#computersecurity risultati di ricerca
#AIbrowsers - Ah, no thanks. #ComputerSecurity youtube.com/watch?v=iUNqFC…

youtube.com
YouTube
AI browsers are scary
This ridiculous pattern is the world's most common password. Even if you aren't from Rome, you should be able to read it... ... if not, just guess it 😒 - - - #computersecurity #password #roman #cybersecurity #day1712

Tech Tip: Use a password manager. lightningstrikestudios.com #ComputerSecurity #InformationTechnology

Cybersecurity Deconstructed: Advanced Techniques and Internals leanpub.com/courses/leanpu… by Steve T. is the featured course on the Leanpub homepage! leanpub.com #ComputerSecurity #CloudComputing #AmazonWebServices #MicrosoftAzure Go beyond abstractions and master the…

Tech Tip: Check your backups regularly. lightningstrikestudios.com #ComputerSecurity #InformationTechnology

Tech Tip: Learn to identify email scams. lightningstrikestudios.com #ComputerSecurity #InformationTechnology

Tech Tip: Wipe your data before trashing old computers. lightningstrikestudios.com #ComputerSecurity #InformationTechnology

CISM: The Last Mile: Your guide to the finish line by Pete Zerger is the featured book on the Leanpub homepage! #ComputerSecurity #books #CISM This book covers every topic in the latest CISM exam syllabus, approaching topics from the ISACA perspective. It's 325+ pages organized…

Fake #CAPTCHA websites hijack your clipboard to install information stealers ⇨ buff.ly/uEmoHun. #malware #computersecurity

Tech Tip: Don't expect “private” browsing mode to keep your data private. lightningstrikestudios.com #ComputerSecurity #InformationTechnology

We have extended the application deadline until 4 September! Undertake research in topics related to #drones, #photonics, #computersecurity, #batteries, #AI, and #mathematics. Apply here: ow.ly/ZKwW50T8u4H #HorizonEU #ResearchImpactEU #ResearchJob #HiringNow #PhDPosition
Secure Android Design and Development: From App Layer to HAL – Aligned with Android 15 by Mohammad Hossein Heydarchi is the featured course on the Leanpub homepage! #Android #ComputerSecurity #ComputerProgramming "Secure Android Design & Development" is an effort to provide a…

🔥 Read our Highly Cited Paper 📚 An Efficient Boosting-Based Windows Malware Family Classification System Using Multi-Features Fusion 🔗 mdpi.com/2076-3417/13/6… 👨🔬 by Zhiguo Chen et al. #computersecurity #machinelearning

ಕಂಪ್ಯೂಟರ್ ಭದ್ರತಾ ದಿನ ತಂತ್ರಜ್ಞಾನ ಮುಂದುವರಿದಂತೆ ನಮ್ಮ ಅತ್ಯಮೂಲ್ಯ ಡೇಟಾಗಳ ಭದ್ರತೆ ಕೂಡ ಮುಖ್ಯವಾಗಿದೆ. ಈ ನಿಟ್ಟಿನಲ್ಲಿ ಇನ್ನಷ್ಟು ಜಾಗೃತಿ ಮೂಡಿಸುವ ಅಗತ್ಯವಿದೆ. #ComputerSecurity #dataprivacy #dataprotection #KeerthanKumar #Congress #congresskarnataka #Karnataka #congressguarantee #Indiabloc #INDIA…

🔍💻 Tensions are rising, as we navigate the exciting landscape where low-level computer architecture innovations meet the critical challenges of system security Join @_onurmutlu_ at #hw_ioNL2024 👉 Know More: hardwear.io/netherlands-20… #computersecurity #hardware #architecture

We've analyzed hundreds of reviews of Computer Security software solutions for you. Find out the top 15 that placed on our 2023 #CategoryLeaders ranking 🏆, and compare the leading tools 👍 ➡️ bit.ly/3SreBWU #ComputerSecurity #SoftwareSelection
Attend the FREE TikTok Privacy Innovation pre-conference meetup to get yourself ready for IEEE S&P Week. 📆May 11 at 4:30 – 6:30 PM PT ✅RSVP bit.ly/4jMUyg6 🗣️ TikTok's here to talk @ Hyatt Regency San Francisco #computersecurity #privacy #technology #dataprivacy

