#communicationsecurity ผลการค้นหา
🔔 Welcome to read Editor's Choice Articles in the Q1 of 2024: 📌Title: A Holistic Analysis of #InternetofThings (IoT) #Security: Principles, Practices, and New Perspectives 🔗 mdpi.com/1999-5903/16/2… #communicationsecurity #devicesecurity #servicesecurity @ComSciMath_Mdpi

In today’s digital age, #communication is everywhere. Here are 8 strategies to consider to keep your organization’s communication safe. buff.ly/x2ajHGi #communicationsecurity #CyberAware

#Witanworld: #Security – Creating a Safer World witanworld.com/article/2020/0… #Communicationsecurity #Computersecurity #Economicsecurity #financialsecurity #Foodsecurity #Homesecurity #Homelandsecurity #Humansecurity #informationsecurity #MonetarySecurity #Nationalsecurity

Virtual Private Network(VPN): What is it and Why is it So Important To Protect Your Privacy? Computers and the Internet have become one of the main means of transmitting and processing information. #VPN #CommunicationSecurity #infosecurity

The AD8361ARMZ chip is a Korean Neowine vehicle-specified certified encryption chip that meets the requirements of vehicle network communication security and data encryption. #AD8361ARMZ #VehicleEncryptionChip #CommunicationSecurity #DataEncryption #AutomotiveElectronics

Never underestimate the security need of TX and TR #RFSecurity #CommunicationSecurity bit.ly/2OPD3Cp

Protecting communications from hackers with a new quantum-based procedure #communications #hackers #communicationsecurity #quantummechanics #UniofYork innovationtoronto.com/2018/06/protec…

Why AM FM Radio is the Ultimate Security Tool! #AMFMRadio #CommunicationSecurity #SnowyLandscape #InternetOfThings #TechDebate #ThrillerChat #RadioVsInternet #NetworkAnalysis #SniperScope #SurveillanceInsights
Shoghi with more than 20 years of experience in the development and design of customer-specific #militaryGrade Crypto System, Shoghi is a sincere partner for your end-to-end #communicationSecurity (COMSEC) and secure information transfer requirements. bit.ly/3kXDzgf

#NumberMasking is an advanced data protection measure designed to ensure the privacy of both the support agent and the caller. Avail of our number masking solution now! To know more, Visit: bit.ly/3v8hBeC #customerprivacy #communicationsecurity #cloud #Fonada

🔒 Security is our top priority! With Vital™ UCaaS, rest assured that your communication is protected by the latest encryption and security protocols. hubs.la/Q02lGQk00 #CommunicationSecurity #DataProtection

Shoghi is a sincere partner for your requirements of end-to-end #communicationsecurity (COMSEC) and secure information transfer. We have strong experience in creating customer-specific Algorithms and Key management schemes. bit.ly/3aiH9e9 #shoghicom #defenceindustry

Discover how Convergia implemented encrypted SIP trunks to ensure secure and reliable voice services in our latest success case here: okt.to/qgy8JG #Convergia #Ecommerce #CommunicationSecurity #SIPTrunks #VoiceServices #TechnologySolutions #WeAreBetterTogether

🔒 Security is our top priority! With Vital™ UCaaS, rest assured that your communication is protected by the latest encryption and security protocols. hubs.la/Q02lGHF80 #CommunicationSecurity #DataProtection

The articles in our January issue survey the topic of cloud-native computing and physical layer covert communications. bit.ly/3IlbhXr #CloudNativeApplications #CommunicationSecurity

in digital and physical convergence through digital communication security, and ultimately elevating the business scene in the SEA region #Partnership #communicationsecurity #kardiaChain #Blockchain
Report: Using Machine Intelligent Technology to Prevent Highly Sensitive Information Being Leaked 📤 buff.ly/2HZ1zMK #MisadressedEmails #DataBreach #CommunicationSecurity

🛡️ Discover the evolution of communication security and how Alien's innovative blockchain-based encryption technology is reshaping the future of secure communication. Learn about Alien's unprecedented security guarantees. #CommunicationSecurity #Blockcha… ift.tt/R0cmYCQ
Le soluzioni di #CommunicationSecurity di #Telsy offrono risposte semplici ed efficienti per la massima protezione alle #comunicazioni on e offline, mantenendo usabilità e design dei dispositivi tradizionali. Scopri di più: bit.ly/3OpWrky @TIM_Enterprise #cybersecurity

