#operationaltechnology 搜尋結果
Cybersecurity Awareness Month reminds us: water, transit, and healthcare rely on OT security. OT attacks disrupt communities, protecting OT means protecting lives. #CybersecurityAwareness #OTSecurity #OperationalTechnology #ProtectOurCommunities
We recently released new joint guidance with our international partners to help organizations build a definitive record of their #OperationalTechnology (OT) environments – because if you can’t see it, you can’t defend it. Read more: cyber.gc.ca/en/news-events…

🎙️ 𝐍𝐞𝐰 𝐁𝐚𝐝 𝐀𝐜𝐭𝐨𝐫𝐬 𝐞𝐩𝐢𝐬𝐨𝐝𝐞 𝐝𝐫𝐨𝐩! 🎙️ ⚙️ From factories to public utilities, #OperationalTechnology keeps our world running yet it has been exposed to increasing cyber threats. Hear from Patrick Gillespie, OT Practice Director at GuidePoint Security, in our…
Your operational technology just malfunctioned. Downtime is critical. Drive for hours to fix it or just use Privleged Remote Access? Check out this OT resource page for more information. lnkd.in/eVUWXbMw #OperationalTechnology #OT
One weak policy could take down your entire operation. Explore the importance of #OperationalTechnology cybersecurity policy management program with our expert Anirban Ghosh. 👇 #CybersecurityAwareness
Our joint guidance on establishing and maintaining a comprehensive view of your #OperationalTechnology architecture remains a foundational element of OT cyber resilience. cyber.gc.ca/en/news-events…

The Hidden Costs Of Legacy #OperationalTechnology (#OT) wateronline.com/doc/the-hidden… via @Stantec
Critical infrastructure requires uncompromising security. With 82,000 miles of pipelines transporting 40% of the U.S. natural gas supply, Kinder Morgan, Inc. needed to strengthen and modernize access to its #DataCenter and #OperationalTechnology environments. That’s why they…

#OperationalTechnology (OT) still makes much of the world go round. In his latest blog, @PhilMuncaster explores new guidance from the NCSC, which emphasises the vital first step to securing OT: visibility: isms.online/information-se…

🔒 Presenting Now: Operational Technology – Like Shadow IT but Bigger and Noisier Dave Cartwright, Chair of the Channel Islands Cyber Security Forum, is addressing the critical issues surrounding Operational Technology. #CyberSecurity #OperationalTechnology h#teissLondon2024

One disruption in critical infrastructure can ripple across the nation. Cyber defense isn’t optional, it’s survival. Read our interview with Monty Mills: hubs.la/Q03LB9Hs0 #Cybersecurity #OperationalTechnology #CriticalInfrastructure #CyberDefense #OTSecurity
As one of North America’s largest energy infrastructure companies, Kinder Morgan transports 40% of the U.S.’s natural gas through its 82,000 miles of pipelines. Securing that infrastructure is mission-critical. After successfully protecting its #OperationalTechnology with Xage,…

IT/OT convergence is the integration of #InformationTechnology (IT) systems with #OperationalTechnology (OT) systems. bit.ly/3JirnBi

Unlike IT, IoT devices don't formally identify themselves on the network, making visibility and security a challenge—especially with encrypted traffic. Learn how to address this critical gap in our webinar replay. spr.ly/6013QZG0W #operationaltechnology #IoT
🔔 Mark April 16 in your calendar and join us and Stora Enso for an insightful webinar focused on #OTcybersecurity. Secure your spot today! Register here: hubs.la/Q02pM0qj0 #cybersecurity #operationaltechnology #OTsecurity #criticalinfrastructure

