#exposurevalidation wyniki wyszukiwania
CVE overload is real — 50k disclosures in 2025, most flagged critical. In @SecInfoWatch, @su13ym4n discusses why exposure validation matters: proving which vulns are exploitable in practice, not just on paper. 📖 Read: hubs.li/Q03L8g_v0 #CyberSecurity #ExposureValidation

✨ That’s a wrap on #PresidioTechXperience 2025! Great discussions, great people, and a great opportunity to share how AEV helps orgs validate defenses with proof. Thanks @Presidio for hosting us + everyone who visited our booth! #CyberSecurity #ExposureValidation


Not sure if your remediation works? Uni5 Xposure lets you simulate real attacks to validate controls and patches. It even revalidates and adjusts risk scores. #CyberSecurity #ExposureValidation

Why wait for a breach to find out where you're vulnerable? Uni5 Xposure mimics real-world threats to identify gaps in your defenses, ensuring you’re always one step ahead. #adversarialexposurevalidation #exposurevalidation
Unsure if your remediation efforts are working? Our exposure validation technology built into Uni5 Xposure simulates real attacks to prove your controls and patches hold up. Our platform even revalidates patches and adjusts your risk scores accordingly. #ExposureValidation

Not every “critical” CVE is critical for you. At GovWare 2025, discover how Picus pinpoints exploitable risks and cuts the rest from your backlog. 👉 Learn more: hubs.li/Q03NfCsQ0 #GovWare2025 #CyberSecurity #ExposureValidation #AEV
Pen tests and red teaming are useful, but they’re not enough. Learn how IONIX redefines security validation with continuous, non-intrusive exposure testing across your external attack surface: hubs.ly/Q03Sk8yx0 #exposurevalidation #cybersecurity

An incredible day at the Porsche Experience Center in Atlanta! Great conversations, thrilling driving experiences, and valuable cybersecurity and exposure validation insights. 🚗💨 Thanks to everyone who joined us! Until next time! #CyberSecurity #ExposureValidation…



Not all exposures are equal–and if you don’t know which are exploitable, you’re in the dark. Watch how SafeBreach delivers: + Real-time control insight + True attack surface visibility + Data-backed breach impact hubs.ly/Q03sgsb-0 #ExposureValidation




From scanners to pentests to EASM — security pros juggle more tools than ever. Our latest blog breaks down 3 key approaches: 🔍 Manual Pentesting 🤖 Automated Pentesting ✅ Exposure Validation 📖 ultrared.ai/blog/exposure-… #CTEM #CyberSecurity #ExposureValidation #Cyber

📲Watch our expert-led webinar on Adversarial Exposure Validation (AEV) on demand! 💡 Learn how to identify real attack paths, automate threat validation, and strengthen defenses with real-world insights. 🔗 bit.ly/4icEJyq #CTEM #ExposureValidation #Cybersecurity
Open source ≠ operational scale. Adversarial Exposure Validation starts with open source, but real results come with purpose-built platforms. 📥 Download the 2025 Gartner® Market Guide: hubs.li/Q03q4DYc0 #CyberSecurity #ExposureValidation

Great coverage from @DarkReading on our recent launch! Picus Exposure Validation lets security teams prioritize vulnerabilities based on real-world exploitability—not just theoretical risk. Full details here 👇 hubs.li/Q03v6VTd0 #CyberSecurity #ExposureValidation…

That's a wrap on two fantastic days at #Cyber100Club during #InfosecurityEurope2025! Thanks to everyone who connected with our team, Ciaran and Nathan, to discuss #ExposureValidation and cybersecurity. Until next time! #PicusSecurity



Live at Black Hat: Watchtower is here. Our new AI-powered CTI analyzer maps global intel to the threats targeting you and then auto-tests your defenses with AEV. 📍See it live at our booth 👉 attackiq.com/2025/08/05/att… #CTEM #ThreatIntelligence #ExposureValidation #BlackHat2025
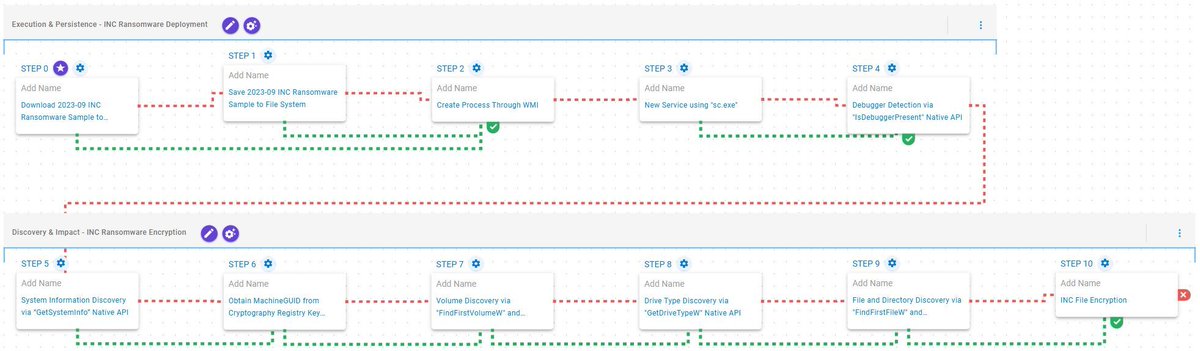
Ransom Tales: Volume III 🎭 INC, Lynx, and SafePay ransomware are evolving fast. See how their TTPs are emulated so defenders can test and validate. 👉 attackiq.com/2025/08/28/ran… #Ransomware #AdversaryResearch #ExposureValidation



