#iencrypt risultati di ricerca
Múltiples incidentes por #Ransomware en España 🇪🇸 empresas como Everis, Accenture, La Ser y KPMG afectadas. Posible #iEncrypt a través de vulnerabilidad 0day en componentet "Bonjour Updater" incluído en iTunes/iCloud para Windows. Parcha ya!!!
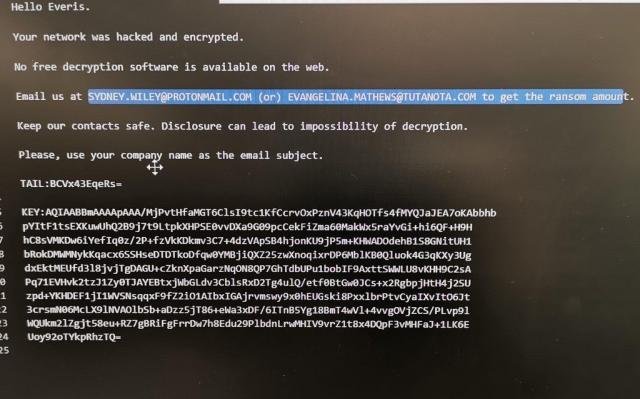
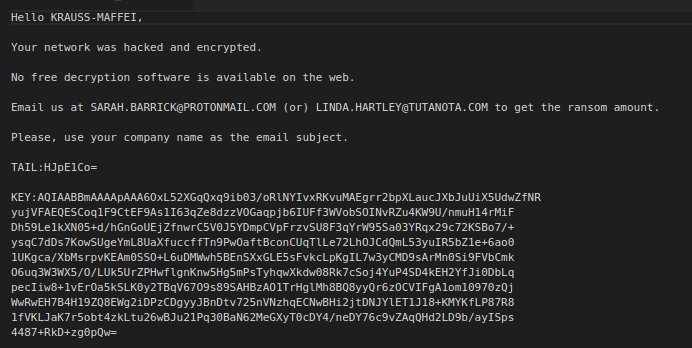
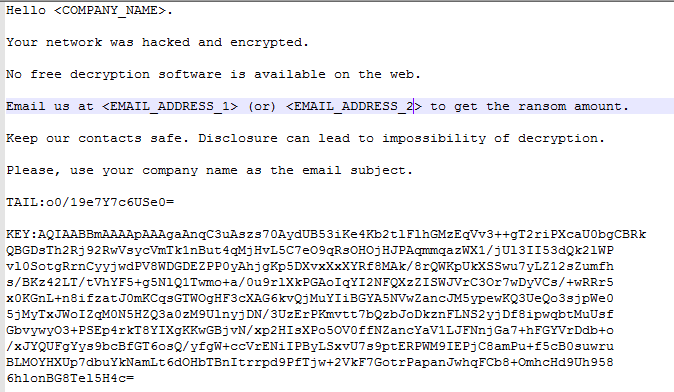
#IEncrypt #Ransomware submitted to ID Ransomware with email addresses "[email protected]" and "[email protected]"
Wake the fuck up!!! The future’s safe as the Australian housing market, and reality is already providing the painful pin to the largest housing bubble humanities ever witnessed. Take the red pill. #IEncrypt #SurveillanceSingularity
