#registryanalysis search results

aumfor – automatic memory #forensics. goo.gl/fb/8x1jCt #digitalforensics #registryanalysis #dfir
giant_backdoor – #windows #backdoor diagnostic tool. goo.gl/fb/kcn4rs #registryanalysis #securitytools
#sandbox attacksurface analysis tools. goo.gl/fb/uKhHhp #registryanalysis #securitytools #memoryanalysis
Auditing tool for PI Security. goo.gl/fb/o2TjqW #firewall #framework #registryanalysis #securitytools
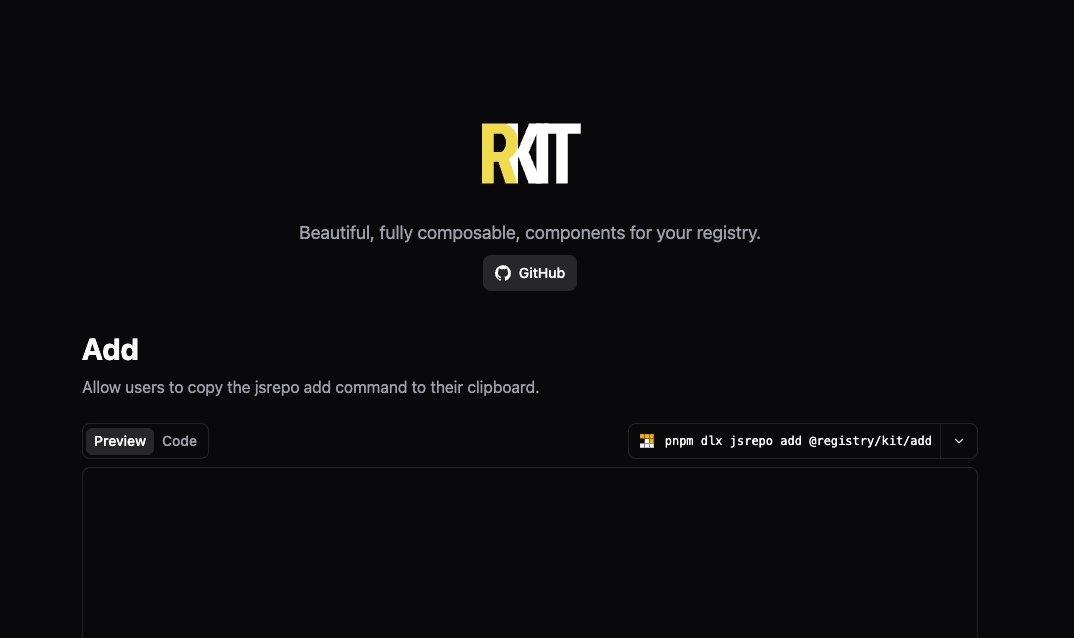
For @sveltejs users we've put together a few components to help you get your registry off the ground faster. These are beautiful, high quality, composable components that can be dropped into your project with a single command. Check them out at registry-kit.dev
Series on Windows registry security analysis and vulnerabilities: Part 1: googleprojectzero.blogspot.com/2024/04/the-wi… Part 2: googleprojectzero.blogspot.com/2024/04/the-wi… Part 3: googleprojectzero.blogspot.com/2024/06/the-wi… Credits Mateusz Jurczyk #windows #infosec
not even the registers are real. what you see as "registers" are just a particularly efficient way to serialize and compress the dataflow graph of what operations consume what operation's results. there is a dancing froth of indirection between the reg names and real flip-flops
