#secureprogramming نتائج البحث
2025 年 10 月 のマイクロソフト月例セキュリティ更新プログラムを公開しました。既定では自動で更新されます。更新管理を行っている組織向けに、概要をブログで公開しています。ご参照の上、早期に更新の展開をお願いします。 #セキュリティ #更新プログラム #マイクロソフト…

When you're writing code, sometimes you may not even know it's broken or vulnerable until something bad happens. So Manish wrote this guide to help you identify common issues that'll make your code less safe. He talks about missing input validation, poor error handling, no rate…

🚨 Nation-state affiliated threat actors have compromised F5’s systems & downloaded portions of its BIG-IP source code—posing serious risk to FCEB agencies. Follow the guidance in ED 26-01 immediately to protect systems from potential exploits. 🔗 go.dhs.gov/isY
🚨 ALERT: Hackers are hiding malware in Ethereum smart contracts, disguising malicious traffic as normal blockchain activity, ReversingLabs reports.

You might be wondering, what security measures is @idOS_network implementing to make their one-fits-all KYC concept safe ? Let me explain to you like the 5-yr old you are 👇 Data Encryption on a personal level So idOS has a bunch of data of you and imagine some hacker breaks…

This software engineer was nearly hacked by a coding interview. I've never seen this attack channel before. Be careful out there, especially vibe coders.

Our latest post breaks down how to secure AI coded apps in the age of vibe coding. 🔒 📖 Read here: blog.pythagora.ai/how-to-secure-…

say hello to Sandboxes ⚡ run any command or process, expose URLs, make file operations, stream real-time logs and directly execute python & javascript! spin up secure & scalable sandboxes with a simple SDK sandbox.cloudflare.com

He pushed the latest build, and the scanner lit up. Another round of fixes. Another late night. But the issue wasn’t the tool. It was how we wrote the code. Real tools. Real VMs. Real results. Don’t just scan code. Train the people who write it. 🧩 #DevSecOps #SecureSoftware


The world is changing. Security breaches are growing every day. KYC can’t solve this only @idOS_network can. Either become history with security flaws, or secure your future.

building apps is easy; securing them is the hard part. > this is the field guide for devs who want to defend against real-world attacks. > a must-read if you ship code to the web

> LOG_004 //⚠️ SYSTEM FAILURE ⚠️ > POWER SPIKE DETECTED > CONTAINMENT = BREACHED > ⚠️ D̶A̶N̶G̶E̶R̶.̶⚠️ ̶D̶A̶N̶G̶E̶R̶.̶⚠️ ̶D̶A̶N̶G̶E̶R̶.̶⚠️ > SYSTEM OVERRIDE >> ☣️ START PERP PROTOCOL ☣️ >ACTION REQUIRED: 3NG4G3 P05T RT F0R $PERP P4YM3/\/T

Excellent free book teaching security hardening for compilers, linkers, JITs and assemblers Low-Level Software Security for Compiler Developers: llsoftsec.github.io/llsoftsecbook/ #cybersecurity #compilers