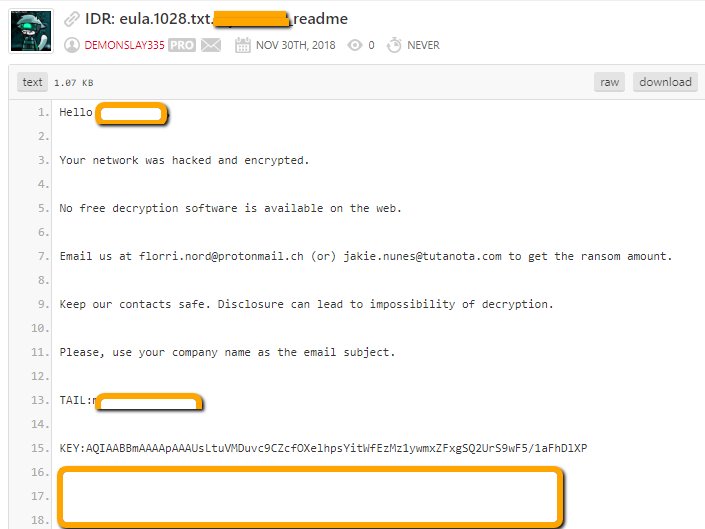
#BitPaymer / #IEncrypt #Ransomware 🆕Extension ".0riz0n" = "Orizon GmbH company"🧐 "The ransom note include the victim’s name, and the file extension appended to encrypted files is also custom to use a representation of the victim’s name" MD5: 34441b7389336a401f4a9acb79172e40
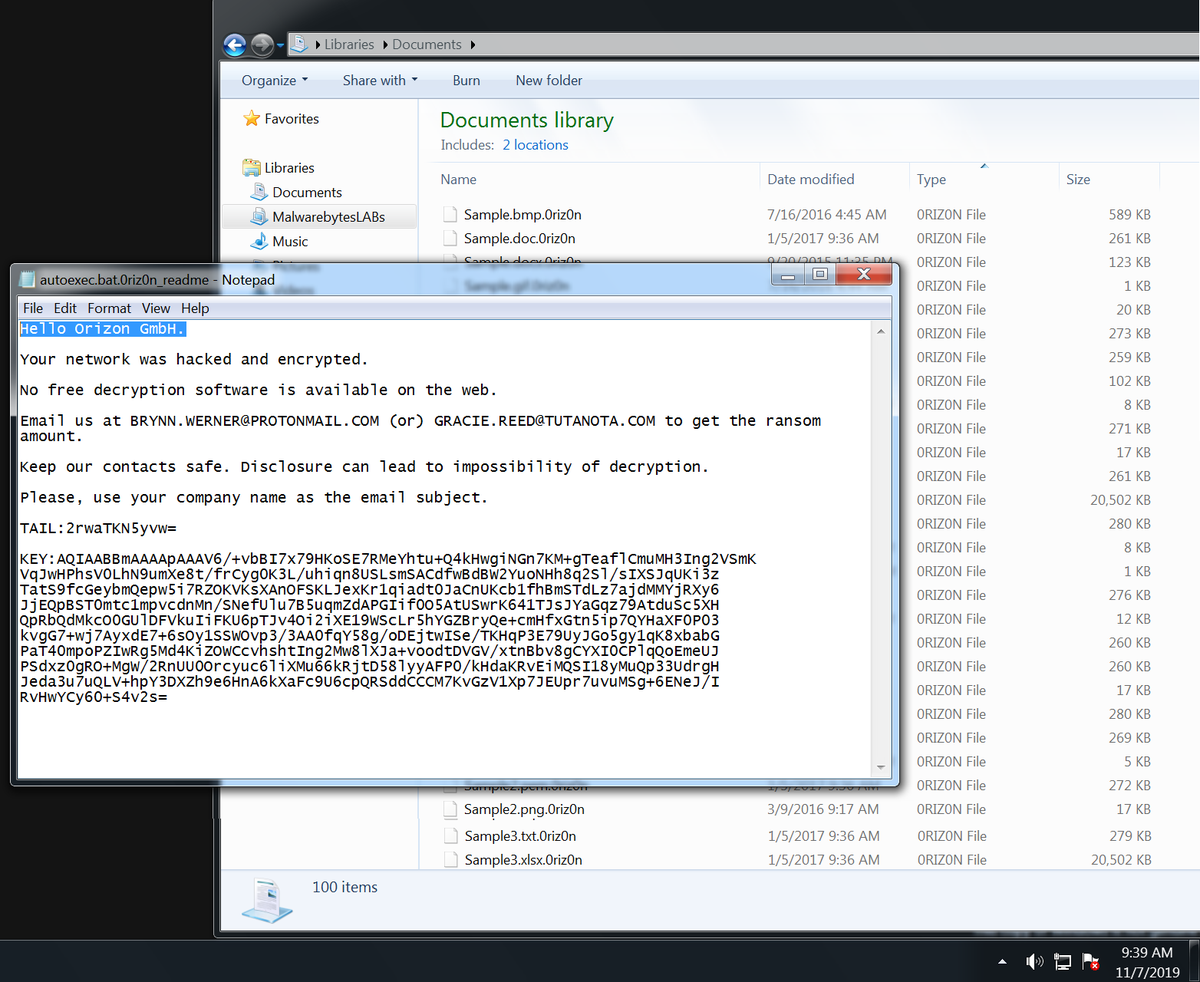
#BitPaymer/ #IEncrypt utiliza un cargador completamente personalizado el día del ataque, generalmente solo 2-3 horas antes. En donde el nombre de la compañía se utiliza como ext y en la nota de rescate, por ej: - Extensión: .3v3r1s = #Everis MD5: 5176924a0fc528db77e9ff2b3afa432b

