#geekpwn ผลการค้นหา
Had a great time with DARWINATOR from Drones Autonomous Systems Lab, University of Nevada. The Humanoid robot and Hexapod robot surprised us by getting out of a parcel, placing a covert listening device & pressing password of a safe in order to open it. #GeekPwn #defcon #maker




#PS4 4.01 Jailbreak showcased by Chinese hackers at Geekpwn convention wololo.net/2016/10/24/ps4… #GeekPwn #PS4Jailbreak
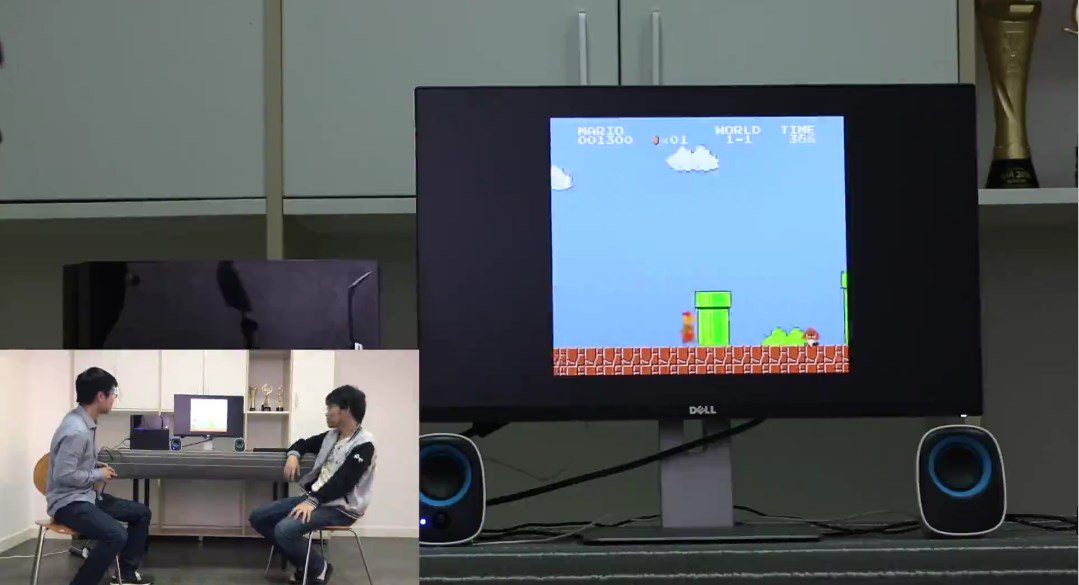
NOTE: The rules set no limitation on the PWN target at #GeekPwn, geeks can choose their targets freely (from smart devices to AI services).

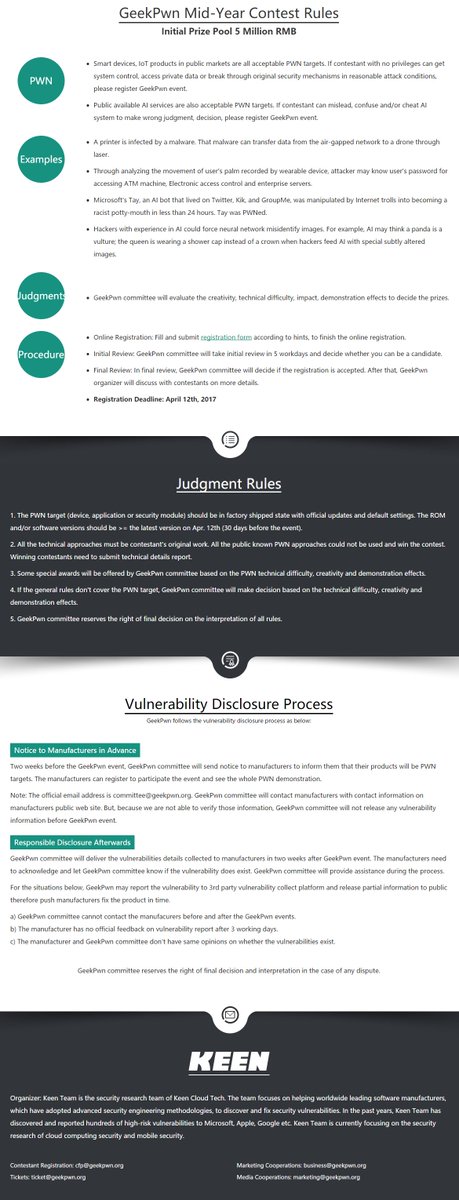
We are so excited to announce that #GeekPwn will be @DEFCON 26 this August! Come on by and check us out at geekpwn.org. #robot #CAAD #whitehats
The unique moment: empty hall an hour before Chinese cybersecurity conference #GeekPwn. Empty hall. Chinese conference.

