#encryptionmethods 搜尋結果
What encryption methods are organizations using for data in Iaas/PaaS environments? 🔐 👇 #Encryption #EncryptionMethods #IaaS #PaaS
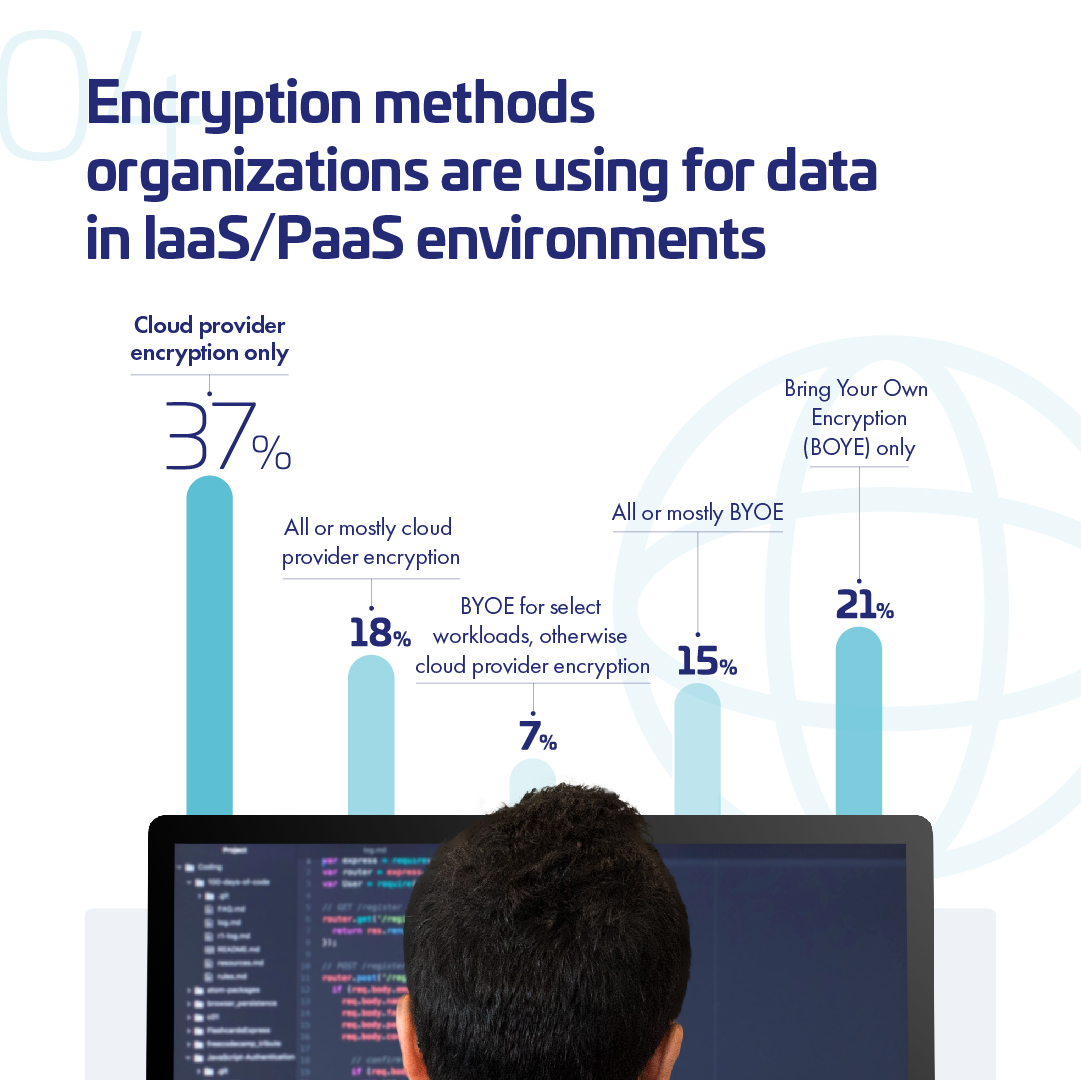
What encryption methods are organizations using for data in Iaas/PaaS environments? 🔐 👇 @ThalesCloudSec - buff.ly/34Ye5K1 #Encryption #EncryptionMethods #IaaS #PaaS

🏊 Dive into the world of cybersecurity with "The Art of Invisibility". 📖 🤓 Drawn from Mitnick's personal experiences as a hacker, this book illuminates real-life scenarios where a security breach could happen. 🛡️ #EncryptionMethods #MustRead #TechPros #EverydayNetizens

Having an encrypted phone will assure that your data will be kept private at all times. Smartphones cannot do this. #encrypt #mostsecurephone2021 #encryptionmethods #secureyourphone #technology #securechat #chatmail #encryptedphone #dataprotection #smartphones #skyphones

