#aprioritblog resultados da pesquisa
📲📷Cross-platform application development allows you to expand the audience by adapting your product to several popular platforms. To learn more about building cross-platform apps using React Native, check out our blog: cutt.ly/4eiGELmu #aprioritblog #mobile #mobileapps…
Drones are widely used in warehouses to lower expenses, improve worker safety, and boost warehouses efficiently. Explore about #drone control systems work and how they can help your business: bit.ly/3T178up #aprioritblog #drivers #cplusplus #droneservices…
⏬In this post, we provide a short explanation of how to calculate development costs for different types of blockchain solutions and what factors to consider. 📷To learn more about the topic, read the full article on our professional blog: cutt.ly/YwJajCB4 #aprioritblog…

Mobile banking apps are convenient to use but vulnerable to cyberattacks🔐 Learn from Apriorit experts about best practices that will help you build the trust of your users and protect their financial data: cutt.ly/jwKAjOGd #aprioritblog #cybersecurity…

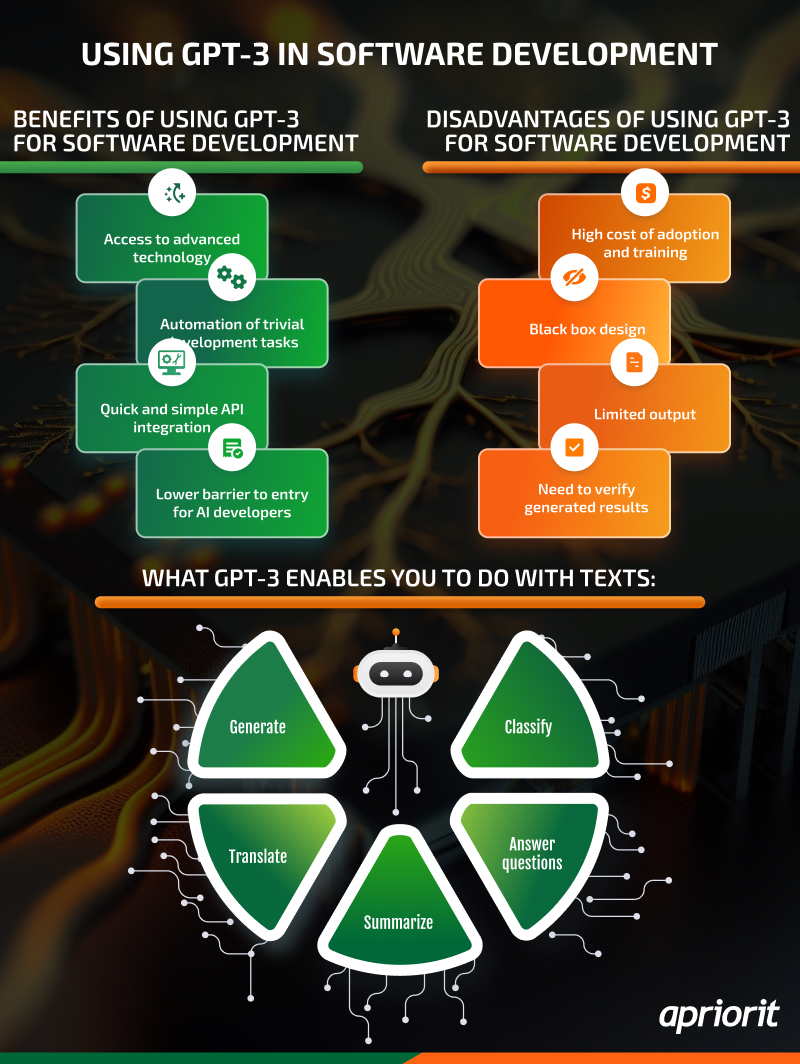
⬇️In the post below, we explore how GPT-3 works, weigh the pros and cons of using it to build AI-powered solutions, and provide examples of OpenAI's GPT-3 in use. Learn more about using GPT-3 from the full article on Apriorit’s blog: cutt.ly/6wYMsurI #aprioritblog #python…

