#bash_script search results
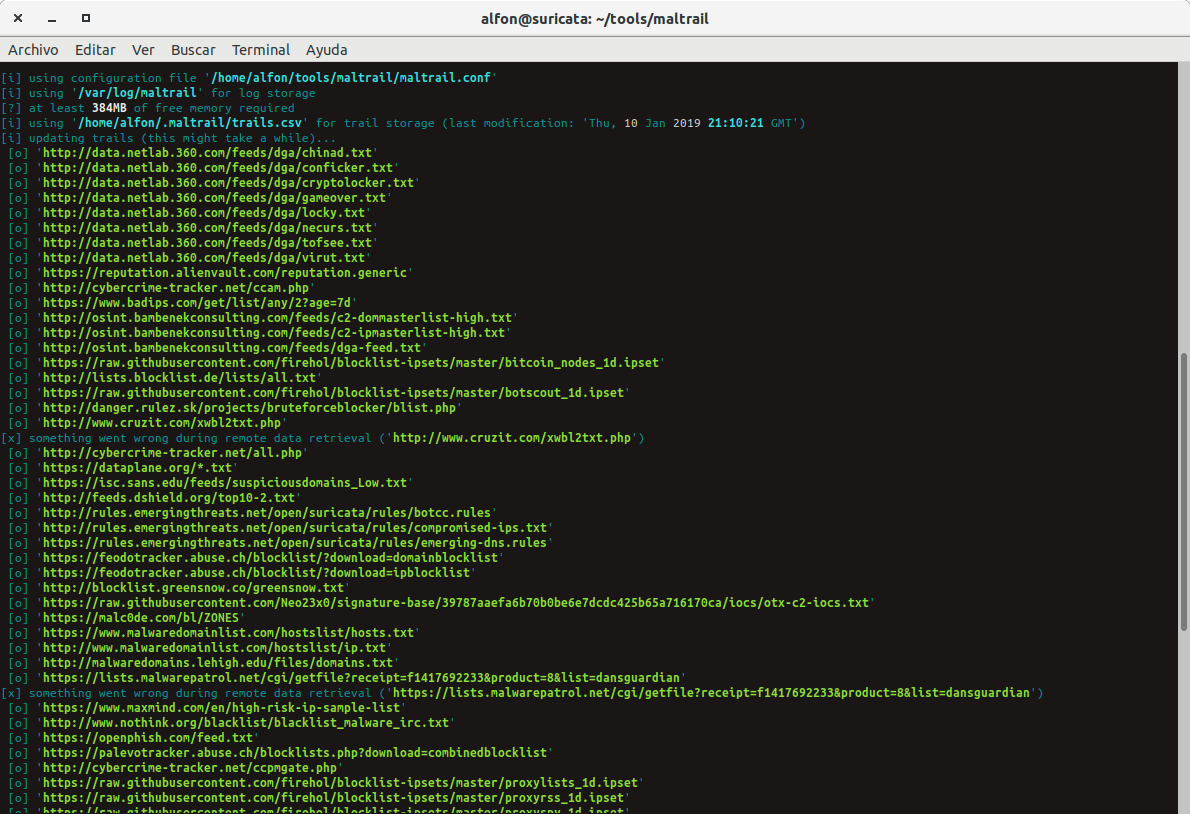
#Suricata_IDS & #Maltrail & #bash_script Actualizamos los trails ... sudo ./sensor.py --console | ccze -m ansi Cositas interesantes hoy .... ;-) Emotet-IcedID. El select: select(.http or .tls)
