#ciscontrolsv8 搜尋結果
18 is the new 20: CIS Controls v8 is here! helpnetsecurity.com/2021/05/19/cis… - @CISecurity #CISControlsv8 #cybersecurity #infosecurity #CISO #itsecurity

Getting a grip on basic cyber hygiene - helpnetsecurity.com/2021/05/10/get… - @CISecurity #CISControlsv8 #cybersecurity #infosecurity #CISO

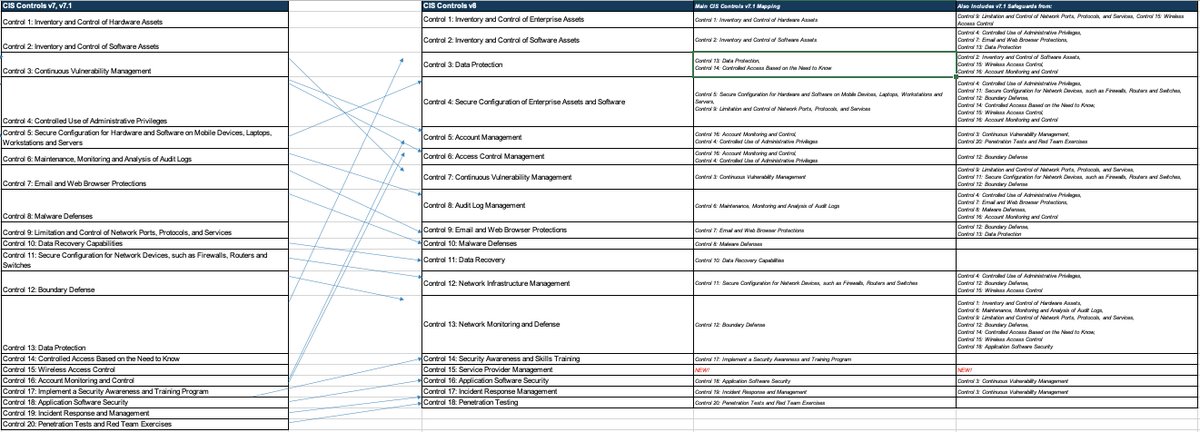
The newly released version of #CIScontrolsv8 has revised the 20 controls and consolidated them into more effective 18 controls w.r.t the activities and emerging #threats to help minimize the attack surface, data breaches, and various other cyber threats. #WomenInCyber #SheSec
Evaluate your risk and safeguard modeling and evaluation when you take the CIS Risk Assessment Method. sforce.co/3iArKgv #CISControlsv8 #cybersecurity

In this 20-minute module, we will help you identify information assets, Safeguards, and vulnerabilities. sforce.co/3iArKgv #CISControlsv8 #cybersecurity

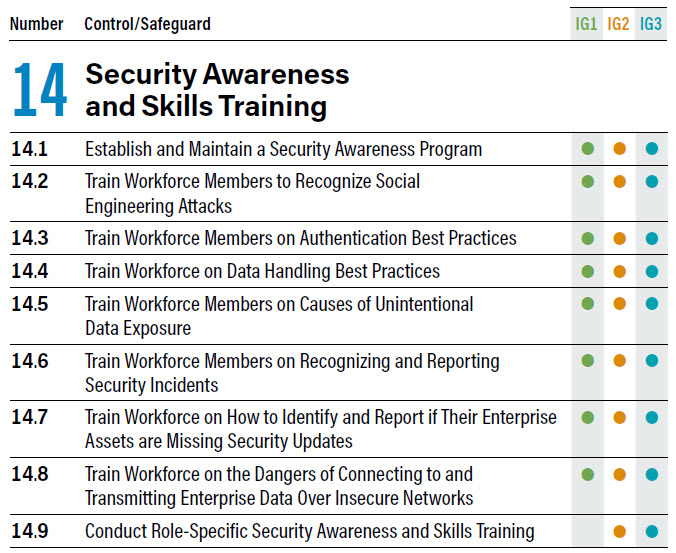
Anyone doubting that educating people about good security behaviours is worth investing the time and effort in; note that all but one of the controls in #CIScontrolsv8 form part of IG1, i.e. #basiccyberhygiene #cybersecurity #infosec #securityawareness cisecurity.org/controls/v8/
#CISControlsv8 sobre los “Grupos de Implementación” algo que viene de versiones anteriores, pero ahora ha reemplazado completamente el concepto de “Basic” y “Foundational”.