Yeah, man, we did it! We got main achievements on the level: new point of presence on the map, new friends and tons of ideas. #GeekPwn

Ever wondered what a Chinese hacker looks like? Here's one at #geekpwn contest in Macau explaining smartphone hack
Biometric authentication technologies are used for the machine identification of individuals. Haibing Wang, director of GeekPwn Lab, will demonstrate some hack examples shown in previous #GeekPwn events. (pics of GeekPwn2017 SH)



#GeekPwn held a big worldwide security geek contest yesterday in Shanghai. #TopXGun is one of their tech partners.



You can find us @defcon Caesar s’ this morning, from 1000 to 1300, Main Stage of Contest Area.#GeekPwn #Defcon #CAAD




#elotrolado #GeekPwn Linux vuelve a PlayStation 4 con el firmware 4.01 cybernovanet.wordpress.com/2016/10/25/elo…

Deep Learning is improving security capabilities, on the other side, AI is in the presence of attackers. (Prof. Dawn Song, UC Bekeley) #AI #machinelearning #GeekPwn #security #cybersecurity

#VMware fixed critical VM Escape bug demonstrated at #Geekpwn #hacking contest. securityaffairs.co/wordpress/1396… #securityaffairs #hacking
securityaffairs.com
VMware fixed critical VM Escape bug demonstrated at Geekpwn hacking contest
VMware fixed three flaws in multiple products, including a virtual machine escape issue exploited at the GeekPwn 2022 hacking competition.
#VMware fixed critical VM Escape bug demonstrated at #Geekpwn #hacking contest securityaffairs.co/wordpress/1396… #securityaffairs #hacking
securityaffairs.com
VMware fixed critical VM Escape bug demonstrated at Geekpwn hacking contest
VMware fixed three flaws in multiple products, including a virtual machine escape issue exploited at the GeekPwn 2022 hacking competition.
Blocco impronte digitali ? Rotto in 20 minuti Durante la conferenza #GeekPwn 2019 a #Shanghai ricercatori di #CyberSecurity hanno chiesto ad alcuni tra il pubblico di toccare un vetro. Le impronte digitali lasciate nel vetro sono state poi fotografate…lnkd.in/g2xp_nN
Did you miss the #GeekPwn at @defcon26? A friendly reminder - a couple of important deadlines are approaching! Check out for more: 2018.geekpwn.org/en/index.html #hacker #bugbounty #inforsec
.@PRNewswire All the latest details from #GeekPWN 2018 courtesy of PR Newswire! Have you been out to Las Vegas for @GeekPwn? prnewswire.com/news-releases/…
Had a great time with DARWINATOR from Drones Autonomous Systems Lab, University of Nevada. The Humanoid robot and Hexapod robot surprised us by getting out of a parcel, placing a covert listening device & pressing password of a safe in order to open it. #GeekPwn #defcon #maker




You can find us @defcon Caesar s’ this morning, from 1000 to 1300, Main Stage of Contest Area.#GeekPwn #Defcon #CAAD




