#cybersecurityarchitecture risultati di ricerca
Fortify Your Career This Cybersecurity Awareness Month: Special October Offer on The Cybersecurity Architect's Handbook secdoc.tech/fortify-your-c… #CybersecurityAwarenessMonth #cybersecurityarchitecture #book #sale #packt #discount #cybersecurity
Interested in learning more about Cybersecurity Architecture? Tune in for a webinar with Mr. Marvin Marin from Booz Allen Hamilton on Thursday, October 12, from 6 - 7 p.m. PST. #Cybersec #CybersecurityArchitecture Zoom link: sandiego.zoom.us/j/96748147507 Meeting ID: 967 4814 7507

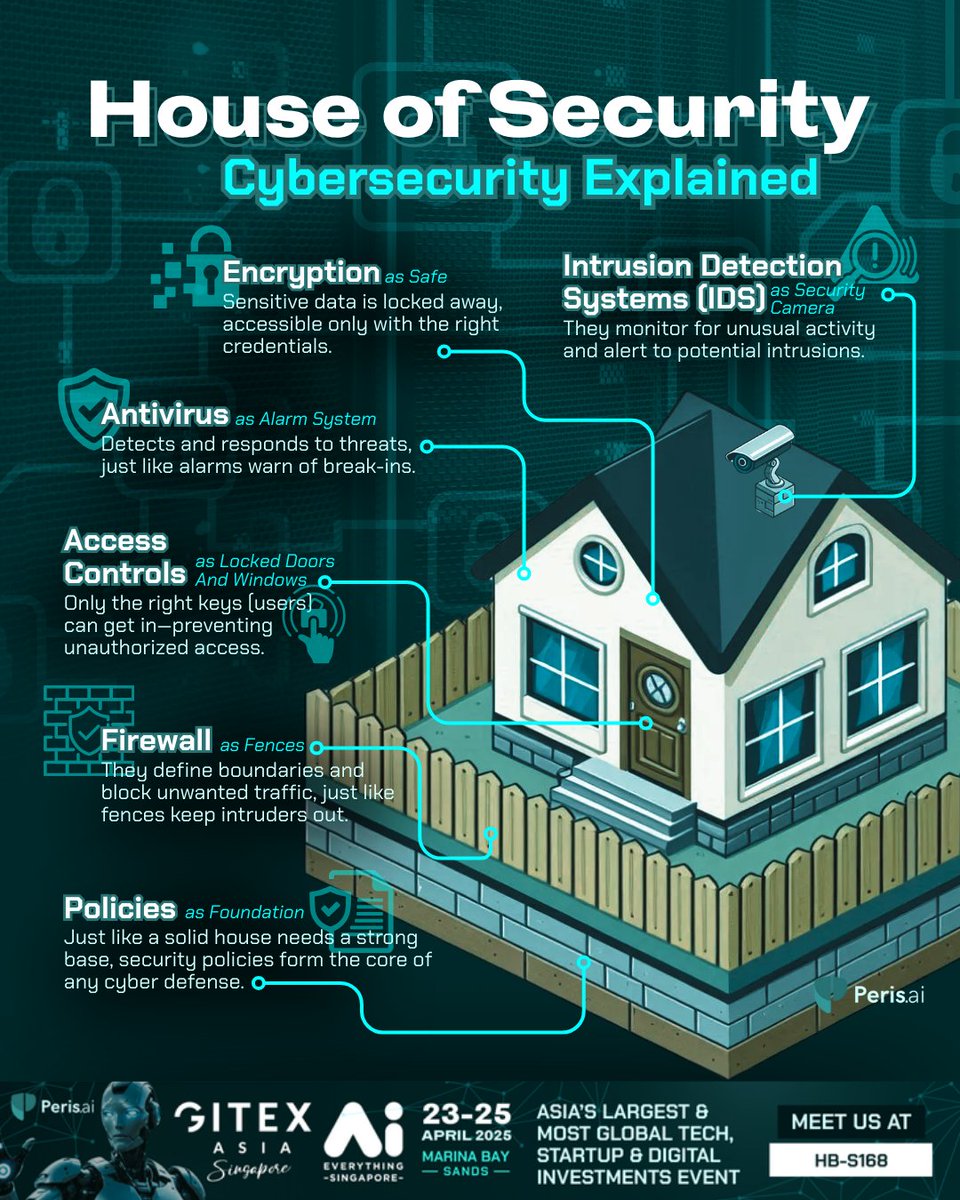
Cybersecurity isn’t just tech—it’s architecture. 🏠 From policy to firewalls, each layer protects your data room by room. 🛡️ #CybersecurityArchitecture #PerisAI #YouBuildWeGuard
On Nov. 25, Tejas Shroff will guide you through the essentials of #CybersecurityArchitecture, from #ZeroTrust principles to #LayeredDefense strategies, and illustrate how to create an agile security framework that adapts to emerging technologies. Register now:…
Join our November 25 #Webinar with Tejas Shroff to explore the critical components of #CybersecurityArchitecture. Explore advanced strategies to protect digital assets across complex environments—including #IoT, #Blockchain, and more. Register now: buff.ly/48DrKCs…
With our #cybersecurity architecture services, we create policies, standards, procedures, and documentation designed to work across all departments and for all applications. If you are in need of #cybersecurityarchitecture contact us for your free quote! 254-458-0014

