#netsupport نتائج البحث
🚨 #NetSupport RAT is a legit remote access app turned cyber weapon. Its activity spiked in 2025 with data theft attacks targeting healthcare, government, and SMBs in NA and EU. 👨💻 Read report and see analysis of a fresh sample: any.run/malware-trends…

This obfuscation was crazy 🤩 I found it in some .bat files used to infect with #NetSupport RAT in July (#HANEYMANEY/#ZPHP distribution), C2: 5.252.178.48. Does anyone know what this type of obfuscation is called? 🧐 I shared the samples on Bazaar, for anyone who wants to dig…

#netsupport #rat Samples Collection updated / tagged Client32.ini (MD5) 619d70ce84063c8e7e0817cb68e00bad 176.124.203.76:443 Client32.ini (MD5) a04a1940b7b97dc88f0d6aadab4cb095 basketballast.]com:443 blueprintsfdskjhfd.]com:443 62.164.177.48:443 1/2
![JAMESWT_WT's tweet image. #netsupport #rat
Samples Collection updated / tagged
Client32.ini (MD5)
619d70ce84063c8e7e0817cb68e00bad
176.124.203.76:443
Client32.ini (MD5)
a04a1940b7b97dc88f0d6aadab4cb095
basketballast.]com:443
blueprintsfdskjhfd.]com:443
62.164.177.48:443
1/2](https://pbs.twimg.com/media/G2urmdKW4AAd3p-.jpg)
#webshell #opendir #netsupport #rat at: https://appointedtimeagriculture\.com/wp-includes/blocks/post-content/ GatewayAddress=95.179.158.213:443 RADIUSSecret=dgAAAPpMkI7ke494fKEQRUoablcA

#netsupport #rat client32.ini MD5 15d827801ccc1c544cbcd6ddf737d19f stenslie.]com:3085 itnblog.]com:3085 MD5 daa0f1d6b1856657445c4d0261db38fd 45.88.104.]5:443 MD5 a7ac424709447b46683d018ba7dac685 95.179.154.]161:443 1/2 cc @500mk500
![JAMESWT_WT's tweet image. #netsupport #rat
client32.ini
MD5 15d827801ccc1c544cbcd6ddf737d19f
stenslie.]com:3085
itnblog.]com:3085
MD5 daa0f1d6b1856657445c4d0261db38fd
45.88.104.]5:443
MD5 a7ac424709447b46683d018ba7dac685
95.179.154.]161:443
1/2
cc @500mk500](https://pbs.twimg.com/media/G1ObaYOXgAAaib9.jpg)
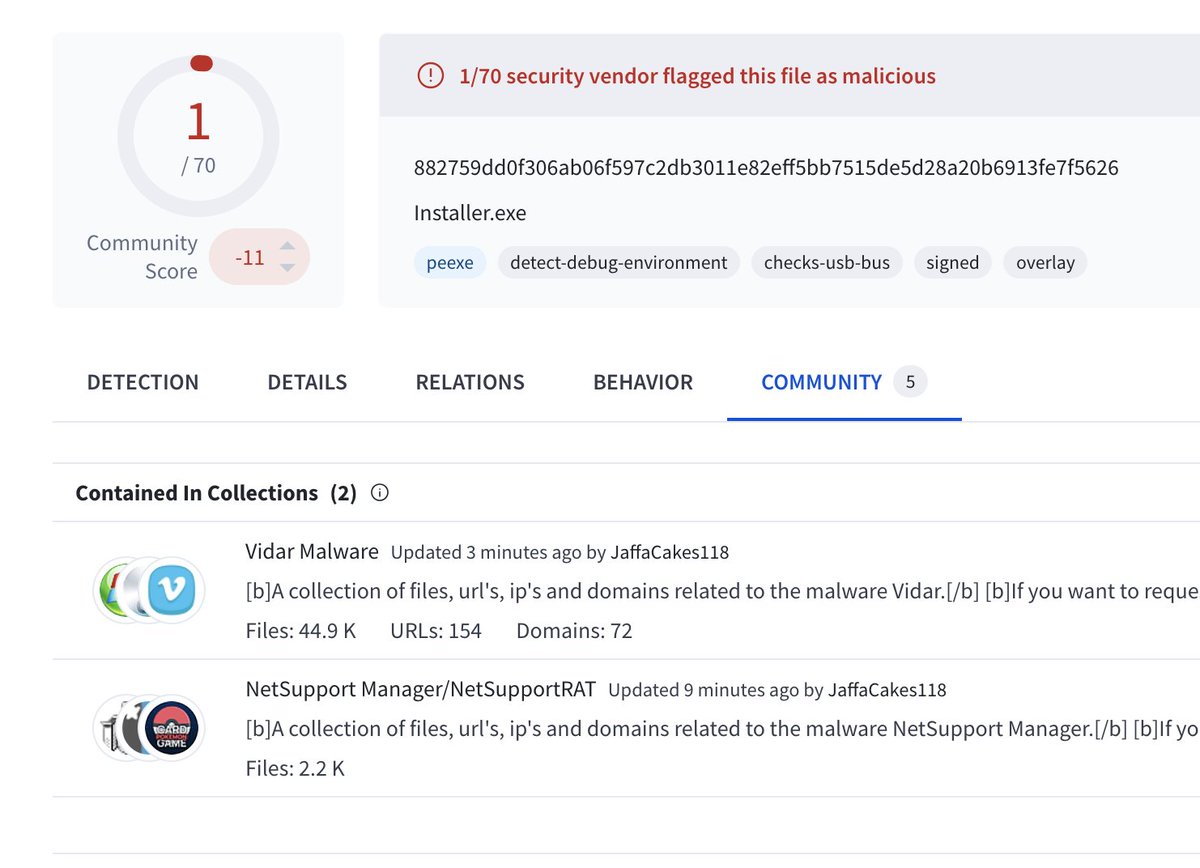
Low detection twofer: #NetSupport and #Vidar virustotal.com/gui/file/88275… bazaar.abuse.ch/sample/882759d… tria.ge/241112-v59c3sx… Signer "ConsolHQ LTD" Reported @JAMESWT_MHT

