#computersecurity search results
This ridiculous pattern is the world's most common password. Even if you aren't from Rome, you should be able to read it... ... if not, just guess it 😒 - - - #computersecurity #password #roman #cybersecurity #day1712

Tech Tip: Use a password manager. lightningstrikestudios.com #ComputerSecurity #InformationTechnology

Tech Tip: Check your backups regularly. lightningstrikestudios.com #ComputerSecurity #InformationTechnology

Tech Tip: Learn to identify email scams. lightningstrikestudios.com #ComputerSecurity #InformationTechnology

Tech Tip: Wipe your data before trashing old computers. lightningstrikestudios.com #ComputerSecurity #InformationTechnology

Tech Tip: Don't expect “private” browsing mode to keep your data private. lightningstrikestudios.com #ComputerSecurity #InformationTechnology

Fake #CAPTCHA websites hijack your clipboard to install information stealers ⇨ buff.ly/uEmoHun. #malware #computersecurity

Cybersecurity Deconstructed: Advanced Techniques and Internals leanpub.com/courses/leanpu… by Steve T. is the featured course on the Leanpub homepage! leanpub.com #ComputerSecurity #CloudComputing #AmazonWebServices #MicrosoftAzure Go beyond abstractions and master the…

ಕಂಪ್ಯೂಟರ್ ಭದ್ರತಾ ದಿನ ತಂತ್ರಜ್ಞಾನ ಮುಂದುವರಿದಂತೆ ನಮ್ಮ ಅತ್ಯಮೂಲ್ಯ ಡೇಟಾಗಳ ಭದ್ರತೆ ಕೂಡ ಮುಖ್ಯವಾಗಿದೆ. ಈ ನಿಟ್ಟಿನಲ್ಲಿ ಇನ್ನಷ್ಟು ಜಾಗೃತಿ ಮೂಡಿಸುವ ಅಗತ್ಯವಿದೆ. #ComputerSecurity #dataprivacy #dataprotection #KeerthanKumar #Congress #congresskarnataka #Karnataka #congressguarantee #Indiabloc #INDIA…

🔥 Read our Highly Cited Paper 📚 An Efficient Boosting-Based Windows Malware Family Classification System Using Multi-Features Fusion 🔗 mdpi.com/2076-3417/13/6… 👨🔬 by Zhiguo Chen et al. #computersecurity #machinelearning

We have extended the application deadline until 4 September! Undertake research in topics related to #drones, #photonics, #computersecurity, #batteries, #AI, and #mathematics. Apply here: ow.ly/ZKwW50T8u4H #HorizonEU #ResearchImpactEU #ResearchJob #HiringNow #PhDPosition
This #ComputerSecurity Day 🌐🔒, #TeamIEM reminds you to be proactive in keeping your digital life safe & secure. Use these #cybersecurity tips: 1️⃣ Use unique, complex passwords 2️⃣ Enable multi-factor authentication 3️⃣ Keep your software updated 4️⃣ Be cautious of phishing

🔍💻 Tensions are rising, as we navigate the exciting landscape where low-level computer architecture innovations meet the critical challenges of system security Join @_onurmutlu_ at #hw_ioNL2024 👉 Know More: hardwear.io/netherlands-20… #computersecurity #hardware #architecture

We've analyzed hundreds of reviews of Computer Security software solutions for you. Find out the top 15 that placed on our 2023 #CategoryLeaders ranking 🏆, and compare the leading tools 👍 ➡️ bit.ly/3SreBWU #ComputerSecurity #SoftwareSelection
🔍 Join @_onurmutlu_ at #hw_ioNL2024 as he explores the vital connection between computer architecture and system security, highlighting trends that shape hardware vulnerabilities! ⚙️💻 Know More: hardwear.io/netherlands-20… #computersecurity #hardwarearchitecture #hardwaresecurity

The bundle Linux Debugging by Dmitry Vostokov is on sale on Leanpub! Its suggested price is $197.00; get it for $111.75 with this coupon: leanpub.com/b/debugging/c/… @DumpAnalysis #CAndCpp #ComputerSecurity #OperatingSystemDevelopment
A.I. Is Deciding Who You Are: In the age of A.I., personal data is anything but personal. dlvr.it/TP1rDL #ArtificialIntelligence #ComputersandtheInternet #ComputerSecurity

