#detectionascode 搜索结果
Back with a new blog post! #DetectionEngineering: Practicing #DetectionAsCode – Tuning - Part 8 👉 blog.nviso.eu/2025/11/25/det… If you missed the rest of the parts you can find them here: blog.nviso.eu/tag/detection-…
Wondering how to make your #DetectionSystems more responsive during infrastructure changes? Read the latest blog post by @kristo_b & @_st0pp3r_ on #DetectionEngineering 👉blog.nviso.eu/2025/11/25/det…
What is Detection as Code? Detection as Code (DaC) is a modern cybersecurity practice that treats threat detection logic in the same way as software development. Read here - infosectrain.blogspot.com/2025/11/what-i… #DetectionAsCode #DaC #cybersecurity #infosectrain
Wondering if your detections work as designed? Olaf Hartong outlines a robust development and deployment process using cloud tech and shows you how to code your way to detection confidence. #ATTACKcon4 #DetectionAsCode

great Friday feeling when all your detections finally pass automated CI/CD testing cc @M_haggis #detectionAsCode

Detection-as-Code: From Concept to Practice 👇 Check out @_st0pp3r_ latest blog series, where he unpacks the fundamentals of #DetectionEngineering and takes a closer look at the game-changing concept of #DetectionAsCode. blog.nviso.eu/2025/07/08/det…
#Cybersecurity is on the move! 🚀 Amine Besson chats #detectionascode, response engineering, and the future of fusion centers on this episode of the @CloudSecPodcast. Listen now → bit.ly/4gJSK6i

Check out our latest post on #DetectionEngineering: Practicing #DetectionAsCode
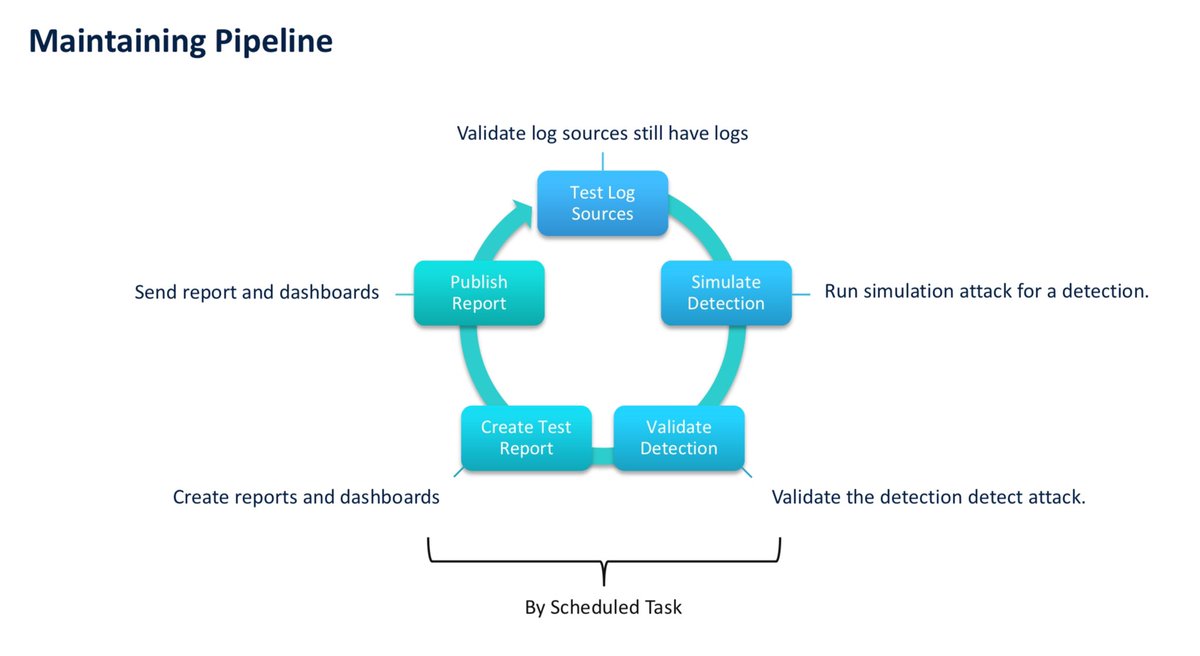
@_st0pp3r_ and @CyberCatz0r latest blog post is your guide to transforming #DetectionEngineering maintenance through automation. Read part 7 of the series now 👉 blog.nviso.eu/2025/10/07/det…

I guess all DE teams are validating their new detections. What about prior detections? Building a pipeline may be good idea for be able to sleep well. #detectionengineering #detectionascode #siem
🚒 Too much firefighting, not enough foresight? #DetectionAsCode (DaC) to the rescue! 🧯 Join the 63% of pros who see fewer incidents. Learn how in our State of Security 2025 report: 🔗[splk.it/4kfjY6I] #SplunkSecurity
Let's kick off this Tuesday with @_st0pp3r_ new blog series on the critical role of versioning in #DetectionEngineering, particularly within #DetectionAsCode. 👉blog.nviso.eu/2025/09/09/det… You'll learn to implement robust versioning strategies for better traceability and more!

