#symmetricencryption 検索結果
Types of Encryption and Cryptography Services. #cryptography #encryption #SymmetricEncryption #AsymmetricEncryption #digitalsignature #hashing #pki #confidentiality #integrity #authentication #nonrepudiation #proofofdelivery #cybersecurity #infosec #informationsecurity


Symmetric VS. Asymmetric encryption: 🔹 #SymmetricEncryption: One key for encryption and decryption. Fast but key distribution can be tricky. 🔹 #AsymmetricEncryption: Two keys – public and private. More secure for key exchange but slower.


SYMMETRIC AND ASYMMETRIC ENCRYPTION youtube.com/watch?v=qyCA6K… #SymmetricEncryption #AsymmetricEncryption #SoftwareEngineering #ComputerEngineering

youtube.com
YouTube
SYMMETRIC AND ASYMMETRIC ENCRYPTION
🔐Symmetric vs Asymmetric Encryption🔐 #Cyber #CyberSecurity #SymmetricEncryption #AsymmetricEncryption #Infosec #Encryption #DataSecurity #KnoeledgeSharing #DataProtection

Symmetric vs asymmetric encryption ............. #SymmetricEncryption, #AsymmetricEncryption, #DataEncryption, #EncryptionAlgorithms, #CyberSecurity, #EncryptionTechnology, #DataProtection, #EncryptionKeys, #EncryptionTools, #Cryptography

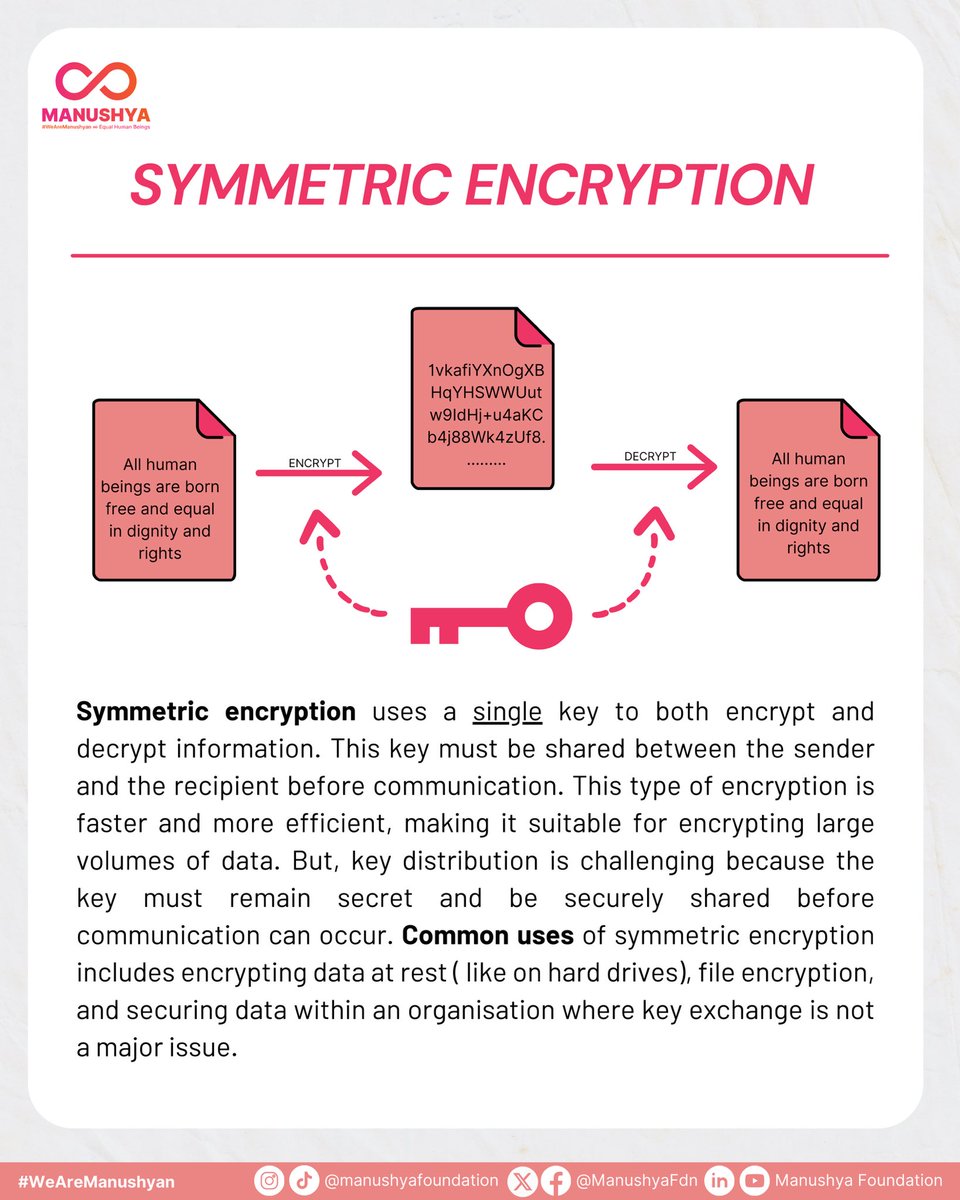
Symmetric encryption uses a single key for both encryption and decryption, making it fast and efficient for large data volumes. However, secure key sharing is crucial. Commonly used for data at rest and internal file encryption. #DataSecurity #SymmetricEncryption #Encryption…