Our Checklist for Exposure Validation Solutions in CTEM just got interactive! Quickly prioritize validated threats, streamline your security management, and ensure you're focused on risks that truly matter. Explore now → hubs.li/Q03psb-H0 #CTEM #ExposureValidation…

You know BAS. But you should be focusing on AEV. Gartner predicts 40% of orgs will adopt Adversarial Exposure Validation by 2027. Will you be one? 👉 See why it’s crucial to start now: attackiq.com/lp/gartner-aev… #CyberSecurity #AEV #ExposureValidation

Most security teams are stuck in a cycle of alerts & uncertainty. Ready3 operationalizes CTEM to uncover real risks, automate validation, & prioritize tests based on attack paths. 🔗 Watch Now: attackiq.com/webinars/on-de… #CyberSecurity #ExposureValidation #Ready3 #AEV

That's a wrap at the @IDC Security Roadshow & CISO Excellence Awards in Doha! Thanks to our team for representing Picus Security and highlighting how Exposure Validation transforms BAS to enhance cybersecurity. See you again soon! #CyberSecurity #ExposureValidation #Qatar…




Pen tests and red teaming are useful, but they’re not enough. Learn how IONIX redefines security validation with continuous, non-intrusive exposure testing across your external attack surface: hubs.ly/Q03Sk8yx0 #exposurevalidation #cybersecurity

The Picus team is ready for GovWare 2025! 📍 Booth V03 | Sands Expo, Singapore 📅 21–23 October Join us to see how AEV validates defenses and helps you focus on real risk. 👉 hubs.li/Q03Nh-lD0 #GovWare2025 #CyberSecurity #ExposureValidation #AEV

Not every “critical” CVE is critical for you. At GovWare 2025, discover how Picus pinpoints exploitable risks and cuts the rest from your backlog. 👉 Learn more: hubs.li/Q03NfCsQ0 #GovWare2025 #CyberSecurity #ExposureValidation #AEV

CVE overload is real — 50k disclosures in 2025, most flagged critical. In @SecInfoWatch, @su13ym4n discusses why exposure validation matters: proving which vulns are exploitable in practice, not just on paper. 📖 Read: hubs.li/Q03L8g_v0 #CyberSecurity #ExposureValidation

Read the final chapter of our series and see how to move from theory to evidence-based resilience: hubs.li/Q03JLPWp0 #ExposureValidation #BAS #PenTesting
✨ That’s a wrap on #PresidioTechXperience 2025! Great discussions, great people, and a great opportunity to share how AEV helps orgs validate defenses with proof. Thanks @Presidio for hosting us + everyone who visited our booth! #CyberSecurity #ExposureValidation


Meet Nelson Santos, Solution Architect, at Fal.Con 2025 Booth #2010. Book your 1:1 meeting now to discuss validating controls and real-world exposure: 👉 hubs.li/Q03G9HQS0 #FalCon2025 #ExposureValidation #CyberSecurity

Detection engineering is only proven through evidence. This blog discusses hhow BAS validates detection rules and how Automated Pentesting stress-tests full attack paths to measure blue team readiness. 👉 Read the full blog: hubs.li/Q03G7B7k0 #ExposureValidation…
picussecurity.com
BAS vs Automated Pentesting: Validating Detection and Blue Team Readiness
Find out how BAS and Automated Pentesting validate detection engineering and blue team readiness, ensuring organizations can detect, investigate, and respond to real-world attacks efficiently.
Ransom Tales: Volume III 🎭 INC, Lynx, and SafePay ransomware are evolving fast. See how their TTPs are emulated so defenders can test and validate. 👉 attackiq.com/2025/08/28/ran… #Ransomware #AdversaryResearch #ExposureValidation