Thanks for sharing! #PureCrypter leads to #NetSupport RAT - 1st stage from: /centredesoinsanj.test-sites.fr/wp-admin/images/css/hills/bo/Zbstsgyoyuo.bmp (+#opendir) - 2nd stage from: /github.com/BotTradingg/loader/releases NetSupport C2: http://176.124.216.31/fakeurl.htm

#netsupport #rat ❇️Client32.ini MD5 👉ef882a180b4d95e3694be055d60367f8 👉26924d58c0d5fadf5e5c96bdc7532ea5 Gateway👇 ⛔️westford-systems.]icu:1203 ⛔️cdn.westford-computing6.]net:1203 Sample👇 bazaar.abuse.ch/sample/d5348df… Reference👇 malware-traffic-analysis.net/2025/08/20/ind… cc @500mk500 @skocherhan
![JAMESWT_WT's tweet image. #netsupport #rat
❇️Client32.ini
MD5
👉ef882a180b4d95e3694be055d60367f8
👉26924d58c0d5fadf5e5c96bdc7532ea5
Gateway👇
⛔️westford-systems.]icu:1203
⛔️cdn.westford-computing6.]net:1203
Sample👇
bazaar.abuse.ch/sample/d5348df…
Reference👇
malware-traffic-analysis.net/2025/08/20/ind…
cc @500mk500 @skocherhan](https://pbs.twimg.com/media/GzqnKG6XEAA1Jqm.jpg)
🚩 #404TDS → #NetSupport RAT (seen 10 days ago, link still active). 1.- https://accesstobenefits[.]com/cjb1z ↩️ 2.- https://ziahasanexposed[.]com/temp/Update_Accounting_billing_details_dtd_0026032024_pdf.zip NetSupport C2: dcnlaleanae8[.]com:3120 dcnlaleanae9[.]com:3120 +…
![1ZRR4H's tweet image. 🚩 #404TDS → #NetSupport RAT
(seen 10 days ago, link still active).
1.- https://accesstobenefits[.]com/cjb1z ↩️
2.- https://ziahasanexposed[.]com/temp/Update_Accounting_billing_details_dtd_0026032024_pdf.zip
NetSupport C2:
dcnlaleanae8[.]com:3120
dcnlaleanae9[.]com:3120
+…](https://pbs.twimg.com/media/GKbcQMcXgAAbvmb.jpg)
![1ZRR4H's tweet image. 🚩 #404TDS → #NetSupport RAT
(seen 10 days ago, link still active).
1.- https://accesstobenefits[.]com/cjb1z ↩️
2.- https://ziahasanexposed[.]com/temp/Update_Accounting_billing_details_dtd_0026032024_pdf.zip
NetSupport C2:
dcnlaleanae8[.]com:3120
dcnlaleanae9[.]com:3120
+…](https://pbs.twimg.com/media/GKbcOXjWkAIq8Df.png)
![1ZRR4H's tweet image. 🚩 #404TDS → #NetSupport RAT
(seen 10 days ago, link still active).
1.- https://accesstobenefits[.]com/cjb1z ↩️
2.- https://ziahasanexposed[.]com/temp/Update_Accounting_billing_details_dtd_0026032024_pdf.zip
NetSupport C2:
dcnlaleanae8[.]com:3120
dcnlaleanae9[.]com:3120
+…](https://pbs.twimg.com/media/GKbcQNMW0AAD_uL.png)
Compromised site blawx[.]com downloads Javascript file BILL47189.js (bazaar.abuse.ch/sample/a95fe0e…) which eventually leads to #Netsupport RAT. "Exclusive Insights: Unveiling 2024's Lucrative Payouts!" Next stages: - https://blawx[.]com/letter.php?36393 -…