🔔 Welcome to read Editor's Choice Articles in the Q1 of 2024: 📌Title: A Holistic Analysis of #InternetofThings (IoT) #Security: Principles, Practices, and New Perspectives 🔗 mdpi.com/1999-5903/16/2… #communicationsecurity #devicesecurity #servicesecurity @ComSciMath_Mdpi

In today’s digital age, #communication is everywhere. Here are 8 strategies to consider to keep your organization’s communication safe. buff.ly/x2ajHGi #communicationsecurity #CyberAware

A giugno è stato scoperto un archivio da 47 GB contenente 184 mln di credenziali rubate, frutto di un’esfiltrazione causata da un #InfoStealer 🔎 Jeremiah Fowler Scopri le soluzioni di #Cybersecurity e #CommunicationSecurity di #Telsy 👉 telsy.com/soluzioni @TIM_Enterprise
🔔 Welcome to read Editor's Choice Articles in the Q1 of 2024: 📌Title: A Holistic Analysis of #InternetofThings (IoT) Security: Principles, Practices, and New Perspectives 🔗 mdpi.com/1999-5903/16/2… #security #communicationsecurity #servicesecurity @ComSciMath_Mdpi
Polymer Labs' integration of AI and blockchain is enhancing the security of blockchain - based communication channels. It prevents eavesdropping. #CommunicationSecurity #PolymerLabs @Polymer_Labs
The future of IT in BIOT could include the development of autonomous systems that streamline defense operations while enhancing communication security. #AutonomousSystems #DefenseOperations #CommunicationSecurity
¥ How can exchanges better communicate security vulnerabilities to their users? What about Huobi, Gate.io and Bitfinex? #CommunicationSecurity #ExchangeVulnerabilities ift.tt/CWf2dR3 Talk crypto with us, comment...
cryptomaps.tech
Gate.io vs Huobi vs Bitfinex: Which Exchange is More Secure?
Gate.io vs Huobi vs Bitfinex: Which Exchange is More Secure?
. @soon_svm #SOONISTHEREDPILL soon_svm's blockchain's secure communication channels protect your data in transit. Send and receive information with confidence. #soon_svm #CommunicationSecurity
it used to be the "third man is listening"....now its the "third man has entered the chat".... 😱🫥 #communicationsecurity
How many times does Pete Hegseth need to leak classified intelligence before Donald Trump and Republicans understand that he isn’t only a f*cking liar, he is a threat to our national security? Every day he stays in his job is another day our troops’ lives are endangered by his…
2025 2nd International Conference on Communication Security and Information Processing (CSIP 2025)will be held in Guangzhou, China from May 9th to 11th, 2025. Conference Website: ais.cn/u/7VJZzu #internationalconference #CommunicationSecurity #InformationProcessing