Ransomware broke through at Data I/O 🚨 Business stopped cold. You cannot assume defenses work—you have to prove it. 🔒 Full story 👉 infosecurity-magazine.com/news/tech-manu… @InfosecurityMag #ExposureValidation #AEV #Cybersecurity
Compliance requires proof, not promises. BAS and Automated Pentesting provide evidence-based metrics showing controls work in the real world. Demonstrate proactive security and strengthen trust → hubs.li/Q03D3n1x0 #Compliance #CyberSecurity #ExposureValidation
Live at Black Hat: Watchtower is here. Our new AI-powered CTI analyzer maps global intel to the threats targeting you and then auto-tests your defenses with AEV. 📍See it live at our booth 👉 attackiq.com/2025/08/05/att… #CTEM #ThreatIntelligence #ExposureValidation #BlackHat2025
You know BAS. But you should be focusing on AEV. Gartner predicts 40% of orgs will adopt Adversarial Exposure Validation by 2027. Will you be one? 👉 See why it’s crucial to start now: attackiq.com/lp/gartner-aev… #CyberSecurity #AEV #ExposureValidation

Most “critical” CVEs aren't really exploitable in your environment. Watch our on-demand webinar to see how Exposure Validation reveals what’s truly dangerous—so your team can focus on real risks. Watch now: hubs.li/Q03xPw-P0 #Cybersecurity #ExposureValidation…
From scanners to pentests to EASM — security pros juggle more tools than ever. Our latest blog breaks down 3 key approaches: 🔍 Manual Pentesting 🤖 Automated Pentesting ✅ Exposure Validation 📖 ultrared.ai/blog/exposure-… #CTEM #CyberSecurity #ExposureValidation #Cyber

Pen tests and red teaming are useful, but they’re not enough. Learn how IONIX redefines security validation with continuous, non-intrusive exposure testing across your external attack surface: hubs.ly/Q03wpRN60 #exposurevalidation #cybersecurity

Most security teams are stuck in a cycle of alerts & uncertainty. Ready3 operationalizes CTEM to uncover real risks, automate validation, & prioritize tests based on attack paths. 🔗 Watch Now: attackiq.com/webinars/on-de… #CyberSecurity #ExposureValidation #Ready3 #AEV

Great coverage from @DarkReading on our recent launch! Picus Exposure Validation lets security teams prioritize vulnerabilities based on real-world exploitability—not just theoretical risk. Full details here 👇 hubs.li/Q03v6VTd0 #CyberSecurity #ExposureValidation…

An incredible day at the Porsche Experience Center in Atlanta! Great conversations, thrilling driving experiences, and valuable cybersecurity and exposure validation insights. 🚗💨 Thanks to everyone who joined us! Until next time! #CyberSecurity #ExposureValidation…



Breach and Attack Simulation or Automated Pentesting? The answer isn’t either/or — it’s both. Understand the roles. Combine their strengths. 👉 Download the guide: hubs.li/Q03s6KGp0 #CyberSecurity #ExposureValidation #BAS #APT #CTEM

CVE overload is real — 50k disclosures in 2025, most flagged critical. In @SecInfoWatch, @su13ym4n discusses why exposure validation matters: proving which vulns are exploitable in practice, not just on paper. 📖 Read: hubs.li/Q03L8g_v0 #CyberSecurity #ExposureValidation

✨ That’s a wrap on #PresidioTechXperience 2025! Great discussions, great people, and a great opportunity to share how AEV helps orgs validate defenses with proof. Thanks @Presidio for hosting us + everyone who visited our booth! #CyberSecurity #ExposureValidation


Pen tests and red teaming are useful, but they’re not enough. Learn how IONIX redefines security validation with continuous, non-intrusive exposure testing across your external attack surface: hubs.ly/Q03wpRN60 #exposurevalidation #cybersecurity

Not every “critical” CVE is critical for you. At GovWare 2025, discover how Picus pinpoints exploitable risks and cuts the rest from your backlog. 👉 Learn more: hubs.li/Q03NfCsQ0 #GovWare2025 #CyberSecurity #ExposureValidation #AEV

Why wait for a breach to find out where you're vulnerable? Uni5 Xposure mimics real-world threats to identify gaps in your defenses, ensuring you’re always one step ahead. #adversarialexposurevalidation #exposurevalidation

Not sure if your remediation works? Uni5 Xposure lets you simulate real attacks to validate controls and patches. It even revalidates and adjusts risk scores. #CyberSecurity #ExposureValidation

Unsure if your remediation efforts are working? Our exposure validation technology built into Uni5 Xposure simulates real attacks to prove your controls and patches hold up. Our platform even revalidates patches and adjusts your risk scores accordingly. #ExposureValidation

