wout
@woetroe2
oscp crto crtl
คุณอาจชื่นชอบ
Now in private beta: Aardvark, an agent that finds and fixes security bugs using GPT-5. openai.com/index/introduc…

Credential Guard was supposed to end credential dumping. It didn't. @bytewreck just dropped a new blog post detailing techniques for extracting credentials on fully patched Windows 11 & Server 2025 with modern protections enabled. Read for more ⤵️ ghst.ly/4qtl2rm
Chinese authorities allege a 27-month NSA operation against the China's National Time Service Center. Initial credential theft apparently via a smartphone-messaging exploit. They relese technical details, including information about 80+ remote logins between April 11 and August…




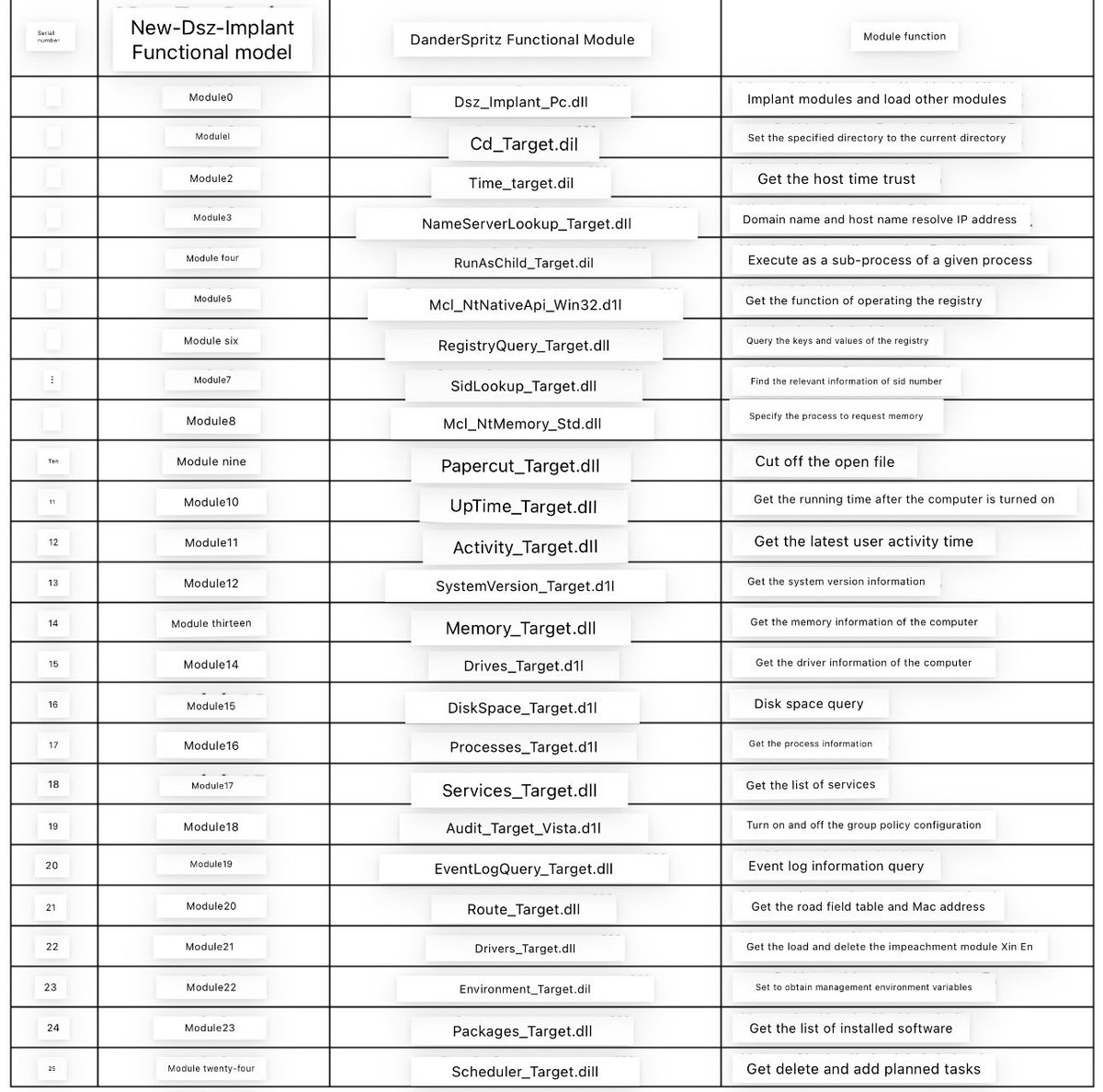
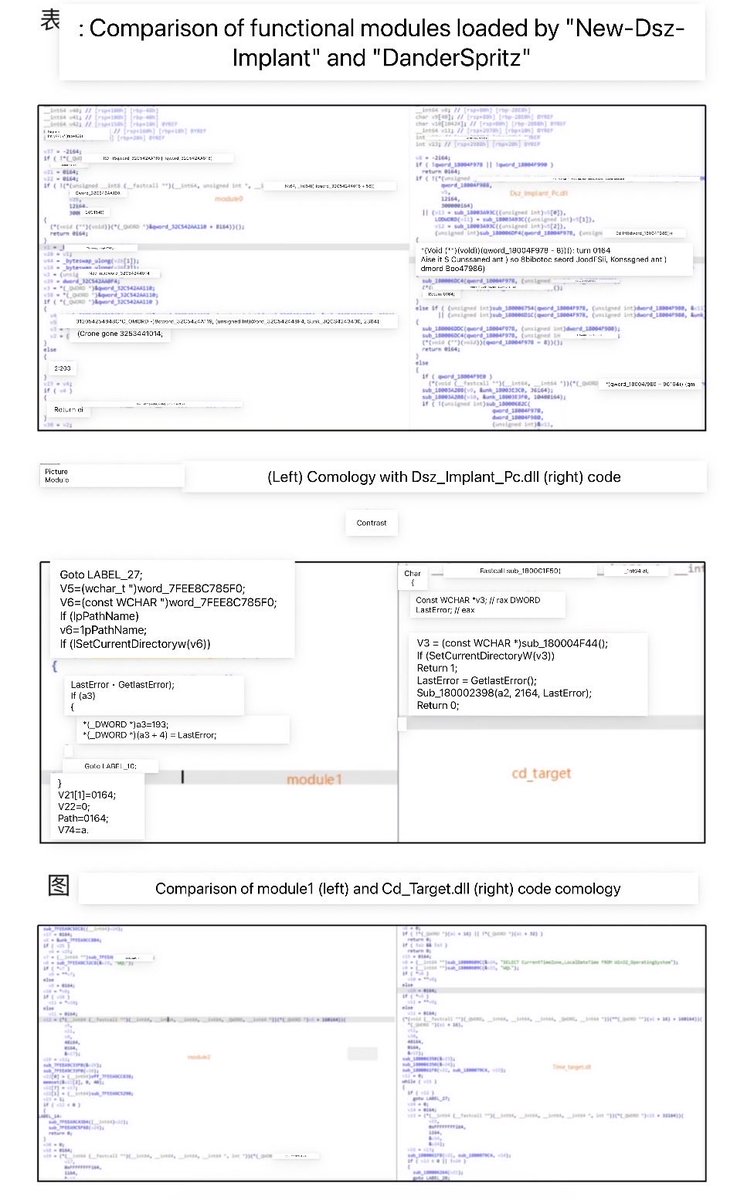
Operation Triangulation + #DanderSpritz Come back … #iphone -> Windows mp.weixin.qq.com/s/XPjT0BVOJPJx…
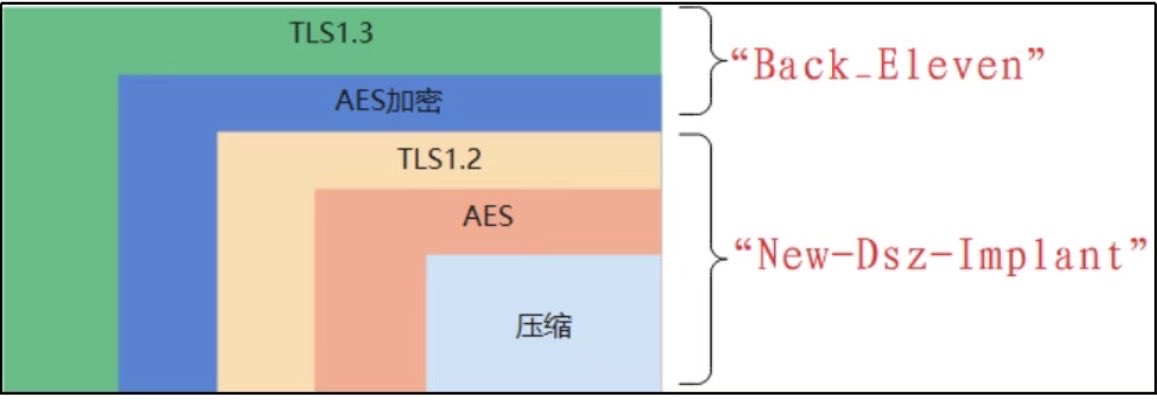
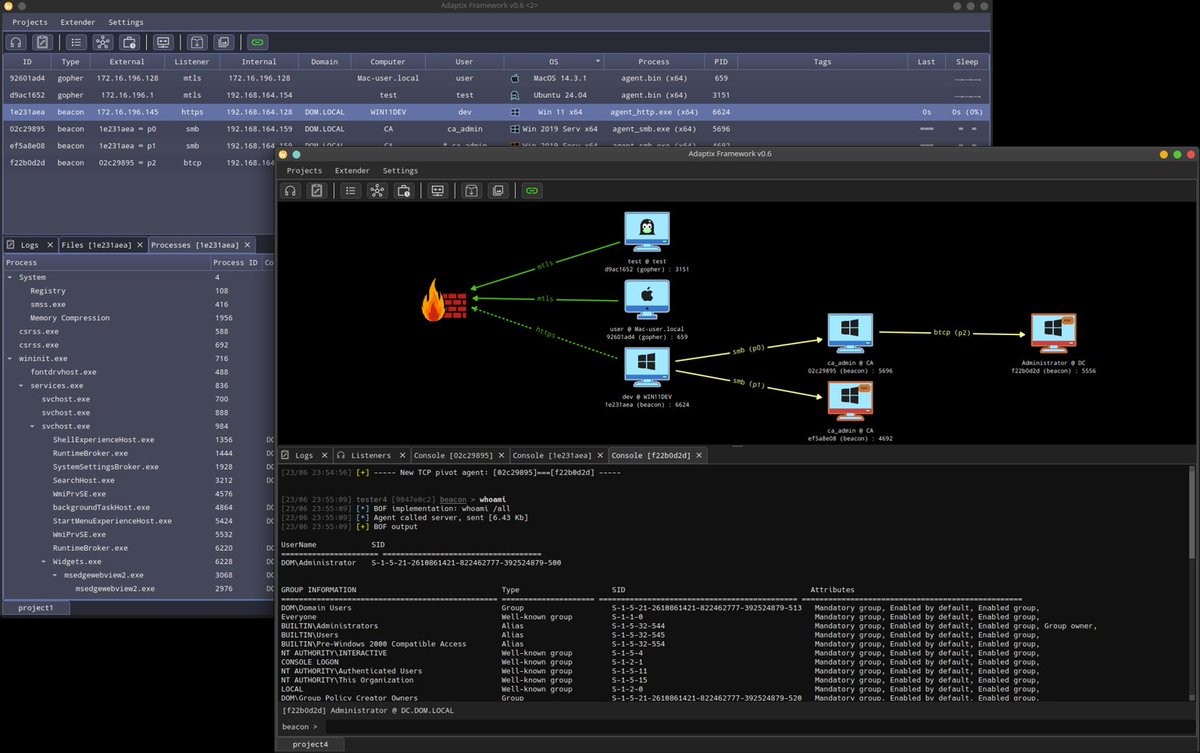
