#networksegmentation نتائج البحث
Use isolated network segments for darknet activities. #NetworkSegmentation #DarknetOps #SecureArchitecture
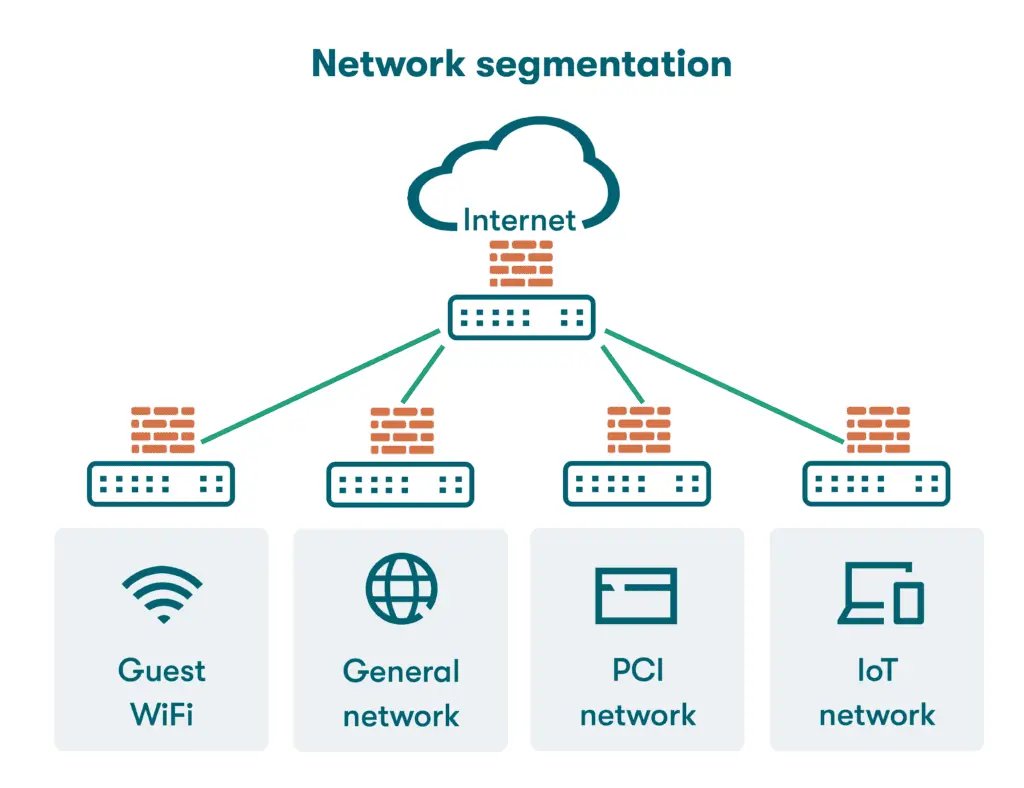
Segmentation limits damage—but only if traffic rules are enforced and monitored. Unchecked connections turn ‘protected zones’ into false security. #NetworkSegmentation #CyberResilience #DefenseInDepth #ArcherEnergySolutions

Why network segmentation matters for bolstering cybersecurity: - 𝗟𝗶𝗺𝗶𝘁𝗶𝗻𝗴 𝗕𝗿𝗲𝗮𝗰𝗵 𝗜𝗺𝗽𝗮𝗰𝘁 🌐 - 𝗘𝗻𝗵𝗮𝗻𝗰𝗲𝗱 𝗦𝗲𝗰𝘂𝗿𝗶𝘁𝘆 𝗖𝗼𝗻𝘁𝗿𝗼𝗹𝘀 🛡️ - 𝗜𝗺𝗽𝗿𝗼𝘃𝗲𝗱 𝗜𝗻𝗰𝗶𝗱𝗲𝗻𝘁 𝗥𝗲𝘀𝗽𝗼𝗻𝘀𝗲 📜 #Cybersecurity #NetworkSegmentation #Defense

Protecting your OT network is crucial! Downtime, financial loss, and even human costs are on the line. Read the full blog: hubs.ly/Q02LbJKv0 #Cybersecurity #OTSecurity #NetworkSegmentation #RiskManagement #ZeroTrust #CriticalInfrastructure

Navigating the Challenges of #NetworkSegmentation and Microsegmentation Without Disrupting Operations - buff.ly/3XOXbDS #IT #technology #cybersecurity #security #ITsecurity #infosec