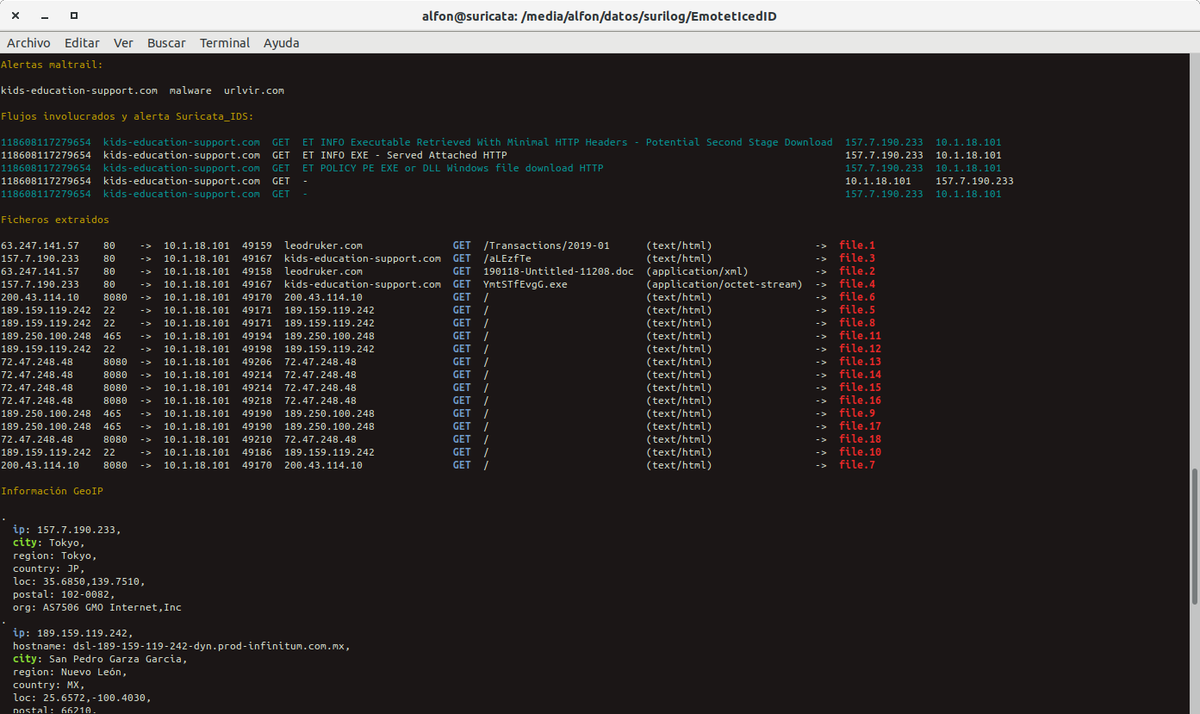
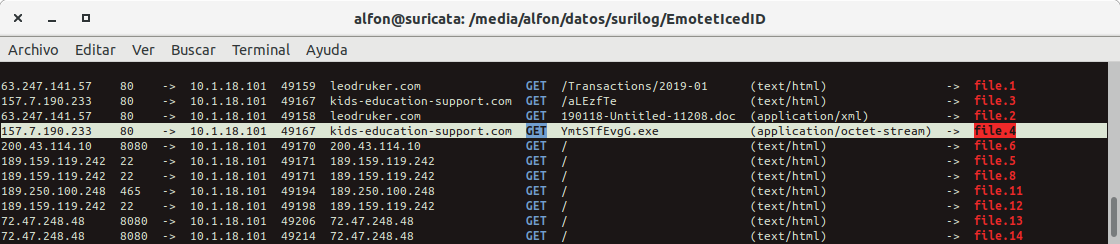
#Suricata_IDS & #Maltrail & #bash_script Bajo una alerta: "ET TROJAN Possible malicious #Office doc hidden in XML file" y en el "Payload_response" usando el select: 'select(.alert and .http and .flow)...

