#encryptionconsulting search results
“It’s not that common, it doesn’t happen to every organization, and it is a big deal.” That’s exactly how it feels when enterprises realize they’re not prepared for the quantum shift. ow.ly/ewKV50Xk1c8 #EncryptionConsulting #CNSA #CNSACompliance #DataProtection…

Our blog unpacks what PQC algorithms mean for businesses, how migration can be managed, and the challenges that lie ahead. It also explores the practical side of readiness- implementation, compliance, and hardware adaptation. ow.ly/FN7050XjKxA #EncryptionConsulting #PQC…

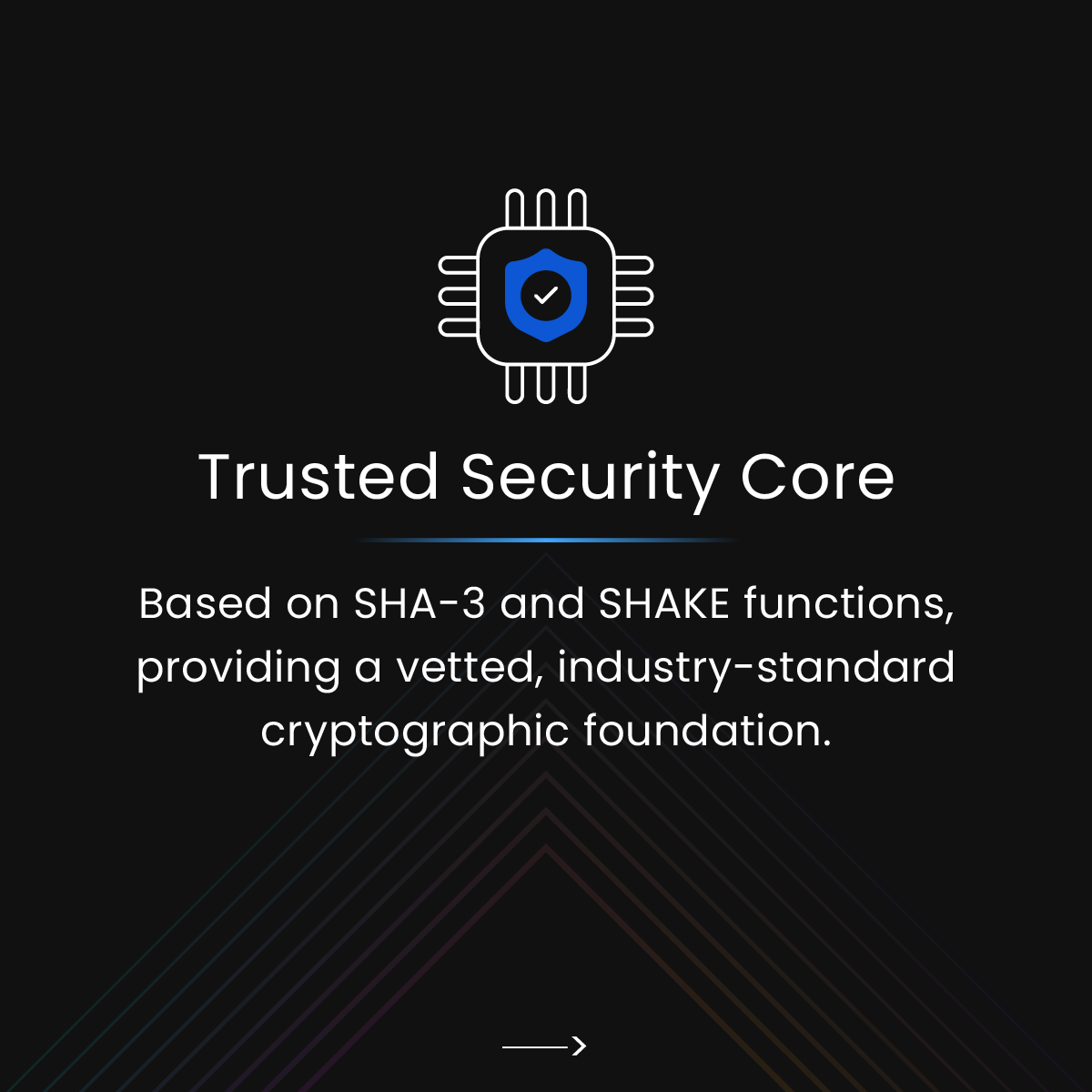
Discover how ML-KEM builds on SHA-3 and SHAKE to establish a trusted foundation for post-quantum key encapsulation. ow.ly/n8xB50XjJjV #EncryptionConsulting #PQC #PostQuantumCryptography #NISTAlgorithms #MLKEM #PQCAlgorithm



Our blog explains how code signing is especially vulnerable in the quantum era, the risks of HNDL and how CodeSign Secure helps keep your software protected. ow.ly/KlRS50X2eWe #EncryptionConsulting #CodeSigning #CICD #Cryptoagility #PQC #HNDL #DataProtection…

We’ll walk you through configuring your MongoDB service, setting paths, registering your agent, and making sure your certificates are in place in our video. ow.ly/fLai50WQqAG #EncryptionConsulting #MongoDB #DatabaseSecurity #CertificateManagement #PKI #CyberSecurity…

Brace yourselves… Quantum is coming. And no, your RSA-2048 won’t survive this winter. ow.ly/IP7a50Wtn8T #EncryptionConsulting #PQC #PostQuantumCryptography #RSA #DataProtection #Cybersecurity

Avoid costly delays and failed validations, 80% of FIPS failures are preventable with proper pre-lab preparation. ow.ly/nWc250WtjWn #EncryptionConsulting #FIPS140 #FIPSCompliance #Cybersecurity #CryptoBoundary #ProductSecurity #FIPS1403 #ComplianceAdvisory…




Which is more secure, symmetric or asymmetric encryption? Discover the details in our blog. ow.ly/Vfcv50WsQYN #EncryptionConsulting #EncryptionStrategy #SymmetricEncryption #AsymmetricEncryption #CyberSecurity #DataProtection #DigitalSecurity #TLS #HSM

Something went wrong.
Something went wrong.
United States Trends
- 1. #BaddiesUSA 52K posts
- 2. Rams 28.1K posts
- 3. Scotty 9,029 posts
- 4. #TROLLBOY 1,726 posts
- 5. Cowboys 97.6K posts
- 6. Chip Kelly 7,936 posts
- 7. Eagles 138K posts
- 8. Stafford 13.9K posts
- 9. Bucs 12K posts
- 10. Baker 20.6K posts
- 11. Raiders 65.6K posts
- 12. #RHOP 10.8K posts
- 13. Stacey 29.6K posts
- 14. #ITWelcomeToDerry 13.4K posts
- 15. Todd Bowles 1,951 posts
- 16. Teddy Bridgewater 1,161 posts
- 17. Ahna 6,106 posts
- 18. Lemmy 4,495 posts
- 19. DOGE 159K posts
- 20. Vin Diesel 1,004 posts