The best SOCs don’t chase every alert. They focus on the right ones. Detection-as-Code enables teams to refine detections, automate tuning, and adapt in real-time. Better alerts = faster triage, smarter decisions, and stronger security. #CyberSecurity #SOC #DetectionAsCode

🚀 Boost Your Security Skills! 🚀 Join our webinar to learn the fundamentals of Detection-as-Code and manage detection rules with Google SecOps’ REST API and CI/CD tools. Live Q&A included! 📅 Register now: bit.ly/4ax3Gka #GoogleSecOps #DetectionAsCode #Webinar

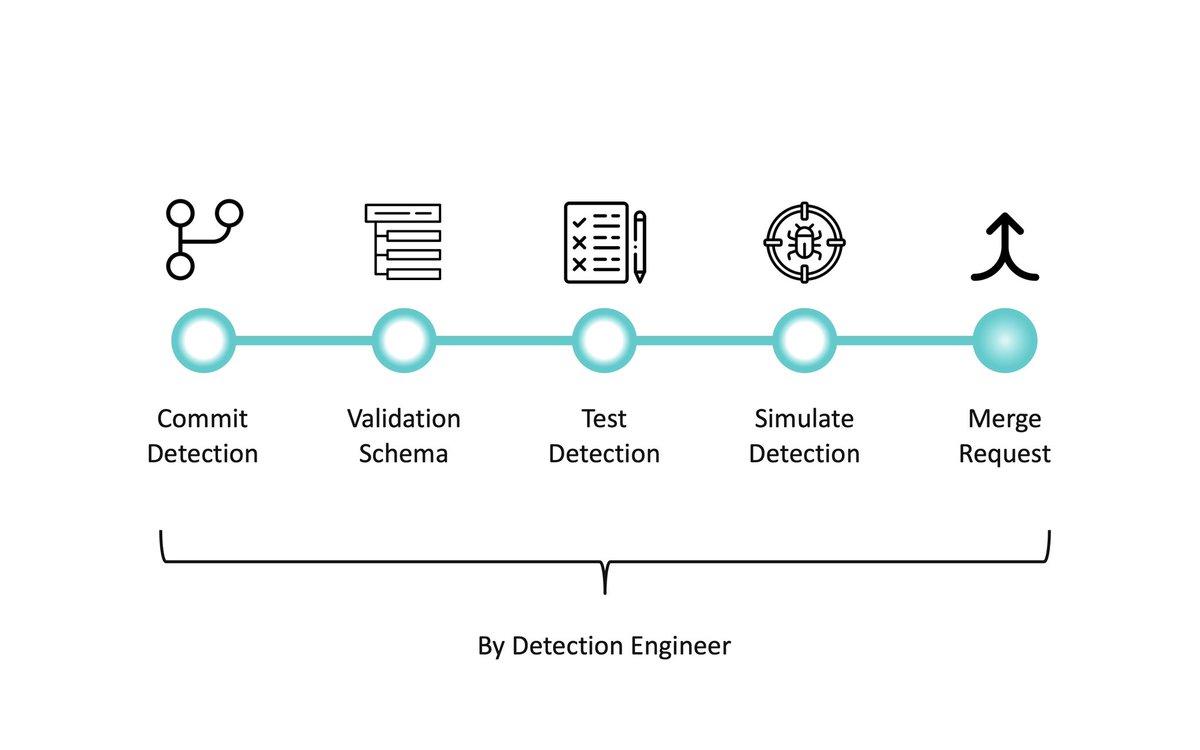
Check out my latest blog post of the series #DetectionEngineering: Practicing #DetectionAsCode for @NVISO_Labs. In this part we are exploring Continuous Delivery pipelines to deploy our detections to the target platform.
This is the follow-up you've been waiting for: The #DetectionEngineering Blog Post Part 6 by @_st0pp3r_ blog.nviso.eu/2025/09/23/det… You'll gain insights on manual, release-based, automatic and multitenant deployments to optimize #ContinuousDeployment processes and more.