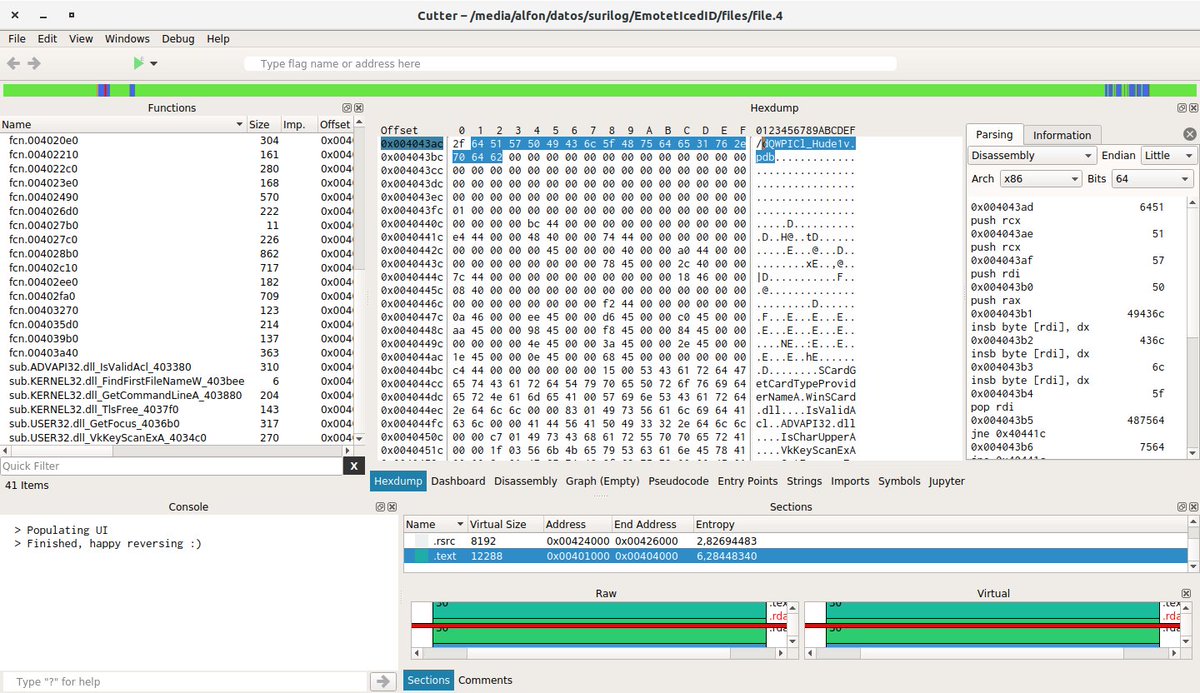
#Suricata_IDS & #Maltrail & #bash_script #Cutter Por ahí había en /files/file.4 ...: así que ahora os dejo que estoy trasteando con #radare/#Cutter y dQWPICl_Hude1v. pdb
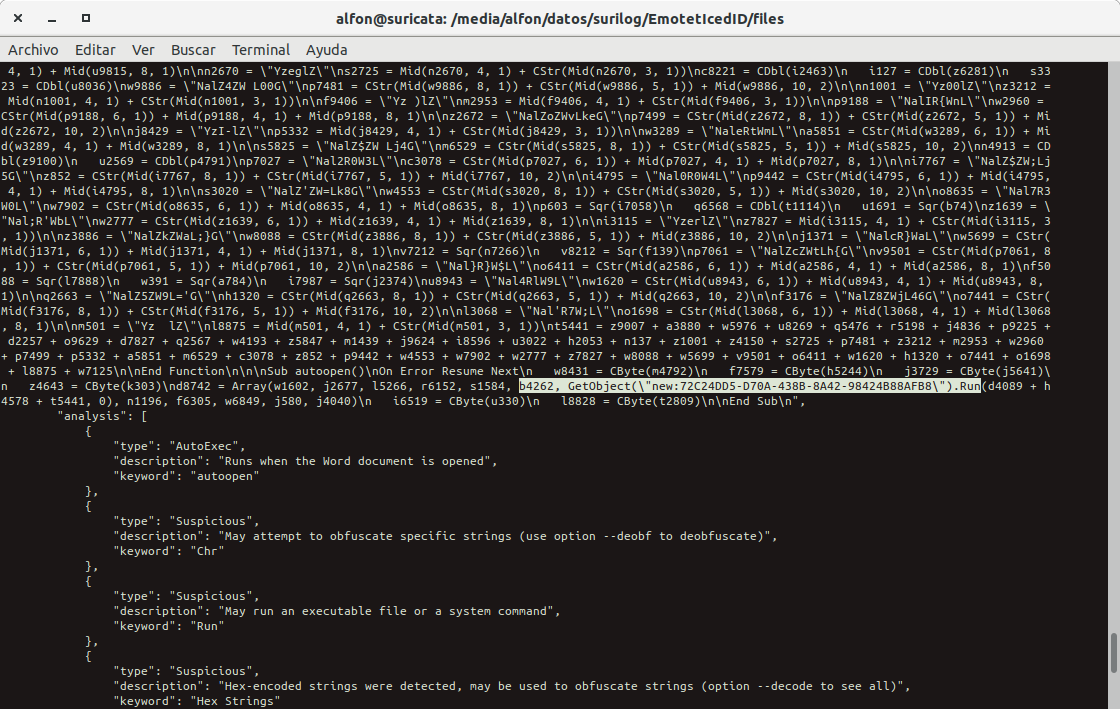
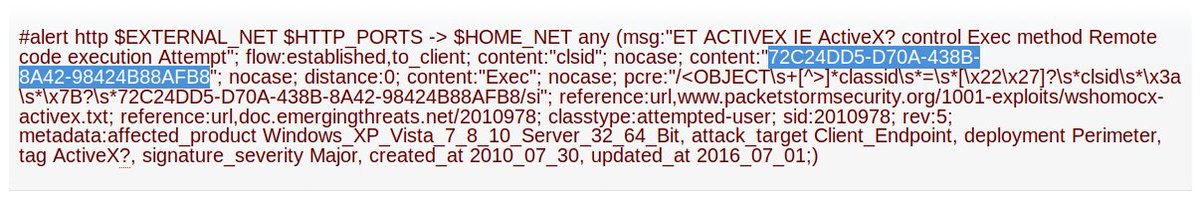
#Suricata_IDS & #Maltrail & #bash_script #OleTools (Trasteando) El doc/XML, no es detectado, pero: ACTIVEX IE ActiveX? control Exec method Remote code execution Attemp GetObject(\"new:72C24DD5-D70A-438B-8A42-98424B88AFB8\").Run #olevba file.2 -a - decode --reveal -j |fold -w150
r/t ezsploit - Linux Bash Script Automation For Metasploit dlvr.it/QGl0bC #Bash #Bash_Script #ezsploit #Metasploit
r/t Converto - Installing Kali Linux On VPS Server dlvr.it/QLdtS1 #Bash_Script #Converto #Cracking #Forensic
If you think you can only implement cache system in the backend or browser you need to watch this !! ☛ github : github.com/Abdallah-Abdel… #cache_strategies #bash_script
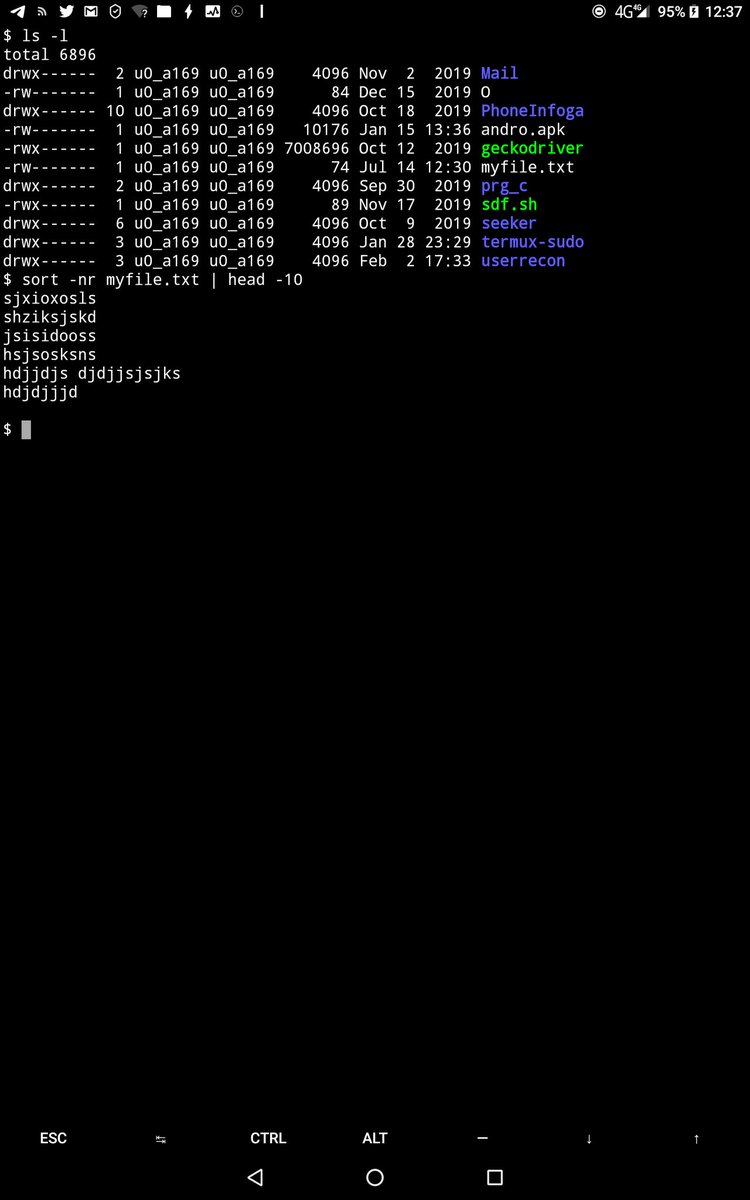
