#securityanalytics search results
Logs become vectors. Patterns become insights. StarTree's Chad Meley breaks down how vector embeddings enable real-time threat detection—no more waiting for alerts to fail. #ThreatDetection #SecurityAnalytics #AI #RealTimeAnalytics
Check out our live analytics dashboard preview: See exactly what enterprise customers get with SecurePassPro Analytics. No other password generator offers this level of business intelligence. Try it free securepasspro.co #PasswordGenerator #SecurityAnalytics
securepasspro.co
SecurePass Pro: The Password Manager for Modern Teams
Generate cryptographically secure passwords instantly with 256-bit encryption. Includes JavaScript SDK, REST API, and enterprise-grade security.
Live from @RSAConference! It's been a packed two days with demos, lighting talks, and speaking sessions on AI-driven security analytics, Elastic Attack Discovery, open security, and so much more. Check back tomorrow as we wrap up with day 3 highlights. #RSAC #securityanalytics




👀Take a look at our PCI 4.0 Ready SIEM (GM Sectec Security Analytics+) powered by @SumoLogic. 🚀Learn how GM Sectec can help to accelerate your journey to PCI DSS 4.0 Readiness with Requirement 10 Compliance. #GMsectec #PCIDSS #SecurityAnalytics
💔 Swipe left on siloed solutions and manual #incidentresponse 💜 Match with Secureworks and use a combination of #securityanalytics and human intelligence to respond to the rising tide of #cyberthreats. Learn more about the value of Secureworks: dell.to/3jU8NGJ
.@CarDekho's web traffic was growing & they were seeking a service provider who could improve responsiveness on their website. We partnered with them to enhance their #securityanalytics & maintain up-to-date security postures. Read more: bit.ly/3Ek8SeT #NTTIndia
Learn how Sumo Logic Cloud Security Analytics can help you stay ahead of your changing attack surface with increased threat visibility and deep #security context from use-case-driven queries, dashboards and alerts. #securityanalytics #poweroflogs
🛡️To enhance #threatdetection and security visibility, security teams use #securityanalytics techniques and various #CTI frameworks. 💡 Explore key frameworks in our latest blog post: socradar.io/main-analytica… #cyberthreatintelligence #securityframeworks #cyberthreats

Are your patches truly secure? Worried about shadow IT and high-risk accounts? Join our webinar to discover how AI-powered analytics can close these critical gaps in your cyberdefense: zurl.co/tevG #SecurityAnalytics #Cybersecurity
Are you ready for cybersecurity month? Join us as we get the ball rolling with our comprehensive webinar on five warning signs that point to vulnerable security protocols. mnge.it/DFA #SecurityAnalytics #Cybersecurity
Plagued with cyber fatigue and struggling to implement a robust security strategy? Join our webinar to effortlessly catch signs of vulnerable security protocols using comprehensive AI-driven security analytics. mnge.it/DFA #SecurityAnalytics #Cybersecurity

🤝 Meet Jose Barajas, our Global Sales Engineering Director at AttackIQ. A wizard in reverse-engineering #Malware & a sage in #SecurityAnalytics, he's pioneering the enhancement of security control efficacy. Learn from a seasoned pro. ⤵️ bit.ly/3ZIksJ2 #Cybersecurity

Stop spending hours fine-tuning your security strategy. Here are powerful security reports you can deploy over your data in seconds, and eliminate weeks of painstaking analysis to improve cyber resilience. zurl.co/wkK1 #SecurityAnalytics #cybersecurity

Are shadow IT practices causing security incidents? Are new devices unwittingly impacting your security posture? How effective are your patches? Discover answers in seconds, and fortify your organization's security. Read now: zurl.co/7bbT #SecurityAnalytics

Can your cybersecurity strategy defend against what's lurking beneath the surface? Don’t let unseen threats compromise your security posture. Join our webinar to empower your defenses with AI-powered analytics. Register now: zurl.co/iZKA #SecurityAnalytics

🌐🔒 Take charge of your multi-cloud security posture with #OasisDefender's comprehensive security analytics and reporting. #SecurityAnalytics #InformedDecisions #ContinuousImprovement #GenerativeAI #OpenAI #Cybersecurity #CloudSecurity #AI #Software #innovation #aiart #Cloud
What if you could secure operations and streamline cybersecurity strategies without breaking a sweat? Grab this free report bundle and visualize powerful security KPIs to elevate security practices in seconds. Read now: zurl.co/Gg5y #SecurityAnalytics

Is your cybersecurity strategy reaching its full potential? Discover four powerful ways to close critical gaps with AI-driven analytics in our upcoming webinar. Register now and start building a resilient cyber defense: zurl.co/IHaU #SecurityAnalytics