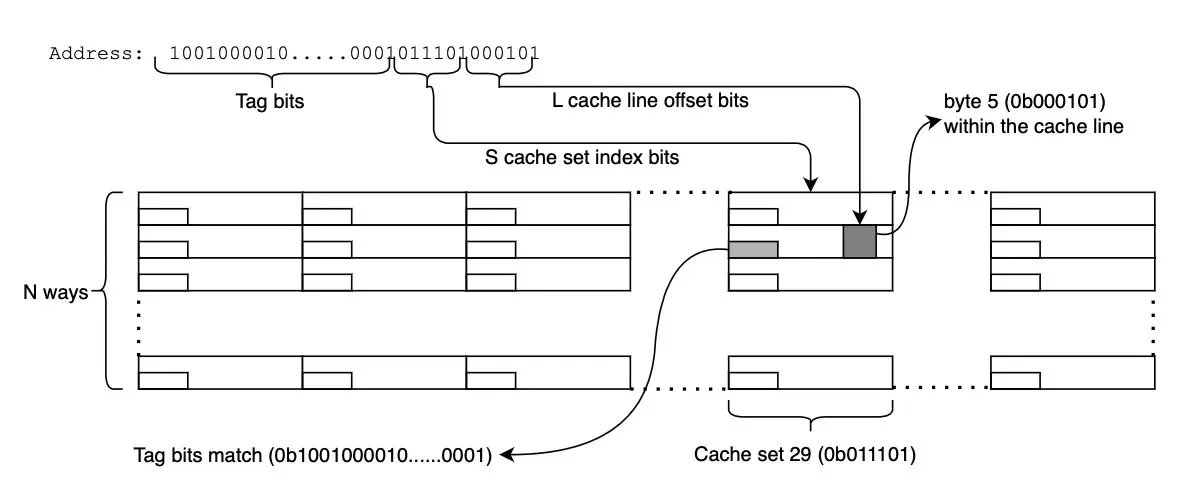
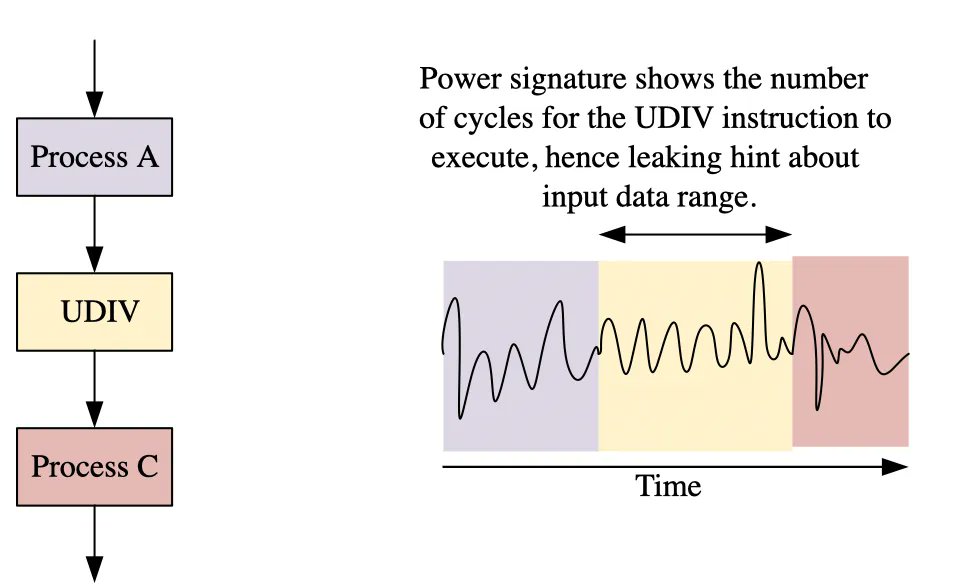
4/ Here's what frustrates me: We have the technology to prevent these incidents. ✅ Real-time security scanning ✅ Automated test generation ✅ Mutation testing Yet the industry still treats security as something you bolt on AFTER development.
If you're building AI apps, you'll want to make sure they're secure. And in this course, Robert teaches you how to build security right into the apps as you go. You'll learn about how securing AI apps is different from regular apps, how to identify potential weaknesses, how to…

Good morning friends happy mornings Today I want to talk a little about @idOS_network approach to data security Data protection isn't just about encryption what matters is how, where, and with whom it is shared. In our system, every file is protected with advanced AES 256…
Can I get a GM☕️ @idOS_network Reply guys in the building, check this out quickly ☟ ☟ ☟ ☟ ☟ ☟ ☟ ☟ ☟ ☟ ☟ ☟ ☟ ☟ ☟ In idOS, instead of plaintext data, sensitive data such as credentials are encrypted on the user's device before being sent. And so, once data leaves…

How do we design secure and safe APIs? The rise in API-related security breaches highlights the necessity for robust API security. Let’s look at 12 essential tips for improving API security: 𝗥𝗮𝘁𝗲 𝗹𝗶𝗺𝗶𝘁𝗶𝗻𝗴 𝗮𝗻𝗱 𝘁𝗵𝗿𝗼𝘁𝘁𝗹𝗶𝗻𝗴 ↳ Throttling and rate limiting…

