#sourcecodeanalysis search results
Day 26/100: Evaluating Eclipse PMD plug-in for source code analysis, what can help us to code better. #SourceCodeAnalysis #codeanalysis #100DaysOfCode

Ever wonder how frequently different C/C++ token types are used? Wonder no more! #SemiUsefulVisualizations #SourceCodeAnalysis

Most breaches occur due to weak protection in software and systems within organizations. Is your source code safe or not? معظم الأختراقات تحدث بسبب ضعف الحمايه في البرمجيات والأنظمه داخل المؤسسات. هل الكود المصدري الخاص بك آمن أم لا ؟ #sourcecodeanalysis #programmers

Looking for #SecuritySolution that applies #SourceCodeAnalysis algorithm for maximumAccuracy?bit.ly/1TKkEge

@SumaSoftPvtLtd explains why #SourceCodeAnalysis is one of the most preferred security measures. Read More - ow.ly/ON2Z30bwQwa

🔍 Secure code review is crucial for identifying vulnerabilities in applications! Whether manual or automated, it plays a vital role in ensuring robust cybersecurity. Enhance your defenses with thorough #SourceCodeAnalysis & #Pentesting. 🌐bit.ly/3kuavyN #TechSecurity

I'm hooked on source code analysis! 😄✨ I've created code to extract the locations where specific methods are called, imported from a specified module! 🔍💻 Check it out below ⬇️ github.com/Ayato-kosaka/s… #SourceCodeAnalysis #TypeScript #Programming #CodeAnalysis #Development

#SumaSoft with #Checkmarx jointly offers #SourceCodeAnalysis solutions to various MNC's.. ow.ly/7xDZ300Q4sG

67% of commercial apps have vulnerabilities. Does yours? Let Suma Soft do a source code analysis for you #appsecurity #sourcecodeanalysis - ow.ly/o6RJ30jdkge

#ThursdayThoughts 5 Benefits of Secure Source Code Analysis for Businesses- goo.gl/ZRGYkR #CyberSecurity #SourceCodeAnalysis

Is your application using 3rd party components? Reduce risk from third-party components, remediate vulnerabilities and ensure license compliance with @Kiuwan Insights. Get the data sheet: #sca #sourcecodeanalysis #codesecurity buff.ly/3rRwKOx

Reservoir's R-Check SCA tool is used by #DoD's JTNC to verify radio waveforms. Our partner NordiaSoft has a white paper on SCA. R-Check SCA: reservoir.com/product/r-chec… SCA white paper: nordiasoft.com/knowledge-cent… #softwaredefinedradio #sourcecodeanalysis

Shocking Video Altered: Source Code Reveals The Truth #VideoManipulation #SourceCodeAnalysis #Conspiracy #DigitalForensics #TruthRevealed #VideoEditing #HiddenTruth #Investigation #DigitalSecrets #BreakingNews
Source code analysis is not just for developers—it's a crucial part of your security strategy. Let Lean Security find and fix vulnerabilities at the code level. #CodeSecurity #SourceCodeAnalysis Here are three ways you can stay secure on MMO games online: t.ly/2bVTt

In our latest series, you'll identify different ways a stack overflow vulnerability can be present in source code and prove that they can be used to exploit a program. Don't have a license? Book a demo👉 hubs.ly/Q016fxXw0 #redteam #sourcecodeanalysis #stackoverflow

How To Lean Away From Lagging Indicators In Application Security bit.ly/46BWr8w #ApplicationSecurity #PenetrationTesting #SourceCodeAnalysis #Software #SDLC #vulnerabilities #AttackSolutions

The Repeat Offenders: Characterizing and Predicting Extremely Bug-Prone Source Methods. arxiv.org/abs/2511.22726
if you want to go deeper into source code review, check out the book: The Art of Software Security Assessment: Identifying and Preventing Software Vulnerabilities
2. Compiler Design 🎬 Source Code (2011) ➡ Shows layers of execution, abstraction, and interpretation like a program runtime. youtu.be/1HCsSOuDS7Y?si…

youtube.com
YouTube
SOURCE CODE - Trailer - Starring Jake Gyllenhaal
3/8 18 Advanced Analysis Options including: Hidden string extraction from packed regions Entry point analysis to find real malicious code Entropy visualization for packed vs unpacked areas Anti-analysis technique detection (debuggers, VMs, sandboxes) #DigitalForensics #RE
An open source static code analysis tool for finding security issues : - github.com/opengrep/openg… #infosec #cybersec #bugbountytips
static code analysis for finding bugs and enforcing code standards across 30+ languages