The course Secure Android Design and Development by Mohammad Hossein Heydarchi is on sale on Leanpub! Its suggested price is $179.00; get it for $89.00 with this coupon: leanpub.com/sh/VxPNyVsp #Android #ComputerSecurity #ComputerProgramming
#AIbrowsers - Ah, no thanks. #ComputerSecurity youtube.com/watch?v=iUNqFC…

youtube.com
YouTube
AI browsers are scary
A brief history of computers and cyber warfare #computersecurity #CyberSecurity #history #ComputingForever slideshare.net/slideshow/a-br…

slideshare.net
A Brief History of Computer and Cyber Warfare
JavaScript for hackers by Gareth Heyes is on sale on Leanpub! Its suggested price is $35.00; get it for $14.00 with this coupon: leanpub.com/sh/7pBsj0nv @garethheyes #Javascript #ComputerSecurity #ComputerProgramming
The course Secure Android Design and Development by Mohammad Hossein Heydarchi is on sale on Leanpub! Its suggested price is $179.00; get it for $89.00 with this coupon: leanpub.com/sh/jJ5qtBVq #Android #ComputerSecurity #ComputerProgramming
JavaScript for hackers by Gareth Heyes is on sale on Leanpub! Its suggested price is $35.00; get it for $14.00 with this coupon: leanpub.com/sh/EGOZSh0o @garethheyes #Javascript #ComputerSecurity #ComputerProgramming
🔒 Your Data Deserves Defense As cyber threats evolve, compliance and protection are no longer optional — they’re essential. #ComputerSecurity #CyberSecurity #DataProtection #TechCompliance #DigitalSafety #TechDigitalMinds

The course Secure Android Design and Development by Mohammad Hossein Heydarchi is on sale on Leanpub! Its suggested price is $179.00; get it for $89.00 with this coupon: leanpub.com/sh/eq3BzoQP #Android #ComputerSecurity
Hoy es el Día Internacional de la Seguridad Informática #SeguridadInformática / Today is International Computer Security Day #ComputerSecurity 😉💗


Today is Computer Security Day! 💻 Always take steps to ensure your critical data is safe, including: 1. Utilizing unique, long and complex passwords 2. Enabling multi-factor authentication 3. Keeping software updated And the list goes on! #computersecurity #criticaldata #mfa

Attend the FREE TikTok Privacy Innovation pre-conference meetup to get yourself ready for IEEE S&P Week. 📆May 11 at 4:30 – 6:30 PM PT ✅RSVP bit.ly/4jMUyg6 🗣️ TikTok's here to talk @ Hyatt Regency San Francisco #computersecurity #privacy #technology #dataprivacy

Fake #CAPTCHA websites hijack your clipboard to install information stealers ⇨ buff.ly/uEmoHun. #malware #computersecurity

On this Computer Security Day, brush up on your online safety practices with strong passwords, updated software, and regular data backing. Ensuring Digital safety is the need of the hour! #computersecurity #informationtechnology #CyberSecurityAwareness #ideateimplementsucceed

AmericaComputers.com live domain name auction. #laptops #computersecurity #techy #computerspellen #geek #gamingcomputers #gadget #computersciencemajor #device #computers #technology #computerscience #tech #electronics #computersetup #gadgets #computerscientist #techie

A #ComputerVirus can wreak havoc on devices and be a huge threat to your company's private data. Here is a simple but important reminder as to why computer viruses occur. #ComputerSecurity #CyberSecurity




+1 month after a successful internship, Denim Latic joined our team as a full member. 📌Reinforcing our security team, he'll analyse & manage #computersecurity incidents while pursuing his study in B.U.T réseaux et télécommunications at @IUTNancyBrabois 👏 Welcome (back) aboard!

It’s National Computer Security Day and #YourFDLE wants you and your business to stay safe & #secure! Visit FDLE’s SecureFlorida.org for tips & resources to help you safeguard your info systems & reduce your vulnerability to cyber-attacks. #ComputerSecurity #Cybersecurity

Payloads All The Things: Web Application Security Cheatsheets by Swissky is the featured book on the Leanpub homepage! #ComputerProgramming #ComputerSecurity #books #ebooks @pentest_swissky Complete with detailed explanations, practical examples, and real-world scenarios,…