Exploring blockchain, Bulgaria's telecom industry is set to revolutionize communication security, creating a safer digital space. #BlockchainInnovation #CommunicationSecurity 🔗🔒
First, WhatsApp wasn’t compliant. Then, Microsoft Teams and Slack became prime #cyberattack targets. And with messaging apps constantly under scrutiny, businesses need to rethink their #communicationsecurity.’ Learn how here: hubs.la/Q037tb0J0
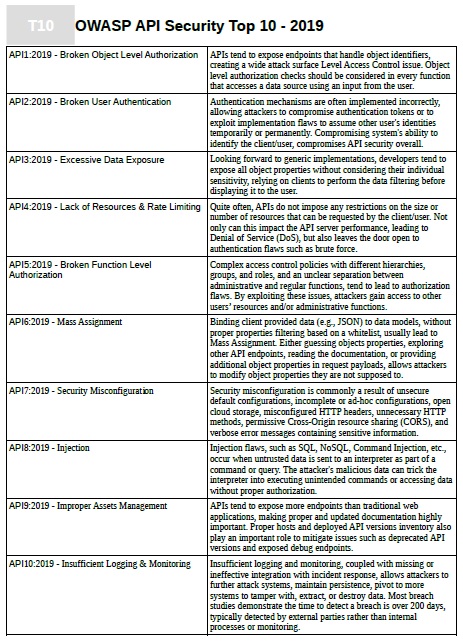
📢 MDPIfutureinternet [Top Cited Papers in 2024] 🚩Title: A Holistic Analysis of #InternetofThings (IoT) #Security: Principles, Practices, and New Perspectives 📌Views: 8806 📌Citations: 14 mdpi.com/1999-5903/16/2… #communicationsecurity #devicesecurity #servicesecurity
![FutureInternet6's tweet image. 📢 MDPIfutureinternet [Top Cited Papers in 2024]
🚩Title: A Holistic Analysis of #InternetofThings (IoT) #Security: Principles, Practices, and New Perspectives
📌Views: 8806
📌Citations: 14
mdpi.com/1999-5903/16/2…
#communicationsecurity #devicesecurity #servicesecurity](https://pbs.twimg.com/media/GkNlwgtboAA1bQv.png)
6️⃣ GSM Jammer Urządzenie blokujące sygnały telefonii komórkowej i zakłócające komunikację. 🚫 Nielegalne w wielu regionach ze względu na możliwość niewłaściwego wykorzystania—bądź świadomy! #SignalBlocking #GSMJammer #CommunicationSecurity
6️⃣ GSM Jammer A device that blocks cell phone signals and disrupts communication. 🚫 Illegal in many regions due to misuse potential—stay aware! #SignalBlocking #GSMJammer #CommunicationSecurity
Why AM FM Radio is the Ultimate Security Tool! #AMFMRadio #CommunicationSecurity #SnowyLandscape #InternetOfThings #TechDebate #ThrillerChat #RadioVsInternet #NetworkAnalysis #SniperScope #SurveillanceInsights
"Starlink's launch in India opens new opportunities! Let's collaborate to strengthen India's communication security & propel growth. #StarlinkIndiaLaunch #CommunicationSecurity #IndiaGrows #DigitalFuture" From #CustomerExperience @elonmusk @
📢#MDPIfutureinternet [Most Viewed Papers in Last 12 Months] 📌A Holistic Analysis of #InternetofThings (IoT) Security: Principles, Practices, and New Perspectives Views: 6955 Citations: 5 mdpi.com/1999-5903/16/2… #communicationsecurity #devicesecurity #servicesecurity
![FutureInternet6's tweet image. 📢#MDPIfutureinternet [Most Viewed Papers in Last 12 Months]
📌A Holistic Analysis of #InternetofThings (IoT) Security: Principles, Practices, and New Perspectives
Views: 6955
Citations: 5
mdpi.com/1999-5903/16/2…
#communicationsecurity #devicesecurity #servicesecurity](https://pbs.twimg.com/media/GWdb8x9boAA-Wz8.jpg)
🔔 Welcome to read Editor's Choice Articles in the Q1 of 2024: 📌Title: A Holistic Analysis of #InternetofThings (IoT) #Security: Principles, Practices, and New Perspectives 🔗 mdpi.com/1999-5903/16/2… #communicationsecurity #devicesecurity #servicesecurity @ComSciMath_Mdpi

In today’s digital age, #communication is everywhere. Here are 8 strategies to consider to keep your organization’s communication safe. buff.ly/x2ajHGi #communicationsecurity #CyberAware

The articles in our January issue survey the topic of cloud-native computing and physical layer covert communications. bit.ly/3IlbhXr #CloudNativeApplications #CommunicationSecurity

#Witanworld: #Security – Creating a Safer World witanworld.com/article/2020/0… #Communicationsecurity #Computersecurity #Economicsecurity #financialsecurity #Foodsecurity #Homesecurity #Homelandsecurity #Humansecurity #informationsecurity #MonetarySecurity #Nationalsecurity

Never underestimate the security need of TX and TR #RFSecurity #CommunicationSecurity bit.ly/2OPD3Cp

The AD8361ARMZ chip is a Korean Neowine vehicle-specified certified encryption chip that meets the requirements of vehicle network communication security and data encryption. #AD8361ARMZ #VehicleEncryptionChip #CommunicationSecurity #DataEncryption #AutomotiveElectronics

Le soluzioni di #CommunicationSecurity di #Telsy offrono risposte semplici ed efficienti per la massima protezione alle #comunicazioni on e offline, mantenendo usabilità e design dei dispositivi tradizionali. Scopri di più: bit.ly/3OpWrky @TIM_Enterprise #cybersecurity

Discover how Convergia implemented encrypted SIP trunks to ensure secure and reliable voice services in our latest success case here: okt.to/qgy8JG #Convergia #Ecommerce #CommunicationSecurity #SIPTrunks #VoiceServices #TechnologySolutions #WeAreBetterTogether