#SonicWall Do you want to reduce attack surfaces and better secure your network? SonicWall’s 5-point #networksegmentation checklist can help. Enhance your defense strategy, control access to critical assets, and minimize damage if a breach occurs. Get it…

#NetworkSegmentation is evolving with the expanding XIoT landscape. In this blog, read how to speed up segmentation without slowing down operations, and why a proactive strategy makes all the difference. hubs.li/Q03xBkmw0

🔒Enhance your network security with these 4 network segmentation types🌐 Physical, Logical, Wireless, and Device segmentation. Each provides layers of protection, safeguarding your digital assets. #CyberSecurity #NetworkSegmentation #ZeroTrust #InstaSafe

Research shows that large numbers of Operational and Clinical #IoT assets ship with known vulnerabilities, and in many cases are not (or cannot be) routinely patched. Find out how #NetworkSegmentation can help improve your Cyber Posture. #IoMT hubs.ly/Q01QtFpP0

Being proactive is key to a successful #cybersecurity strategy. Leverage SonicWall’s 5-point #networksegmentation checklist to reduce attack surfaces, enhance defenses, and secure your network. Learn more ➡️ bit.ly/3IeqtG9

⚡ Ask Archer: True resilience isn’t just isolation. Layered defenses, strong access controls, and continuous monitoring work together to protect critical systems from evolving threats. 📩 [email protected] #AskArcher #NetworkSegmentation #CriticalInfrastructure


Don’t let your network be vulnerable to a single attack. By segmenting your network you can keep your sensitive data secure and minimize risk. Scroll through to see our top network segmentation tips. #NetworkSegmentation #CyberSecurityTips




Join Catherine and the crew at @ExertisBrdcast as they discuss how to secure your network and prevent cyberattacks in the latest episode of Techsplanation 2.0. Watch the full episode: bit.ly/3DOVTk7 #cyberattack #kvm #networksegmentation #airgapping #matroxvideo #ipkvm
A network that is secure by design, with effective access control, segmentation and contextual awareness helps you to identify risks, prevent threats and limit the blast radius of a successful attack. Find out more - hubs.ly/Q01QtQzv0 #NetworkSegmentation #NetworkSecurity

Maximize gateway security with network segmentation to protect sensitive data, deploy multiple distributed gateways to avoid single points of failure, and enhance performance across hybrid and remote environments. #NetworkSegmentation #HybridWork ift.tt/kqWGuQh
𝗔𝗜 𝗶𝘀 𝘁𝗿𝗮𝗻𝘀𝗳𝗼𝗿𝗺𝗶𝗻𝗴 𝗯𝘂𝘀𝗶𝗻𝗲𝘀𝘀𝗲𝘀. I𝘀 𝗶𝘁 𝗹𝗲𝗮𝘃𝗶𝗻𝗴 𝘆𝗼𝘂 𝗲𝘅𝗽𝗼𝘀𝗲𝗱 𝘁𝗼 𝗰𝘆𝗯𝗲𝗿 𝘁𝗵𝗿𝗲𝗮𝘁𝘀? 🤔cttsonline.com/2025/02/26/why… #CyberSecurity #AI #NetworkSegmentation #ITSecurity #TechTips #CTTSonline #GeorgetownTX #RoundRockTX #AustinTX

As IBRs become more widespread, their digital interfaces also expand the attack surface. Are your inverter management systems properly segmented from business networks? Isolation is the first line of defense. ⚠️🛡️ #Cybersecurity #IBR #NetworkSegmentation #ArcherEnergySolutions

Find guidelines to evaluate zero trust network segmentation solutions. bit.ly/42Tph3r #networksegmentation #zerotrust #informationsecurity

Do you want to reduce attack surfaces and better secure your network? SonicWall’s 5-point #networksegmentation checklist can help. Enhance your defense strategy, control access to critical assets, and minimize damage if a breach occurs. Get it here: bit.ly/3IeqtG9

12/14 Entreprises, segmentez vos réseaux ! Un intrus ne doit jamais passer du mail à la diffusion. Cloisonnez vos systèmes critiques. Sans murs, une brèche devient un effondrement. #TV5Monde #Cybersecurité #NetworkSegmentation

Maximize gateway security with network segmentation to protect sensitive data, deploy multiple distributed gateways to avoid single points of failure, and enhance performance across hybrid and remote environments. #NetworkSegmentation #HybridWork ift.tt/kqWGuQh
Segmentation limits damage—but only if traffic rules are enforced and monitored. Unchecked connections turn ‘protected zones’ into false security. #NetworkSegmentation #CyberResilience #DefenseInDepth #ArcherEnergySolutions