🔴 𝗡𝗲𝘄 𝗥𝗲𝘀𝗲𝗮𝗿𝗰𝗵: 𝗛𝘂𝗻𝘁𝗶𝗻𝗴 𝗔𝗱𝗮𝗽𝘁𝗶𝘅𝗖𝟮 – 𝗧𝗿𝗮𝗰𝗶𝗻𝗴 𝗼𝘃𝗲𝗿 𝟭𝟬𝟬 𝗟𝗶𝘃𝗲 𝗖𝟮 𝗦𝗲𝗿𝘃𝗲𝗿𝘀 𝗶𝗻 𝘁𝗵𝗲 𝗪𝗶𝗹𝗱 Our team investigated AdaptixC2, an open-source command and control framework that’s being used in real attacks. Using HuntSQL™,…



I've been researching the Microsoft cloud for almost 7 years now. A few months ago that research resulted in the most impactful vulnerability I will probably ever find: a token validation flaw allowing me to get Global Admin in any Entra ID tenant. Blog: dirkjanm.io/obtaining-glob…
Analysis of Windows CLFS #EoP vuln (#CVE-2025-29824) in-the-wild exploitation sample and root cause Report: ti.qianxin.com/blog/articles/… ITW sample: virustotal.com/gui/file/808cb…



Exciting times. I'm publishing Dittobytes today after presenting it at @OrangeCon_nl ! Dittobytes is a true metamorphic cross-compiler aimed at evasion. Use Dittobytes to compile your malware. Each compilation produces unique, functional shellcode. github.com/tijme/dittobyt…
Announcing our whitepaper on the future of endpoint security. preludesecurity.com/runtime-memory…
blog.malicious.group/the-quiet-side… This is a living document at the moment, but here it is for now. 😅As mentioned in the paper, if you are a researcher and have questions after reading, just reach out to me and I will answer everything I can.