🔍 Join @_onurmutlu_ at #hw_ioNL2024 as he explores the vital connection between computer architecture and system security, highlighting trends that shape hardware vulnerabilities! ⚙️💻 Know More: hardwear.io/netherlands-20… #computersecurity #hardwarearchitecture #hardwaresecurity

The course Cybersecurity Deconstructed by Steve T. is on sale on Leanpub! Its suggested price is $179.00; get it for $89.00 with this coupon: leanpub.com/sh/kAiFWgMN #ComputerSecurity #CloudComputing #AmazonWebServices #MicrosoftAzure
Code, Chips and Control by Sal Kimmich is on sale on Leanpub! Its suggested price is $39.00; get it for $14.99 with this coupon: leanpub.com/sh/dySYpeZE #ComputerSecurity
The bundle Accelerated Windows Memory Dump Analysis by Dmitry Vostokov is on sale on Leanpub! Its suggested price is $98.00; get it for $60.00 with this coupon: leanpub.com/b/dumpanalysis… @DumpAnalysis #CAndCpp #ComputerSecurity #Resiliency
Several security weaknesses have been found in #Mozilla products that could potentially enable hackers to run any code they choose. More info: mzl.la/3GMlVoA #computersecurity #vulnerabilities #cybersecurity

There has been an update to #Adobe products. If you are using any of the products indicated in the advisory, please make sure you are running the latest versions. More info: helpx.adobe.com/security.html #computersecurity #vulnerabilities

The course Cybersecurity Deconstructed by Steve T. is on sale on Leanpub! Its suggested price is $179.00; get it for $89.00 with this coupon: leanpub.com/sh/kAiFWgMN #ComputerSecurity #CloudComputing #AmazonWebServices #MicrosoftAzure
The course Secure Android Design and Development by Mohammad Hossein Heydarchi is on sale on Leanpub! Its suggested price is $179.00; get it for $89.00 with this coupon: leanpub.com/sh/h3pouttj #Android #ComputerSecurity #ComputerProgramming
Please ensure that all your #Apple devices are up-to-date as there are vulnerabilities that could put them at risk of being hacked. More info: support.apple.com/en-us/HT201222 #computersecurity #vulnerabilities #cybersecurity

Secure Android Design and Development: From App Layer to HAL – Aligned with Android 15 by Mohammad Hossein Heydarchi is the featured course on the Leanpub homepage! #Android #ComputerSecurity #ComputerProgramming "Secure Android Design & Development" is an effort to provide a…

CISM: The Last Mile: Your guide to the finish line by Pete Zerger is the featured book on the Leanpub homepage! #ComputerSecurity #books #CISM This book covers every topic in the latest CISM exam syllabus, approaching topics from the ISACA perspective. It's 325+ pages organized…

Code, Chips and Control: The Security Posture of Digital Isolation leanpub.com/codechipsandco… by Sal Kimmich is the featured book on the Leanpub homepage! leanpub.com #ComputerSecurity #cybersecurity #technology #opensource #history
The bundle Linux Debugging by Dmitry Vostokov is on sale on Leanpub! Its suggested price is $197.00; get it for $111.75 with this coupon: leanpub.com/b/debugging/c/… @DumpAnalysis #CAndCpp #ComputerSecurity #OperatingSystemDevelopment
A.I. Is Deciding Who You Are: In the age of A.I., personal data is anything but personal. dlvr.it/TP1rDL #ArtificialIntelligence #ComputersandtheInternet #ComputerSecurity

The course Secure Android Design and Development by Mohammad Hossein Heydarchi is on sale on Leanpub! Its suggested price is $179.00; get it for $89.00 with this coupon: leanpub.com/sh/VxPNyVsp #Android #ComputerSecurity #ComputerProgramming
#AIbrowsers - Ah, no thanks. #ComputerSecurity youtube.com/watch?v=iUNqFC…

youtube.com
YouTube
AI browsers are scary
A brief history of computers and cyber warfare #computersecurity #CyberSecurity #history #ComputingForever slideshare.net/slideshow/a-br…

slideshare.net
A Brief History of Computer and Cyber Warfare
Hoy es el Día Internacional de la Seguridad Informática #SeguridadInformática / Today is International Computer Security Day #ComputerSecurity 😉💗