With the release of ChatGPT, we are seeing increased excitement around the application of AI technologies to enable secure outcomes, with the greatest interest in #generativeAI. Read IDC’s latest blog. bit.ly/3Ol3YDf #AI #securityanalytics

Leverage Security Guard App’s real-time analytics to monitor performance, identify trends, and make smarter operational decisions. 👉 Learn more: securityguard.app #SecurityGuardApp #SecurityAnalytics #DataDrivenDecisions #SecurityManagementSoftware #GuardPerformance
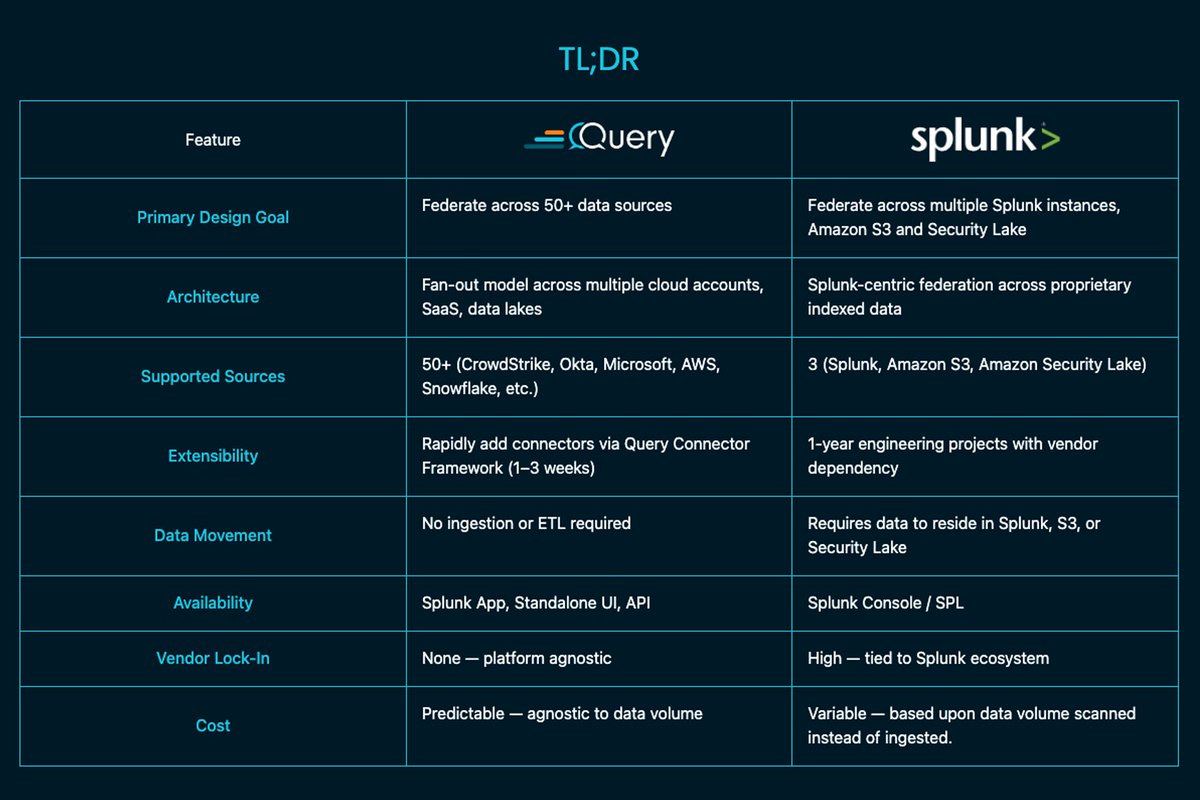
Evaluating Splunk Federated Search? This quick TL;DR shows how Query’s federated-first approach compares side-by-side with Splunk’s model. Cut through the noise and see the difference: hubs.li/Q03NWF210 #FederatedSearch #SecurityAnalytics #SIEM #CyberSecurity #DataOps
Check out our live analytics dashboard preview: See exactly what enterprise customers get with SecurePassPro Analytics. No other password generator offers this level of business intelligence. Try it free securepasspro.co #PasswordGenerator #SecurityAnalytics
securepasspro.co
SecurePass Pro: The Password Manager for Modern Teams
Generate cryptographically secure passwords instantly with 256-bit encryption. Includes JavaScript SDK, REST API, and enterprise-grade security.
🔍 Log aggregation without correlation is just expensive data hoarding. Context turns noise into actionable intelligence. #LogManagement #SIEM #SecurityAnalytics #ThreatDetection #SOC
Your firewall sees traffic. hawkshield.ai sees the truth. 🔍 Real-time analytics ⏱️ Instant anomaly detection ⚠️ Know who accessed what, and why #DataSecurity #ThreatDetection #SecurityAnalytics #HawkShield
See why Gurucul has become a core part of Hornblower’s security strategy. CISO & CTO Stewart Alpert shares what truly matters when it comes to daily results. go1.gurucul.com/Hornblower_Cor… #CyberSecurity #SIEM #SecurityAnalytics #CISO #SOC