Wintel is coming for your SMEP bypasses! No more flipping the U/S bit in a PTE to mark a user-mode page as supervisor-mode on Intel Arrow Lake CPUs :) (note: this is meant for protection against speculative attacks, with the side effect of becoming SMEP 2.0)


We’re cooked, guys. A new vulnerability has been discovered in sudo and you don’t even need to be in the sudo group to get root. I just tried it 👇
Published the third part of my blog series about Hydroph0bia (CVE-2025-4275) vulnerability, this one is about the fix as Insyde applied it, and my thoughts on improvements for it. coderush.me/hydroph0bia-pa…
Releasing this fun tool Golem based on @0xdea, LLVM, LLM and @semgrep Golem automates C/C++ vulnerability discovery by combining Semgrep rule scans, LLVM call-graph & CFG slicing, and AI-driven context analysis. Tool: github.com/20urc3/golem Article: bushido-sec.com/index.php/2025…
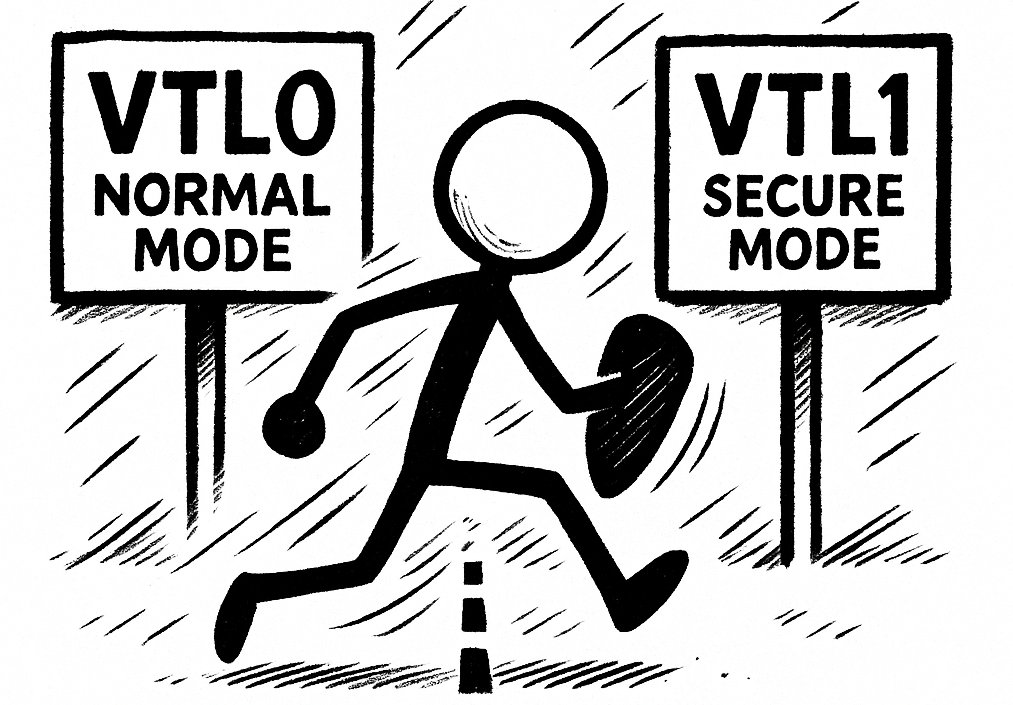