Attend the FREE TikTok Privacy Innovation pre-conference meetup to get yourself ready for IEEE S&P Week. 📆May 11 at 4:30 – 6:30 PM PT ✅RSVP bit.ly/4jMUyg6 🗣️ TikTok's here to talk @ Hyatt Regency San Francisco #computersecurity #privacy #technology #dataprivacy

Fake #CAPTCHA websites hijack your clipboard to install information stealers ⇨ buff.ly/uEmoHun. #malware #computersecurity

🔍💻 Tensions are rising, as we navigate the exciting landscape where low-level computer architecture innovations meet the critical challenges of system security Join @_onurmutlu_ at #hw_ioNL2024 👉 Know More: hardwear.io/netherlands-20… #computersecurity #hardware #architecture

CISSP: The Last Mile: Your guide to the finish line by Pete Zerger is the featured book on the Leanpub homepage! #ComputerSecurity #CloudComputing #Cryptography #books #ebooks #CISSP The book covers every topic in the latest CISSP exam syllabus, organized in a format that makes…

🔍 Join @_onurmutlu_ at #hw_ioNL2024 as he explores the vital connection between computer architecture and system security, highlighting trends that shape hardware vulnerabilities! ⚙️💻 Know More: hardwear.io/netherlands-20… #computersecurity #hardwarearchitecture #hardwaresecurity

Tech Tip: Back up your cell phone. lightningstrikestudios.com #ComputerSecurity #InformationTechnology

Tech Tip: Use a password manager. lightningstrikestudios.com #ComputerSecurity #InformationTechnology

This ridiculous pattern is the world's most common password. Even if you aren't from Rome, you should be able to read it... ... if not, just guess it 😒 - - - #computersecurity #password #roman #cybersecurity #day1712

AmericaComputers.com live domain name auction. #laptops #computersecurity #techy #computerspellen #geek #gamingcomputers #gadget #computersciencemajor #device #computers #technology #computerscience #tech #electronics #computersetup #gadgets #computerscientist #techie

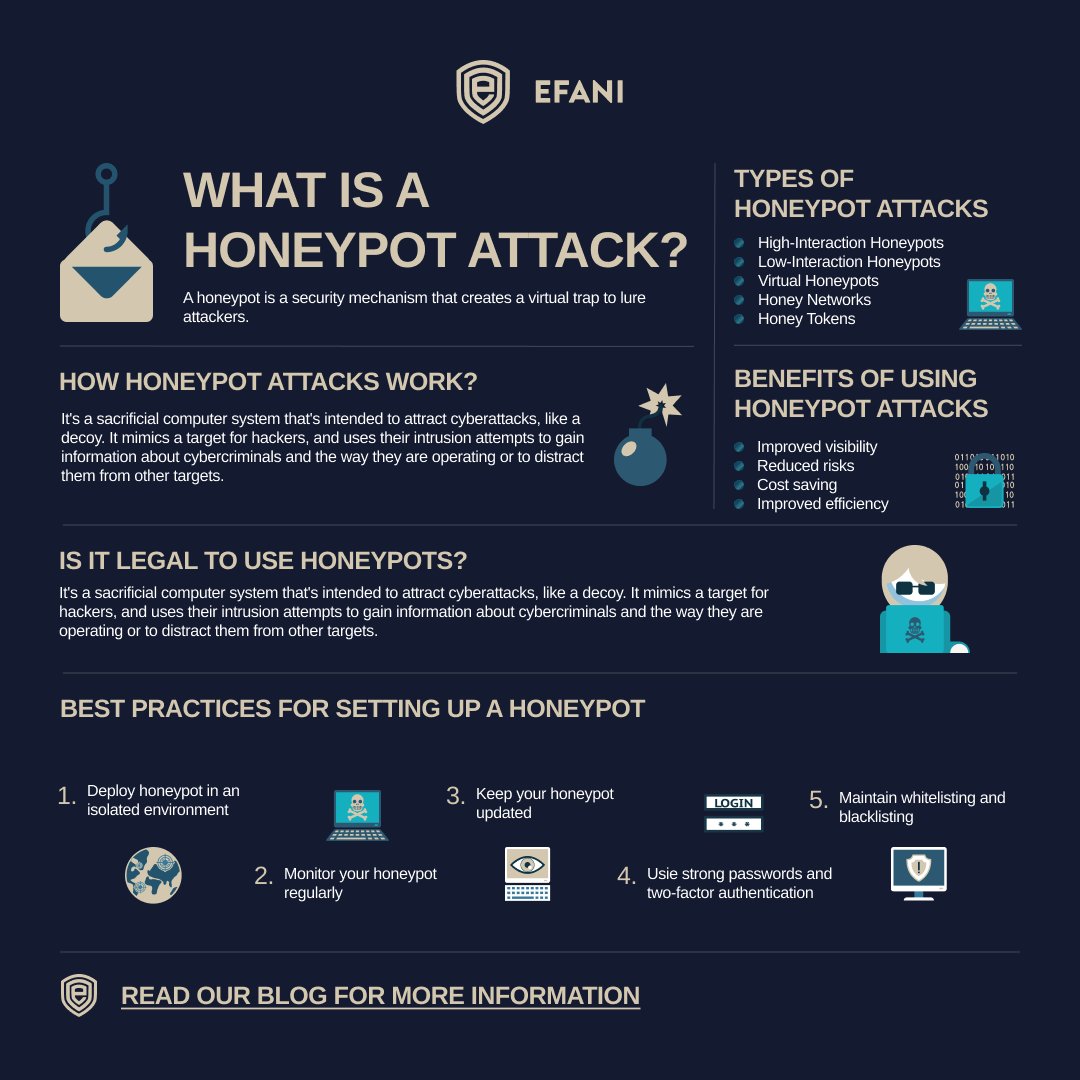
A cyber honeypot is a sacrificial computer system intended to attract cyberattacks. It mimics a target for hackers & uses their intrusion attempts to gain information about cyber criminals & how they operate/distract them from other targets. #computersecurity #honeypot
Tech Tip: Use unique secure passwords. lightningstrikestudios.com #ComputerSecurity #InformationTechnology

