#encryptionstrategy resultados de búsqueda
🔐 Day 02 of our 30 Days of Data Security is here! Today, we're exploring how organizations like yours are making encryption strategy a top priority to protect their valuable data. #EncryptionStrategy #DataSecurity #EncryptionStrategy #ProtectYourData




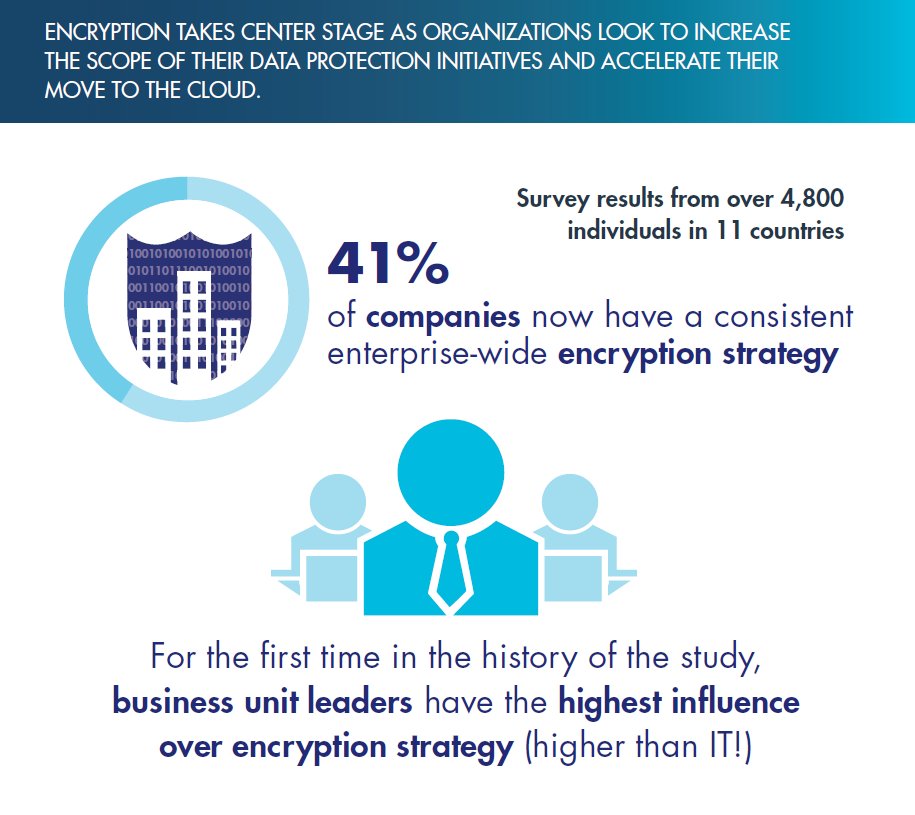
#EncryptionStrategy is more than just an IT problem according to our 2017 Global Encryption Trends Study thls.co/QIdU30aPDW0
Explore our detailed guide to implementing encryption effectively for robust data protection. ow.ly/3RwQ50SEjJL #EncryptionConsulting #DataSecurity #EncryptionStrategy #Cybersecurity #InfoSec #DataProtection #DataPrivacy #ITSecurity #NetworkSecurity

#EncryptionStrategy #EncryptionConsulting is a customer-focused #cybersecurity firm that provide a multitude of services in all aspects of #Encryption for our clients. ow.ly/1bJ750Ie9u5
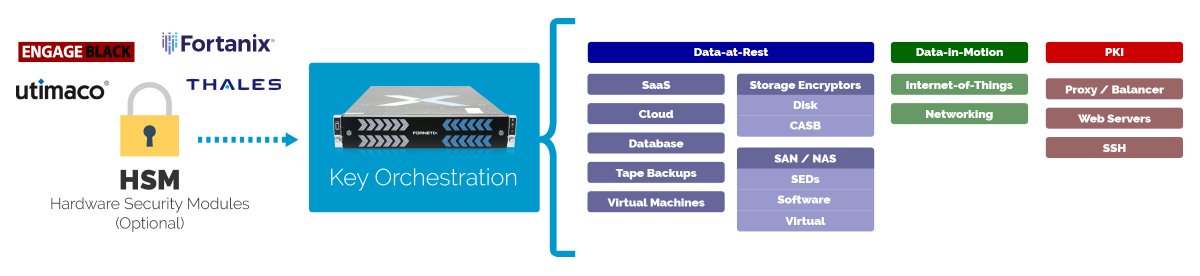
Think #HardwareSecurityModules are the same as Key Managers? Think Again. Empower your #EncryptionStrategy with both! bit.ly/2s2Wysm
Which is more secure, symmetric or asymmetric encryption? Discover the details in our blog. ow.ly/Vfcv50WsQYN #EncryptionConsulting #EncryptionStrategy #SymmetricEncryption #AsymmetricEncryption #CyberSecurity #DataProtection #DigitalSecurity #TLS #HSM