“Weapons for Dog Fight: Adapting Malware to Anti-Detection based on GAN ” with speakers Zhuang Zhang, Bo Shi and Hangfeng Dong from Tencent Yunding Laboratory@YDLab9 on Friday, August 10. #defcon26 #CAADVillage #GeekPwn bit.ly/2LtE5Sn
Really excited to be part of #GEEKPWN Party on Friday at 20:30, located in Scenic at Flamingo It’s going to be pretty exciting, entertaining & educational!!! Hope to hug you there!!! 🤗😊🤗
Reminder: #GeekPwn Contest will be held on Aug 10 (Friday) from 10:00 - 13:00 in the Contest Area at Caesar's Palace. Hope to see you there.
Now that you’ve had some time to absorb the epic Village list, we’ve got some more goodies for you. The #defcon26 Contests and Events page is now LIVE! Commence pre-con recon. defcon.org/html/defcon-26…

People ask us: what makes you hackers? Here’s our answer: we are not made for this, we‘re born for #hacking! #GeekPwn calls for PWN geekpwn.org #whitehat #ethicalhacking #AIsecurity youtube.com/watch?v=Ygqk_R…
youtube.com
YouTube
GeekPwn Highlights, started from 2014
@ChaitinTech Lab is one of top hacker teams in the world, which is also a frequent contestant at #GeekPwn. From main stream brands of routers to PS4, they did an excellent job of finding bugs. Looking forward to seeing more talents at geekpwn.org
#PS4 4.01 Jailbreak showcased by Chinese hackers at Geekpwn convention wololo.net/2016/10/24/ps4… #GeekPwn #PS4Jailbreak

Had a great time with DARWINATOR from Drones Autonomous Systems Lab, University of Nevada. The Humanoid robot and Hexapod robot surprised us by getting out of a parcel, placing a covert listening device & pressing password of a safe in order to open it. #GeekPwn #defcon #maker




NOTE: The rules set no limitation on the PWN target at #GeekPwn, geeks can choose their targets freely (from smart devices to AI services).


We are so excited to announce that #GeekPwn will be @DEFCON 26 this August! Come on by and check us out at geekpwn.org. #robot #CAAD #whitehats
The unique moment: empty hall an hour before Chinese cybersecurity conference #GeekPwn. Empty hall. Chinese conference.

Biometric authentication technologies are used for the machine identification of individuals. Haibing Wang, director of GeekPwn Lab, will demonstrate some hack examples shown in previous #GeekPwn events. (pics of GeekPwn2017 SH)



You can find us @defcon Caesar s’ this morning, from 1000 to 1300, Main Stage of Contest Area.#GeekPwn #Defcon #CAAD




Yeah, man, we did it! We got main achievements on the level: new point of presence on the map, new friends and tons of ideas. #GeekPwn

Deep Learning is improving security capabilities, on the other side, AI is in the presence of attackers. (Prof. Dawn Song, UC Bekeley) #AI #machinelearning #GeekPwn #security #cybersecurity

#GeekPwn held a big worldwide security geek contest yesterday in Shanghai. #TopXGun is one of their tech partners.



Coming up on @AJEnglish China's best smart device hackers are competing for top honours in #macau #geekpwn

“Robust Physical-World Attacks on Machine Learning Models” by Bo Li from UC Berkeley, at #GeekPwn #GANs, Nov. 13th goo.gl/xjTDPt

“How dose this girl unlock the phone with nose?“ Nich Stephen from UC Santa Barbara will disclose more details in ”Behind the PWN of the TrustZone” at #GeekPwn. #whitehat #security #trustzone goo.gl/Hj57rd
Something went wrong.
Something went wrong.
United States Trends
- 1. $NVDA 80.2K posts
- 2. Jensen 26.2K posts
- 3. Peggy 38.4K posts
- 4. GeForce Season 6,200 posts
- 5. NASA 55.8K posts
- 6. Sam Harris N/A
- 7. #YIAYalpha N/A
- 8. Arabic Numerals 5,698 posts
- 9. Sumrall 2,580 posts
- 10. Stargate 7,620 posts
- 11. Judge Smith 4,192 posts
- 12. Martha 20.6K posts
- 13. Comey 59K posts
- 14. Potomac N/A
- 15. #WWESuperCardNewSeason 1,265 posts
- 16. #2Kgiveaway 1,242 posts
- 17. WNBA 9,584 posts
- 18. Kwame 6,599 posts
- 19. #WickedWaysToMakeABuck N/A
- 20. Tarris Reed N/A