#CISControlsv8 se recomienda un plan de migración hacia la última versión. Sin embargo, si estás trabajando con v7 o v7.1 es algo que puedes planificar con más tiempo.

Use the CIS Risk Assessment Method today to evaluate your current CIS Safeguard Maturity. sforce.co/3iArKgv #CISControlsv8 #cybersecurity

This 20-minute module will help you evaluate your current maturity against the Safeguards in #CISControlsv8. sforce.co/3iArKgv #cybersecurity

In only 20-minutes you can have an understanding of your information assets, Safeguards, and vulnerabilities. Take the CIS risk assessment method today. sforce.co/3iArKgv #CISControlsv8 #cybersecurity

The #CISControlsv8 webinar recording is now available. cisecurity.wistia.com/medias/9qnuy1s…
cisecurity.wistia.com
Webinar | Welcome to CIS Controls v8
Cybersecurity risk analysis is an inexact but important process. Take the CIS risk assessment method today to identify your vulnerabilities. sforce.co/3iArKgv #CISControlsv8 #cybersecurity

#CyberHygiene is more important than ever before. Know more about IG1 of #CISControlsv8 cisecurity.org/controls/imple…

Going forward all new and updated #CISBenchmarks will be mapped to #CISControlsv8. bit.ly/3iI27J1
Did you hear, in #CISControlsv8 we added a new Control? bit.ly/3wzcYsk
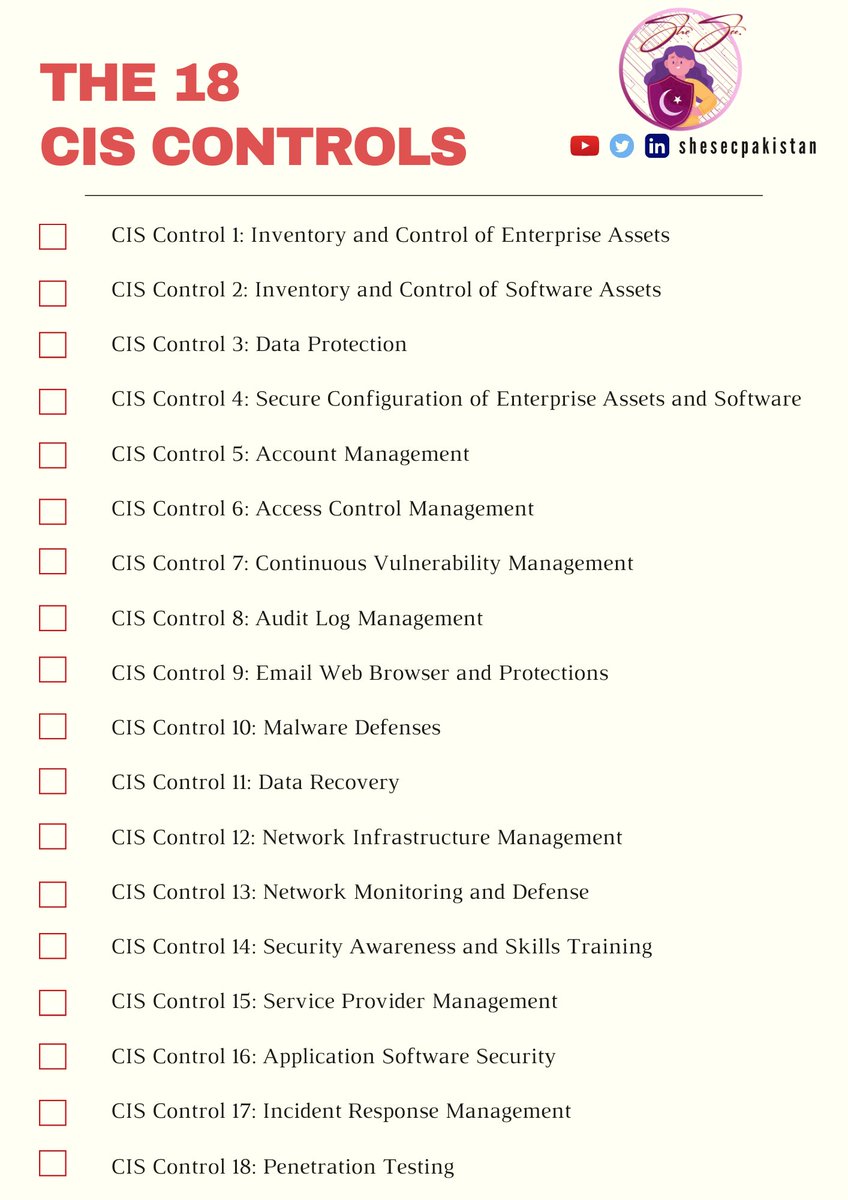
18 CIS Controls - an Effective Framework for Security Read More: hubs.la/Q01dS8K00 #ciscontrols #cissecurity #ciscontrolsv8 #cybersecurity #dataprotection #securityprogram #technology #datasecurity #cybersecurityawareness #informationsecurity
What does the CIS Controls Version 8 say about Pen Testing? hubs.la/Q01gK1s_0 #ciscontrols #cissecurity #ciscontrolsv8 #cybersecurity #dataprotection #securityprogram #technology #datasecurity #cybersecurityawareness #informationsecurity
#CISControlsv8 is here! Check out our blog post to learn what's changed. bit.ly/344wqB6
From cloud computing to remote work, we're covering the essential 18 safeguards to protect your digital landscape against evolving threats. Ready to future-proof your business? Let's dive in. 🌐💡 #CyberSecurity #CISControlsV8 #ProtectYourData itconsultants.com.au/latest-news/20…
Use the CIS Risk Assessment Method today to evaluate your current CIS Safeguard Maturity. sforce.co/3iArKgv #CISControlsv8 #cybersecurity