There are actually *no* programming languages that express "how computers work"! Not even C. The operating system runs other programs 'between' your lines. CPUs execute both branches of ifs, and magically run multiple lines of your code at once. Your code is just a suggestion
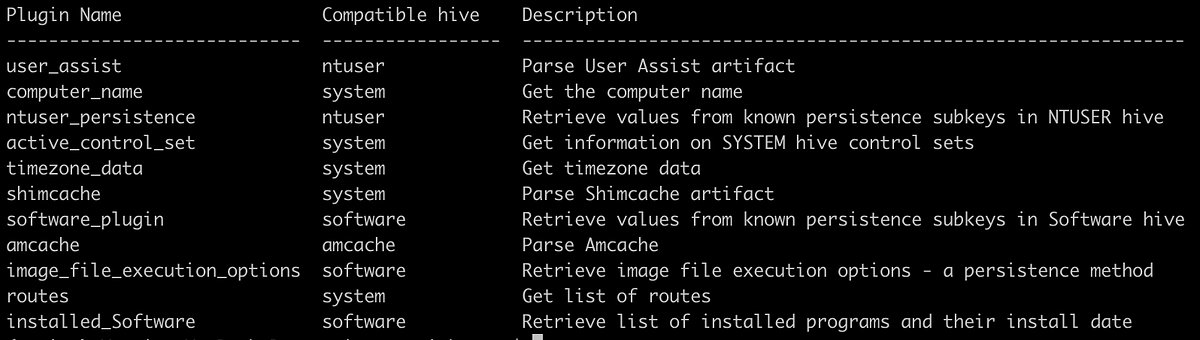
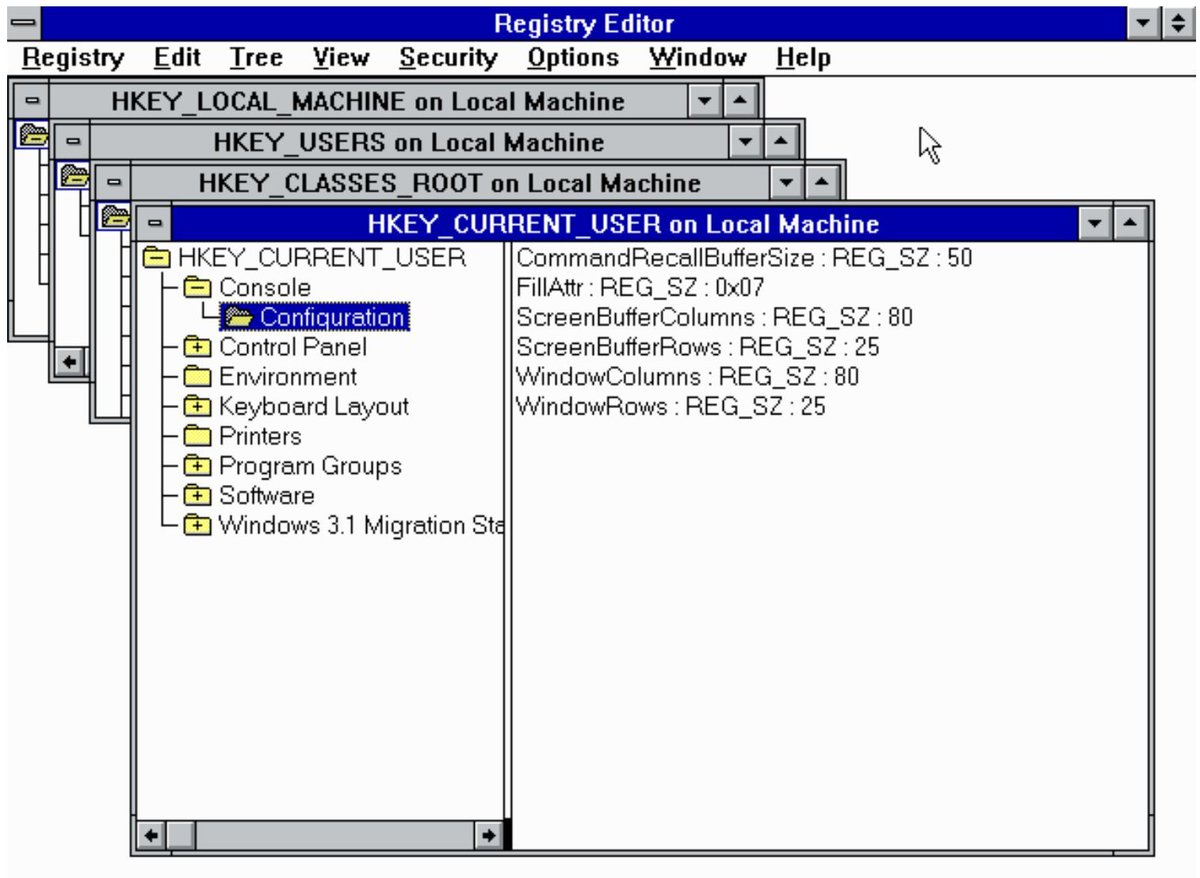
Windows Registry Analysis Cheat Sheet #DFIR #Forensics #IncidentResponse github.com/Ahmed-AL-Maghr…
Best of Computer Forensics Pagefile.sys hackingarticles.in/forensic-inves… Prefetch File hackingarticles.in/forensic-inves… Windows Registry Analysis hackingarticles.in/forensic-inves… Volatility Workbench hackingarticles.in/memory-forensi… #infosec #cybersecurity #cybersecuritytips #pentesting #redteam…




Best of Digital Forensics Pagefile.sys hackingarticles.in/forensic-inves… Prefetch File hackingarticles.in/forensic-inves… Windows Registry Analysis hackingarticles.in/forensic-inves… Volatility Workbench hackingarticles.in/memory-forensi… #infosec #cybersecurity #cybersecuritytips #pentesting #forensics #Digital




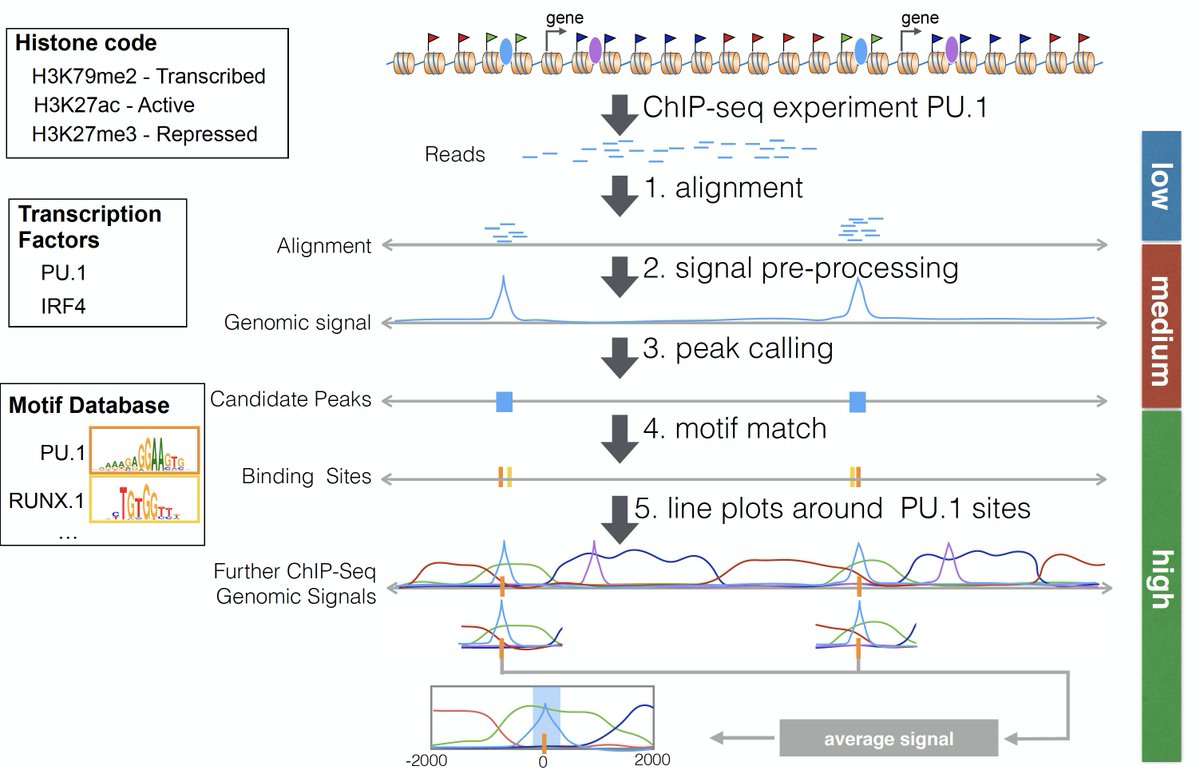
We are happy to share our manuscript describing the Regulatory Genomics Toolbox (RGT). RGT is a python framework for analysis of chromatin and regulatory genomics data as interval algebra, peak calling, motif matching and IO tinyurl.com/wfeccn4c