🔆 Spotlight on The Citadel Programming Lab! This virtual laboratory was introduced in 2021 by Manuel Maarek (Heriot-Watt University) designed to teach #SecureProgramming in #CyberSecurity. Check this resource out and more on our website! 🔗 buff.ly/f6cZ3DA #CyBOK

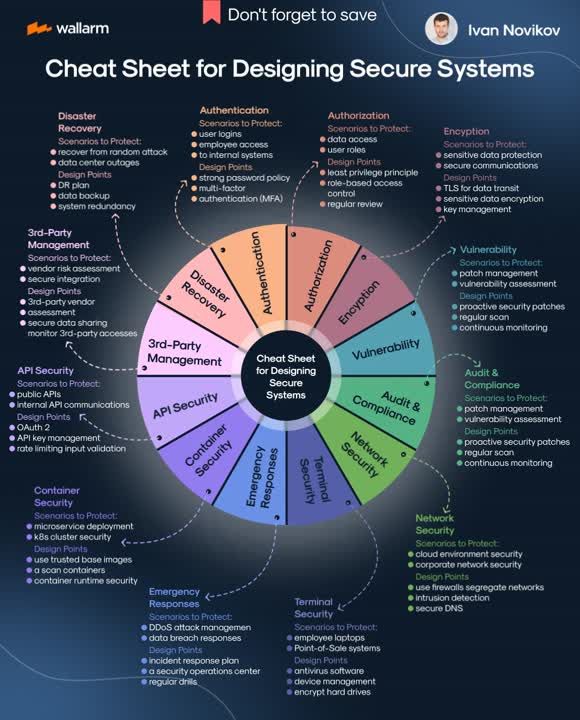
#Infographic: Here's a cheat sheet for designing secure programs! Source Ivan Novikov #SecureProgramming #Cybersecurity #SoftwareDevelopment #TechSafety #DataProtection #SecureCode #Programmers cc: @PawlowskiMario @pierrepinna @sonu_monika
Secure your code like a pro with The Essential Guide to Secure Programming! Learn best practices, avoid common vulnerabilities, and write safer code. Grab your copy today 👉 store.expliot.io/products/the-e… #SecureProgramming #Coding #Cybersecurity #EXPLIoT
"Bypassing airport security via SQL injection" (ian.sh/tsa) -> Thats why Secure Programming of Web Applications - Developers and TPMs (hissenit.com/it-training-en…) is so important! #security #securecode #secureprogramming
Online Course: Secure Programming of Web Applications hissenit.com/train #security #securecode #secureprogramming #awareness
Dankzij de Secure Programming cursus heb ik geleerd hoe ik veilige applicaties kan ontwikkelen.’ Ontdek meer en begin nu. #SecureProgramming #CyberSecurity #SecurityTraining #DevSecOps #CodeSafely #ITTraining officeelearningmenu.nl/nl/secure-prog…

Secure your software development with our Secure Programming course. Learn the best practices for writing secure code! #SecureProgramming #CyberSecurity #SoftwareSecurity #SafeCoding #SecurityTraining #CodeSafely #ApplicationSecurity #DevSecOps officeelearningmenu.nl/nl/secure-prog…

Secure Programming of Web Applications – for Developers and Technical Project Managers hissenit.com/it-training-en… #secureprogramming #webappsec #security #courses
Imagine a future where trust and security are built into every line of code. #Blockchain #SecureProgramming

The use of security testing tools to identify and fix vulnerabilities. #secureprogramming #trends
The adoption of secure coding practices by developers. #secureprogramming #trends
🔆 Spotlight on The Citadel Programming Lab! This virtual laboratory was introduced in 2021 by Manuel Maarek (Heriot-Watt University) designed to teach #SecureProgramming in #CyberSecurity. Check this resource out and more on our website! 🔗 buff.ly/f6cZ3DA #CyBOK