There are two basic types of encryption - symmetric and asymmetric. As the name implies, #SymmetricEncryption uses the same key for both encryption and decryption. #AsymmetricEncryption uses a public key for encryption and a separate private key for decryption.

#SymmetricEncryption, what is it? It is a #cryptographic #algorithm that uses the same secret #key for its operation and, if applicable, for reversing the effects of the operation (e.g., an AES key for #encryption and #decryption). #TelsyABC #cryptography #crypto #cybersecurity
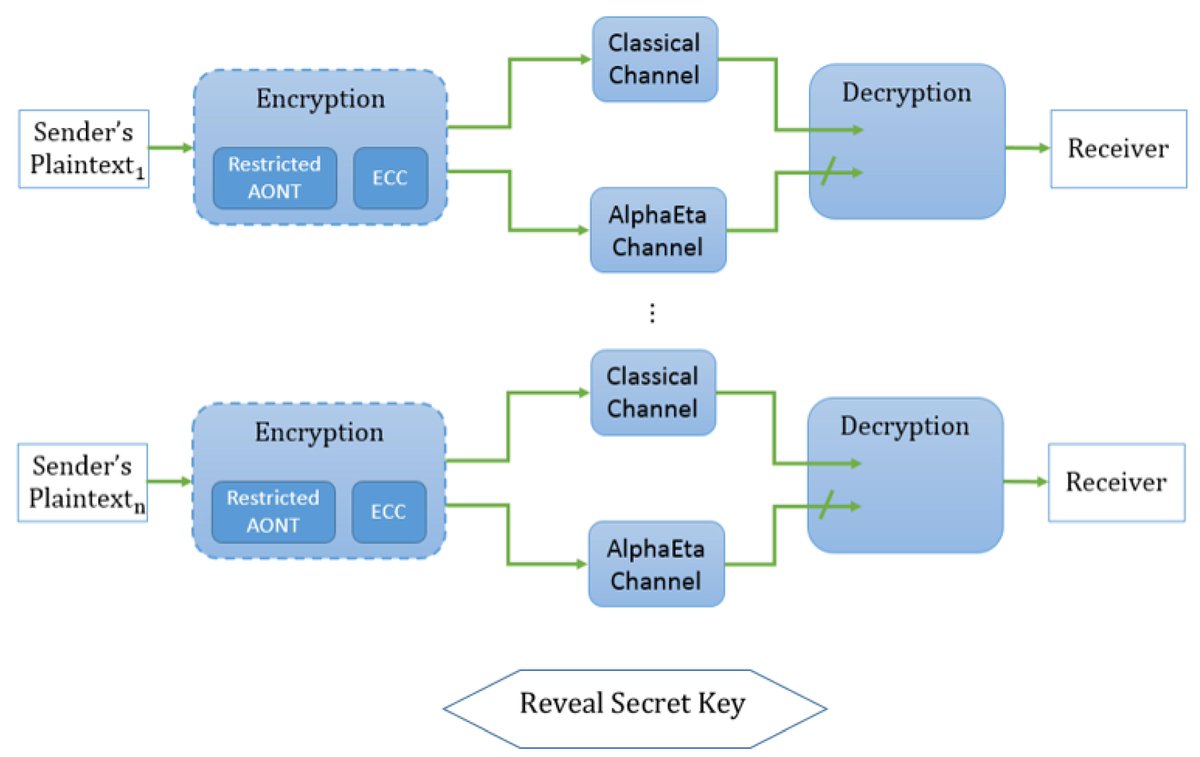
#mdpientropy Integrating Classical Preprocessing into an Optical Encryption Scheme mdpi.com/1099-4300/21/9… #symmetricencryption #allornothing #transform #opticalchannel #provablesecurity
🔒 Today’s #wordoftheday is Secret Key (Symmetric) Cryptographic Algorithm! Symmetric algorithms rely on one key for both encryption and decryption. But how do we ensure that key stays secure in the quantum era? #SymmetricEncryption #SecretKey #QuantumSecurity