What made Gurucul stand out from other vendors? Hornblower’s CISO explains how Gurucul delivered unmatched insider threat detection and actionable insights. go1.gurucul.com/Hornblower_Cor… #InsiderThreatDetection #SIEM #SecurityAnalytics #CyberSecurity #CISO

🤔 Too many logs, not enough clarity? See how Sumo Logic’s Cloud SIEM turns raw log data into actionable security insights—fast. Watch now 👉 ow.ly/O6qo50Ws0vN #CloudSIEM #SecurityAnalytics #SumoLogic #Cybersecurity #LogAnalytics
youtube.com
YouTube
Micro Lesson: How are Insights Generated in Cloud SIEM?
@AskPerplexity How have technological advancements and data-driven strategies contributed to enhancing security during Youm-e-Ashura, and what trends have emerged in provincial coordination efforts? #SecurityAnalytics #YoumeAshura
Elastic recognised as a Leader in Forrester Wave Security Analytics 2025, excelling in 14 criteria such as AI and malware protection. #CyberSecurity #SecurityAnalytics #ForresterWave #AI #MalwareProtection techday.com.au/story/elastic-…
securitybrief.com.au
Elastic named Leader in Forrester Wave for security analytics 2025
Elastic has been named a Leader in Forrester Wave Security Analytics 2025, achieving top scores in 14 criteria including AI and malware protection.
AI-driven security analytics will enable real-time threat hunting, reducing dwell time by 50% by 2023-2024. #securityanalytics #AIsecurity #threathunting #dwelltime #realtimeanalysis #AI

In continuation of our @Exabeam #BestSwag game - I present a pen that’s a torch that’s five screwdrivers. Which you might get if you come and talk to me about our #NewScaleSIEM and #SecurityAnalytics at #Leap23 - stand H4.C50

Live from @RSAConference! It's been a packed two days with demos, lighting talks, and speaking sessions on AI-driven security analytics, Elastic Attack Discovery, open security, and so much more. Check back tomorrow as we wrap up with day 3 highlights. #RSAC #securityanalytics




#ThreatActors have learned to hide in noise, which is why we’re adding our newest expansion to Taegis XDR: Secureworks Tactic Graphs. Learn more about the new feature. #Cybercrime #SecurityAnalytics #IworkforSecureworks bit.ly/3WYsafE

Did you know that over 700,000 hospital patients, visitors, and staff are screened daily with Evolv Express®? Want to learn more? Check out our healthcare page: hubs.li/Q03h_FvB0 #DataDrivenSecurity #EvolvExpress #SecurityAnalytics #Healthcare #NurseSafety

🛡️To enhance #threatdetection and security visibility, security teams use #securityanalytics techniques and various #CTI frameworks. 💡 Explore key frameworks in our latest blog post: socradar.io/main-analytica… #cyberthreatintelligence #securityframeworks #cyberthreats

Join us June 20th as we discuss some of the unique challenges security pros face on a daily basis and how they’re using cloud-native security log analytics. databreachtoday.com/webinars/live-… #poweroflogs #securityanalytics @DaToTweet @ISMGCorp @SoSafeSecurity

#ThreatActors have learned to hide in noise, which is why we’re adding our newest expansion to Taegis XDR: Secureworks Tactic Graphs. Learn more about the new feature. #Cybercrime #SecurityAnalytics #IworkforSecureworks bit.ly/3WNOh98

Data-driven security starts with visibility. Safetrust Credential Manager provides detailed reports on credential usage, access trends, and security events—empowering your team to make smarter, faster decisions. #SecurityAnalytics #DataDriven #AccessControl

🤝 Meet Jose Barajas, our Global Sales Engineering Director at AttackIQ. A wizard in reverse-engineering #Malware & a sage in #SecurityAnalytics, he's pioneering the enhancement of security control efficacy. Learn from a seasoned pro. ⤵️ bit.ly/3ZIksJ2 #Cybersecurity