How to handle strings in Linux OS, shell command. Example. ghost@linuxpc# sort -nr myfile.txt | head -10 #bash_script #bash #script #hacking #ethicalhacker #Linux #unix #shell программист #линукс #хакер #Этическийхакер #Кибербезопасность
دوستان اینجا کسی هست بتونه توی بازه یک هفته اسکریپت نویسی بَش مقدماتی رو آموزش بده #bash_script #Linux #RETWEEET
SSH login without password linkedin.com/posts/milo%C5%… #bash #bash_script #bash_scripting #ssh #root #certiciate #remote #remote_access #administration #no_pass_auth #no_password_ssh #linux #development #cybersecurity #devops
Script to change directory in bash script. #!/bin/bash mydir =/usr/local pushd $mydir echo "Changed directory in `pwd`." #bash_script #unix #Linux #ethicalhacker #programming
How to run script on ssh connect remote host. Example. ssh myserver bash < ./myscript.sh #script #bash_script #bash #hacking #penetration-testing #penetrationtester #ethicalhacker #cybersecurity #unix #linux
.. else printf "Password is ok!" exit 1 fi #bash_script #unix #Linux #ethicalhacker #bash #script #hacking #cybersecurity #osint
do echo $i " / " ${arraylength} " : " ${mytest[$i-1]} done #bash_script #bash #script #linux #unix #ethicalhacker #программист #линукс #хакер #Этическийхакер
# Print the welcome message echo "Welcome user ${name}." #bash_script #bash #script #linux #programming #unix #administrator
How to process line of the text file, in bash script, through While loop. Example. #!/bin/bash while read lineoftext do sed 's/Tommy/Frank/' done < myfile.txt #bash_script #bash #script #hacking #ethicalhacker #unix #linux #old_programming
If you think you can only implement cache system in the backend or browser you need to watch this !! ☛ github : github.com/Abdallah-Abdel… #cache_strategies #bash_script
#100DaysOfCode #Day43 On this day I worked over a number of lessons in the first third of @GrasshopperApp's Intro to Interviewing course, studied an idea for a #bash_script, went over some Promineo Tech stuff, more bash stuff, some git stuff. Probably other stuff I didn't record.