Confused about #SymmetricEncryption and #AsymmetricEncryption? 🤔 Get help deciphering the differences. #Encryption #Cryptography bit.ly/2nzYpX7

The Ultimate guide to understanding Symmetric Encryption! Know here : clickssl.net/blog/what-is-s… #SymmetricEncryption #Symmetrickeyalgorithm #SymmetricEncryptionAlgorithms

SYMMETRIC AND ASYMMETRIC ENCRYPTION youtube.com/watch?v=qyCA6K… #SymmetricEncryption #AsymmetricEncryption #SoftwareEngineering #ComputerEngineering #FollowBack #FB #FollowForFollow #FFF #Follow4Follow #F4F #FollowForFollowBack #FFFB #Follow4FollowBack #F4FB

youtube.com
YouTube
SYMMETRIC AND ASYMMETRIC ENCRYPTION
Keeping information secure is important, but do you know the difference between symmetric and asymmetric encryption? Comment your answer below! #Encryption101 #Cybersecurity #SymmetricEncryption #AsymmetricEncryption #DataSecurity #EncryptThis #TechTrivia #ProtectYourData

Which is more secure, symmetric or asymmetric encryption? Discover the details in our blog. ow.ly/Vfcv50WsQYN #EncryptionConsulting #EncryptionStrategy #SymmetricEncryption #AsymmetricEncryption #CyberSecurity #DataProtection #DigitalSecurity #TLS #HSM

In case you missed it: "Not your keys, not your #crypto": Why? Because anyone with your private keys can drain your accounts. Learn what private and public keys are. Will be necessary to know for #Web3. geeq.io/geeqs-introduc… #SymmetricEncryption #AsymmetricEncryption $Geeq
geeq.io
Geeq's Introduction to Encryption • Geeq
Introduction to Encryption - An entry level explainer of the encryption underlying public and private keys.
2/15 Symmetric encryption is the simpler form. It uses the same key to encrypt and decrypt data. Think of it like a shared password between sender and receiver. #SymmetricEncryption #InfoSec
Symmetric vs asymmetric #encryption: what’s the difference? How do they work and when to use them? Plus, we share some #BestPractices. What you should know about #symmetricencryption and #asymmetricencryption 👇 blog.mailfence.com/symmetric-vs-a… #infosec #cybersecurity #endtoendencryption

Explore the differences between #SymmetricEncryption and #AsymmetricEncryption, as well as how to evaluate the #encryption method for your enterprise. 🗝 bit.ly/2nD2n1l
#PrivacyPreserving #MedicalDataSharing System with #SymmetricEncryption Based on #Blockchain ✏️ Mingqi Hu, Yanli Ren and Cien Chen 🔗 brnw.ch/21wVKZv Viewed: 3000; Cited: 8 #mdpisymmetry

SYMMETRIC AND ASYMMETRIC ENCRYPTION youtube.com/watch?v=qyCA6K… #SymmetricEncryption #AsymmetricEncryption #SoftwareEngineering #ComputerEngineering

youtube.com
YouTube
SYMMETRIC AND ASYMMETRIC ENCRYPTION
#PrivacyPreserving #MedicalDataSharing System with #SymmetricEncryption Based on #Blockchain ✏️ Mingqi Hu, Yanli Ren and Cien Chen 🔗 brnw.ch/21wVKZv Viewed: 3000; Cited: 8 #mdpisymmetry

Which is more secure, symmetric or asymmetric encryption? Discover the details in our blog. ow.ly/Vfcv50WsQYN #EncryptionConsulting #EncryptionStrategy #SymmetricEncryption #AsymmetricEncryption #CyberSecurity #DataProtection #DigitalSecurity #TLS #HSM

Which is more secure, symmetric or asymmetric encryption? Discover the details in our blog. ow.ly/Vfcv50WsQYN #EncryptionConsulting #EncryptionStrategy #SymmetricEncryption #AsymmetricEncryption #CyberSecurity #DataProtection #DigitalSecurity #TLS #HSM