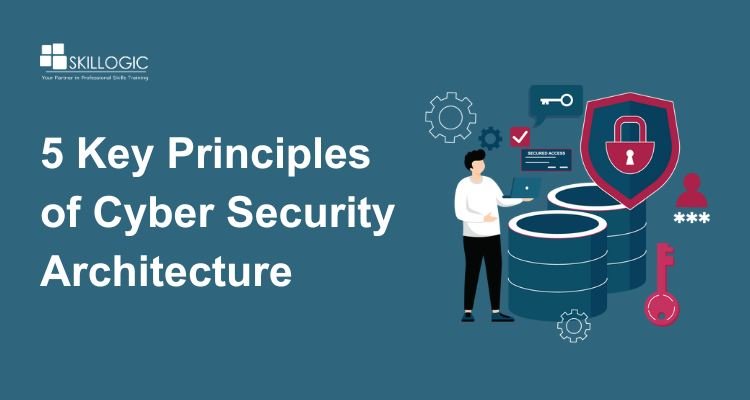
5 Key Principles of Cyber Security Architecture Learn the core principles that strengthen cyber security and protect digital systems skillogic.com/blog/5-key-pri… #CyberSecurityCourse #CyberSecurityArchitecture #SkillogicCyberSecurityCourse #SkillogicInstitute
Companies must have a strong cybersecurity architecture. Let our Certified Freelance Security Architects help you! bit.ly/2SGZ6Lw #Cybersecurity #CybersecurityArchitecture #CertifiedFreelancers #SecurityArchitects #HireNow#RandomActsOfKindnessDay

Also known as information technology (IT) security. Cybersecurity combats threats against networked systems and applications. With the internet, this risk is increased, with the right security strategy, these threats can be prevented. #CyberSecurity #CyberSecurityArchitecture

What is a Security Architecture? Read now: infosectrain.com/blog/what-is-a… #SecurityArchitecture #CybersecurityArchitecture #InformationSecurityArchitecture #ITSecurityArchitecture #CloudSecurityArchitecture #SecurityStrategies #SecurityPrinciples #infosectrain #learntorise
Register now: attendee.gotowebinar.com/register/28366… Join our November 25 #Webinar with Tejas Shroff to explore the critical components of #CybersecurityArchitecture. Explore advanced strategies to protect digital assets across complex environments—including #IoT, #Blockchain, and more.
On Nov. 25, Tejas Shroff will guide you through the essentials of #CybersecurityArchitecture, from #ZeroTrust principles to #LayeredDefense strategies. Register now: attendee.gotowebinar.com/register/28366… #ECCU
Advanced Cybersecurity Experts provides #cybersecurityarchitecture and engineering for your #business. This means every aspect of your #cybersecurity is accounted for, supported, and made #secure. Call us for your cybersecurity needs. 254-458-0014

Register now: attendee.gotowebinar.com/register/28366… We're going live at 7:30 AM CST (8:30 AM EST | 7:00 PM IST)! Today is your chance to explore advanced #CybersecurityArchitecture strategies, including how to future-proof your framework, with Tejas Shroff. #ECCouncilUniversity #Webinar

Register here: attendee.gotowebinar.com/register/28366… Join Tejas Shroff on Nov. 25 for an essential session on #CybersecurityArchitecture, covering #ZeroTrust and #LayeredDefense strategies. Build an agile security framework for emerging tech. #ECCU
Review your current #CybersecurityArchitecture and identify potential areas for improvement to cover your biggest #SecurityRisks as soon as possible. hubs.ly/H0c7JNx0
What is the value of increased automation in the Data Center and NOC? currnt.com/q1801/what-is-… #CybersecurityArchitecture
When preparing your #CybersecurityArchitecture to protect your business with an #IncidentResponsePlan, it’s important to develop strategies for thoroughly investigating a breach and notifying any and all affected parties. hubs.ly/H0fJNbr0
Setting Security Architecture Goals dlvr.it/S02fkB #cybersecurity #cybersecurityarchitecture
A one-size-fits-all approach to network security is outdated and can leave the business vulnerable, so a layered security architecture is recommended. seacom.co.za/business-insig… #CyberSecurityArchitecture #CyberSecurity #SEACOM #SEACOMBusiness #SEACOMSouthAfrica