As quantum computers advance, encryption methods will need to keep up ow.ly/pEkM50Rrwf7 #QuantumComputing #EncryptionMethods #CyberSecurity #TechInnovation #DataProtection #FutureTech #TechTrends #ITSecurity
🔐🔓 Symmetric vs. Asymmetric: Meet the dynamic duo of encryption. One key or two? Learn how DES and RSA play their roles. 🤝 #CryptoKeys #EncryptionMethods
#Holder says ... #EncryptionMethods #EricHolder #GOOGLE #Jr #LawEnforcement #LawEnforcementOfficials tehlozangeleztimez.com/2014/09/30/hol…
Smartphones are quickly becoming our wallets, cameras, notebooks, even our personal safes. You wouldn't leave any of those just lying around for anyone to pick up and browse. This is why encrypted mobiles protect. #encryptedmobilephone #encryptionmethods #mostsecurephone2021

Which encryption method does your organization rely on most: symmetric, asymmetric, or hashing? Share your preferred approach and why it works best for your business. Let's discuss the pros and cons of different strategies! #EncryptionMethods #CyberSecurity #BusinessTech

Protecting your data is crucial. Discover the various encryption methods used to safeguard sensitive information. From symmetric to asymmetric encryption, we break down the techniques that keep your data secure. #DataSecurity #EncryptionMethods cloudavize.com/complete-guide…

Explore the world of modern encryption techniques. Discover how AES, RSA, and quantum encryption keep your data safe. youtu.be/PzCBjQ98igU #EncryptionMethods #InfoSec #DataPrivacy

What encryption methods are organizations using for data in Iaas/PaaS environments? 🔐 👇 @ThalesCloudSec - buff.ly/34Ye5K1 #Encryption #EncryptionMethods #IaaS #PaaS

Avast! #Holder says cellphone encryption ... #Apple #EncryptionMethods #EricHHolderJr #GOOGLE #LawEnforcement j.mp/1A9gUMT
Top 3 Myths About Homomorphic Encryption ... by Andrew Zola @DrewZola #datasecurity #encryptionmethods #itsecurityanddataprotection #privacy #security securityboulevard.com/2020/01/top-3-…
Explore the world of modern encryption techniques. Discover how AES, RSA, and quantum encryption keep your data safe. tinyurl.com/y69d2zep #EncryptionMethods #InfoSec #DataPrivacy

Andrew Zola @DrewZola shared: Top 3 Myths About Homomorphic Encryption #datasecurity #encryptionmethods #itsecurityanddataprotection #privacy #security securityboulevard.com/2020/01/top-3-…
@fogochain's network upgrades its security measures to protect against cross - chain bridge vulnerabilities using advanced encryption methods. #CrossChainSecurity #EncryptionMethods
Check out latest blog from Andrew Zola: @DrewZola Top 3 Myths About Homomorphic Encryption #datasecurity #encryptionmethods #itsecurityanddataprotection #privacy #security securityboulevard.com/2020/01/top-3-…
New #encryptionmethods may enable reliable, user-friendly authentication while protecting users’ #biometric data bit.ly/2fxEmTT
Choosing the right encryption methods is essential for effective data protection. Consider factors like data sensitivity, regulatory requirements, and performance to ensure the best fit for your organization. #DataPrivacy #EncryptionMethods
Explore the world of modern encryption techniques. Discover how AES, RSA, and quantum encryption keep your data safe. #EncryptionMethods #InfoSec #DataPrivacy
@fogochain's network upgrades its security measures to protect against cross - chain bridge vulnerabilities using advanced encryption methods. #CrossChainSecurity #EncryptionMethods
Explore the world of modern encryption techniques. Discover how AES, RSA, and quantum encryption keep your data safe. northlondonitsupport.com/ultimate-guide… #EncryptionMethods #InfoSec #DataPrivacy

Explore the world of modern encryption techniques. Discover how AES, RSA, and quantum encryption keep your data safe. youtu.be/PzCBjQ98igU #EncryptionMethods #InfoSec #DataPrivacy

Explore the world of modern encryption techniques. Discover how AES, RSA, and quantum encryption keep your data safe. tinyurl.com/y69d2zep #EncryptionMethods #InfoSec #DataPrivacy

🔒 Curious about how encryption keeps your data safe? This post explains different methods like AES, RSA, and quantum encryption. #EncryptionMethods #InfoSec #DataPrivacy #NovoIT buff.ly/3WeU5u2

Explore the world of modern encryption techniques. Discover how AES, RSA, and quantum encryption keep your data safe. #EncryptionMethods #InfoSec #DataPrivacy #AcadianaTech buff.ly/40aYSxO

Protecting your data is crucial. Discover the various encryption methods used to safeguard sensitive information. From symmetric to asymmetric encryption, we break down the techniques that keep your data secure. #DataSecurity #EncryptionMethods cloudavize.com/complete-guide…

Which encryption method does your organization rely on most: symmetric, asymmetric, or hashing? Share your preferred approach and why it works best for your business. Let's discuss the pros and cons of different strategies! #EncryptionMethods #CyberSecurity #BusinessTech