Tempted to skip the discovery phase?🤔 Explore why a discovery phase is essential for any project and learn all you need to get the most out of it: cutt.ly/BrwvpFY7 #projectdiscoveryphase #softwaredevelopment #aprioritblog #businessanalyst #projectdevelopment

🔸Stakeholder management isn’t just about meetings – it’s about impact. In this post, we break down the key stakeholder roles, how to effectively manage them, and best practices to keep everyone aligned: cutt.ly/VraimOjs #SoftwareDevelopment #aprioritblog #stakeholders…

Choosing the right software vendor can be the key to your project’s success!💪 Discover how to assess vendors effectively and secure a reliable partner for your business in this article: cutt.ly/9eLiq6WM #apriorit #aprioritblog #softwaredevelopment…

🕚 Legacy hardware doesn’t have to mean outdated systems. ⬇️ Discover how hardware reverse engineering helps companies extend device lifespans, improve performance, and stay compliant without replacing hardware: cutt.ly/BrA0BUKQ #hardware #reverseengineering #aprioritblog…

In 2024, OWASP released a final version of their Mobile Top 10 list📃Learn what’s changed and which types of mobile security risks to prioritize when building and testing your mobile products: cutt.ly/uefRJbM5 #OWASP #aprioritblog #mobiledevelopment #mobilesolution #qa…

🕚 Legacy hardware doesn’t have to mean outdated systems. ⬇️ Discover how hardware reverse engineering helps companies extend device lifespans, improve performance, and stay compliant without replacing hardware: cutt.ly/BrA0BUKQ #hardware #reverseengineering #aprioritblog…

🔸Stakeholder management isn’t just about meetings – it’s about impact. In this post, we break down the key stakeholder roles, how to effectively manage them, and best practices to keep everyone aligned: cutt.ly/VraimOjs #SoftwareDevelopment #aprioritblog #stakeholders…

Tempted to skip the discovery phase?🤔 Explore why a discovery phase is essential for any project and learn all you need to get the most out of it: cutt.ly/BrwvpFY7 #projectdiscoveryphase #softwaredevelopment #aprioritblog #businessanalyst #projectdevelopment

Choosing the right software vendor can be the key to your project’s success!💪 Discover how to assess vendors effectively and secure a reliable partner for your business in this article: cutt.ly/9eLiq6WM #apriorit #aprioritblog #softwaredevelopment…

⏬In this post, we provide a short explanation of how to calculate development costs for different types of blockchain solutions and what factors to consider. 📷To learn more about the topic, read the full article on our professional blog: cutt.ly/YwJajCB4 #aprioritblog…

In 2024, OWASP released a final version of their Mobile Top 10 list📃Learn what’s changed and which types of mobile security risks to prioritize when building and testing your mobile products: cutt.ly/uefRJbM5 #OWASP #aprioritblog #mobiledevelopment #mobilesolution #qa…

📲📷Cross-platform application development allows you to expand the audience by adapting your product to several popular platforms. To learn more about building cross-platform apps using React Native, check out our blog: cutt.ly/4eiGELmu #aprioritblog #mobile #mobileapps…
⬇️In the post below, we explore how GPT-3 works, weigh the pros and cons of using it to build AI-powered solutions, and provide examples of OpenAI's GPT-3 in use. Learn more about using GPT-3 from the full article on Apriorit’s blog: cutt.ly/6wYMsurI #aprioritblog #python…

Drones are widely used in warehouses to lower expenses, improve worker safety, and boost warehouses efficiently. Explore about #drone control systems work and how they can help your business: bit.ly/3T178up #aprioritblog #drivers #cplusplus #droneservices…
⬇ Explore the best practices for increasing the #security of your project when using containers and #microservices: bit.ly/40kVjmI #aprioritblog #cloud #cloudcomputing #cybersecurity #securityawareness #cloudsecurity
Boost your AI chatbot’s security!🔐 Discover the basics of LLMs and their vulnerabilities in our latest article. ⬇Gain insights into prompt injection attacks and learn essential tips to protect your LLM-based chatbot from security breaches: cutt.ly/Pw9drWSj #aprioritblog…