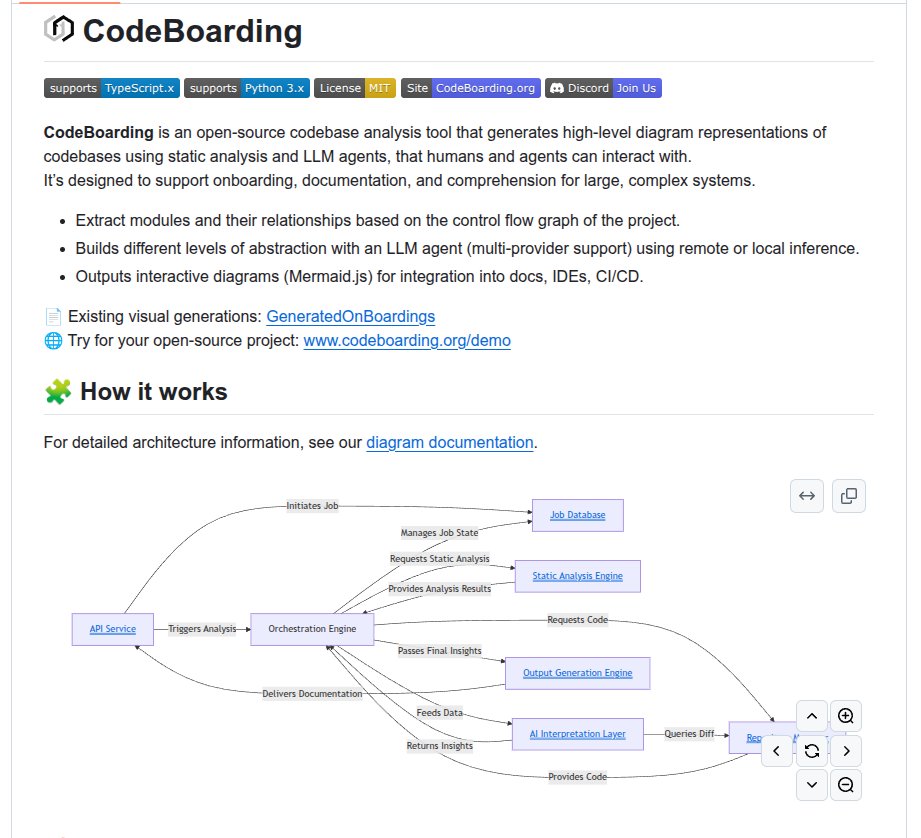
👨🔧 Github: open-source codebase analysis tool that generates high-level diagram representations of codebases using static analysis and LLM agents, that humans and agents can interact with. Extract modules and their relationships based on the control flow graph of the project.…
Shocking Video Altered: Source Code Reveals The Truth #VideoManipulation #SourceCodeAnalysis #Conspiracy #DigitalForensics #TruthRevealed #VideoEditing #HiddenTruth #Investigation #DigitalSecrets #BreakingNews
Want to learn how to discover the root cause of recently patched OSS vulnerabilities and find some more to report? #SourceCodeAnalysis #BSidesDE buff.ly/48EFJb5
🚀 Dive into the Source Code Analysis series of Apache SeaTunnel Zeta Engine by Apache SeaTunnel! Gain insights from three articles for a deeper understanding when using SeaTunnel. #Apache #SeaTunnel #SourceCodeAnalysis 🚀 ift.tt/TIzo3On
always examine the .js files in the source code, for this I can recommend this simple but effective tool github.com/w9w/JSA from here you can access the endpoints of critical data, the places where backup files are stored and many endpoints 🌹🥰🥳 #bugbountytip #bugbounty…

Source code analysis is not just for developers—it's a crucial part of your security strategy. Let Lean Security find and fix vulnerabilities at the code level. #CodeSecurity #SourceCodeAnalysis Here are three ways you can stay secure on MMO games online: t.ly/2bVTt

🔍 Secure code review is crucial for identifying vulnerabilities in applications! Whether manual or automated, it plays a vital role in ensuring robust cybersecurity. Enhance your defenses with thorough #SourceCodeAnalysis & #Pentesting. 🌐bit.ly/3kuavyN #TechSecurity

👉 Machine Learning on Source Code A curated list of awesome research papers, datasets and software projects devoted to machine learning and source code. 🔗 github.com/src-d/awesome-…

How To Lean Away From Lagging Indicators In Application Security bit.ly/46BWr8w #ApplicationSecurity #PenetrationTesting #SourceCodeAnalysis #Software #SDLC #vulnerabilities #AttackSolutions

👉 Machine Learning on Source Code A curated list of awesome research papers, datasets and software projects devoted to machine learning and source code. 🔗 github.com/src-d/awesome-…
I'm hooked on source code analysis! 😄✨ I've created code to extract the locations where specific methods are called, imported from a specified module! 🔍💻 Check it out below ⬇️ github.com/Ayato-kosaka/s… #SourceCodeAnalysis #TypeScript #Programming #CodeAnalysis #Development