2/15 Symmetric encryption is the simpler form. It uses the same key to encrypt and decrypt data. Think of it like a shared password between sender and receiver. #SymmetricEncryption #InfoSec
Word of the Week: Symmetric Encryption – the art of using one secret key to lock and unlock your data. Efficient and effective, it’s a cornerstone of cloud security. Learn More → bit.ly/4ioGxok #CloudSecurity #Encryption #SymmetricEncryption
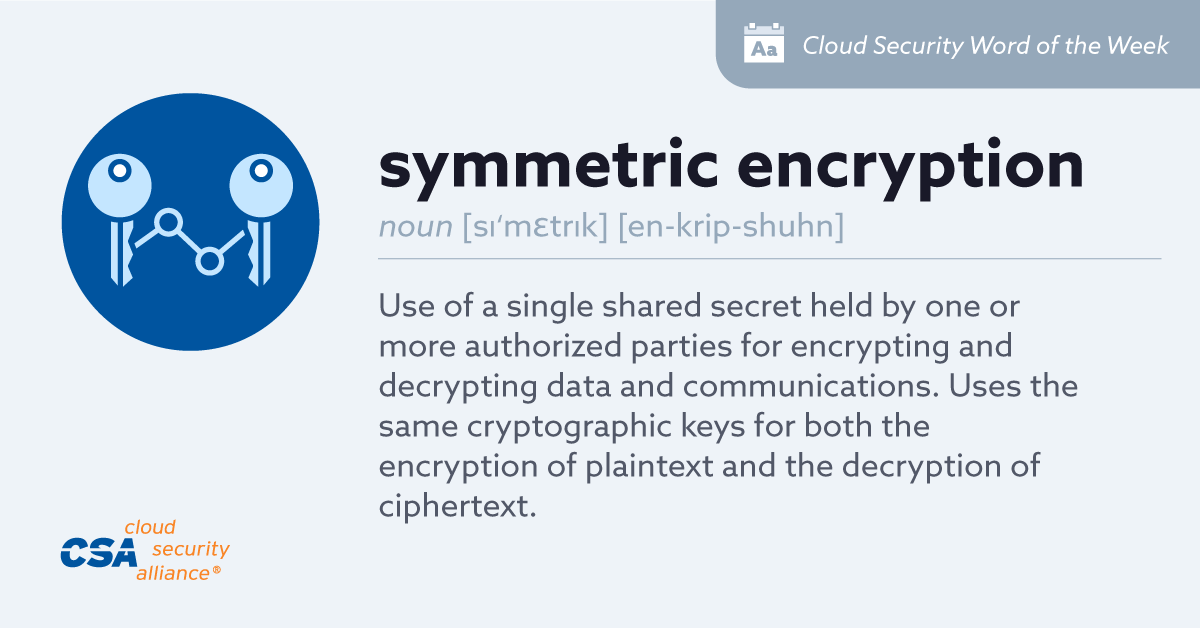
🔒 Today’s #wordoftheday is Secret Key (Symmetric) Cryptographic Algorithm! Symmetric algorithms rely on one key for both encryption and decryption. But how do we ensure that key stays secure in the quantum era? #SymmetricEncryption #SecretKey #QuantumSecurity

Explore the key differences between symmetric and asymmetric encryption, their uses, and how they protect sensitive data in cybersecurity. fintter.com/2025/03/06/und… via @Fintter Security #CyberSecurity #SymmetricEncryption #EncryptionAlgorithms #Cryptography #Trending
Thread 2: Two main encryption types: Symmetric: One key for locking and unlocking data. Fast but tricky to share keys safely. Asymmetric: Uses two keys - public for encrypting, private for decrypting. Enhances security in sharing. #SymmetricEncryption #AsymmetricEncryption