Here's our new blog on hiding your implant in VTL1, where even an EDR's kernel sensor can't see it.🧑🦯 Post includes full operational details. Plus our OST offering has been updated with a Cobalt Strike sleep mask exploiting secure enclaves. Full read ➡️ outflank.nl/blog/2025/06/1…
Dive deep into malware detection with the latest article by John Uhlmann: "Call Stacks: No More Free Passes for Malware." Discover how call stacks provide vital insights into malware behavior. Read more: go.es.io/4kDWjgr
How #PreventionEngineering is used to stop #ADCS 𝐂𝐞𝐫𝐭𝐢𝐟𝐢𝐞𝐝 𝐏𝐫𝐞-𝐎𝐰𝐧𝐞𝐝 attacks? @SagieDulce demos how attacks via #Certify and other tools are mitigated with the #RPCFirewall, #LDAPFirewall and #NetworkSegmentation. Read more here: hubs.li/Q02PlSxC0
New post: dawnslab.jd.com/%E4%B9%8B%E6%A… writeup for CVE-2025-22056, which we also found but collide with other researchers. A nice bug that can be stably exploited to get kernel privilege on Ubuntu.
United States เทรนด์
- 1. Good Friday 50.2K posts
- 2. #FanCashDropPromotion N/A
- 3. LINGORM DIOR AT MACAU 399K posts
- 4. #FridayVibes 3,785 posts