Cybersecurity risk analysis is an inexact but important process. Take the CIS risk assessment method today to identify your vulnerabilities. sforce.co/3iArKgv #CISControlsv8 #cybersecurity

In this 20-minute module, we will help you identify information assets, Safeguards, and vulnerabilities. sforce.co/3iArKgv #CISControlsv8 #cybersecurity

Evaluate your risk and safeguard modeling and evaluation when you take the CIS Risk Assessment Method. sforce.co/3iArKgv #CISControlsv8 #cybersecurity

In only 20-minutes you can have an understanding of your information assets, Safeguards, and vulnerabilities. Take the CIS risk assessment method today. sforce.co/3iArKgv #CISControlsv8 #cybersecurity

This 20-minute module will help you evaluate your current maturity against the Safeguards in #CISControlsv8. sforce.co/3iArKgv #cybersecurity

Learn how you can manage #cybersecurity risks using the #CISControlsv8 in this 50-minute module. bit.ly/3KIyW3N
cisecurity.org
Blog | CIS Controls v8 Introductory Course Available on Salesforce’s Trailhead
The CIS Controls v8 introductory course available on Trailhead offers a 50-minute overview on managing cybersecurity risks using the CIS Controls.
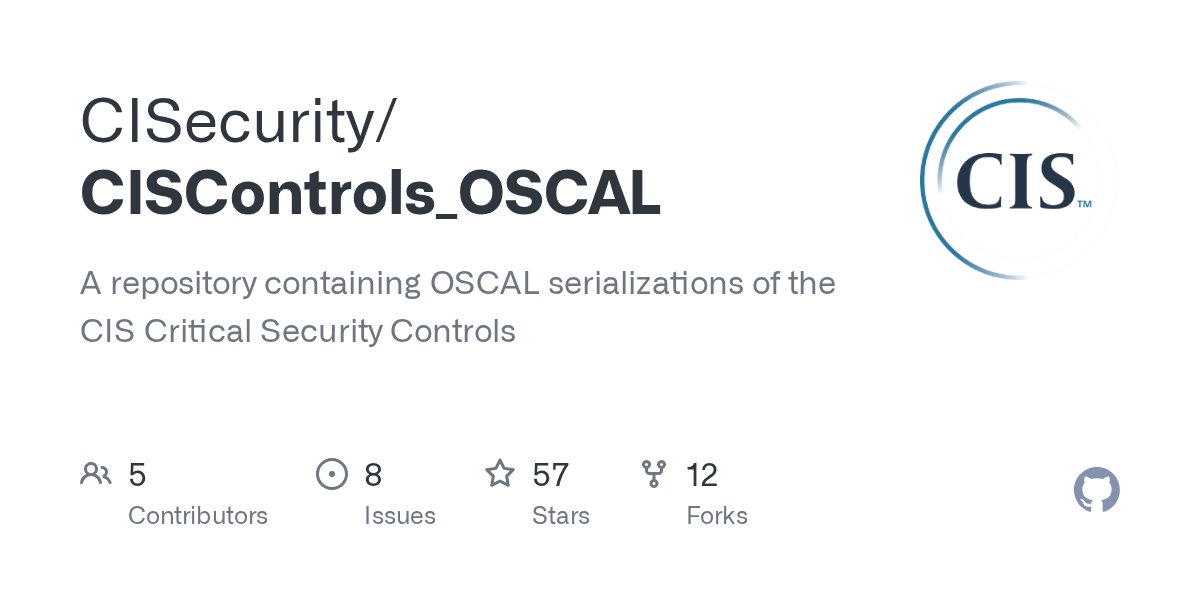
Exciting #OSCAL news: the @CISecurity released #CISControlsv8 and a mapping to #RMF 800-53 controls in OSCAL on Github. github.com/CISecurity/CIS…
#CISControlsv8 ya está disponible en español cisecurity.org/controls vía @CISecurity
In this new series, we take a look at each of the controls in v8 of the CIS Controls. First up, Matthew Jerzewski goes through the 5 safeguards for CIS Control 1 and offers an interpretation of what he's found. ⤵️ #CISControlsv8 @CISecurity sprou.tt/1oP7WdMwe35
Looking for an overview of #CISControlsv8? @BHinfoSecurity published a great blog post. bit.ly/3xVASOU
Is your organization required to meet CMMC requirements? The #CISControlsv8 mapped to CMMC levels can help. #CMMC #cybersecurity bit.ly/3A4Jfcq
We’ve mapped #CISControlsv8 to security and privacy controls for federal information systems and organizations. #cybersecurity bit.ly/3inXX8y
cisecurity.org
CIS Controls v8 Mapping to NIST SP 800-53 R5 including moderate and low baselines
This document provides a detailed mapping of the relationships between CIS Controls v8 and NIST SP 800-53 R5.
Movement to #WFH and cloud-based computing prompted the #CISControlsv8 update to support an enterprise’s security as they move to both fully cloud and hybrid environments. #cybersecurity wi.st/3Aczb1Z
Hear from key contributors of the #CISControlsv8 update in our on-demand webinar bit.ly/3uGrCNJ
Hear from key contributors of the #CISControlsv8 update in our on-demand webinar bit.ly/3uGrCNJ
We changed a few things in #CISControlsv8. @TripwireInc wrote up a nice summary of what those changes included.
Did you miss our #CISControlsv8 webinar? Don't worry - you can catch the recording on-demand. bit.ly/3uGrCNJ
18 is the new 20: CIS Controls v8 is here! helpnetsecurity.com/2021/05/19/cis… - @CISecurity #CISControlsv8 #cybersecurity #infosecurity #CISO #itsecurity