![1ZRR4H's tweet image. Compromised site blawx[.]com downloads Javascript file BILL47189.js (bazaar.abuse.ch/sample/a95fe0e…) which eventually leads to #Netsupport RAT. "Exclusive Insights: Unveiling 2024's Lucrative Payouts!"
Next stages:
- https://blawx[.]com/letter.php?36393
-…](https://pbs.twimg.com/media/GEnTWwAXIAEJF9f.jpg)
![1ZRR4H's tweet image. Compromised site blawx[.]com downloads Javascript file BILL47189.js (bazaar.abuse.ch/sample/a95fe0e…) which eventually leads to #Netsupport RAT. "Exclusive Insights: Unveiling 2024's Lucrative Payouts!"
Next stages:
- https://blawx[.]com/letter.php?36393
-…](https://pbs.twimg.com/media/GEnXz_3WEAAPgJ5.png)
![1ZRR4H's tweet image. Compromised site blawx[.]com downloads Javascript file BILL47189.js (bazaar.abuse.ch/sample/a95fe0e…) which eventually leads to #Netsupport RAT. "Exclusive Insights: Unveiling 2024's Lucrative Payouts!"
Next stages:
- https://blawx[.]com/letter.php?36393
-…](https://pbs.twimg.com/media/GEnYIjyXQAA3IO1.png)
![1ZRR4H's tweet image. Compromised site blawx[.]com downloads Javascript file BILL47189.js (bazaar.abuse.ch/sample/a95fe0e…) which eventually leads to #Netsupport RAT. "Exclusive Insights: Unveiling 2024's Lucrative Payouts!"
Next stages:
- https://blawx[.]com/letter.php?36393
-…](https://pbs.twimg.com/media/GEnYySaWQAApXEs.jpg)
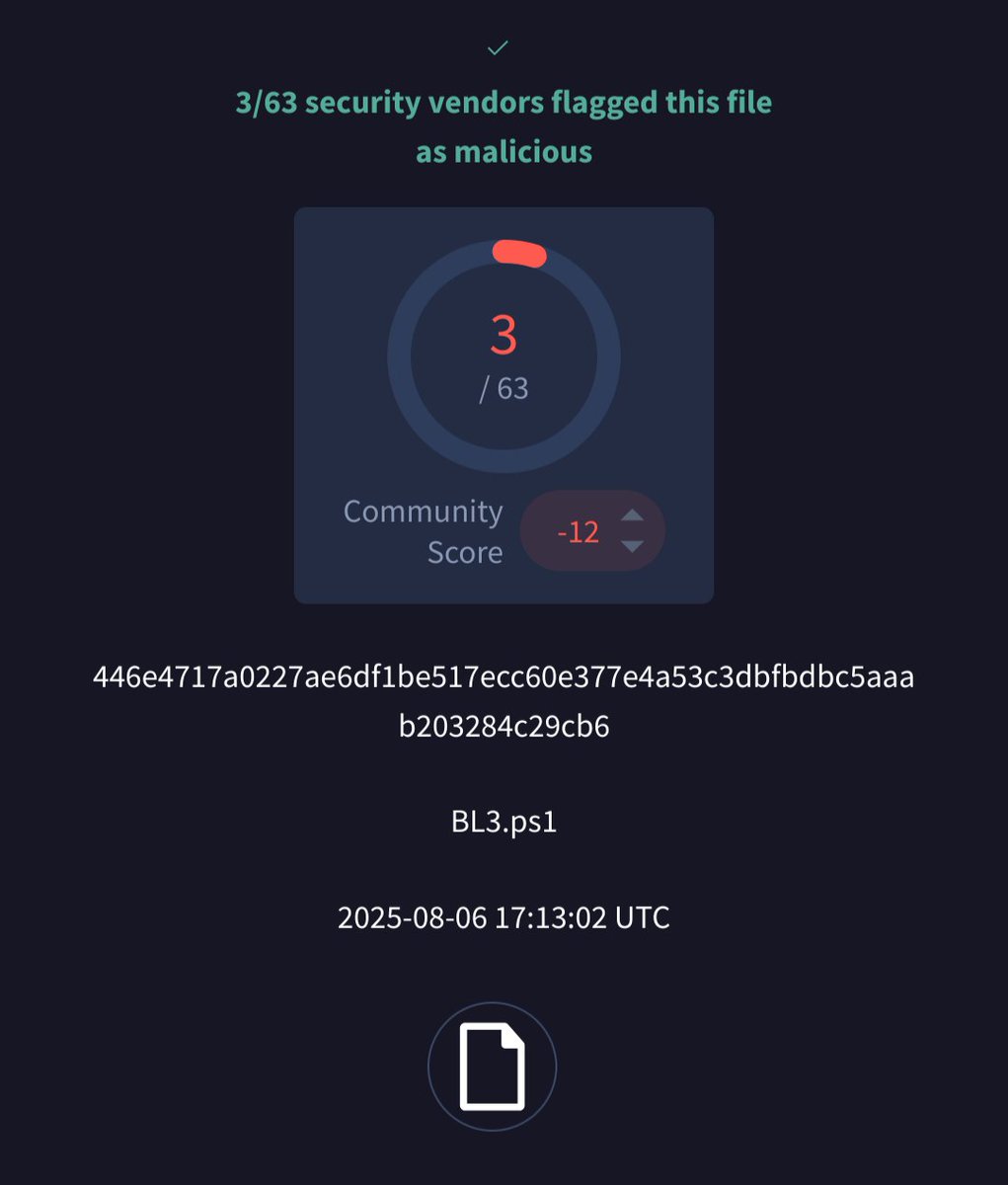
'BL3.ps1' looks like #NetSupport @abuse_ch bazaar.abuse.ch/sample/446e471… 193.143.1(.)216:443 (Proton66)
🚩 "svcservice.exe": bazaar.abuse.ch/sample/0fdc3d4…. Next stages: hxxp://andater393[.]net/see1.zip hxxp://andater393[.]net/see2.zip hxxp://andater393[.]net/see3.zip #NetSupport RAT C2: svanaten1[.]com:1061 svanaten2[.]com:1061 licensee=DERRJON34 serial_no=NSM186593 [+]…
![1ZRR4H's tweet image. 🚩 "svcservice.exe": bazaar.abuse.ch/sample/0fdc3d4….
Next stages:
hxxp://andater393[.]net/see1.zip
hxxp://andater393[.]net/see2.zip
hxxp://andater393[.]net/see3.zip
#NetSupport RAT C2:
svanaten1[.]com:1061
svanaten2[.]com:1061
licensee=DERRJON34
serial_no=NSM186593
[+]…](https://pbs.twimg.com/media/GAXQDFeW4AIqqLu.png)
❌ WARNING 🚨 Hackers have used a well-crafted #PokemonNFT card game website to distribute the #NetSupport remote access tool 💀 They can now remotely connect to a user's device to steal data, install other malware, etc #pokemonCards #Hacked #GamingNews #NFTs

