🅰🅳🅼
@securityfreax -
 Artem I. Baranov 🐦
Artem I. Baranov 🐦
@artem_i_baranov -
 TomU | I'm still here... til the end 🕊️🇨🇭
TomU | I'm still here... til the end 🕊️🇨🇭
@c_APT_ure -
 Andre M. DiMino
Andre M. DiMino
@sempersecurus
Something went wrong.
Something went wrong.