Are you watching? #CISControlsv8

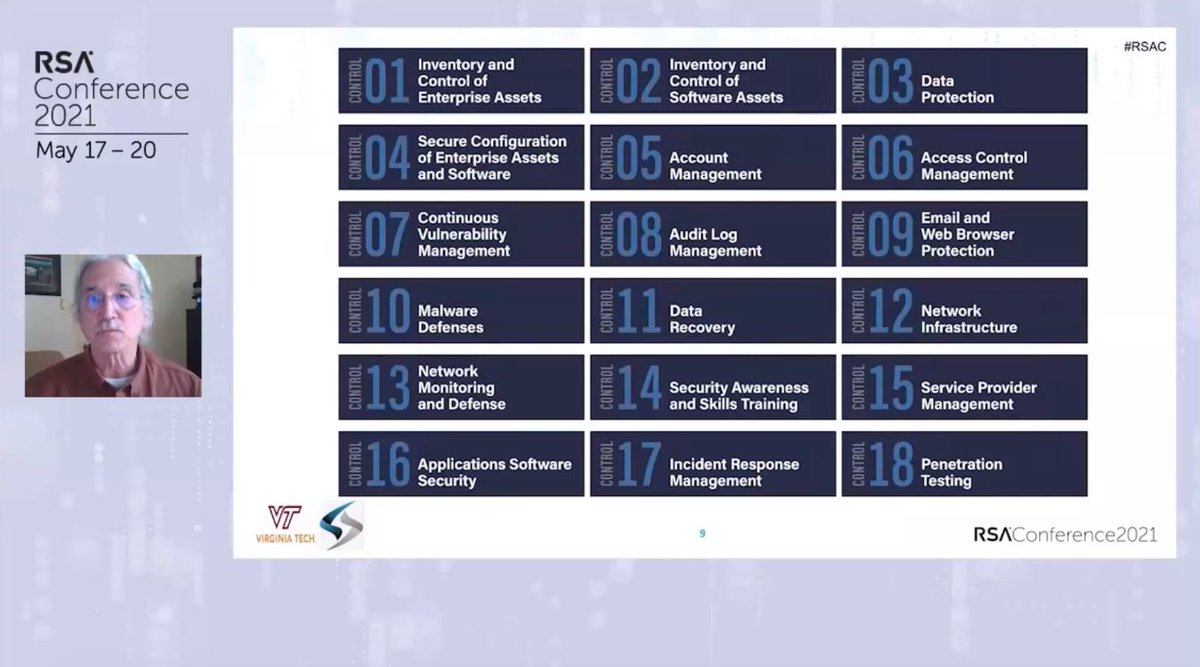
Today is the day - Join @randymarchany & @russelleubanks as they discuss what is new in Version 8 of the @CISecurity Critical Security Controls. Learn more about all of the @SANSInstitute instructors' talks: sans.org/u/1cgm #RSAC #CISControls