📣 Need to get in touch with NET? 🤝 We are here to help. For any inquiries, questions, or assistance, you can contact us through the following channels. Our team is ready to assist you! Don't hesitate to reach out. 🔗 #ContactUs #NETSupport

#NetSupport #Rat Client32.ini MD5 de6d8f6af4bf9087a4d2ab3c88e2cb14 👇 ⛔️194.0.234.]17:443 Client32.ini MD5 006a74830a4047fe9e1d5e574a2e6eba 👇 ⛔️193.24.123.]37:443 Samples bazaar.abuse.ch/browse/tag/194… bazaar.abuse.ch/browse/tag/193… cc @500mk500 @skocherhan @abuse_ch
![JAMESWT_WT's tweet image. #NetSupport #Rat
Client32.ini
MD5 de6d8f6af4bf9087a4d2ab3c88e2cb14
👇
⛔️194.0.234.]17:443
Client32.ini
MD5 006a74830a4047fe9e1d5e574a2e6eba
👇
⛔️193.24.123.]37:443
Samples
bazaar.abuse.ch/browse/tag/194…
bazaar.abuse.ch/browse/tag/193…
cc @500mk500 @skocherhan @abuse_ch](https://pbs.twimg.com/media/GzRMrRzXMAEkEN8.jpg)
Wonderful to finally meet and chat with the fab @OliverSlt IRL! Great #NetSupportInsights episode to come all about #Leadership. @NetSupportGroup #NetSupport #SE51 @Bett_show #Bett23

North American transportation companies have been targeted in a sophisticated cyber espionage campaign using malware like Lumma Stealer and NetSupport. Read more about the campaign here: hubs.ly/Q02RllF_0 #LummaStealer #NetSupport #CyberEspionage #OSINT

#netsupport #rat Samples Collection updated / tagged Client32.ini (MD5) 619d70ce84063c8e7e0817cb68e00bad 176.124.203.76:443 Client32.ini (MD5) a04a1940b7b97dc88f0d6aadab4cb095 basketballast.]com:443 blueprintsfdskjhfd.]com:443 62.164.177.48:443 1/2
![JAMESWT_WT's tweet image. #netsupport #rat
Samples Collection updated / tagged
Client32.ini (MD5)
619d70ce84063c8e7e0817cb68e00bad
176.124.203.76:443
Client32.ini (MD5)
a04a1940b7b97dc88f0d6aadab4cb095
basketballast.]com:443
blueprintsfdskjhfd.]com:443
62.164.177.48:443
1/2](https://pbs.twimg.com/media/G2urmdKW4AAd3p-.jpg)
'@GITEX_GLOBAL 2025 is coming! We're excited to be part of the world’s largest tech show to showcase our award-winning software solutions! ✅ Remote control ✅ITAM ✅Alerting and notification ✅Training and onboarding ✅Classroom management #GITEXGLOBAL #NetSupport #TechNews

