#networksecurityassignmentsolutions resultados da pesquisa
🆕 Nueva carrera de grado en CIBERSEGURIDAD-CIBERDEFENSA, 2026. Con título intermedio. Recomiendo a informáticos, abogados, o a cualquiera que tenga interés. Un área IT que es MUY requerida y bien paga, se necesitan estos perfiles cada vez más. - A distancia - No arancelada

Bringing brands to life through design 💼✨ Poster + business cards for SecureNet Solutions in bold blue & yellow 💙💛, built to show trust, innovation & style. DESIGN | PRINT | BRAND #StrivingTowardsPerfection

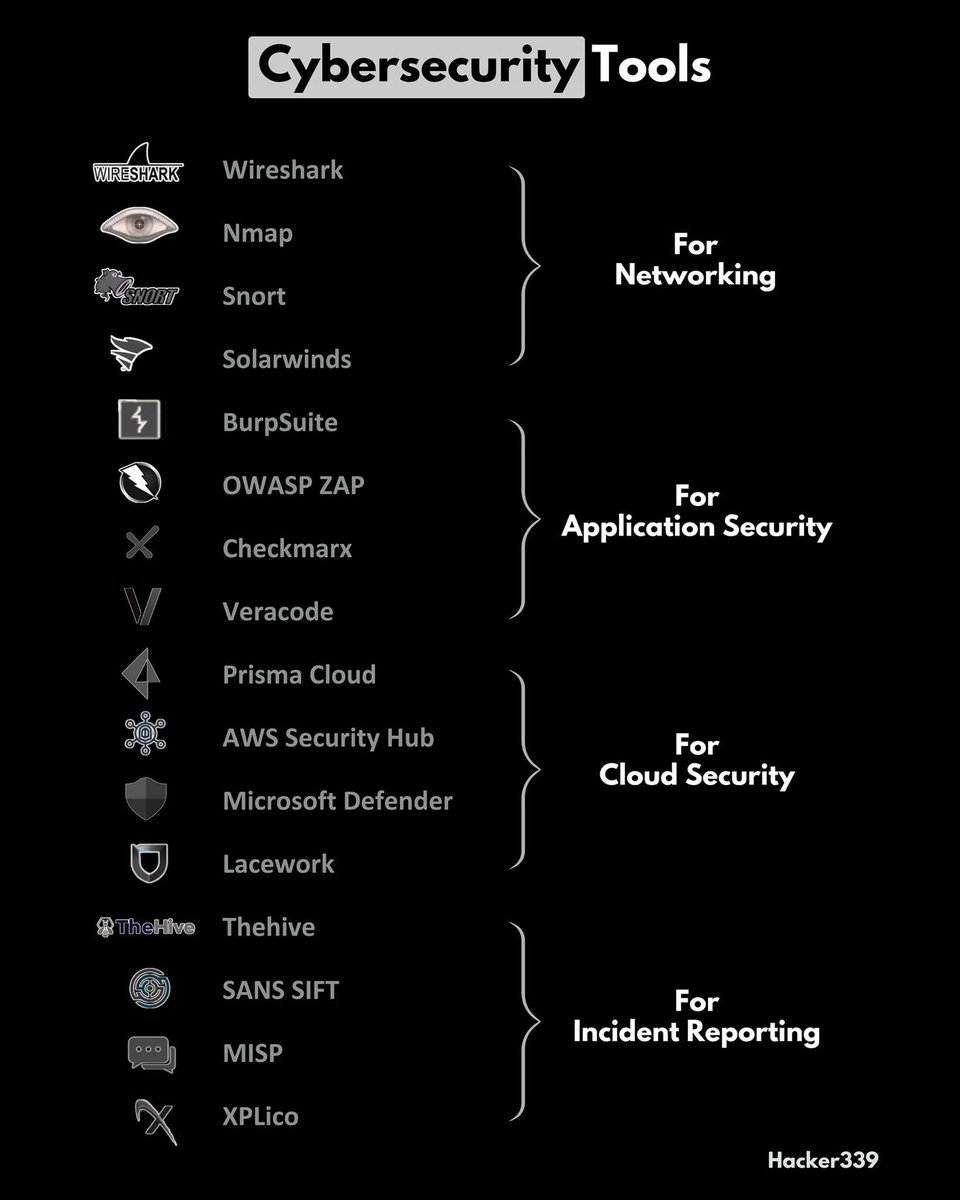
Cybersecurity Tools For Networking • Wireshark → Used for network traffic analysis and packet inspection. • Nmap → Network scanner for discovering devices, open ports, and services. • Snort → Intrusion detection and prevention system (IDS/IPS). • SolarWinds → Network…