@richardmhope OMG, Help! Assignment due the day before the exam, then Exam? Is this even legit? #SecureProgramming

It is great to meet with the Ada Community again this year and be hosted by GE in Warsaw. We are proud to support #AdaEurope2019 ! #ada #secureprogramming #programminglanguage



Nice seeing @jeanqasaur (who came on the show) featured on @techreview 👩🏻💻👍💡🔐#SecureProgramming #EmTechDigital

We are now presenting our Product Update at #AdaCoreTechDays . Learn what's new about GNATPro, CodePeer, SPARK Pro and QGen. #SecureProgramming #SafeAndSecureSoftware #Ada #SPARK

The 3 least secure programming languages buff.ly/2W7uHoo #security #appsec #secureprogramming #softwaredevelopment

Contact us to discuss secure coding training for your development team #secureprogramming #cybersecurity

#Infographic: Here's a cheat sheet for designing secure programs! Source Ivan Novikov #SecureProgramming #Cybersecurity #SoftwareDevelopment #TechSafety #DataProtection #SecureCode #Programmers cc: @PawlowskiMario @pierrepinna @sonu_monika

Imagine a future where trust and security are built into every line of code. #Blockchain #SecureProgramming

#secureprogramming #itsec Sichere Programmierung von Web-Anwendungen - SQL Code Injection frankhissen.de/sichere-progra…

Where would you implement user input validation? Client side, server side or both? #quiz #secureprogramming #training #sharingknowledge #securacademy #CyberSecurityMonth

SophistiNET.com 4sale #internetofthings #bigdata #secureprogramming domainomy.com/portfolio/soph… @internet @igcbp

It's out on @seradio now! @RCS, author of Effective C, The CERT C Coding Standard and Secure Coding in C and C++, discusses the top 5 security issues and the tools and techniques you can employ to write secure code in C. se-radio.net/2022/01/episod… #secureprogramming #seradio

EXCERPT: Well-known educator Matt Bishop discusses informal techniques for writing programs that enforce security policies. ow.ly/YgeV50u14Kq #Security #SecureCode #SecureProgramming

Rafael, muito obrigado! :)👨🎓 Obtenha também sua certificação internacional! Acesse: news.pmgacademy.com/secureprogramm… #secureprogramming #soufã #cursooficial #ti #technology #depoimentos #gestãodeti #governançadeti #itsm #certificacaointerrnacional #cursooficial #peoplecert #exin

CYB5CPR Secure Programming Assignment Help and Solution, La Trobe University - Assessment Writing Service expertsmind.com/library/cyb5cp… #CYB5CPR #SecureProgramming #AssignmentHelp #Solution #LaTrobeUniversity #AssessmentWritingService #Australia

RT @ryancsmith2222: The 3 least secure programming languages buff.ly/2W7uHoo #security #appsec #secureprogramming #softwaredevelopment

Dankzij de Secure Programming cursus heb ik geleerd hoe ik veilige applicaties kan ontwikkelen.’ Ontdek meer en begin nu. #SecureProgramming #CyberSecurity #SecurityTraining #DevSecOps #CodeSafely #ITTraining officeelearningmenu.nl/nl/secure-prog…

Something went wrong.
Something went wrong.
United States Trends
- 1. Ace Frehley 52.3K posts
- 2. Aaron Rodgers 11.5K posts
- 3. Bengals 29.6K posts
- 4. #911onABC 7,824 posts
- 5. #HereWeGo 5,741 posts
- 6. Bolton 154K posts
- 7. Cuomo 40.8K posts
- 8. Asheville 10.3K posts
- 9. RIP Spaceman 1,795 posts
- 10. athena 11.3K posts
- 11. #TNFonPrime 1,929 posts
- 12. Glasnow 3,873 posts
- 13. #NYCMayoralDebate N/A
- 14. Space Ace 1,948 posts
- 15. Tommy Edman 1,053 posts
- 16. Sliwa 16.6K posts
- 17. Uribe 32.3K posts
- 18. New York Groove N/A
- 19. #PITvsCIN 1,450 posts
- 20. Jonnu Smith 1,466 posts








