It's time to ditch the loyalty tax! Check out our modern, secure and feature-rich tools with flexible pricing and free training. buff.ly/rC6Onh9 #SoftwareSolutions #ITPros #NetSupport
It's time to ditch the loyalty tax! Check out our modern, secure and feature-rich tools with flexible pricing and free training. buff.ly/rC6Onh9 #SoftwareSolutions #ITPros #NetSupport
It's time to ditch the loyalty tax! Check out our modern, secure and feature-rich tools with flexible pricing and free training. buff.ly/rC6Onh9 #SoftwareSolutions #ITPros #NetSupport
Es ist Zeit, die Loyalitätssteuer abzuschaffen! Entdecken Sie unsere modernen, sicheren und funktionsreichen Tools mit flexiblen Preisen und kostenlosen Schulungen. buff.ly/rC6Onh9 #SoftwareLösungen #ITProfis #NetSupport

#netsupport #rat client32.ini MD5 15d827801ccc1c544cbcd6ddf737d19f stenslie.]com:3085 itnblog.]com:3085 MD5 daa0f1d6b1856657445c4d0261db38fd 45.88.104.]5:443 MD5 a7ac424709447b46683d018ba7dac685 95.179.154.]161:443 1/2 cc @500mk500
![JAMESWT_WT's tweet image. #netsupport #rat
client32.ini
MD5 15d827801ccc1c544cbcd6ddf737d19f
stenslie.]com:3085
itnblog.]com:3085
MD5 daa0f1d6b1856657445c4d0261db38fd
45.88.104.]5:443
MD5 a7ac424709447b46683d018ba7dac685
95.179.154.]161:443
1/2
cc @500mk500](https://pbs.twimg.com/media/G1ObaYOXgAAaib9.jpg)
So #netsupport #rat Client32.ini 2025-09-19 MD5 9b408f3004b6e26f2d53a987a701c3b0 👇 Gateway 141.98.11.]224:5555 nsgatetest1.]digital:5555 From f003.backblazeb2.]com/file/tempfilestorage/adaptive.msi Samples Collection bazaar.abuse.ch/browse/tag/nsg… 🤟 @SquiblydooBlog cc @500mk500
![JAMESWT_WT's tweet image. So #netsupport #rat
Client32.ini 2025-09-19
MD5
9b408f3004b6e26f2d53a987a701c3b0
👇
Gateway
141.98.11.]224:5555
nsgatetest1.]digital:5555
From
f003.backblazeb2.]com/file/tempfilestorage/adaptive.msi
Samples Collection
bazaar.abuse.ch/browse/tag/nsg…
🤟 @SquiblydooBlog
cc @500mk500](https://pbs.twimg.com/media/G1ORjX3X0AsPGGL.jpg)
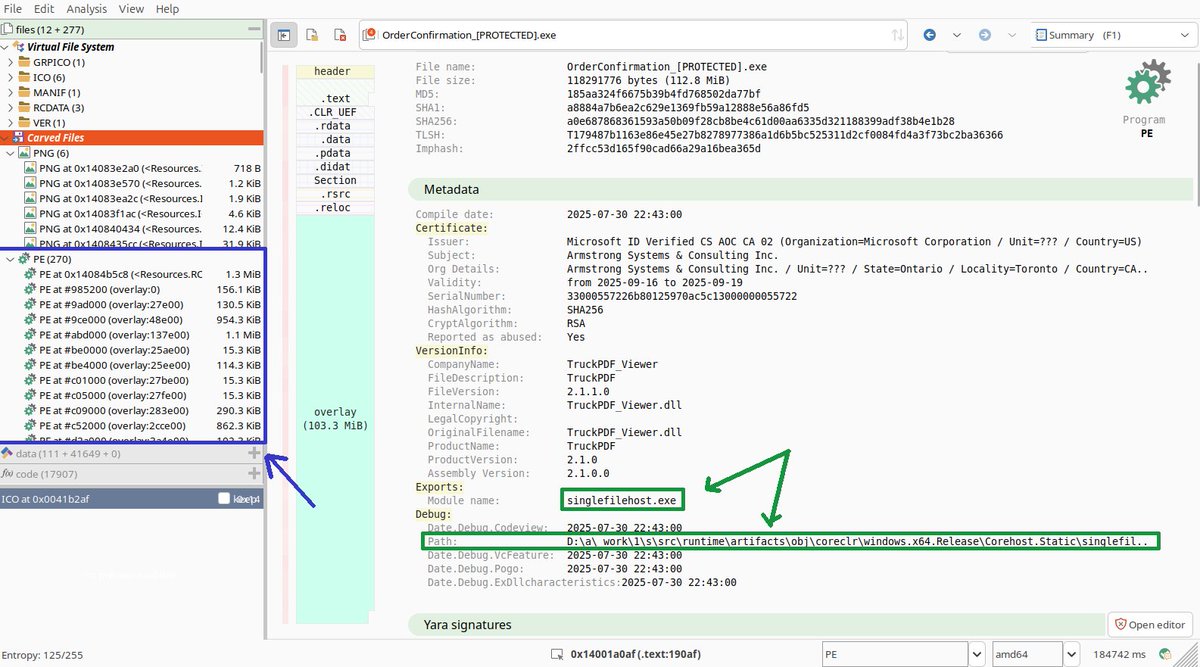
"FUD" from VirusTotal. Signed, 112 MB file. Lets analyze. File is SingleFile .NET; I see this with Malcat: Debug and Exports indicate it is SingleFile (green arrows in image) Also, Malcat carved 270 PE out of the overlay (blue arrow), indicative of SingleFile .NET 1/8