⚡ Ask Archer: True resilience isn’t just isolation. Layered defenses, strong access controls, and continuous monitoring work together to protect critical systems from evolving threats. 📩 [email protected] #AskArcher #NetworkSegmentation #CriticalInfrastructure


What is zero trust network segmentation? It reduces the attack surface by isolating potential threats. Every access request is verified, ensuring better control. #ZeroTrust #NetworkSegmentation
Data diodes enforce one-way traffic. Great for integrity, but don’t expect them to solve every security challenge. #DataDiodes #NetworkSegmentation #OTSecurity #ArcherEnergySolutions

IoT devices often lack proper security. Segment networks to reduce risk #IoTSecurity #NetworkSegmentation #CyberRisk #TechTrends
Cyber Fact 164 #Cybersecurity #Facts #NetworkSegmentation #Attack #CriticalInfrastructure #ArcherEnergySolutions

Flat networks are a hacker’s playground. Segmentation creates chokepoints that slow intruders and buy defenders time. #NetworkSegmentation #CyberDefense #OTSecurity #ArcherEnergySolutions

One weak link can put your entire hospital network at risk. Network segmentation protects sensitive systems, boosts HIPAA compliance, and keeps operations running smoothly. #NetworkSegmentation #HealthcareSecurity #DataProtection #ITForScrubs #Healthcare itforscrubs.com/blog/segmentin…
itforscrubs.com
Network Segmentation in Hospitals: Boosting Cybersecurity
Discover how network segmentation helps hospitals secure IoMT devices, meet compliance standards, and isolate threats across departments before they escalate.
Cyber Definition: Network Segmentation #Cybersecurity #Definition #NetworkSegmentation #Breach #ArcherEnergySolutions

Cyber Fact 163 #Cybersecurity #Facts #NetworkSegmentation #CriticalInfrastructure #Breach #ArcherEnergySolutions

The Purdue Model has guided network segmentation for decades—but is it enough for today’s IT/OT environments? Stacy Bressler breaks it down in our new On Target with Archer episode. Watch here: youtu.be/zwfS1AbVDKI #PurdueModel #NetworkSegmentation #CriticalInfrastructure #OT
youtube.com
YouTube
The Purdue Model Explained: Does It Still Protect Critical Infrastr...
The Purdue Model isn’t just theory—it’s a map for survival. Without proper segmentation, a breach at the corporate level can cascade down to control systems. #PurdueModel #NetworkSegmentation #CyberResilience #ArcherEnergySolutions

Today's pentest crystal ball. Implement network segmentation across all systems. Visit ayb.ad. #NetworkSegmentation #CyberDefence #SecureNetworks #CyberBestPractices

Segmentation limits damage—but only if traffic rules are enforced and monitored. Unchecked connections turn ‘protected zones’ into false security. #NetworkSegmentation #CyberResilience #DefenseInDepth #ArcherEnergySolutions

Use isolated network segments for darknet activities. #NetworkSegmentation #DarknetOps #SecureArchitecture

Cyber Fact 164 #Cybersecurity #Facts #NetworkSegmentation #Attack #CriticalInfrastructure #ArcherEnergySolutions

Cyber Fact 163 #Cybersecurity #Facts #NetworkSegmentation #CriticalInfrastructure #Breach #ArcherEnergySolutions

Keep checking vulnerabilities of cyber infra to prevent cyberattacks! #cybersecurity #networksegmentation

Cyber Definition: Network Segmentation #Cybersecurity #Definition #NetworkSegmentation #Breach #ArcherEnergySolutions

Via @ElisityInc: At RSAC 2025, @Claroty's Skip Sorrels explored the revolutionary transformation of #NetworkSegmentation in #healthcare environments, highlighting how modern solutions are finally solving decade-old challenges. 🎥 Watch here: hubs.li/Q03rpHks0

Navigating the Challenges of #NetworkSegmentation and Microsegmentation Without Disrupting Operations - buff.ly/3XOXbDS #IT #technology #cybersecurity #security #ITsecurity #infosec

⏰ LAST CALL to join TOMORROW's webinar with #cybersecurity leaders from @Claroty, @Cisco, and @ChildrensLA, who'll share the secrets to overcoming #NetworkSegmentation challenges. 📌 Sign up now: hubs.li/Q02Fvk1R0