- 5. #TheWorldWithVenezuela 2,364 posts
- 6. #ElMundoConVenezuela 2,399 posts
- 7. Happy Friyay N/A
- 8. #GenshinSpecialProgram 15.5K posts
- 9. Josh Allen 43.9K posts
- 10. Haier EST SUPHA 129K posts
- 11. RED Friday 2,292 posts
- 12. Ja Rule N/A
- 13. Sedition 335K posts
- 14. Parisian 1,669 posts
- 15. Texans 62.6K posts
- 16. Niger 61.4K posts
- 17. namjoon 69.1K posts
- 18. Beane 3,212 posts
- 19. Cole Palmer 16.2K posts
- 20. Traitor 120K posts
คุณอาจชื่นชอบ
-
 rehackxyz
rehackxyz
@rehackxyz -
 Soumyani1
Soumyani1
@reveng007 -
 KAI
KAI
@kaisai121 -
 Juuzou Suzuya
Juuzou Suzuya
@0x255x -
 BitFre4k
BitFre4k
@BiteFre4k -
 Troy
Troy
@Troy_shi -
 Akhmad Yudha
Akhmad Yudha
@Akhmad_Yudha -
 bruh
bruh
@cppbruh -
 Sebastian Lujan
Sebastian Lujan
@delegate_call -
 knightmare2600
knightmare2600
@knightmare2600 -
 Evangelos
Evangelos
@lex0tanil -
 Рахул
Рахул
@pl4y_m4k3r -
 Adrian Luca (infosec.exchange/@adrian_luca)
Adrian Luca (infosec.exchange/@adrian_luca)
@adrian__luca -
 rv
rv
@rvikrant09 -
 Christian {tty503}
Christian {tty503}
@tty_503
Something went wrong.
Something went wrong.