Build a strong, future-proof encryption strategy with our expert advisory services. Let’s secure your data effectively! ow.ly/o5fX50UFQ5Y #EncryptionConsulting #Cryptography #EncryptionStrategy #CyberSecurity #Encryption #DataProtection #CyberResilience #DataSecurity



Protect your sensitive data and streamline your encryption strategy with Trabic's cutting-edge Crypto as a Service technology. - - - #CryptoAsAService #DataSecurity #EncryptionStrategy #Trabic #StreamlineYourEncryption #PeaceOfMind

Are you neglecting your edge computing data when it comes to security? Improve your #encryptionstrategy before a breach occurs - Learn more about our joint solution with @StorMagic - free webcast bit.ly/2yl0ZoO

Companies are embracing an enterprise-wide #EncryptionStrategy ow.ly/TGhE301Nlon ow.ly/PkwFL ow.ly/XTsPi
Companies are embracing an enterprise-wide #EncryptionStrategy ow.ly/TGhE301Nlon ow.ly/PkwFL ow.ly/XTsPi
#GDPR is poised to disrupt the future of how data is stored, shared, and protected for everyone. What's your #DataProtection #EncryptionStrategy for the long term? And YES you'll need one. bit.ly/2ICYLBZ

What should define an #enterprise #encryptionstrategy? information-age.com/enterprise-enc… #cloud #compliance @Thalesesecurity

Steps to Secure Your Data Against Evolving Threats and Technologies fintter.com/2025/03/06/fut… via @Fintter Security #DataEncryption #CyberSecurity #EncryptionStrategy #QuantumComputing #DataProtection #SecureData #EncryptionBestPractices #KeyManagement #CyberResilience #Trending
Using virtual appliances for offload is a key #encryptionstrategy Find out strategies enterprises can use to improve throughput. The results are striking! @arraynetworks #ScopeMiddleEast #Distributor #NetworkPerformance #virtualAppliances #NetworkSecurity searchsecurity.techtarget.com/report/Using-v…
هر زمان اطلاعاتی از کاربر در دیتابیس ذخیره میکنی، به این فکر کن: "اگر دیتابیس لو بره، این فیلد قراره چقدر دردسر درست کنه؟" این سوال، راهنمای خوبی برای تصمیمات رمزنگاریه. #DataSensitivity #EncryptionStrategy #programming
‘Cloud adoption and escalating threats accelerate encryption deployments’ information-age.com/cloud-adoption… #encryptionstrategy @Thalesesecurity
Do you have an encryption strategy in place? #encryptionstrategy #cloudsecurity bit.ly/2Ix7Trm
Which is more secure, symmetric or asymmetric encryption? Discover the details in our blog. ow.ly/Vfcv50WsQYN #EncryptionConsulting #EncryptionStrategy #SymmetricEncryption #AsymmetricEncryption #CyberSecurity #DataProtection #DigitalSecurity #TLS #HSM

Which is more secure, symmetric or asymmetric encryption? Discover the details in our blog. ow.ly/Vfcv50WsQYN #EncryptionConsulting #EncryptionStrategy #SymmetricEncryption #AsymmetricEncryption #CyberSecurity #DataProtection #DigitalSecurity #TLS #HSM

هر زمان اطلاعاتی از کاربر در دیتابیس ذخیره میکنی، به این فکر کن: "اگر دیتابیس لو بره، این فیلد قراره چقدر دردسر درست کنه؟" این سوال، راهنمای خوبی برای تصمیمات رمزنگاریه. #DataSensitivity #EncryptionStrategy #programming
Build a strong, future-proof encryption strategy with our expert advisory services. Let’s secure your data effectively! ow.ly/o5fX50UFQ5Y #EncryptionConsulting #Cryptography #EncryptionStrategy #CyberSecurity #Encryption #DataProtection #CyberResilience #DataSecurity