🔐Securing your web application is a must if you want to prevent breaches and data leaks. ⬇In this post, we share tried and proven practices that help protect your product from attacks: cutt.ly/Vw0zVpzz #aprioritblog #cybersecurity #cybersecurityawareness #webdevelopment…

Securing your web application is a must if you want to prevent breaches and data leaks. ⏬In this post, we share tried and proven practices that help protect your product from attacks: cutt.ly/yw0uyfQd #aprioritblog #cybersecurity #webapplication #webappdevelopment #ba…

Deliver a reliable product by enhancing its protection against DLL injection attacks. ⏬Learn nuances to be aware of and discover a practical example of securing a Windows application from malicious DLL injection: cutt.ly/gwCW8yDq #aprioritblog #cyberdefense…

Check out our article to learn more about five key cloud data #security threats as well as legal requirements for protecting data in the #cloud that can help you combat them: bit.ly/3xrzB4u #aprioritblog #clouddevelopment #cloudinfrastructure #cybersecurity…
Mobile banking apps are convenient to use but vulnerable to cyberattacks🔐 Learn from Apriorit experts about best practices that will help you build the trust of your users and protect their financial data: cutt.ly/jwKAjOGd #aprioritblog #cybersecurity…

🔸Altering system behavior is a way to protect software from data leaks. But doing so is challenging.⏬In this article, we reveal how to take control over application operations by reversing API calls and implementing custom API hooks: cutt.ly/swJcazUh #aprioritblog…

⏬In this post, we provide a short explanation of how to calculate development costs for different types of blockchain solutions and what factors to consider. 🤔To learn more about the topic, read the full article on our professional blog: cutt.ly/YwJajCB4 #aprioritblog…
As blockchain technology becomes widespread, it attracts more attention from hackers🔓Learn what the weak spots are in a blockchain network, how hackers can attack them, and what you can do to improve your product’s security: cutt.ly/dwDUgPou #aprioritblog #blockchain…

Establishing clear communication between all team members and stakeholders is one of the keys to a project’s success.⬇️Explore how Apriorit PMs keep communication on our projects efficient and concise: cutt.ly/GwSs7slI #aprioritblog #business #businessdevelopement…

Tempted to skip the discovery phase?🤔 Explore why a discovery phase is essential for any project and learn all you need to get the most out of it: cutt.ly/BrwvpFY7 #projectdiscoveryphase #softwaredevelopment #aprioritblog #businessanalyst #projectdevelopment

⬇️In the post below, we explore how GPT-3 works, weigh the pros and cons of using it to build AI-powered solutions, and provide examples of OpenAI's GPT-3 in use. Learn more about using GPT-3 from the full article on Apriorit’s blog: cutt.ly/6wYMsurI #aprioritblog #python…
🔸Stakeholder management isn’t just about meetings – it’s about impact. In this post, we break down the key stakeholder roles, how to effectively manage them, and best practices to keep everyone aligned: cutt.ly/VraimOjs #SoftwareDevelopment #aprioritblog #stakeholders…

🕚 Legacy hardware doesn’t have to mean outdated systems. ⬇️ Discover how hardware reverse engineering helps companies extend device lifespans, improve performance, and stay compliant without replacing hardware: cutt.ly/BrA0BUKQ #hardware #reverseengineering #aprioritblog…

Choosing the right software vendor can be the key to your project’s success!💪 Discover how to assess vendors effectively and secure a reliable partner for your business in this article: cutt.ly/9eLiq6WM #apriorit #aprioritblog #softwaredevelopment…