Shoghi with more than 20 years of experience in the development and design of customer-specific #militaryGrade Crypto System, Shoghi is a sincere partner for your end-to-end #communicationSecurity (COMSEC) and secure information transfer requirements. bit.ly/3kXDzgf

Shoghi is a sincere partner for your requirements of end-to-end #communicationsecurity (COMSEC) and secure information transfer. We have strong experience in creating customer-specific Algorithms and Key management schemes. bit.ly/3aiH9e9 #shoghicom #defenceindustry

Virtual Private Network(VPN): What is it and Why is it So Important To Protect Your Privacy? Computers and the Internet have become one of the main means of transmitting and processing information. #VPN #CommunicationSecurity #infosecurity

Protecting communications from hackers with a new quantum-based procedure #communications #hackers #communicationsecurity #quantummechanics #UniofYork innovationtoronto.com/2018/06/protec…

2025 2nd International Conference on Communication Security and Information Processing (CSIP 2025)will be held in Guangzhou, China from May 9th to 11th, 2025. Conference Website: ais.cn/u/7VJZzu #internationalconference #CommunicationSecurity #InformationProcessing

🔒 Security is our top priority! With Vital™ UCaaS, rest assured that your communication is protected by the latest encryption and security protocols. hubs.la/Q02lGHF80 #CommunicationSecurity #DataProtection

Report: Using Machine Intelligent Technology to Prevent Highly Sensitive Information Being Leaked 📤 buff.ly/2HZ1zMK #MisadressedEmails #DataBreach #CommunicationSecurity

#NumberMasking is an advanced data protection measure designed to ensure the privacy of both the support agent and the caller. Avail of our number masking solution now! To know more, Visit: bit.ly/3v8hBeC #customerprivacy #communicationsecurity #cloud #Fonada

📢#MDPIfutureinternet [Most Viewed Papers in Last 12 Months] 📌A Holistic Analysis of #InternetofThings (IoT) Security: Principles, Practices, and New Perspectives Views: 6955 Citations: 5 mdpi.com/1999-5903/16/2… #communicationsecurity #devicesecurity #servicesecurity
![FutureInternet6's tweet image. 📢#MDPIfutureinternet [Most Viewed Papers in Last 12 Months]
📌A Holistic Analysis of #InternetofThings (IoT) Security: Principles, Practices, and New Perspectives
Views: 6955
Citations: 5
mdpi.com/1999-5903/16/2…
#communicationsecurity #devicesecurity #servicesecurity](https://pbs.twimg.com/media/GWdb8x9boAA-Wz8.jpg)
Join the conversation on ephemeral messaging and its impact on compliance. Expert insights for robust communication strategies 📊 safeguardcyber.com/blog/complianc… #communicationsecurity #expertdiscussion

🔒 Security is our top priority! With Vital™ UCaaS, rest assured that your communication is protected by the latest encryption and security protocols. hubs.la/Q02lGQk00 #CommunicationSecurity #DataProtection

Something went wrong.
Something went wrong.
United States Trends
- 1. Texas 155K posts
- 2. 3-8 Florida 2,007 posts
- 3. #HookEm 10.4K posts
- 4. Austin Reaves 11.7K posts
- 5. Sark 5,005 posts
- 6. Jeff Sims 1,654 posts
- 7. Arch 25.3K posts
- 8. Aggies 9,233 posts
- 9. #JimmySeaFanconD1 210K posts
- 10. Arizona 32.5K posts
- 11. Marcel Reed 4,413 posts
- 12. #LakeShow 3,392 posts
- 13. #DonCheadleDay 1,091 posts
- 14. Elko 2,970 posts
- 15. SEC Championship 5,186 posts
- 16. Banana Fish 8,661 posts
- 17. Ole Miss 25.8K posts
- 18. Devin Vassell 2,315 posts
- 19. Lindor 2,643 posts
- 20. #OPLive 2,453 posts

























![LovingMY_Aniya's profile picture. Mother Of Two Gorgeous Girls [Aniya & Aaliyah] Wifey Of An Amazing Rapper [Travis] ♥12.30.11| 09.06.2013 | 06.06.12♥](https://pbs.twimg.com/profile_images/2886117351/b917e09a047da64df072e808bdbbd2f8.jpeg)