Explore our detailed guide to implementing encryption effectively for robust data protection. ow.ly/3RwQ50SEjJL #EncryptionConsulting #DataSecurity #EncryptionStrategy #Cybersecurity #InfoSec #DataProtection #DataPrivacy #ITSecurity #NetworkSecurity

🔐 Day 02 of our 30 Days of Data Security is here! Today, we're exploring how organizations like yours are making encryption strategy a top priority to protect their valuable data. #EncryptionStrategy #DataSecurity #EncryptionStrategy #ProtectYourData




Protect your sensitive data and streamline your encryption strategy with Trabic's cutting-edge Crypto as a Service technology. - - - #CryptoAsAService #DataSecurity #EncryptionStrategy #Trabic #StreamlineYourEncryption #PeaceOfMind

#EncryptionStrategy #EncryptionConsulting is a customer-focused #cybersecurity firm that provide a multitude of services in all aspects of #Encryption for our clients. ow.ly/1bJ750Ie9u5

#EncryptionStrategy is more than just an IT problem according to our 2017 Global Encryption Trends Study thls.co/QIdU30aPDW0

Explore our detailed guide to implementing encryption effectively for robust data protection. ow.ly/3RwQ50SEjJL #EncryptionConsulting #DataSecurity #EncryptionStrategy #Cybersecurity #InfoSec #DataProtection #DataPrivacy #ITSecurity #NetworkSecurity

🔐 Day 02 of our 30 Days of Data Security is here! Today, we're exploring how organizations like yours are making encryption strategy a top priority to protect their valuable data. #EncryptionStrategy #DataSecurity #EncryptionStrategy #ProtectYourData




#EncryptionStrategy #EncryptionConsulting is a customer-focused #cybersecurity firm that provide a multitude of services in all aspects of #Encryption for our clients. ow.ly/1bJ750Ie9u5

Think #HardwareSecurityModules are the same as Key Managers? Think Again. Empower your #EncryptionStrategy with both! bit.ly/2s2Wysm

Build a strong, future-proof encryption strategy with our expert advisory services. Let’s secure your data effectively! ow.ly/o5fX50UFQ5Y #EncryptionConsulting #Cryptography #EncryptionStrategy #CyberSecurity #Encryption #DataProtection #CyberResilience #DataSecurity



Which is more secure, symmetric or asymmetric encryption? Discover the details in our blog. ow.ly/Vfcv50WsQYN #EncryptionConsulting #EncryptionStrategy #SymmetricEncryption #AsymmetricEncryption #CyberSecurity #DataProtection #DigitalSecurity #TLS #HSM

#GDPR is poised to disrupt the future of how data is stored, shared, and protected for everyone. What's your #DataProtection #EncryptionStrategy for the long term? And YES you'll need one. bit.ly/2ICYLBZ

What should define an #enterprise #encryptionstrategy? information-age.com/enterprise-enc… #cloud #compliance @Thalesesecurity

Protect your sensitive data and streamline your encryption strategy with Trabic's cutting-edge Crypto as a Service technology. - - - #CryptoAsAService #DataSecurity #EncryptionStrategy #Trabic #StreamlineYourEncryption #PeaceOfMind

Are you neglecting your edge computing data when it comes to security? Improve your #encryptionstrategy before a breach occurs - Learn more about our joint solution with @StorMagic - free webcast bit.ly/2yl0ZoO

Something went wrong.
Something went wrong.
United States Trends
- 1. Good Friday 43.9K posts
- 2. Warner Bros 49.4K posts
- 3. #FridayVibes 3,276 posts
- 4. #FridayMotivation 3,306 posts
- 5. RED Friday 3,367 posts
- 6. Cloudflare 36.1K posts
- 7. HBO Max 29.2K posts
- 8. Jake Tapper 49.6K posts
- 9. Happy Farmers 2,704 posts
- 10. The EU 124K posts
- 11. #heatedrivalry 33.5K posts
- 12. Wizkid 192K posts
- 13. Pickens 16K posts
- 14. Paramount 23.6K posts
- 15. #PutThatInYourPipe N/A
- 16. The Gong Show N/A
- 17. Davido 108K posts
- 18. White Man 94K posts
- 19. Gibbs 21.7K posts
- 20. #PowerForce 1,020 posts