In the evolving landscape of #OperationalTechnology cybersecurity, ensuring compliance to NERC CIP regulations is more critical than ever. Join our upcoming #LinkedInLive to ensure your organization builds a strong industrial #CybersecurityProgram: ms.spr.ly/6013SdvBZ
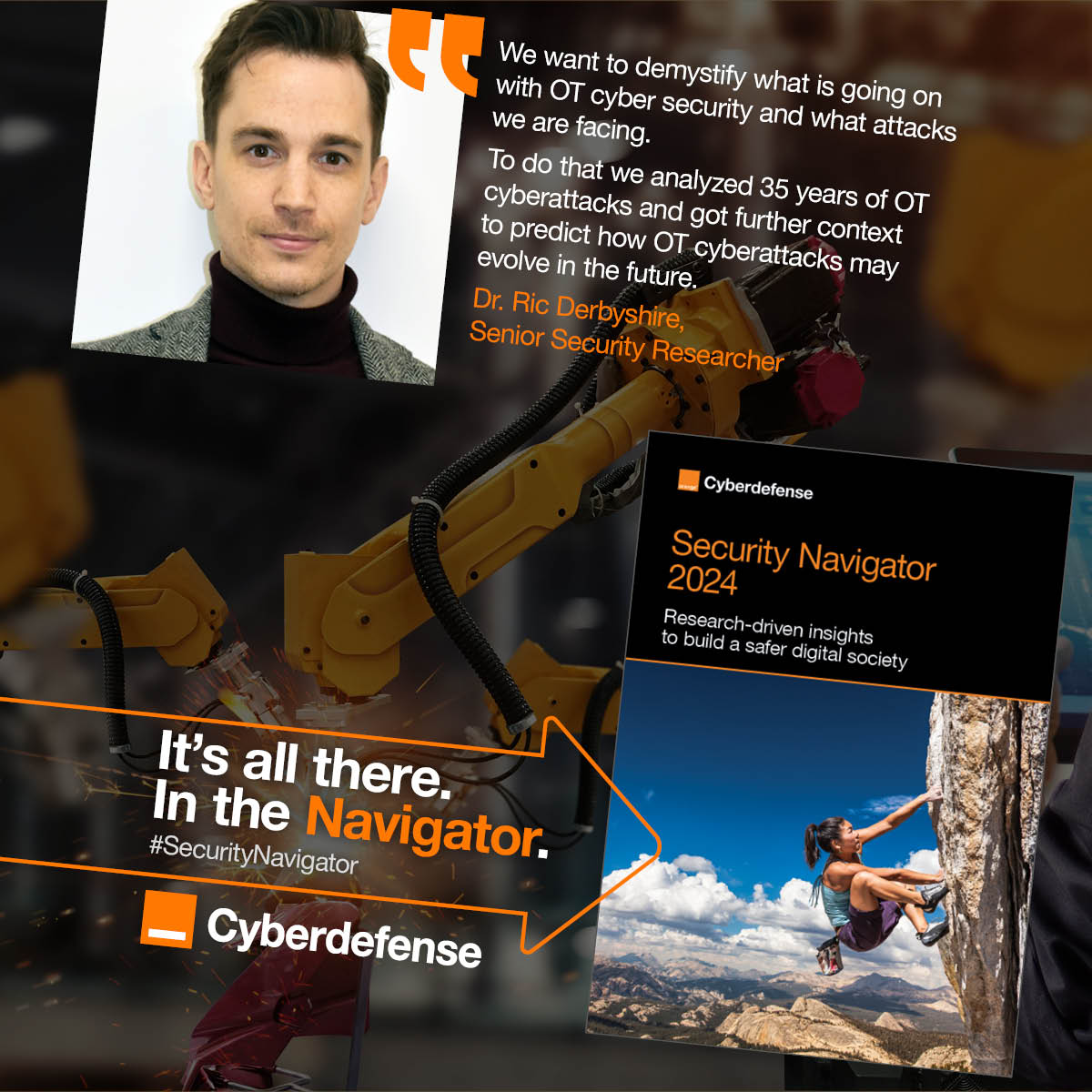
🔎🔒When you read reports about cyberattacks affecting #OperationalTechnology, it’s easy to assume every single one is sophisticated. But are OT environments really besieged by a constant barrage of complex cyberattacks? 🧐📙Find it out, get your copy: ow.ly/IjOA50R28yj
#CISOTraining "From classroom to control room! 🚀 See how Hemanth mastered OT security with Wazuh and Wireshark, turning knowledge into real-world expertise." #CyberSecurity #OperationalTechnology #OTSecurity #SCADASecurity #Wazuh #Wireshark #IndustrialCyberSecurity…
#CISOTraining How did Hemanth turn theory into real OT security skills? Discover the tools that changed his game! From mastering Wazuh to analyzing with Wireshark, this training bridged the gap between learning and real-world application." #CyberSecurity #OperationalTechnology…
🛠️ OT Security — Operational Technology protetta, industria al sicuro. . #OTSecurity #OperationalTechnology #SCADA #PLC #ITStudio #IndustrialSecurity #IDS #FirewallOT #ITsoluzioni #consulenteinformatico #massaecozzile #pistoia #montecatiniterme #studioinformaticodg