Are there any well known and well used shell scripting IDEs for Un*x? - Visit programmatic.solutions/4nkwlh/are-the… for the answer. #bash_script #ide #unix #devlife #programming
دوستان اینجا کسی هست بتونه توی بازه یک هفته اسکریپت نویسی بَش مقدماتی رو آموزش بده #bash_script #Linux #RETWEEET
# Print the welcome message echo "Welcome user ${name}." #bash_script #bash #script #linux #programming #unix #administrator
#chec the return code for grep; if it is 0, file contains errors. if [[ $? -eq 0 ]]; then echo "${file} contains error(s), copying it to archive ${DIR}." cp ${file} ${DIR} fi done #bash_script #bash #script #linux #unix #programming #shell #программист #линукс #хакер
Shell command bash example. How to create a directory and test about this. #!/bin/bash mkdir /mytemp # Test if [[ $? -ne 0 ]]; then echo "mkdir don't created") ; exit 1 fi #bash_script #bash #script #linux #unix #programming #shell #программист #линукс
How to handle strings in Linux OS, shell command. Example. ghost@linuxpc# sort -nr myfile.txt | head -10 #bash_script #bash #script #hacking #ethicalhacker #Linux #unix #shell программист #линукс #хакер #Этическийхакер #Кибербезопасность

How to handle strings in Linux OS, shell command. Example. ghost@linuxpc# sort -nr myfile.txt | head -10 #bash_script #bash #script #hacking #ethicalhacker #Linux #unix #shell программист #линукс #хакер #Этическийхакер #Кибербезопасность
#Suricata_IDS & #Maltrail & #bash_script Actualizamos los trails ... sudo ./sensor.py --console | ccze -m ansi Cositas interesantes hoy .... ;-) Emotet-IcedID. El select: select(.http or .tls)


How to handle strings in Linux OS, shell command. Example. ghost@linuxpc# sort -nr myfile.txt | head -10 #bash_script #bash #script #hacking #ethicalhacker #Linux #unix #shell программист #линукс #хакер #Этическийхакер #Кибербезопасность

r/t ezsploit - Linux Bash Script Automation For Metasploit dlvr.it/QGl0bC #Bash #Bash_Script #ezsploit #Metasploit

r/t Converto - Installing Kali Linux On VPS Server dlvr.it/QLdtS1 #Bash_Script #Converto #Cracking #Forensic

#Suricata_IDS & #Maltrail & #bash_script #Cutter Por ahí había en /files/file.4 ...: así que ahora os dejo que estoy trasteando con #radare/#Cutter y dQWPICl_Hude1v. pdb


#Suricata_IDS & #Maltrail & #bash_script #OleTools (Trasteando) El doc/XML, no es detectado, pero: ACTIVEX IE ActiveX? control Exec method Remote code execution Attemp GetObject(\"new:72C24DD5-D70A-438B-8A42-98424B88AFB8\").Run #olevba file.2 -a - decode --reveal -j |fold -w150


#Suricata_IDS & #Maltrail & #bash_script Bajo una alerta: "ET TROJAN Possible malicious #Office doc hidden in XML file" y en el "Payload_response" usando el select: 'select(.alert and .http and .flow)...

Something went wrong.
Something went wrong.
United States Trends
- 1. Luka 57K posts
- 2. Lakers 43.9K posts
- 3. Clippers 16.7K posts
- 4. #DWTS 93.1K posts
- 5. #LakeShow 3,351 posts
- 6. Robert 132K posts
- 7. Kris Dunn 2,333 posts
- 8. Reaves 10.1K posts
- 9. Kawhi 5,798 posts
- 10. Jaxson Hayes 2,172 posts
- 11. Ty Lue 1,463 posts
- 12. Alix 14.9K posts
- 13. Elaine 45.8K posts
- 14. Jordan 117K posts
- 15. Collar 40.6K posts
- 16. Zubac 2,241 posts
- 17. Dylan 34.6K posts
- 18. NORMANI 6,054 posts
- 19. Colorado State 2,345 posts
- 20. Godzilla 36.3K posts