Everything you need to know about NetSupport Manager, all in one place. 👉 Watch our videos to see how you can securely manage devices from anywhere. buff.ly/HuKXX6d #NetSupport #RemoteDesktop #ITPro

Everything you need to know about NetSupport Manager, all in one place. 👉 Watch our videos to see how you can securely manage devices from anywhere. buff.ly/HuKXX6d #NetSupport #RemoteDesktop #ITPro

Everything you need to know about NetSupport Manager, all in one place. 👉 Watch our videos to see how you can securely manage devices from anywhere. buff.ly/HuKXX6d #NetSupport #RemoteDesktop #ITPro

#APT #UAC0050 #NetSupport #RAT C2: 178.16.54./125 178.16.54./134 178.16.54./139
🚨 UAC-0050 is spreading NetSupport Manager in a new campaign. C2 servers: hxxp://178.16.54[.]130/fakeurl.htm hxxp://178.16.54[.]131/fakeurl.htm hxxp://178.16.54[.]132/fakeurl.htm
#netsupport #rat👇 Client32.ini MD5 1bbaaefeaa6cc19451eb65ebb88a69b3 141.98.11.]175:443 lastmychancetoss.]com:443 kaldotrototo.]com:443 Samples👇 bazaar.abuse.ch/browse/tag/141… cc @500mk500 @skocherhan
![JAMESWT_WT's tweet image. #netsupport #rat👇
Client32.ini
MD5 1bbaaefeaa6cc19451eb65ebb88a69b3
141.98.11.]175:443
lastmychancetoss.]com:443
kaldotrototo.]com:443
Samples👇
bazaar.abuse.ch/browse/tag/141…
cc @500mk500 @skocherhan](https://pbs.twimg.com/media/G0ZTryHXMAAxxSo.jpg)
Every school needs a proactive way to protect students. classroom.cloud gives educators the insights they need to keep kids safe. buff.ly/hbgO4DP #SchoolSafety #CyberSecurity #NetSupport
No bots, just people. 🗣️ When you contact us, you'll always get a real person ready to help. That's the NetSupport difference. buff.ly/YteoHAo #NetSupport #CustomerService #ITSupport

Get started fast! 🚀 Our 30-min installation guide makes setting up NetSupport a breeze. Watch our step-by-step walkthrough now. buff.ly/ASgQUB0 #NetSupport #QuickStart #EasySetup #TechTips
Find the NetSupport team at an event near you! We're at ICT for Education, GITEX Global & more this fall. See the full list! buff.ly/b3tOxWa #NetSupport #UpcomingEvents #EdTech #ITManagement #GITEX #ICTforEducation #Networking
This obfuscation was crazy 🤩 I found it in some .bat files used to infect with #NetSupport RAT in July (#HANEYMANEY/#ZPHP distribution), C2: 5.252.178.48. Does anyone know what this type of obfuscation is called? 🧐 I shared the samples on Bazaar, for anyone who wants to dig…

#webshell #opendir #netsupport #rat at: https://appointedtimeagriculture\.com/wp-includes/blocks/post-content/ GatewayAddress=95.179.158.213:443 RADIUSSecret=dgAAAPpMkI7ke494fKEQRUoablcA

Interesting #FakeSG execution from an HTA payload that leads to #NetSupport. Find my SIGMA rule for detecting this cool cmstp.exe execution technique below: ➡️Lots of initial PowerShell obfuscated scripts ➡️Using cmstp.exe to install a fake connection manager service profile…


Thanks for sharing! #PureCrypter leads to #NetSupport RAT - 1st stage from: /centredesoinsanj.test-sites.fr/wp-admin/images/css/hills/bo/Zbstsgyoyuo.bmp (+#opendir) - 2nd stage from: /github.com/BotTradingg/loader/releases NetSupport C2: http://176.124.216.31/fakeurl.htm

Low detection twofer: #NetSupport and #Vidar virustotal.com/gui/file/88275… bazaar.abuse.ch/sample/882759d… tria.ge/241112-v59c3sx… Signer "ConsolHQ LTD" Reported @JAMESWT_MHT


A brief example analysis of the malware spread over SEO Poisoning, delivering #Lumma Stealer and #NetSupport targeting hard crypto wallets Thread👇👇