Password Decryption due to Sensitive Data Exposure in Front End Source Code dlvr.it/SZptg2 #cybersecurity #sourcecodeanalysis #sensitivedata
Most breaches occur due to weak protection in software and systems within organizations. Is your source code safe or not? معظم الأختراقات تحدث بسبب ضعف الحمايه في البرمجيات والأنظمه داخل المؤسسات. هل الكود المصدري الخاص بك آمن أم لا ؟ #sourcecodeanalysis #programmers

Day 26/100: Evaluating Eclipse PMD plug-in for source code analysis, what can help us to code better. #SourceCodeAnalysis #codeanalysis #100DaysOfCode

Ever wonder how frequently different C/C++ token types are used? Wonder no more! #SemiUsefulVisualizations #SourceCodeAnalysis

Most breaches occur due to weak protection in software and systems within organizations. Is your source code safe or not? معظم الأختراقات تحدث بسبب ضعف الحمايه في البرمجيات والأنظمه داخل المؤسسات. هل الكود المصدري الخاص بك آمن أم لا ؟ #sourcecodeanalysis #programmers

Looking for #SecuritySolution that applies #SourceCodeAnalysis algorithm for maximumAccuracy?bit.ly/1TKkEge

@SumaSoftPvtLtd explains why #SourceCodeAnalysis is one of the most preferred security measures. Read More - ow.ly/ON2Z30bwQwa

I'm hooked on source code analysis! 😄✨ I've created code to extract the locations where specific methods are called, imported from a specified module! 🔍💻 Check it out below ⬇️ github.com/Ayato-kosaka/s… #SourceCodeAnalysis #TypeScript #Programming #CodeAnalysis #Development

🔍 Secure code review is crucial for identifying vulnerabilities in applications! Whether manual or automated, it plays a vital role in ensuring robust cybersecurity. Enhance your defenses with thorough #SourceCodeAnalysis & #Pentesting. 🌐bit.ly/3kuavyN #TechSecurity

#SumaSoft with #Checkmarx jointly offers #SourceCodeAnalysis solutions to various MNC's.. ow.ly/7xDZ300Q4sG

#ThursdayThoughts 5 Benefits of Secure Source Code Analysis for Businesses- goo.gl/ZRGYkR #CyberSecurity #SourceCodeAnalysis

Reservoir's R-Check SCA tool is used by #DoD's JTNC to verify radio waveforms. Our partner NordiaSoft has a white paper on SCA. R-Check SCA: reservoir.com/product/r-chec… SCA white paper: nordiasoft.com/knowledge-cent… #softwaredefinedradio #sourcecodeanalysis

67% of commercial apps have vulnerabilities. Does yours? Let Suma Soft do a source code analysis for you #appsecurity #sourcecodeanalysis - ow.ly/o6RJ30jdkge

In our latest series, you'll identify different ways a stack overflow vulnerability can be present in source code and prove that they can be used to exploit a program. Don't have a license? Book a demo👉 hubs.ly/Q016fxXw0 #redteam #sourcecodeanalysis #stackoverflow

Is your application using 3rd party components? Reduce risk from third-party components, remediate vulnerabilities and ensure license compliance with @Kiuwan Insights. Get the data sheet: #sca #sourcecodeanalysis #codesecurity buff.ly/3rRwKOx

How To Lean Away From Lagging Indicators In Application Security bit.ly/46BWr8w #ApplicationSecurity #PenetrationTesting #SourceCodeAnalysis #Software #SDLC #vulnerabilities #AttackSolutions

Is your application using 3rd party components? Reduce risk from third-party components, remediate vulnerabilities and ensure license compliance with Kiuwan Insights. Get the data sheet: kiuwan.com/wp-content/upl… #sca #sourcecodeanalysis #codesecurity

Source code analysis is not just for developers—it's a crucial part of your security strategy. Let Lean Security find and fix vulnerabilities at the code level. #CodeSecurity #SourceCodeAnalysis Here are three ways you can stay secure on MMO games online: t.ly/2bVTt

Something went wrong.
Something went wrong.
United States Trends
- 1. Pat Spencer 2,489 posts
- 2. Kerr 5,328 posts
- 3. Podz 3,153 posts
- 4. Jimmy Butler 2,567 posts
- 5. Shai 14.7K posts
- 6. Seth Curry 4,327 posts
- 7. Hield 1,556 posts
- 8. Mark Pope 1,891 posts
- 9. #DubNation 1,405 posts
- 10. Carter Hart 3,909 posts
- 11. Derek Dixon 1,247 posts
- 12. Connor Bedard 2,296 posts
- 13. Brunson 7,329 posts
- 14. #ThunderUp N/A
- 15. Kuminga 1,388 posts
- 16. Caleb Wilson 1,146 posts
- 17. Notre Dame 38.9K posts
- 18. Braylon Mullins N/A
- 19. #SeanCombsTheReckoning 4,342 posts
- 20. Jaylen Brown 9,633 posts