5 Key Principles of Cyber Security Architecture Learn the core principles that strengthen cyber security and protect digital systems skillogic.com/blog/5-key-pri… #CyberSecurityCourse #CyberSecurityArchitecture #SkillogicCyberSecurityCourse #SkillogicInstitute
Fortify Your Career This Cybersecurity Awareness Month: Special October Offer on The Cybersecurity Architect's Handbook secdoc.tech/fortify-your-c… #CybersecurityAwarenessMonth #cybersecurityarchitecture #book #sale #packt #discount #cybersecurity
OT Security Starts with the Right Cybersecurity Architecture. Read the full blog post: shieldworkz.com/blogs/building… #OTSecurity #cybersecurityarchitecture #ICSsecurity #industrialcybersecurity #shieldworkz #CriticalInfrastructure #CISO #SCADA #CyberSecurity #secureindustrialsystems

426 Days and Counting: How "The Cybersecurity Architect's Handbook" Continues to Lead Amazon's Security Categories secdoc.tech/426-days-and-c… #packt #cybersecurityarchitecture #cybersecurity #book
Cybersecurity isn’t just tech—it’s architecture. 🏠 From policy to firewalls, each layer protects your data room by room. 🛡️ #CybersecurityArchitecture #PerisAI #YouBuildWeGuard

Secure your organization with an effective cybersecurity architecture. Learn how to integrate defenses against modern cyber threats and ensure business success. medium.com/@lenaztyson/th… #CyberSecurity #CyberSecurityArchitecture #RiskManagement #BusinessSecurity #DataProtection
medium.com
The Game-Changing Role of Cybersecurity Architecture in Safeguarding Your Business
Businesses rely significantly on digital infrastructures for daily operations, innovation, and expansion in this hyperconnected world…
Register now: attendee.gotowebinar.com/register/28366… We're going live at 7:30 AM CST (8:30 AM EST | 7:00 PM IST)! Today is your chance to explore advanced #CybersecurityArchitecture strategies, including how to future-proof your framework, with Tejas Shroff. #ECCouncilUniversity #Webinar

Register here: attendee.gotowebinar.com/register/28366… Join Tejas Shroff on Nov. 25 for an essential session on #CybersecurityArchitecture, covering #ZeroTrust and #LayeredDefense strategies. Build an agile security framework for emerging tech. #ECCU

On Nov. 25, Tejas Shroff will guide you through the essentials of #CybersecurityArchitecture, from #ZeroTrust principles to #LayeredDefense strategies, and illustrate how to create an agile security framework that adapts to emerging technologies. Register now:…

On Nov. 25, Tejas Shroff will guide you through the essentials of #CybersecurityArchitecture, from #ZeroTrust principles to #LayeredDefense strategies. Register now: attendee.gotowebinar.com/register/28366… #ECCU

Register now: attendee.gotowebinar.com/register/28366… Join our November 25 #Webinar with Tejas Shroff to explore the critical components of #CybersecurityArchitecture. Explore advanced strategies to protect digital assets across complex environments—including #IoT, #Blockchain, and more.

Join our November 25 #Webinar with Tejas Shroff to explore the critical components of #CybersecurityArchitecture. Explore advanced strategies to protect digital assets across complex environments—including #IoT, #Blockchain, and more. Register now: buff.ly/48DrKCs…

What is a Security Architecture? Read now: infosectrain.com/blog/what-is-a… #SecurityArchitecture #CybersecurityArchitecture #InformationSecurityArchitecture #ITSecurityArchitecture #CloudSecurityArchitecture #SecurityStrategies #SecurityPrinciples #infosectrain #learntorise

Interested in learning more about Cybersecurity Architecture? Tune in for a webinar with Mr. Marvin Marin from Booz Allen Hamilton on Thursday, October 12, from 6 - 7 p.m. PST. #Cybersec #CybersecurityArchitecture Zoom link: sandiego.zoom.us/j/96748147507 Meeting ID: 967 4814 7507

A one-size-fits-all approach to network security is outdated and can leave the business vulnerable, so a layered security architecture is recommended. seacom.co.za/business-insig… #CyberSecurityArchitecture #CyberSecurity #SEACOM #SEACOMBusiness #SEACOMSouthAfrica

What is Security Architecture A Full Guide? Read More:- buff.ly/3vhn9ns #securityarchitecture #cybersecurityarchitecture #securityarchitectureframework #TheNextTrends
#cybersecurityarchitecture #CyberSecurity #NetworkSecurityArchitecture #NetworkArchitecture #teamDeliveryCentric #WeLoveTechnology #QualityOutcomes #OnTimeDelivery #OnBudgetDelivery #MakingCustomersHappy