In this on-demand @Claroty webinar, esteemed speakers from @CiscoSecure and @ChildrensLA discuss common pitfalls encountered in hospitals' #NetworkSegmentation efforts and explore strategies for overcoming these obstacles. ⏯️ Watch here: hubs.li/Q02_yz6h0

Coming up Sep. 26: Join us for a live webinar and Q&A on #NetworkSegmentation in clinical environments. See how Medigate by @Claroty can reduce resources and boost segmentation initiatives across your full #cybersecurity journey. Register here: bit.ly/47ObWvQ

🔏 Journey into hospital #cybersecurity with this series on the #NetworkSegmentation of medical devices, feat. interviews with hospital systems expoert, who'll offer insights into their experiences, challenges, and triumphs. Sign up here: hubs.li/Q02BfxJ_0
#NetworkSegmentation is evolving with the expanding XIoT landscape. In this blog, read how to speed up segmentation without slowing down operations, and why a proactive strategy makes all the difference. hubs.li/Q03xBkmw0

𝗔𝗜 𝗶𝘀 𝘁𝗿𝗮𝗻𝘀𝗳𝗼𝗿𝗺𝗶𝗻𝗴 𝗯𝘂𝘀𝗶𝗻𝗲𝘀𝘀𝗲𝘀. I𝘀 𝗶𝘁 𝗹𝗲𝗮𝘃𝗶𝗻𝗴 𝘆𝗼𝘂 𝗲𝘅𝗽𝗼𝘀𝗲𝗱 𝘁𝗼 𝗰𝘆𝗯𝗲𝗿 𝘁𝗵𝗿𝗲𝗮𝘁𝘀? 🤔cttsonline.com/2025/02/26/why… #CyberSecurity #AI #NetworkSegmentation #ITSecurity #TechTips #CTTSonline #GeorgetownTX #RoundRockTX #AustinTX

Just 24 hours left until our #CIP #cybersecurity webinar, “Strategic Segmentation”. Unlock the potential of #NetworkSegmentation to boost your system's security. Don’t miss out! Haven’t registered yet? ⏰ There’s still time. Sign up now! hubs.la/Q02DwBQq0

In this on-demand webinar, @Claroty, @CiscoSecure, and @ChildrensLA reveal the common pitfalls encountered by hospitals in #NetworkSegmentation efforts and explore strategies for overcoming these obstacles. ⏯️ Watch here: hubs.li/Q02_cWkS0

🗓️ Join us on July 9 with @Cisco and @ChildrensLA as we uncover the reasons behind common pitfalls encountered by hospitals in #NetworkSegmentation efforts and explore strategies for overcoming these obstacles. Register here: hubs.li/Q02C0T6h0 @CiscoSecure @CiscoPartners

🗣️ Join speakers from @Claroty, @Cisco, and @ChildrensLA next Tuesday, as they divulge their secrets to overcoming #NetworkSegmentation challenges and streamlining processes. Sign up now: bit.ly/4bxWRz3

Being proactive is key to a successful #cybersecurity strategy. Leverage SonicWall’s 5-point #networksegmentation checklist to reduce attack surfaces, enhance defenses, and secure your network. Learn more ➡️ bit.ly/3IeqtG9

💡 On Nexus, Jim Miller, Director of OT Cybersecurity for @MagnaInt, explains how distributed #OT factory environments manage #cybersecurity from cultural issues, to the need for proper #NetworkSegmentation, etc. Watch here: hubs.li/Q02_2GLC0 #Nexus24

Something went wrong.
Something went wrong.
United States Trends
- 1. World Cup 227K posts
- 2. Paraguay 23.7K posts
- 3. FINALLY DID IT 426K posts
- 4. The Jupiter 96.9K posts
- 5. Brazil 66.7K posts
- 6. Croatia 18.2K posts
- 7. Argentina 200K posts
- 8. Portugal 84.4K posts
- 9. #USMNT 1,286 posts
- 10. Infantino 59.1K posts
- 11. Matt Campbell 9,866 posts
- 12. Group L 13.2K posts
- 13. Ghana 69.6K posts
- 14. Norway 29.4K posts
- 15. Wayne Gretzky 3,675 posts
- 16. Senegal 39.8K posts
- 17. Lauryn Hill 10.4K posts
- 18. Iowa State 8,455 posts
- 19. Warner Bros 217K posts
- 20. #Mundial2026 31.9K posts


