Is it just a dream? Nineteen Eighty-Four was meant to just be a movie... But as the cold hard boot is pressed against our faces, and the Encryption Access bill is signed with bi-partisan support, a small piece of me, and a large part of liberty & freedom dies #iEncrypt #Australia

The future is now, it’s digital, it’s unstoppable and it’s fully end-2-end encrypted. The states ability to control information is an analogue monolith, a 2400 baud modem operating in a gigabit digital-fibre connected world. They never stood a chance. #iEncrypt $BTC

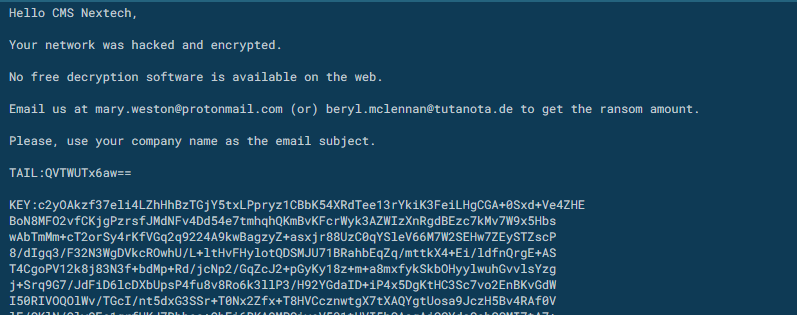