🚩 "svcservice.exe": bazaar.abuse.ch/sample/0fdc3d4…. Next stages: hxxp://andater393[.]net/see1.zip hxxp://andater393[.]net/see2.zip hxxp://andater393[.]net/see3.zip #NetSupport RAT C2: svanaten1[.]com:1061 svanaten2[.]com:1061 licensee=DERRJON34 serial_no=NSM186593 [+]…
![1ZRR4H's tweet image. 🚩 "svcservice.exe": bazaar.abuse.ch/sample/0fdc3d4….
Next stages:
hxxp://andater393[.]net/see1.zip
hxxp://andater393[.]net/see2.zip
hxxp://andater393[.]net/see3.zip
#NetSupport RAT C2:
svanaten1[.]com:1061
svanaten2[.]com:1061
licensee=DERRJON34
serial_no=NSM186593
[+]…](https://pbs.twimg.com/media/GAXQDFeW4AIqqLu.png)
🚩 #404TDS → #NetSupport RAT (seen 10 days ago, link still active). 1.- https://accesstobenefits[.]com/cjb1z ↩️ 2.- https://ziahasanexposed[.]com/temp/Update_Accounting_billing_details_dtd_0026032024_pdf.zip NetSupport C2: dcnlaleanae8[.]com:3120 dcnlaleanae9[.]com:3120 +…
![1ZRR4H's tweet image. 🚩 #404TDS → #NetSupport RAT
(seen 10 days ago, link still active).
1.- https://accesstobenefits[.]com/cjb1z ↩️
2.- https://ziahasanexposed[.]com/temp/Update_Accounting_billing_details_dtd_0026032024_pdf.zip
NetSupport C2:
dcnlaleanae8[.]com:3120
dcnlaleanae9[.]com:3120
+…](https://pbs.twimg.com/media/GKbcQMcXgAAbvmb.jpg)
![1ZRR4H's tweet image. 🚩 #404TDS → #NetSupport RAT
(seen 10 days ago, link still active).
1.- https://accesstobenefits[.]com/cjb1z ↩️
2.- https://ziahasanexposed[.]com/temp/Update_Accounting_billing_details_dtd_0026032024_pdf.zip
NetSupport C2:
dcnlaleanae8[.]com:3120
dcnlaleanae9[.]com:3120
+…](https://pbs.twimg.com/media/GKbcOXjWkAIq8Df.png)
![1ZRR4H's tweet image. 🚩 #404TDS → #NetSupport RAT
(seen 10 days ago, link still active).
1.- https://accesstobenefits[.]com/cjb1z ↩️
2.- https://ziahasanexposed[.]com/temp/Update_Accounting_billing_details_dtd_0026032024_pdf.zip
NetSupport C2:
dcnlaleanae8[.]com:3120
dcnlaleanae9[.]com:3120
+…](https://pbs.twimg.com/media/GKbcQNMW0AAD_uL.png)
🚨 #NetSupport RAT is a legit remote access app turned cyber weapon. Its activity spiked in 2025 with data theft attacks targeting healthcare, government, and SMBs in NA and EU. 👨💻 Read report and see analysis of a fresh sample: any.run/malware-trends…

'@GITEX_GLOBAL 2025 is coming! We're excited to be part of the world’s largest tech show to showcase our award-winning software solutions! ✅ Remote control ✅ITAM ✅Alerting and notification ✅Training and onboarding ✅Classroom management #GITEXGLOBAL #NetSupport #TechNews

#ClickFix campaign targeting web3 users on YouTube sponsored videos spreading #Netsupport RAT Malicious paste: /pastesnip.com/raw/sNu60aPq Video: //www.youtube.com/watch?v=Qabajxy0OKY Detonation: app.any.run/tasks/f993b425…