Join our November 25 #Webinar with Tejas Shroff to explore the critical components of #CybersecurityArchitecture. Explore advanced strategies to protect digital assets across complex environments—including #IoT, #Blockchain, and more. Register now: buff.ly/48DrKCs…

Interested in learning more about Cybersecurity Architecture? Tune in for a webinar with Mr. Marvin Marin from Booz Allen Hamilton on Thursday, October 12, from 6 - 7 p.m. PST. #Cybersec #CybersecurityArchitecture Zoom link: sandiego.zoom.us/j/96748147507 Meeting ID: 967 4814 7507

On Nov. 25, Tejas Shroff will guide you through the essentials of #CybersecurityArchitecture, from #ZeroTrust principles to #LayeredDefense strategies, and illustrate how to create an agile security framework that adapts to emerging technologies. Register now:…

What is a Security Architecture? Read now: infosectrain.com/blog/what-is-a… #SecurityArchitecture #CybersecurityArchitecture #InformationSecurityArchitecture #ITSecurityArchitecture #CloudSecurityArchitecture #SecurityStrategies #SecurityPrinciples #infosectrain #learntorise

Cybersecurity isn’t just tech—it’s architecture. 🏠 From policy to firewalls, each layer protects your data room by room. 🛡️ #CybersecurityArchitecture #PerisAI #YouBuildWeGuard

Register now: attendee.gotowebinar.com/register/28366… Join our November 25 #Webinar with Tejas Shroff to explore the critical components of #CybersecurityArchitecture. Explore advanced strategies to protect digital assets across complex environments—including #IoT, #Blockchain, and more.

Companies must have a strong cybersecurity architecture. Let our Certified Freelance Security Architects help you! bit.ly/2SGZ6Lw #Cybersecurity #CybersecurityArchitecture #CertifiedFreelancers #SecurityArchitects #HireNow#RandomActsOfKindnessDay

Also known as information technology (IT) security. Cybersecurity combats threats against networked systems and applications. With the internet, this risk is increased, with the right security strategy, these threats can be prevented. #CyberSecurity #CyberSecurityArchitecture

With our #cybersecurity architecture services, we create policies, standards, procedures, and documentation designed to work across all departments and for all applications. If you are in need of #cybersecurityarchitecture contact us for your free quote! 254-458-0014

On Nov. 25, Tejas Shroff will guide you through the essentials of #CybersecurityArchitecture, from #ZeroTrust principles to #LayeredDefense strategies. Register now: attendee.gotowebinar.com/register/28366… #ECCU

Register here: attendee.gotowebinar.com/register/28366… Join Tejas Shroff on Nov. 25 for an essential session on #CybersecurityArchitecture, covering #ZeroTrust and #LayeredDefense strategies. Build an agile security framework for emerging tech. #ECCU

Register now: attendee.gotowebinar.com/register/28366… We're going live at 7:30 AM CST (8:30 AM EST | 7:00 PM IST)! Today is your chance to explore advanced #CybersecurityArchitecture strategies, including how to future-proof your framework, with Tejas Shroff. #ECCouncilUniversity #Webinar

Advanced Cybersecurity Experts provides #cybersecurityarchitecture and engineering for your #business. This means every aspect of your #cybersecurity is accounted for, supported, and made #secure. Call us for your cybersecurity needs. 254-458-0014

A one-size-fits-all approach to network security is outdated and can leave the business vulnerable, so a layered security architecture is recommended. seacom.co.za/business-insig… #CyberSecurityArchitecture #CyberSecurity #SEACOM #SEACOMBusiness #SEACOMSouthAfrica

OT Security Starts with the Right Cybersecurity Architecture. Read the full blog post: shieldworkz.com/blogs/building… #OTSecurity #cybersecurityarchitecture #ICSsecurity #industrialcybersecurity #shieldworkz #CriticalInfrastructure #CISO #SCADA #CyberSecurity #secureindustrialsystems

Something went wrong.
Something went wrong.
United States Trends
- 1. #HardRockBet 2,882 posts
- 2. #IDontWantToOverreactBUT 3,213 posts
- 3. SNAP 643K posts
- 4. Jamaica 86.2K posts
- 5. #MondayMotivation 39.2K posts
- 6. Victory Monday 3,651 posts
- 7. $QCOM 15.2K posts
- 8. Good Monday 54K posts
- 9. MRIs 2,059 posts
- 10. jungkook 358K posts
- 11. #MondayVibes 3,892 posts
- 12. #P1SD N/A
- 13. Sports Equinox 2,795 posts
- 14. WINWIN 26.3K posts
- 15. Hurricane Melissa 50.7K posts
- 16. Aroldis Chapman N/A
- 17. Walter Reed 5,754 posts
- 18. Milei 718K posts
- 19. Jack DeJohnette 2,271 posts
- 20. Master Chief 6,865 posts