#ThreatActors have learned to hide in noise, which is why we’re adding our newest expansion to Taegis XDR: Secureworks Tactic Graphs. Learn more about the new feature. #Cybercrime #SecurityAnalytics #IworkforSecureworks #Secureworks bit.ly/3IjHgIH

Join us as we examine the mechanisms cybercriminals use to exploit retail stores and platforms and what can be done to thwart threats and leave cyber criminals on the shelf. sans.org/webcasts/is-re… #poweroflogs #securityanalytics @awscloud

💯🌟 @ReliaQuest Adds AI Capabilities to its GreyMatter Intelligent Analysis Solution — AI integration leads to reduction of up to 90% in meantime to resolve security incidents: reliaquest.com/news-and-press… ————— #Cybersecurity #MachineLearning #SecurityAnalytics #BigData #DataScience
Are your patches truly secure? Worried about shadow IT and high-risk accounts? Join our webinar to discover how AI-powered analytics can close these critical gaps in your cyberdefense: zurl.co/tevG #SecurityAnalytics #Cybersecurity

Evaluating Splunk Federated Search? This quick TL;DR shows how Query’s federated-first approach compares side-by-side with Splunk’s model. Cut through the noise and see the difference: hubs.li/Q03NWF210 #FederatedSearch #SecurityAnalytics #SIEM #CyberSecurity #DataOps

#ThreatActors have learned to hide in noise, which is why we’re adding our newest expansion to Taegis XDR: Secureworks Tactic Graphs. Learn more about the new feature: dell.to/3Qe7XAy #Cybercrime #SecurityAnalytics

With the release of ChatGPT, we are seeing increased excitement around the application of AI technologies to enable secure outcomes, with the greatest interest in #generativeAI. Read IDC’s latest blog. bit.ly/3Ol3YDf #AI #securityanalytics

The age of Security Analytics, Video Analytics and VCA #security #Ipsotek #securityanalytics #vca #VideoAnalytics @PittockJon Read more here: securitybuyer.com/the-age-of-sec…
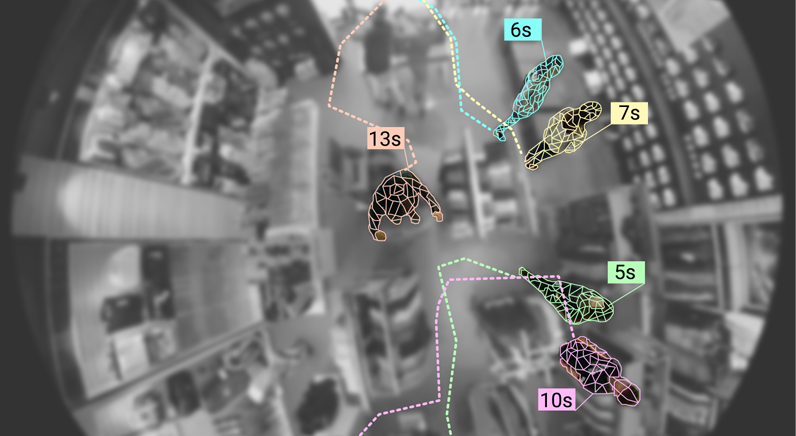
SPEAKING SESSION ANNOUNCEMENT! "Rules Writers and Threat Hunters in the Age of AI" by @EricZietlow , from Deep Tempo When: April 28, 2025 | 3:30 PM | Main Track #HackTheBay #ThreatHunting #SecurityAnalytics #LogAnalysis #LLM #AI #AnomalyDetection #SFSecurityWeek #RSA

Did you know that a single, purpose-built security platform makes it easier for teams to address security challenges with limited staff? sumologic.com/brief/right-si… #poweroflogs #securityanalytics

Something went wrong.
Something went wrong.
United States Trends
- 1. #SpotifyWrapped 114K posts
- 2. Chris Paul 20.8K posts
- 3. Clippers 30.9K posts
- 4. #NSD26 14.8K posts
- 5. Good Wednesday 34.2K posts
- 6. $MSFT 12.8K posts
- 7. #WednesdayMotivation 3,936 posts
- 8. National Signing Day 4,996 posts
- 9. #TierraDeAmorYSoberanía 1,801 posts
- 10. Hump Day 13.6K posts
- 11. GreetEat Corp. N/A
- 12. Nashville 32.4K posts
- 13. Fisherman 12.4K posts
- 14. Welcome Home 18K posts
- 15. Elden Campbell 1,485 posts
- 16. $CAPR N/A
- 17. HERE I COME 34.9K posts
- 18. Happy Hump 9,111 posts
- 19. Somalis 107K posts
- 20. #Wednesdayvibe 2,157 posts