(4/11) 🌐 Symmetric encryption: Same key for encryption and decryption (e.g., AES). #SymmetricEncryption
Yesterday in our GDSC Cybersecurity class, we dove into the world of encryption! 🛡️🔐 Learned the fundamentals of #AsymmetricEncryption and #SymmetricEncryption. Big thanks to all the students for their participation and enthusiasm! #CyberSecurity #GDSC #TechEducation
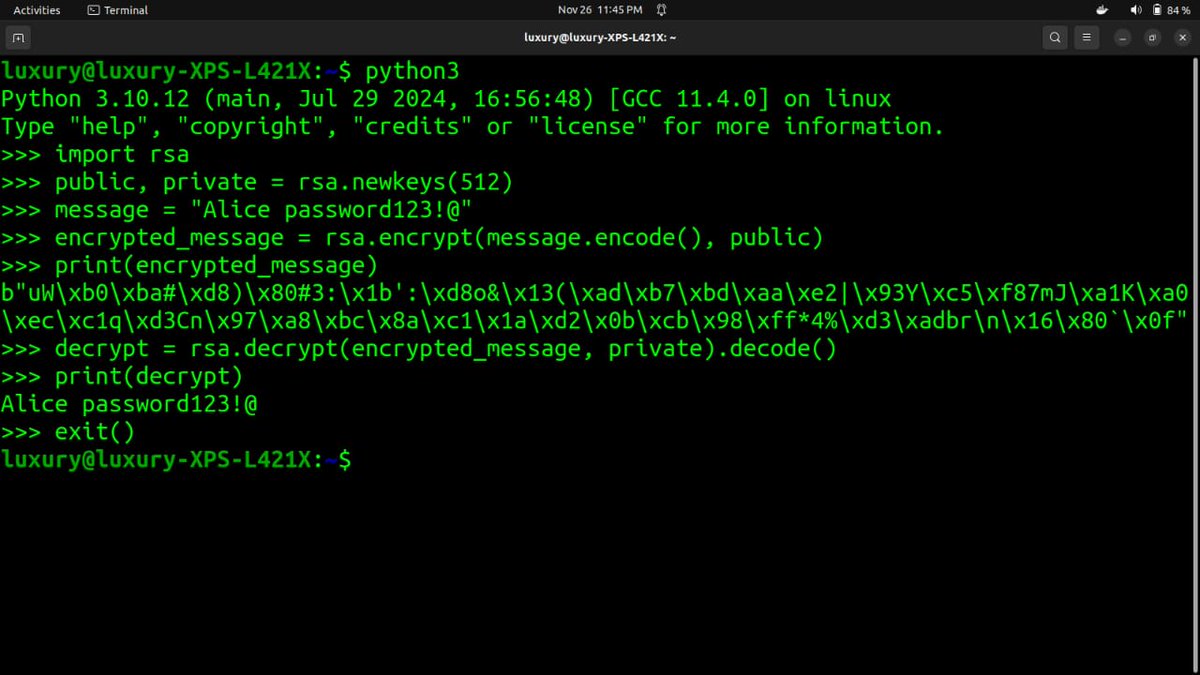
(4/11) 🌐 Symmetric encryption: Same key for encryption and decryption (e.g., AES). #SymmetricEncryption
Symmetric encryption uses a single key for both encryption and decryption, making it fast and efficient for large data volumes. However, secure key sharing is crucial. Commonly used for data at rest and internal file encryption. #DataSecurity #SymmetricEncryption #Encryption…

Symmetric encryption uses a single key for both encryption and decryption, making it fast and efficient for large data volumes. However, secure key sharing is crucial. Commonly used for data at rest and internal file encryption. #DataSecurity #SymmetricEncryption #Encryption…
8/20: You’ve probably heard of AES (Advanced Encryption Standard), the most widely used symmetric encryption method today. Governments and corporations trust it for sensitive data! 🛡️ #AES #SymmetricEncryption
5/20: Symmetric encryption uses the same key for both encryption and decryption. Think of it as a lock and key system that works both ways. 🔐 #SymmetricEncryption
Symmetric VS. Asymmetric encryption: 🔹 #SymmetricEncryption: One key for encryption and decryption. Fast but key distribution can be tricky. 🔹 #AsymmetricEncryption: Two keys – public and private. More secure for key exchange but slower.


Symmetric encryption uses a single key for both encryption and decryption, making it fast and efficient for large data volumes. However, secure key sharing is crucial. Commonly used for data at rest and internal file encryption. #DataSecurity #SymmetricEncryption #Encryption…

Types of Encryption and Cryptography Services. #cryptography #encryption #SymmetricEncryption #AsymmetricEncryption #digitalsignature #hashing #pki #confidentiality #integrity #authentication #nonrepudiation #proofofdelivery #cybersecurity #infosec #informationsecurity


Symmetric vs asymmetric encryption ............. #SymmetricEncryption, #AsymmetricEncryption, #DataEncryption, #EncryptionAlgorithms, #CyberSecurity, #EncryptionTechnology, #DataProtection, #EncryptionKeys, #EncryptionTools, #Cryptography

🔐Symmetric vs Asymmetric Encryption🔐 #Cyber #CyberSecurity #SymmetricEncryption #AsymmetricEncryption #Infosec #Encryption #DataSecurity #KnoeledgeSharing #DataProtection

There are two basic types of encryption - symmetric and asymmetric. As the name implies, #SymmetricEncryption uses the same key for both encryption and decryption. #AsymmetricEncryption uses a public key for encryption and a separate private key for decryption.