The Hidden Costs Of Legacy #OperationalTechnology (#OT) wateronline.com/doc/the-hidden… via @Stantec
Operational Technology (OT) connects your entire facility, enabling real-time monitoring, optimized automation, predictive maintenance, and enhanced safety. Turn data into actionable insights and make faster, smarter decisions for a future-ready industry. #OperationalTechnology…
#OperationalTechnology (OT) still makes much of the world go round. In his latest blog, @PhilMuncaster explores new guidance from the NCSC, which emphasises the vital first step to securing OT: visibility: isms.online/information-se…

Rockwell Automation launches SecureOT, a cybersecurity suite designed to improve industrial asset visibility and compliance within operational technology systems. #Cybersecurity #IndustrialSafety #OperationalTechnology #Security techday.com.au/story/rockwell…
Asia-Pacific Leads the Charge in Operational Technology Adoption Amid Smart Factory Boom psintelligence.blogspot.com/2025/11/operat… #operationaltechnology #smartfactory
What is Operational Technology (OT)? OT powers industrial systems including SCADA, DCS and IoT. Driving automation & real-time monitoring. Read our guide- senselearner.com/what-is-operat… #CyberSecurity #Senseacademy #operationaltechnology

🚀 We’re kicking off a new series: PreCrime Deep Dives Explore the application of pre-crime technology in operational technology (OT) environments ▶️ youtube.com/watch?si=Iqdpd… #OperationalTechnology #PreCrime #Predictive #Preemptive #Cybersecurity #CriticalInfrastructure

youtube.com
YouTube
PreCrime Deep Dive: The application of PreCrime in operational...
AI isn’t just entering critical infrastructure, it’s rewriting how it thinks. At @ADIPECOfficial 2025, our team engaged with leaders driving that shift, where LLM-powered “think engines” are moving beyond Enterprise IT into #OperationalTechnology, redefining automation, safety,…




AI isn’t just entering critical infrastructure, it’s rewriting how it thinks. At @ADIPECOfficial 2025, our team engaged with leaders driving that shift, where LLM-powered “think engines” are moving beyond Enterprise IT into #OperationalTechnology, redefining automation, safety,…




We recently released new joint guidance with our international partners to help organizations build a definitive record of their #OperationalTechnology (OT) environments – because if you can’t see it, you can’t defend it. Read more: cyber.gc.ca/en/news-events…

As we rush to connect everything, it's not just #IT systems & devices that become open to threats, but also our #OperationalTechnology that oversees industrial equipment. Discover the relationship between vulnerability & intelligence in #CyberSecurity. wartsi.ly/3LyBynB

An effective #OperationalTechnology #security strategy could prevent #CyberAttacks & mitigate their impact. It helps protect critical infrastructure & assets from #CyberThreats, including physical damage, data breaches & operational disruptions. wartsi.ly/3LyBynB

Our joint guidance on establishing and maintaining a comprehensive view of your #OperationalTechnology architecture remains a foundational element of OT cyber resilience. cyber.gc.ca/en/news-events…

🆕 È online il nuovo numero di Cybersecurity Trends n.03/2025, dedicato all’#OperationalTechnology Non perdere le interviste Vip a Gian Maria Fara, Andrea Granelli e Nicola Spagnuolo, Marco Di Luzio, Roberto Masiero e altro ancora. 👉 Scarica la tua copia! cybertrends.it/sfoglia-la-riv…