Panther raises $120 million at $1.4 billion valuation! 👏 Our Series B will power accelerated growth with cloud-first security teams to make detection and response fast, flexible and scalable. Learn more⬇️ runpanther.io/press-releases… #DetectionasCode

Discover insights from David French on detection as code in the latest episode of Simply Defensive. Explore his journey, professional growth, and the vital role of coding in cybersecurity. 💻🔍 #DetectionAsCode #TechUSA #CyberInsights link: ift.tt/gok7uWA

Proactive Cybersecurity – Staying Ahead of Threats with a Preventive Approach bit.ly/45FnPVT #DetectionAsCode #ThreatDetection #CyberAutomation #SecurityOperations #IntelligentSecurity #CyberDefense #TechUnity

Why Detection-As-Code (DAC) Is the Future of #ThreatDetection buff.ly/3iUUoXG #detectionascode #DAC #cybersecurity

🚀 Get ready, Toronto! Just one more week ‘til #AWSSummitToronto! Come chat with us at booth #425 and we’ll show you exactly why Panther is the SIEM for code-driven SecOps at cloud scale. #DetectionAsCode #SecurityEngineering #DetectionEngineering

🚨Today’s the day, Toronto!! Visit at booth #425 to talk about code-driven SecOps at cloud scale. Snag a 🎶 Views from the SOC 🎶 #Detectapalooza shirt by being the first 5 to schedule a sales call. #AWSSummitToronto #DetectionAsCode #SecurityEngineering #DetectionEngineering

Mom life: 14 Goldfish requests, 1 WISEcode scan, and suddenly you’re a food detective. No more guessing what’s in your pantry. Just real transparency for real families. Scan. Know. Empower. #FoodTransparency #WISEcode
Your stack isn’t perfect—but detection engineering shows you where it’s slipping. Our #guide explains how modern teams stay ahead of misconfigs, silent failures, and constant change. 👉 Read the #DetectionEngineering Guide: hubs.ly/Q03WQ-bZ0
In the session "Through the Pipeline: Scaling Detection Engineering with Detection-as-Code" at #BlackHatMEA, Sr. Detection Engineer Abdulmalik Banaser of Cipher discussed the biggest challenge in Detection Engineering: the need for process, not content.

We do trials to track active codes, then it gets matched with our ML "Datas are real time"
You can use #AI to spot code anti-patterns the same way a lint tool catches smells — but smarter. Feed it diffs, patterns, repos, and it surfaces drift, hidden complexity, dead logic, security gaps, and style violations you’d miss at 2am. It’s code review with x-ray vision.
Liu et al. introduce a multimodal vulnerability detector that fuses features from both source and binary code using an attention-based strategy. It was evaluated across three datasets in C, C++, and Java, achieving improved performance over 7 baselines. authors.elsevier.com/a/1mABjc7X5EoKb
This is a RUNTIME threat, not just a deserialization issue. The suspicious code doesn't execute when you load the model - it triggers when you actually USE the model for inference. This makes it harder to detect in security scans. ⚠️
Data are not very accurate. Detector AI very often flags article written by human as "AI coded". That's why e.g. universities don't use it at all. So don't take these data too seriously. There is currently no program that would be 100 % accurate.
wrote my own detection engine because i didn't wanna pay $200k for one (golang + py) github.com/bilals12/iota
Detection with bad detectors is not viable. But at least so far, AI detection is very viable. We have the receipts:

I don't think the general public is going to accept that "ai detection" isn't really viable
#tools #Sec_code_review "InfCode: Adversarial Iterative Refinement of Tests and Patches for Reliable Software Issue Resolution", Nov. 2025. ]-> github.com/Tokfinity/InfC… // InfCode is an adversarial multi-agent Code Agent System which uses LLMs to automatically analyze and fix…
You said exactly what most people pretend not to see. Detection doesn’t work and won’t work, and that changes the entire evaluation logic. I’d just add one thing, because it strengthens your point, serious labs already warn that these detectors aren’t proof and must be used with…
At some point you niggas need to learn that these "detectors" don't "detect" anything, they merely run with a set of prejudged statements. There's no such thing as the ability to detect if a computer program put words into a sentence cuz every word and every sentence is man-made.
⚠️ New SOC Alert: Security Software Discovery Detected Attackers use Security Software Discovery to detect antivirus, firewalls, or other defenses on a system. This lets them evade detection, disable tools, or tailor attacks for success. 👥 Role: Incident Responder 🛠️ Type:…

We've showed that as early as in 2023. So-called detectors are extremely prone to false positive when facing essays or texts written in a pedagogical style. We even released an adversarial dataset if you want to try it out on those "detectors" aclanthology.org/2023.jeptalnre…
Kinda. You don't see code perse. It's more like scanning for keywords and numerical statistical anomalies.
great Friday feeling when all your detections finally pass automated CI/CD testing cc @M_haggis #detectionAsCode

Wondering if your detections work as designed? Olaf Hartong outlines a robust development and deployment process using cloud tech and shows you how to code your way to detection confidence. #ATTACKcon4 #DetectionAsCode

#Cybersecurity is on the move! 🚀 Amine Besson chats #detectionascode, response engineering, and the future of fusion centers on this episode of the @CloudSecPodcast. Listen now → bit.ly/4gJSK6i