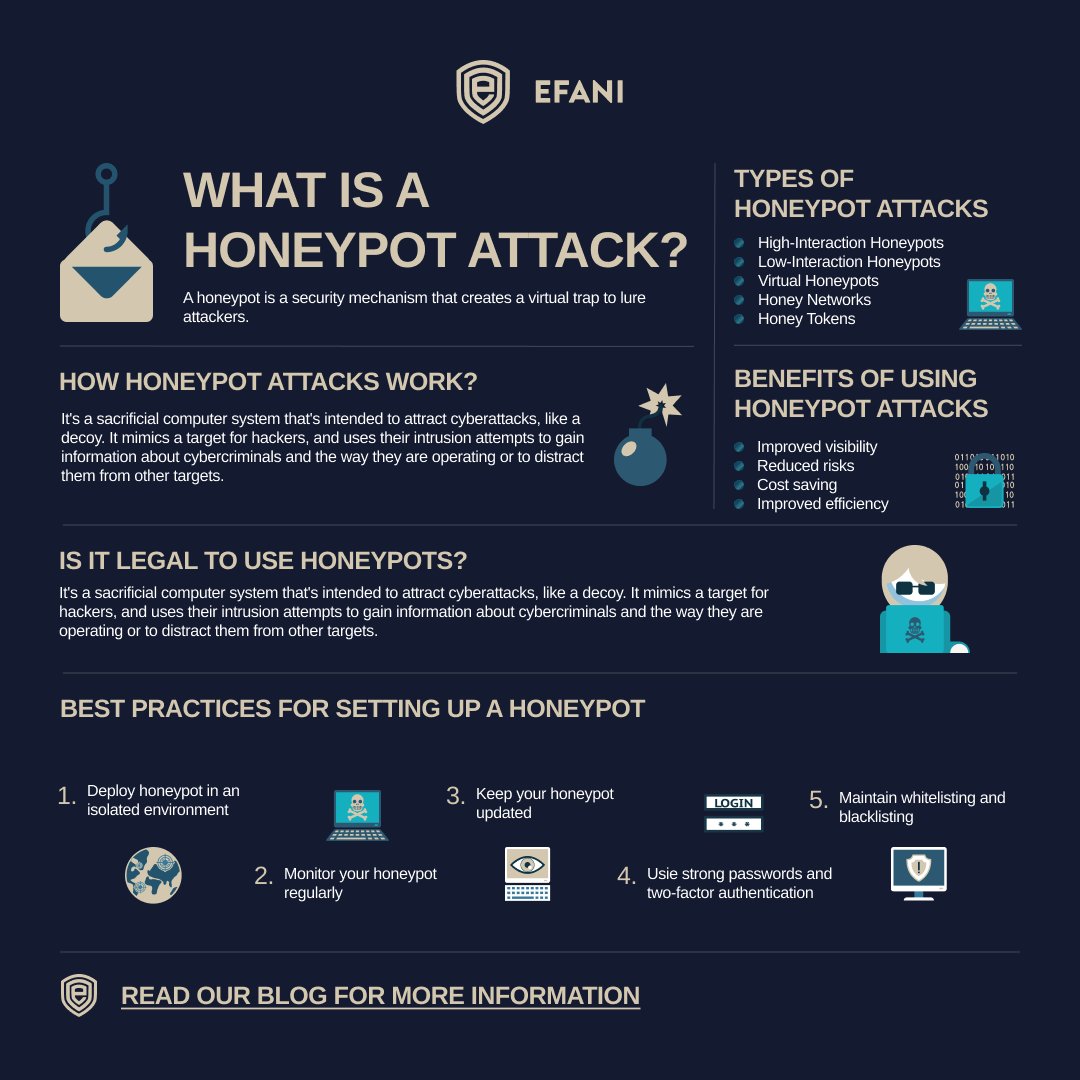
A cyber honeypot is a sacrificial computer system intended to attract cyberattacks. It mimics a target for hackers & uses their intrusion attempts to gain information about cyber criminals & how they operate/distract them from other targets. #computersecurity #honeypot
🔍💻 Tensions are rising, as we navigate the exciting landscape where low-level computer architecture innovations meet the critical challenges of system security Join @_onurmutlu_ at #hw_ioNL2024 👉 Know More: hardwear.io/netherlands-20… #computersecurity #hardware #architecture

CISSP: The Last Mile: Your guide to the finish line by Pete Zerger is the featured book on the Leanpub homepage! #ComputerSecurity #CloudComputing #Cryptography #books #ebooks #CISSP The book covers every topic in the latest CISSP exam syllabus, organized in a format that makes…

JavaScript for hackers: Learn to think like a hacker by Gareth Heyes @garethheyes is the featured book on the Leanpub homepage! #JavaScript #ComputerSecurity #ComputerProgramming #books #ebooks Learn how to find interesting behaviour and flaws in JavaScript. Reading this book…

Tech Tip: Back up your cell phone. lightningstrikestudios.com #ComputerSecurity #InformationTechnology

Tech Tip: Use a password manager. lightningstrikestudios.com #ComputerSecurity #InformationTechnology

This ridiculous pattern is the world's most common password. Even if you aren't from Rome, you should be able to read it... ... if not, just guess it 😒 - - - #computersecurity #password #roman #cybersecurity #day1712

The API Gateway Handbook: Your Practical Guide to API Gateway Setup, Security, and Operation by Thomas Bayer and Tobias Polley @rrayst is the featured book on the Leanpub homepage! #Networking #ComputerSecurity #apis #books #ebooks Whether you’re exposing APIs to partners,…

Something went wrong.
Something went wrong.
United States Trends
- 1. Jets 114K posts
- 2. Sauce 80.8K posts
- 3. Courtois 39.1K posts
- 4. Colts 55K posts
- 5. Breece Hall 10.4K posts
- 6. Garrett Wilson 5,152 posts
- 7. $JFB N/A
- 8. Cheney 231K posts
- 9. Liverpool 211K posts
- 10. Luis Diaz 28.4K posts
- 11. Beane 4,833 posts
- 12. AD Mitchell 6,538 posts
- 13. Bayern 111K posts
- 14. Hakimi 27.8K posts
- 15. Veach 5,436 posts
- 16. Shaheed 16.9K posts
- 17. Brad Holmes 1,162 posts
- 18. Trevor Penning 1,893 posts
- 19. Mazi Smith 5,835 posts
- 20. Jermaine Johnson 3,272 posts