🏊 Dive into the world of cybersecurity with "The Art of Invisibility". 📖 🤓 Drawn from Mitnick's personal experiences as a hacker, this book illuminates real-life scenarios where a security breach could happen. 🛡️ #EncryptionMethods #MustRead #TechPros #EverydayNetizens

As quantum computers advance, encryption methods will need to keep up ow.ly/pEkM50Rrwf7 #QuantumComputing #EncryptionMethods #CyberSecurity #TechInnovation #DataProtection #FutureTech #TechTrends #ITSecurity

🔐🔓 Symmetric vs. Asymmetric: Meet the dynamic duo of encryption. One key or two? Learn how DES and RSA play their roles. 🤝 #CryptoKeys #EncryptionMethods
Choosing the right encryption methods is essential for effective data protection. Consider factors like data sensitivity, regulatory requirements, and performance to ensure the best fit for your organization. #DataPrivacy #EncryptionMethods
What encryption methods are organizations using for data in Iaas/PaaS environments? 🔐 👇 #Encryption #EncryptionMethods #IaaS #PaaS

🏊 Dive into the world of cybersecurity with "The Art of Invisibility". 📖 🤓 Drawn from Mitnick's personal experiences as a hacker, this book illuminates real-life scenarios where a security breach could happen. 🛡️ #EncryptionMethods #MustRead #TechPros #EverydayNetizens

What encryption methods are organizations using for data in Iaas/PaaS environments? 🔐 👇 @ThalesCloudSec - buff.ly/34Ye5K1 #Encryption #EncryptionMethods #IaaS #PaaS

As quantum computers advance, encryption methods will need to keep up ow.ly/pEkM50Rrwf7 #QuantumComputing #EncryptionMethods #CyberSecurity #TechInnovation #DataProtection #FutureTech #TechTrends #ITSecurity

What encryption methods are organizations using for data in Iaas/PaaS environments? 🔐 👇 @ThalesCloudSec - buff.ly/34Ye5K1 #Encryption #EncryptionMethods #IaaS #PaaS

Which encryption method does your organization rely on most: symmetric, asymmetric, or hashing? Share your preferred approach and why it works best for your business. Let's discuss the pros and cons of different strategies! #EncryptionMethods #CyberSecurity #BusinessTech

Explore the world of modern encryption techniques. Discover how AES, RSA, and quantum encryption keep your data safe. youtu.be/PzCBjQ98igU #EncryptionMethods #InfoSec #DataPrivacy

Explore the world of modern encryption techniques. Discover how AES, RSA, and quantum encryption keep your data safe. northlondonitsupport.com/ultimate-guide… #EncryptionMethods #InfoSec #DataPrivacy

Having an encrypted phone will assure that your data will be kept private at all times. Smartphones cannot do this. #encrypt #mostsecurephone2021 #encryptionmethods #secureyourphone #technology #securechat #chatmail #encryptedphone #dataprotection #smartphones #skyphones

Smartphones are quickly becoming our wallets, cameras, notebooks, even our personal safes. You wouldn't leave any of those just lying around for anyone to pick up and browse. This is why encrypted mobiles protect. #encryptedmobilephone #encryptionmethods #mostsecurephone2021

Protecting your data is crucial. Discover the various encryption methods used to safeguard sensitive information. From symmetric to asymmetric encryption, we break down the techniques that keep your data secure. #DataSecurity #EncryptionMethods cloudavize.com/complete-guide…

Explore the world of modern encryption techniques. Discover how AES, RSA, and quantum encryption keep your data safe. tinyurl.com/y69d2zep #EncryptionMethods #InfoSec #DataPrivacy

Explore the world of modern encryption techniques. Discover how AES, RSA, and quantum encryption keep your data safe. #EncryptionMethods #InfoSec #DataPrivacy #AcadianaTech buff.ly/40aYSxO

🔒 Curious about how encryption keeps your data safe? This post explains different methods like AES, RSA, and quantum encryption. #EncryptionMethods #InfoSec #DataPrivacy #NovoIT buff.ly/3WeU5u2

Something went wrong.
Something went wrong.
United States Trends
- 1. Jets 75.6K posts
- 2. Bengals 44.5K posts
- 3. Giants 88K posts
- 4. Eagles 102K posts
- 5. Falcons 36.5K posts
- 6. Zac Taylor 3,847 posts
- 7. Caleb 35.3K posts
- 8. Bears 64.2K posts
- 9. Ravens 47.7K posts
- 10. Browns 42.7K posts
- 11. Myles Garrett 6,759 posts
- 12. Dolphins 26.8K posts
- 13. Skattebo 40K posts
- 14. 49ers 29.3K posts
- 15. Andy Dalton 8,716 posts
- 16. Drake Maye 13.2K posts
- 17. Justin Fields 6,659 posts
- 18. Dillon Gabriel 4,920 posts
- 19. Texans 23.8K posts
- 20. Tyler Huntley 4,221 posts





