Cybersecurity Compliance 🔒 🛡️ Our SD-WAN connectivity platform is more than a technology – it's a vehicle to access our suite of #CyberSecurity, training, and compliance solutions, enabling our customers to meet the compliance levels required by their organizations. Learn…
We’ve just completed a full round of internal security audits across Tensora’s repositories and contracts. Every module and dependency was reviewed, from validator logic to bridge relayers, and all potential vulnerabilities or key exposure risks have been identified and patched.…
Keeping your firewalls, routers, and software up to date is one of the simplest and most effective ways to protect your network from cyber threats. Cybercriminals often exploit outdated systems to gain unauthorized access or install malware. 💡 Tips for staying protected:…

😨🎃🐈⬛ ¿Tenés miedo de ser la próxima víctima? Podemos ayudarte con nuestros servicios: > @Vulseek para que puedas enterarte rápido de tus #vulnerabilidades y gestionarlas desde una única plataforma SaaS. > Logseek, nuestro #SIEM tipo SaaS para que identifiques anomalías en tus…

🚀 My Recent Cybersecurity Project: Network Recon & Security Mapping with Nmap 🔍 A Thread (🧵) I’m excited to share my recent hands-on cybersecurity project, where I used Nmap for advanced network scanning, analysis, and security assessment—all without any extra tools! 🛡️ 🔧…


Cyberattacks on telecoms are up 94% — and BEAD compliance is more critical than ever. ISPs must prove they can secure what they’ve built. CHR Solutions helps ISPs stay compliant & protected with practical cybersecurity tools. Learn more: chrsolutions.com/blog/after-bea…
🔒 Looking to simplify your security? See how Extreme takes the complexity out of networking with integrated, #AI-native security solutions this #CybersecurityAwareness Month! Learn more: extremenetworks.com/solutions/secu…
Most breaches start with compromised credentials. Strengthen identity layers with MFA, passwordless tech & role-based access as part of a Zero Trust strategy. See how Exclusive Networks helps partners deliver scalable, secure solutions. eu1.hubs.ly/H0nQd0g0 #WeAreExclusive

Cybersecurity Tools ■ For Networking • Wireshark → Used for network traffic analysis and packet inspection. • Nmap → Network scanner for discovering devices, open ports, and services. • Snort → Intrusion detection and prevention system (IDS/IPS). • SolarWinds →…

Cybersecurity Tools For Networking • Wireshark → Used for network traffic analysis and packet inspection. • Nmap → Network scanner for discovering devices, open ports, and services. • Snort → Intrusion detection and prevention system (IDS/IPS). • SolarWinds → Network…
When ransomware hits, panic follows. 💻💥 But paying the ransom doesn’t guarantee recovery — it fuels attackers. Backups, response plans & awareness are your real defense. Preparedness defines leadership. 🛡️ #Ransomware #CyberSecurity #StaySecure

This time I tried to make a visualization of few Network Attacks. Do lemme know if you'd like to see more. Download : securityzines.com/flyers/network… #infosec #appsec #network #technology #cybersecurity

Red Team Roadmap 🔴🎯 ├── Foundations │ ├── Networking Basics │ │ ├── TCP/IP & Protocol Exploitation │ │ ├── DNS & DHCP Attacks │ │ ├── Subnetting & Network Mapping │ │ └── Topology Enumeration │ ├── Operating…
Unmanaged infrastructure exposes your enterprise to critical, devastating risks. We deliver the seamless, constant defense you need. Get inherent defense, not just repair. Upgrade your foundation with our expert Managed Services. #ITSupport #ManagedServices
Cybersecurity isn’t just IT’s job — it’s everyone’s. One careless click can expose everything. Build awareness, train your teams, and make security part of your culture. Strong tools need smarter people. 💪🔐 #CybersecurityAwareness #CyberReadiness #TeamSecurity
Something went wrong.
Something went wrong.
United States Trends
- 1. Clippers 11.4K posts
- 2. Harden 8,618 posts
- 3. #DWTS 48.2K posts
- 4. Giannis 26.8K posts
- 5. Ty Lue 1,001 posts
- 6. Kawhi 3,069 posts
- 7. Whitney 15.1K posts
- 8. #RHOSLC 7,032 posts
- 9. Markstrom 1,660 posts
- 10. Brunson 7,028 posts
- 11. Ryan Rollins 2,837 posts
- 12. Chris Paul 1,449 posts
- 13. #Blackhawks 2,503 posts
- 14. Alix 6,581 posts
- 15. Caden 7,802 posts
- 16. UTEP 1,984 posts
- 17. Huda 4,502 posts
- 18. Elaine 37.3K posts
- 19. Sixers 22.1K posts
- 20. Connor Bedard 4,641 posts



