Getting a grip on basic cyber hygiene - helpnetsecurity.com/2021/05/10/get… - @CISecurity #CISControlsv8 #cybersecurity #infosecurity #CISO

With #CISControlsv8 each Safeguard is focused on measurable actions, and defines the measurement as part of the process. #RSAC @russelleubanks

Who's ready for @randymarchany & @russelleubanks's #RSAC presentation about the #CISControlsv8 update?! @RSAConference

Evaluate your risk and safeguard modeling and evaluation when you take the CIS Risk Assessment Method. sforce.co/3iArKgv #CISControlsv8 #cybersecurity

In this 20-minute module, we will help you identify information assets, Safeguards, and vulnerabilities. sforce.co/3iArKgv #CISControlsv8 #cybersecurity

Thank you for collaborating with us on #CISControlsv8, @SAFECode!
Congratulations to @CISecurity on the release of #CISControlsv8 SAFECode is honored to have had the opportunity to play a role in the development. Learn more about our collaboration here: bit.ly/3tXMb7a
Use the CIS Risk Assessment Method today to evaluate your current CIS Safeguard Maturity. sforce.co/3iArKgv #CISControlsv8 #cybersecurity

This 20-minute module will help you evaluate your current maturity against the Safeguards in #CISControlsv8. sforce.co/3iArKgv #cybersecurity

In only 20-minutes you can have an understanding of your information assets, Safeguards, and vulnerabilities. Take the CIS risk assessment method today. sforce.co/3iArKgv #CISControlsv8 #cybersecurity

Join some of the CIS team, @cloudsa, and @SAFECode for a webinar on May 4 where they'll discuss their partnership in updating cloud infrastructure guidance for #CISControlsv8. bit.ly/3dVrrIw

Cybersecurity risk analysis is an inexact but important process. Take the CIS risk assessment method today to identify your vulnerabilities. sforce.co/3iArKgv #CISControlsv8 #cybersecurity

#CISControlsv8 sobre los “Grupos de Implementación” algo que viene de versiones anteriores, pero ahora ha reemplazado completamente el concepto de “Basic” y “Foundational”.

Anyone doubting that educating people about good security behaviours is worth investing the time and effort in; note that all but one of the controls in #CIScontrolsv8 form part of IG1, i.e. #basiccyberhygiene #cybersecurity #infosec #securityawareness cisecurity.org/controls/v8/

#CISControlsv8 se recomienda un plan de migración hacia la última versión. Sin embargo, si estás trabajando con v7 o v7.1 es algo que puedes planificar con más tiempo.

The newly released version of #CIScontrolsv8 has revised the 20 controls and consolidated them into more effective 18 controls w.r.t the activities and emerging #threats to help minimize the attack surface, data breaches, and various other cyber threats. #WomenInCyber #SheSec

#CyberHygiene is more important than ever before. Know more about IG1 of #CISControlsv8 cisecurity.org/controls/imple…

Something went wrong.
Something went wrong.
United States Trends
- 1. Thanksgiving 1.93M posts
- 2. Packers 33.6K posts
- 3. Thankful 378K posts
- 4. Wicks 3,857 posts
- 5. Jordan Love 5,108 posts
- 6. #GoPackGo 5,440 posts
- 7. Goff 5,615 posts
- 8. #GBvsDET 2,214 posts
- 9. Turkey 253K posts
- 10. #OnePride 4,797 posts
- 11. Tom Kennedy N/A
- 12. Amon Ra 1,813 posts
- 13. Brian Branch N/A
- 14. Cece Winans N/A
- 15. LaFleur 1,611 posts
- 16. Romeo Doubs N/A
- 17. David Montgomery N/A
- 18. Ray J 2,664 posts
- 19. Josh Jacobs 1,646 posts
- 20. #ProBowlVote 28.9K posts