Michael and Sam are gearing up for OT.SEC.CON. with keynote speaker, Marco Ayala! Don’t miss this episode of HOU.SEC.CAST. – the HOU.SEC.CON. podcast on Apple, Spotify, Stitcher, or wherever you get your podcasts. buzzsprout.com/2215185/episod… #OperationalTechnology…

Critical infrastructure requires uncompromising security. With 82,000 miles of pipelines transporting 40% of the U.S. natural gas supply, Kinder Morgan, Inc. needed to strengthen and modernize access to its #DataCenter and #OperationalTechnology environments. That’s why they…

OT.SEC.CON. is now accepting speaker submissions! Head to accelevents.com/e/otseccon/spe… to submit your abstract. #OTSECCON #OperateandSecure #OperationalTechnology #CriticalInfrastructure #Cybersecurity #CFP #CallForPapers #Speakers

.@cyberconiq: A growing #risk of #cyberattacks on #operationaltechnology highlights the need to prepare for breaches that take down industrial systems. tinyurl.com/3wzkwxy2 #technology #cybersecurity #IT #OT #OTsecurity

Die Lücke zwischen IT und OT mit ganzheitlichem Netzwerk-Monitoring überbrücken #Ausfallsicherheit #NetzwerkMonitoring #OperationalTechnology #OTMonitoring #OTProtokolle @Paessler #SCADA netzpalaver.de/2025/07/15/die…

🔔 Mark April 16 in your calendar and join us and Stora Enso for an insightful webinar focused on #OTcybersecurity. Secure your spot today! Register here: hubs.la/Q02pM0qj0 #cybersecurity #operationaltechnology #OTsecurity #criticalinfrastructure

IT/OT convergence is the integration of #InformationTechnology (IT) systems with #OperationalTechnology (OT) systems. bit.ly/3JirnBi

#OperationalTechnology encompasses hardware and software capable of detecting or inducing alterations in industrial equipment, assets, and events directly. It highlights the technological and functional distinctions from traditional #IT systems. Read More 👇…

Ransomware Attacks Are Increasing— How Hackers Are Adapting cysecurity.news/2025/03/ransom… #2FA #Cybercrimes #OperationalTechnology

Meet Mandiant, now part of Google Cloud, at the @SecureWorld Manufacturing Virtual Conference on August 23. @ChrisSistrunk will discuss Incident Response for OT at 1pm ET. Register here: mndt.info/43U4yMj #Cybersecurity #OT #OperationalTechnology #ICS #ThreatIntelligence

#OperationalTechnology (OT) powers some of the UK’s most critical national infrastructure (#CNI), but the risk to OT systems is often overlooked. @PhilMuncaster outlines the perils - and financial impact - of neglecting OT risk: isms.online/cyber-security… #Cybersecurity

For 20+ years, @INL has been a world leader in #OperationalTechnology cybersecurity. We're dedicated to protecting our #CriticalInfrastructure through cutting-edge #cybersecurity, keeping the lights on and clean water flowing. 💡🚰 ➡️ inl.gov/national-secur… #DOENationalLabs

Discover how @Dragos secures #operationaltechnology with its powerful platform, built for #threathunting & #incidentresponse. Learn more about their #cybersecurity solutions on 8/8: carah.io/6d38ce

Something went wrong.
Something went wrong.
United States Trends
- 1. Paqueta 13.6K posts
- 2. Ole Miss 46.5K posts
- 3. Isak 36.2K posts
- 4. Wirtz 21K posts
- 5. #HardRockBet N/A
- 6. #AskFFT N/A
- 7. Ryan Silverfield 1,449 posts
- 8. Vidal 3,994 posts
- 9. Gakpo 20.4K posts
- 10. Good Sunday 77K posts
- 11. Golesh 4,636 posts
- 12. #WHULIV 13.8K posts
- 13. Neal 5,374 posts
- 14. #sundayvibes 6,359 posts
- 15. Lane Kiffin 55.3K posts
- 16. West Ham 7,896 posts
- 17. Saliba 18.4K posts
- 18. Dowdle 1,138 posts
- 19. Judkins 1,320 posts
- 20. Michael Wilson N/A