Compromised site blawx[.]com downloads Javascript file BILL47189.js (bazaar.abuse.ch/sample/a95fe0e…) which eventually leads to #Netsupport RAT. "Exclusive Insights: Unveiling 2024's Lucrative Payouts!" Next stages: - https://blawx[.]com/letter.php?36393 -…
![1ZRR4H's tweet image. Compromised site blawx[.]com downloads Javascript file BILL47189.js (bazaar.abuse.ch/sample/a95fe0e…) which eventually leads to #Netsupport RAT. "Exclusive Insights: Unveiling 2024's Lucrative Payouts!"
Next stages:
- https://blawx[.]com/letter.php?36393
-…](https://pbs.twimg.com/media/GEnTWwAXIAEJF9f.jpg)
![1ZRR4H's tweet image. Compromised site blawx[.]com downloads Javascript file BILL47189.js (bazaar.abuse.ch/sample/a95fe0e…) which eventually leads to #Netsupport RAT. "Exclusive Insights: Unveiling 2024's Lucrative Payouts!"
Next stages:
- https://blawx[.]com/letter.php?36393
-…](https://pbs.twimg.com/media/GEnXz_3WEAAPgJ5.png)
![1ZRR4H's tweet image. Compromised site blawx[.]com downloads Javascript file BILL47189.js (bazaar.abuse.ch/sample/a95fe0e…) which eventually leads to #Netsupport RAT. "Exclusive Insights: Unveiling 2024's Lucrative Payouts!"
Next stages:
- https://blawx[.]com/letter.php?36393
-…](https://pbs.twimg.com/media/GEnYIjyXQAA3IO1.png)
![1ZRR4H's tweet image. Compromised site blawx[.]com downloads Javascript file BILL47189.js (bazaar.abuse.ch/sample/a95fe0e…) which eventually leads to #Netsupport RAT. "Exclusive Insights: Unveiling 2024's Lucrative Payouts!"
Next stages:
- https://blawx[.]com/letter.php?36393
-…](https://pbs.twimg.com/media/GEnYySaWQAApXEs.jpg)
#NetSupport #Rat Client32.ini MD5 de6d8f6af4bf9087a4d2ab3c88e2cb14 👇 ⛔️194.0.234.]17:443 Client32.ini MD5 006a74830a4047fe9e1d5e574a2e6eba 👇 ⛔️193.24.123.]37:443 Samples bazaar.abuse.ch/browse/tag/194… bazaar.abuse.ch/browse/tag/193… cc @500mk500 @skocherhan @abuse_ch
![JAMESWT_WT's tweet image. #NetSupport #Rat
Client32.ini
MD5 de6d8f6af4bf9087a4d2ab3c88e2cb14
👇
⛔️194.0.234.]17:443
Client32.ini
MD5 006a74830a4047fe9e1d5e574a2e6eba
👇
⛔️193.24.123.]37:443
Samples
bazaar.abuse.ch/browse/tag/194…
bazaar.abuse.ch/browse/tag/193…
cc @500mk500 @skocherhan @abuse_ch](https://pbs.twimg.com/media/GzRMrRzXMAEkEN8.jpg)
'BL3.ps1' looks like #NetSupport @abuse_ch bazaar.abuse.ch/sample/446e471… 193.143.1(.)216:443 (Proton66)

#netsupport #rat ❇️Client32.ini MD5 👉ef882a180b4d95e3694be055d60367f8 👉26924d58c0d5fadf5e5c96bdc7532ea5 Gateway👇 ⛔️westford-systems.]icu:1203 ⛔️cdn.westford-computing6.]net:1203 Sample👇 bazaar.abuse.ch/sample/d5348df… Reference👇 malware-traffic-analysis.net/2025/08/20/ind… cc @500mk500 @skocherhan
![JAMESWT_WT's tweet image. #netsupport #rat
❇️Client32.ini
MD5
👉ef882a180b4d95e3694be055d60367f8
👉26924d58c0d5fadf5e5c96bdc7532ea5
Gateway👇
⛔️westford-systems.]icu:1203
⛔️cdn.westford-computing6.]net:1203
Sample👇
bazaar.abuse.ch/sample/d5348df…
Reference👇
malware-traffic-analysis.net/2025/08/20/ind…
cc @500mk500 @skocherhan](https://pbs.twimg.com/media/GzqnKG6XEAA1Jqm.jpg)
#NetSupport #Rat ✅Samples Collection updated/tagged bazaar.abuse.ch/browse/signatu… Client32.ini hash list👇 pastebin.com/EUu8rjiU cc @500mk500 @skocherhan @c_APT_ure @VirITeXplorer


Something went wrong.
Something went wrong.
United States Trends
- 1. Branch 37.1K posts
- 2. Chiefs 112K posts
- 3. Red Cross 53.8K posts
- 4. Exceeded 5,846 posts
- 5. Binance DEX 5,137 posts
- 6. #njkopw 8,011 posts
- 7. Mahomes 34.8K posts
- 8. Rod Wave 1,659 posts
- 9. Air Force One 57.7K posts
- 10. #LaGranjaVIP 83.3K posts
- 11. Eitan Mor 17.3K posts
- 12. #TNABoundForGlory 59.7K posts
- 13. #LoveCabin 1,384 posts
- 14. Ziv Berman 20.2K posts
- 15. Alon Ohel 17.9K posts
- 16. Tel Aviv 59.4K posts
- 17. Matan Angrest 16.1K posts
- 18. Omri Miran 16.4K posts
- 19. Bryce Miller 4,608 posts
- 20. Tom Homan 81.5K posts






![skocherhan's tweet image. 5[.]181[.]157[.]34
AS39798 MivoCloud SRL 🇲🇩
#NetSupport @JAMESWT_WT](https://pbs.twimg.com/media/GwYl3GtWwAE0_Bn.jpg)













![skocherhan's tweet image. 43[.]218[.]76[.]102:790
#NetSupport](https://pbs.twimg.com/media/G0UBPk1W4AAtks6.jpg)




























![skocherhan's tweet image. vietnam24hvoyage[.]com
C2: 185[.]163[.]45[.]41
AS39798 MivoCloud SRL 🇲🇩
#NetSupport @JAMESWT_WT](https://pbs.twimg.com/media/Gv89Gp-XMAAMM21.jpg)
![skocherhan's tweet image. 144[.]172[.]104[.]121
AS14956 ROUTERHOSTING 🇺🇸
#NetSupport](https://pbs.twimg.com/media/GyDBHrKXAAEGeDv.jpg)