🚀 Boost Your Security Skills! 🚀 Join our webinar to learn the fundamentals of Detection-as-Code and manage detection rules with Google SecOps’ REST API and CI/CD tools. Live Q&A included! 📅 Register now: bit.ly/4ax3Gka #GoogleSecOps #DetectionAsCode #Webinar

Detection-as-Code: From Concept to Practice 👇 Check out @_st0pp3r_ latest blog series, where he unpacks the fundamentals of #DetectionEngineering and takes a closer look at the game-changing concept of #DetectionAsCode. blog.nviso.eu/2025/07/08/det…

Is “Detection as Code” the next logical step for security operations? @anton_chuvakin explores the implications for improving SOC efficiency. What do you think? Read More: tinyurl.com/3w5yp6vp #DetectionAsCode #SecurityOperations

🚀 Get ready, Toronto! Just one more week ‘til #AWSSummitToronto! Come chat with us at booth #425 and we’ll show you exactly why Panther is the SIEM for code-driven SecOps at cloud scale. #DetectionAsCode #SecurityEngineering #DetectionEngineering

🚨Today’s the day, Toronto!! Visit at booth #425 to talk about code-driven SecOps at cloud scale. Snag a 🎶 Views from the SOC 🎶 #Detectapalooza shirt by being the first 5 to schedule a sales call. #AWSSummitToronto #DetectionAsCode #SecurityEngineering #DetectionEngineering

Let's kick off this Tuesday with @_st0pp3r_ new blog series on the critical role of versioning in #DetectionEngineering, particularly within #DetectionAsCode. 👉blog.nviso.eu/2025/09/09/det… You'll learn to implement robust versioning strategies for better traceability and more!

How’s the view from your SOC, Toronto?? 👀 Visit booth #425 to talk cloud SecOps at #AWSSummitToronto. We’re giving away the finest #Detectapalooza swag to a few lucky 🍀 folks who sign up for a chat with our sales team. #DetectionAsCode #SecurityEngineering…

I guess all DE teams are validating their new detections. What about prior detections? Building a pipeline may be good idea for be able to sleep well. #detectionengineering #detectionascode #siem

Panther raises $120 million at $1.4 billion valuation! 👏 Our Series B will power accelerated growth with cloud-first security teams to make detection and response fast, flexible and scalable. Learn more⬇️ runpanther.io/press-releases… #DetectionasCode

Proactive Cybersecurity – Staying Ahead of Threats with a Preventive Approach bit.ly/45FnPVT #DetectionAsCode #ThreatDetection #CyberAutomation #SecurityOperations #IntelligentSecurity #CyberDefense #TechUnity

Detection as code: Revolutionizing security operations through automated, intelligent threat detection bit.ly/3Sl0fGB #DetectionAsCode #Cybersecurity #ThreatDetection #DevSecOps #AutomatedSecurity #CyberDefense #CloudSecurity #CyberThreats #AttackSolutions

The best SOCs don’t chase every alert. They focus on the right ones. Detection-as-Code enables teams to refine detections, automate tuning, and adapt in real-time. Better alerts = faster triage, smarter decisions, and stronger security. #CyberSecurity #SOC #DetectionAsCode

Detection as code: Revolutionizing security operations through automated, intelligent threat detection bit.ly/4fxywgv #DetectionAsCode #ThreatDetection #CyberAutomation #SecurityOperations #IntelligentSecurity #CyberDefense #TechUnity

Why Detection-As-Code (DAC) Is the Future of #ThreatDetection buff.ly/3iUUoXG #detectionascode #DAC #cybersecurity

Rely on Threat Detection Marketplace to create your custom repositories for #detectionascode projects smartly linked to ATT&CK. Store and manage your #detection code in a secure environment to boost the use case management lifecycle. Learn more: my.socprime.com/threat-detecti…

.@SnowflakeDB Ventures Invests in @runpanther_ to Add #DetectionAsCode to the #DataCloud buff.ly/3xTmqbD #CyberSecurity #TheDataCloud

Something went wrong.
Something went wrong.
United States Trends
- 1. Comet 27.6K posts
- 2. Oviedo 5,270 posts
- 3. Matt Campbell 1,846 posts
- 4. Fame 56.9K posts
- 5. Amon Ra 1,206 posts
- 6. TPUSA 88.7K posts
- 7. The Password 3,553 posts
- 8. #MissVenezuela2025 1,604 posts
- 9. Letitia James 17.2K posts
- 10. Supreme Court 48.4K posts
- 11. SCOTUS 15K posts
- 12. Teslaa 2,147 posts
- 13. Amorim 55.7K posts
- 14. fnaf 2 18K posts
- 15. Jarry N/A
- 16. ARSB N/A
- 17. Spaghetti 11.2K posts
- 18. #TakoTori1stConcert 1,013 posts
- 19. #LightningStrikes N/A
- 20. Jordan Walsh N/A