Not all exposures are equal–and if you don’t know which are exploitable, you’re in the dark. Watch how SafeBreach delivers: + Real-time control insight + True attack surface visibility + Data-backed breach impact hubs.ly/Q03sgsb-0 #ExposureValidation




From scanners to pentests to EASM — security pros juggle more tools than ever. Our latest blog breaks down 3 key approaches: 🔍 Manual Pentesting 🤖 Automated Pentesting ✅ Exposure Validation 📖 ultrared.ai/blog/exposure-… #CTEM #CyberSecurity #ExposureValidation #Cyber

Ransom Tales: Volume III 🎭 INC, Lynx, and SafePay ransomware are evolving fast. See how their TTPs are emulated so defenders can test and validate. 👉 attackiq.com/2025/08/28/ran… #Ransomware #AdversaryResearch #ExposureValidation




Great coverage from @DarkReading on our recent launch! Picus Exposure Validation lets security teams prioritize vulnerabilities based on real-world exploitability—not just theoretical risk. Full details here 👇 hubs.li/Q03v6VTd0 #CyberSecurity #ExposureValidation…

Pen tests and red teaming are useful, but they’re not enough. Learn how IONIX redefines security validation with continuous, non-intrusive exposure testing across your external attack surface: hubs.ly/Q03Sk8yx0 #exposurevalidation #cybersecurity

An incredible day at the Porsche Experience Center in Atlanta! Great conversations, thrilling driving experiences, and valuable cybersecurity and exposure validation insights. 🚗💨 Thanks to everyone who joined us! Until next time! #CyberSecurity #ExposureValidation…



Most security teams are stuck in a cycle of alerts & uncertainty. Ready3 operationalizes CTEM to uncover real risks, automate validation, & prioritize tests based on attack paths. 🔗 Watch Now: attackiq.com/webinars/on-de… #CyberSecurity #ExposureValidation #Ready3 #AEV

Overwhelmed by security alerts? Our Security Research Lead Hüseyin Can Yüceel explains on @TheRegister why Adversarial Exposure Validation is key to identifying threats that truly matter. 👉 Read more: hubs.li/Q03s6Ly30 #CyberSecurity #ExposureValidation

You know BAS. But you should be focusing on AEV. Gartner predicts 40% of orgs will adopt Adversarial Exposure Validation by 2027. Will you be one? 👉 See why it’s crucial to start now: attackiq.com/lp/gartner-aev… #CyberSecurity #AEV #ExposureValidation

The Picus team is ready for GovWare 2025! 📍 Booth V03 | Sands Expo, Singapore 📅 21–23 October Join us to see how AEV validates defenses and helps you focus on real risk. 👉 hubs.li/Q03Nh-lD0 #GovWare2025 #CyberSecurity #ExposureValidation #AEV

40k CVEs last year. 61% marked “critical.” Only 1.9% exploited. It’s time to stop guessing. Join @ronaldeddings, @su13ym4n, & Gursel Arici at #AEVSummit2025 🎟 Register: hubs.li/Q03mbVXr0 #ExposureValidation #CyberSecurity

Open source ≠ operational scale. Adversarial Exposure Validation starts with open source, but real results come with purpose-built platforms. 📥 Download the 2025 Gartner® Market Guide: hubs.li/Q03q4DYc0 #CyberSecurity #ExposureValidation

Scaling red teams is hard. Adversarial Exposure Validation makes it possible with automation, GenAI and reusable attack scenarios. 📥 Read the 2025 Gartner® Market Guide to see how organizations are scaling with AEV: hubs.li/Q03k-g9w0 #ExposureValidation #RedTeam…

Something went wrong.
Something went wrong.
United States Trends
- 1. Cloudflare 215K posts
- 2. Gemini 3 26.5K posts
- 3. #AcousticPianoCollection 1,236 posts
- 4. Olivia Dean 4,164 posts
- 5. Piggy 58.7K posts
- 6. Saudi 122K posts
- 7. La Chona 1,279 posts
- 8. Salman 33.9K posts
- 9. Taco Tuesday 14.8K posts
- 10. #LaSayoSeQuedóGuindando N/A
- 11. CAIR 24.8K posts
- 12. #tuesdayvibe 3,186 posts
- 13. #ONEPIECE1166 4,533 posts
- 14. Good Tuesday 35.9K posts
- 15. Anthropic 8,535 posts
- 16. Sam Leavitt N/A
- 17. Mark Epstein 26.7K posts
- 18. #MSIgnite N/A
- 19. Jamal Khashoggi 2,081 posts
- 20. Passan 1,056 posts