The API Gateway Handbook: Your Practical Guide to API Gateway Setup, Security, and Operation by Thomas Bayer and Tobias Polley @rrayst is the featured book on the Leanpub homepage! #Networking #ComputerSecurity #apis #books #ebooks Whether you’re exposing APIs to partners,…

A #ComputerVirus can wreak havoc on devices and be a huge threat to your company's private data. Here is a simple but important reminder as to why computer viruses occur. #ComputerSecurity #CyberSecurity




Tech Tip: Check your backups regularly. lightningstrikestudios.com #ComputerSecurity #InformationTechnology

Payloads All The Things: Web Application Security Cheatsheets by Swissky is the featured book on the Leanpub homepage! #ComputerProgramming #ComputerSecurity #books #ebooks @pentest_swissky Complete with detailed explanations, practical examples, and real-world scenarios,…

JavaScript for hackers: Learn to think like a hacker by Gareth Heyes @garethheyes is the featured book on the Leanpub homepage! #JavaScript #ComputerSecurity #ComputerProgramming #books #ebooks Learn how to find interesting behaviour and flaws in JavaScript. Reading this book…

CISM: The Last Mile: Your guide to the finish line by Pete Zerger is the featured book on the Leanpub homepage! #ComputerSecurity #books #ebooks #CISM @pzerger This book covers every topic in the latest CISM exam syllabus, approaching topics from the ISACA perspective. It's…

🔥 Read our Highly Cited Paper 📚 An Efficient Boosting-Based Windows Malware Family Classification System Using Multi-Features Fusion 🔗 mdpi.com/2076-3417/13/6… 👨🔬 by Zhiguo Chen et al. #computersecurity #machinelearning

Something went wrong.
Something went wrong.
United States Trends
- 1. #UFC322 38.8K posts
- 2. Ewing 5,792 posts
- 3. Bama 19.3K posts
- 4. Wellmaker 4,127 posts
- 5. Oklahoma 29.4K posts
- 6. Noah Thomas N/A
- 7. #AEWCollision 4,958 posts
- 8. Arch 17.8K posts
- 9. Wingo 1,346 posts
- 10. Jeremiah Smith 2,115 posts
- 11. Ty Simpson 3,859 posts
- 12. Bronny 5,206 posts
- 13. Boomer Sooner 2,189 posts
- 14. #GoDawgs 5,191 posts
- 15. Georgia 79.2K posts
- 16. UConn 4,787 posts
- 17. Sabatini 1,386 posts
- 18. Shapen N/A
- 19. Iowa 20.1K posts
- 20. James Peoples N/A