It's been a while since part 2 so here's part 3 of the HyperGuard analysis series: registers, intercepts, extents and more: windows-internals.com/hyperguard-par…

Script of the Day: "RegRecent.ps1" by MVP @guyrleech github.com/guyrleech/Gene… Easily find registry keys last modified within a given time/date range. Awesome when troubleshooting policy/app delivery #ConfigMgr #MSIntune #MEMPowered

Ever try to find out what EDR product is on a box but get burnt looking for it? Well not anymore... Checkout j3ss h1r3s's new tool Registry-Recon, designed to use reg query APIs to get the information you need! github.com/optiv/Registry… #netsec #CobaltStrike #redteam #EDR
Yale study shows limitations of applying artificial intelligence to registry databases - Yale School of Medicine Read more here: ift.tt/2OBwq70 #ArtificialIntelligence #AI #DataScience #100DaysOfCode #Python #MachineLearning #BigData #DeepLearning #NLP #Robots #IoT
Yale study shows limitations of applying artificial intelligence to registry databases - Yale School of Medicine Read more here: ift.tt/3esgM8H #ArtificialIntelligence #AI #DataScience #100DaysOfCode #Python #MachineLearning #BigData #DeepLearning #NLP #Robots #IoT
Very proud to release the first public version of RegRippy! A Python #forensics tool to extract useful data from Windows registry hives. #DFIR 📑 Get the code: github.com/airbus-cert/re… 🐍 Install the package: pypi.org/project/regrip… Contributions are more than welcome 👩💻👨💻