#mdpientropy Integrating Classical Preprocessing into an Optical Encryption Scheme mdpi.com/1099-4300/21/9… #symmetricencryption #allornothing #transform #opticalchannel #provablesecurity

#PrivacyPreserving #MedicalDataSharing System with #SymmetricEncryption Based on #Blockchain ✏️ Mingqi Hu, Yanli Ren and Cien Chen 🔗 brnw.ch/21wVKZv Viewed: 3000; Cited: 8 #mdpisymmetry

Confused about #SymmetricEncryption and #AsymmetricEncryption? 🤔 Get help deciphering the differences. #Encryption #Cryptography bit.ly/2nzYpX7

Which is more secure, symmetric or asymmetric encryption? Discover the details in our blog. ow.ly/Vfcv50WsQYN #EncryptionConsulting #EncryptionStrategy #SymmetricEncryption #AsymmetricEncryption #CyberSecurity #DataProtection #DigitalSecurity #TLS #HSM

Thread 2: Two main encryption types: Symmetric: One key for locking and unlocking data. Fast but tricky to share keys safely. Asymmetric: Uses two keys - public for encrypting, private for decrypting. Enhances security in sharing. #SymmetricEncryption #AsymmetricEncryption

Word of the Week: Symmetric Encryption – the art of using one secret key to lock and unlock your data. Efficient and effective, it’s a cornerstone of cloud security. Learn More → bit.ly/4ioGxok #CloudSecurity #Encryption #SymmetricEncryption

Explore the differences between #SymmetricEncryption and #AsymmetricEncryption, as well as how to evaluate the #encryption method for your enterprise. 🗝 bit.ly/2nD2n1l

Symmetric vs asymmetric #encryption: what’s the difference? How do they work and when to use them? Plus, we share some #BestPractices. What you should know about #symmetricencryption and #asymmetricencryption 👇 blog.mailfence.com/symmetric-vs-a… #infosec #cybersecurity #endtoendencryption

The Ultimate guide to understanding Symmetric Encryption! Know here : clickssl.net/blog/what-is-s… #SymmetricEncryption #Symmetrickeyalgorithm #SymmetricEncryptionAlgorithms

🔒 Today’s #wordoftheday is Secret Key (Symmetric) Cryptographic Algorithm! Symmetric algorithms rely on one key for both encryption and decryption. But how do we ensure that key stays secure in the quantum era? #SymmetricEncryption #SecretKey #QuantumSecurity

Keeping information secure is important, but do you know the difference between symmetric and asymmetric encryption? Comment your answer below! #Encryption101 #Cybersecurity #SymmetricEncryption #AsymmetricEncryption #DataSecurity #EncryptThis #TechTrivia #ProtectYourData

The Key Differences Between Symmetric VS Asymmetric Encryption Read Here :- ssl2buy.com/wiki/symmetric… #symmetricencryption #asymmetricencryption #blog #websecurity #cybersecurity #cybersecurityawareness

Yesterday in our GDSC Cybersecurity class, we dove into the world of encryption! 🛡️🔐 Learned the fundamentals of #AsymmetricEncryption and #SymmetricEncryption. Big thanks to all the students for their participation and enthusiasm! #CyberSecurity #GDSC #TechEducation

Something went wrong.
Something went wrong.
United States Trends
- 1. Cowboys 72.2K posts
- 2. LeBron 99.3K posts
- 3. Gibbs 19.5K posts
- 4. Lions 89.3K posts
- 5. Pickens 13.9K posts
- 6. #heatedrivalry 21.4K posts
- 7. #OnePride 10.3K posts
- 8. scott hunter 3,931 posts
- 9. Brandon Aubrey 7,156 posts
- 10. Ferguson 10.6K posts
- 11. #DALvsDET 6,131 posts
- 12. Eberflus 2,576 posts
- 13. Shang Tsung 24.2K posts
- 14. CeeDee 10.4K posts
- 15. Goff 8,579 posts
- 16. fnaf 2 24.6K posts
- 17. Paramount 18.7K posts
- 18. Warner Bros 17.4K posts
- 19. Bland 8,514 posts
- 20. DJ Reed N/A