⏬In this post, we provide a short explanation of how to calculate development costs for different types of blockchain solutions and what factors to consider. 📷To learn more about the topic, read the full article on our professional blog: cutt.ly/YwJajCB4 #aprioritblog…

Mobile banking apps are convenient to use but vulnerable to cyberattacks🔐 Learn from Apriorit experts about best practices that will help you build the trust of your users and protect their financial data: cutt.ly/jwKAjOGd #aprioritblog #cybersecurity…

In 2024, OWASP released a final version of their Mobile Top 10 list📃Learn what’s changed and which types of mobile security risks to prioritize when building and testing your mobile products: cutt.ly/uefRJbM5 #OWASP #aprioritblog #mobiledevelopment #mobilesolution #qa…

Establishing clear communication between all team members and stakeholders is one of the keys to a project’s success.⬇️Explore how Apriorit PMs keep communication on our projects efficient and concise: cutt.ly/GwSs7slI #aprioritblog #business #businessdevelopement…

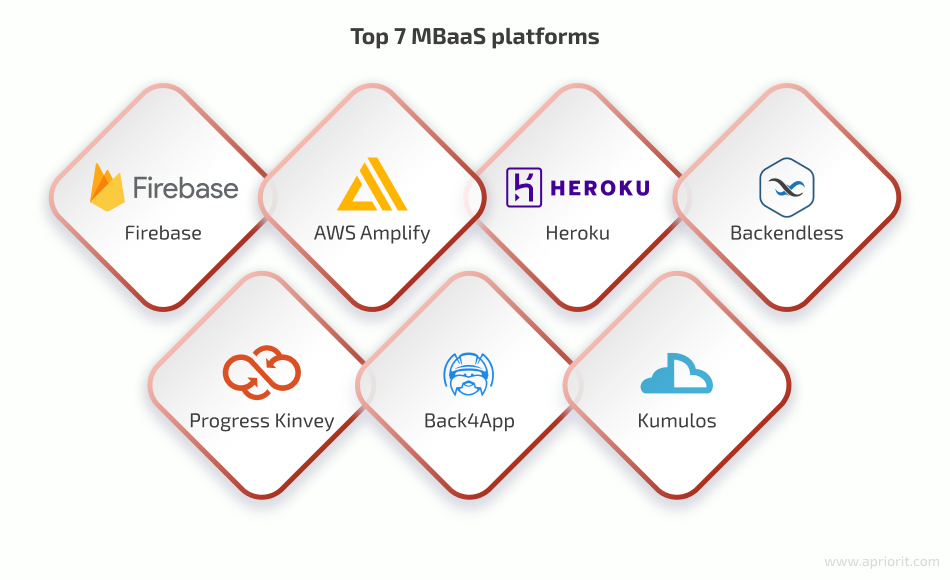
There are the most popular and trusted #MBaaS platforms you can consider. In the full article on our blog we focus on their key features and the types of projects these tools are suitable for. Learn more: cutt.ly/OwTllmmz #aprioritblog #mobiledevelopment #appdevelopment
Something went wrong.
Something went wrong.
United States Trends
- 1. Rickey 2,204 posts
- 2. Big Balls 19.7K posts
- 3. Westbrook 15.6K posts
- 4. Kings 153K posts
- 5. Waddle 3,081 posts
- 6. #TrumpsShutdownDragsOn 4,347 posts
- 7. Maybe in California N/A
- 8. Jakobi Meyers 1,136 posts
- 9. Olave 2,692 posts
- 10. Argentina 520K posts
- 11. Gold Glove 7,797 posts
- 12. Voting Rights Act 22.6K posts
- 13. Hayley 5,032 posts
- 14. Veo 3.1 4,925 posts
- 15. Justice Jackson 14.3K posts
- 16. Josh Simmons N/A
- 17. Aphrodite 3,409 posts
- 18. Capitol Police 24K posts
- 19. Haiku 4.5 1,185 posts
- 20. Eggs 28.5K posts