medium.com/dfir-dudes/reg… I'm releasing Regipy: an OS independent python library for parsing offline registry hives, with a lot of awesome features! #DFIR
My AV Analysis Cheat Sheet applied to AV logs can help detecting a breach in an early stage with low budget toolset nextron-systems.com/2018/09/08/ant… Related Sigma rules github.com/Neo23x0/sigma/… github.com/Neo23x0/sigma/… github.com/Neo23x0/sigma/… github.com/Neo23x0/sigma/… github.com/Neo23x0/sigma/…

aumfor – automatic memory #forensics. goo.gl/fb/8x1jCt #digitalforensics #registryanalysis #dfir
Something went wrong.
Something went wrong.
United States Trends
- 1. #GMMTV2026 2.72M posts
- 2. MILKLOVE BORN TO SHINE 433K posts
- 3. Good Tuesday 30K posts
- 4. #tuesdayvibe 2,228 posts
- 5. Mark Kelly 217K posts
- 6. WILLIAMEST MAGIC VIBES 58.9K posts
- 7. Chelsea 222K posts
- 8. MAGIC VIBES WITH JIMMYSEA 72.9K posts
- 9. JOSSGAWIN MAGIC VIBES 24.3K posts
- 10. TOP CALL 9,500 posts
- 11. Alan Dershowitz 3,339 posts
- 12. AI Alert 8,345 posts
- 13. #JoongDunk 109K posts
- 14. Check Analyze 2,524 posts
- 15. Naps 2,907 posts
- 16. Token Signal 8,758 posts
- 17. #ONEPIECE1167 8,671 posts
- 18. Barca 85.7K posts
- 19. Maddow 15.6K posts
- 20. Hegseth 100K posts