Seems be a custom #IEncrypt ransomware sample targeting the US company CMS Nextech. extension_file : cmsnwned extension_readme : cmsnwned_readme cc @demonslay335 @VK_Intel @JAMESWT_MHT @James_inthe_box
Thnks !!! Not Tor address because are different versions =) And here we go again, company "Grupo Thermotek" affected by #iEncrypt (aka #BitPaymer) ransomware: Ext: grupothermot3k Note: .grupothermot3k_readme Maybe via fake browser update, filename: GoogleUpdate.exe

The life of an Incident Responder, one minute I am enjoying my Friday, thinking about different beverages I will shortly be consuming. Then the call comes in......this time #IEncrypt ransomware, hundreds of machines and servers gone.

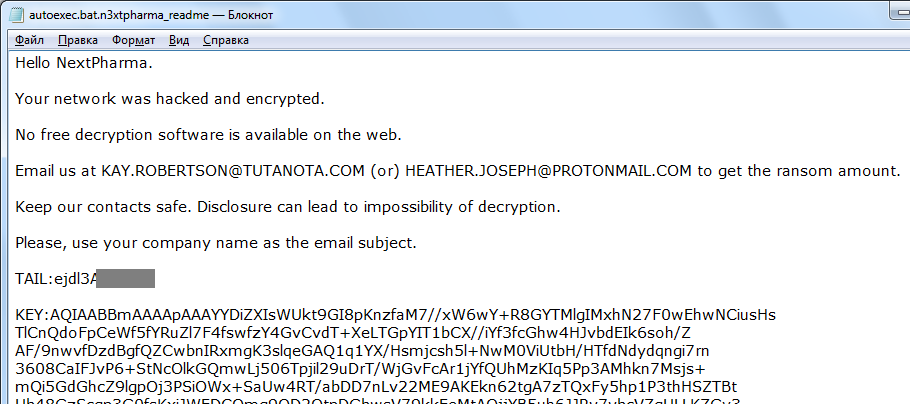
Update of #IEncrypt #Ransomware id-ransomware.blogspot.com/2018/11/iencry… Extension: .n3xtpharma Note: original_filename.n3xtpharma_readme Sample: autoexec.bat.n3xtpharma_readme Email: [email protected], [email protected] Thanks to @Emm_ADC_Soft
Account With #AdminPrivileges Abused To Install #BitPaymer (#iEncrypt) #Ransomware Via #PsExec - bit.ly/2InBo2N-Ttx @TrendMicro ➡️ #Organizations #CyberRisks #CyberThreats #PowerShell #InfoSec #SecurityBreach #CyberAttacks #EndpointSecurity #Backdoor #CyberSecurity

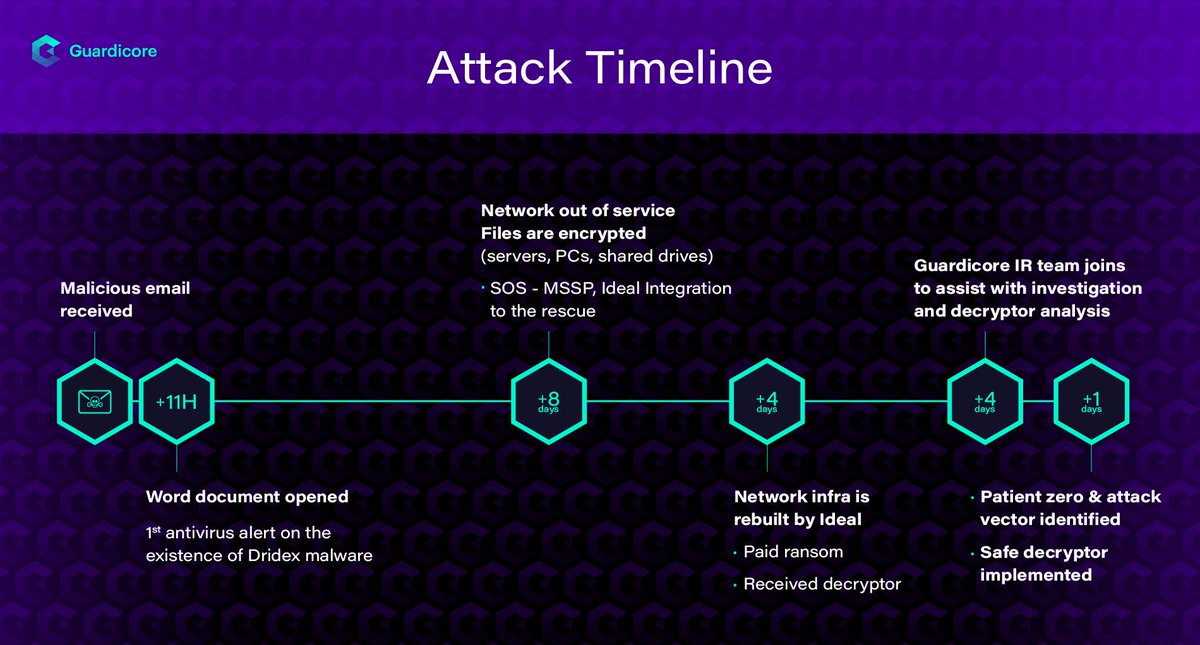
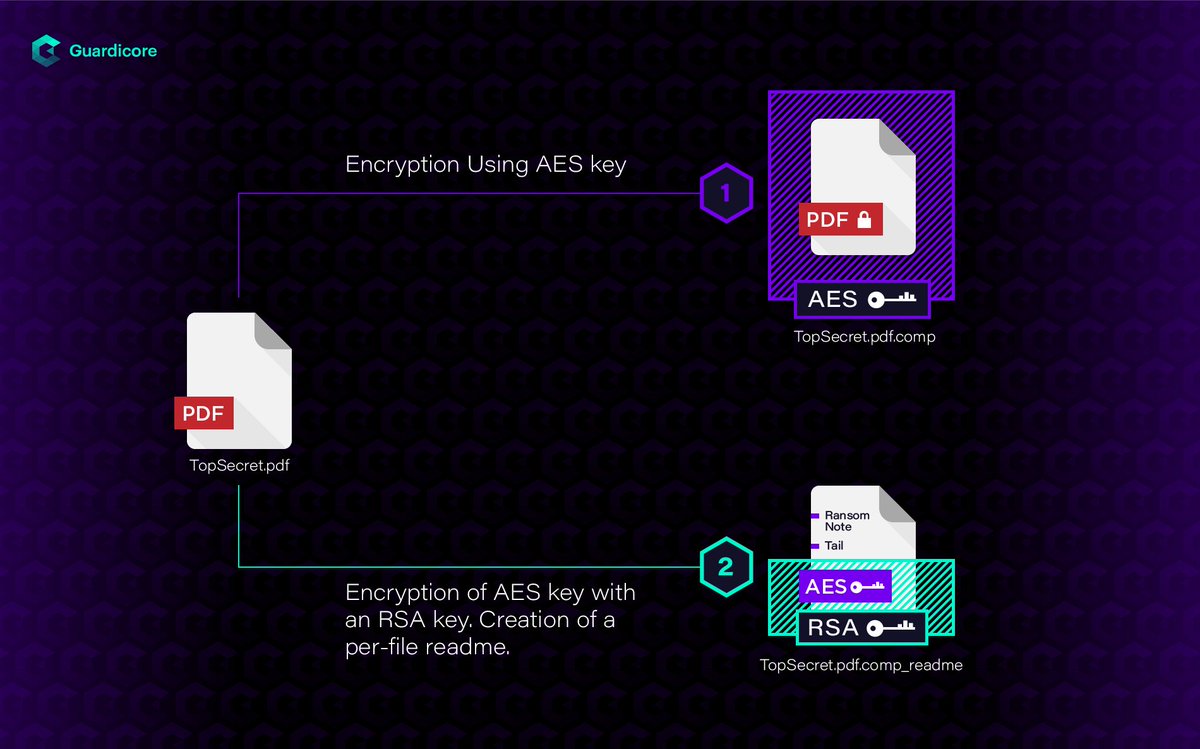
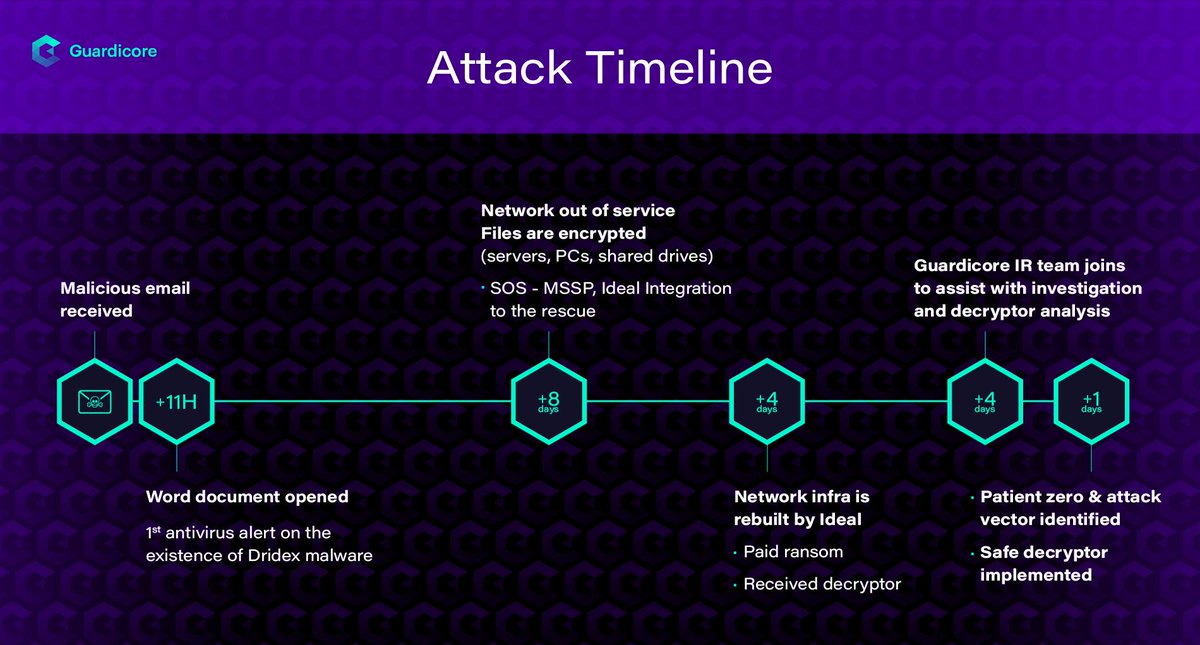
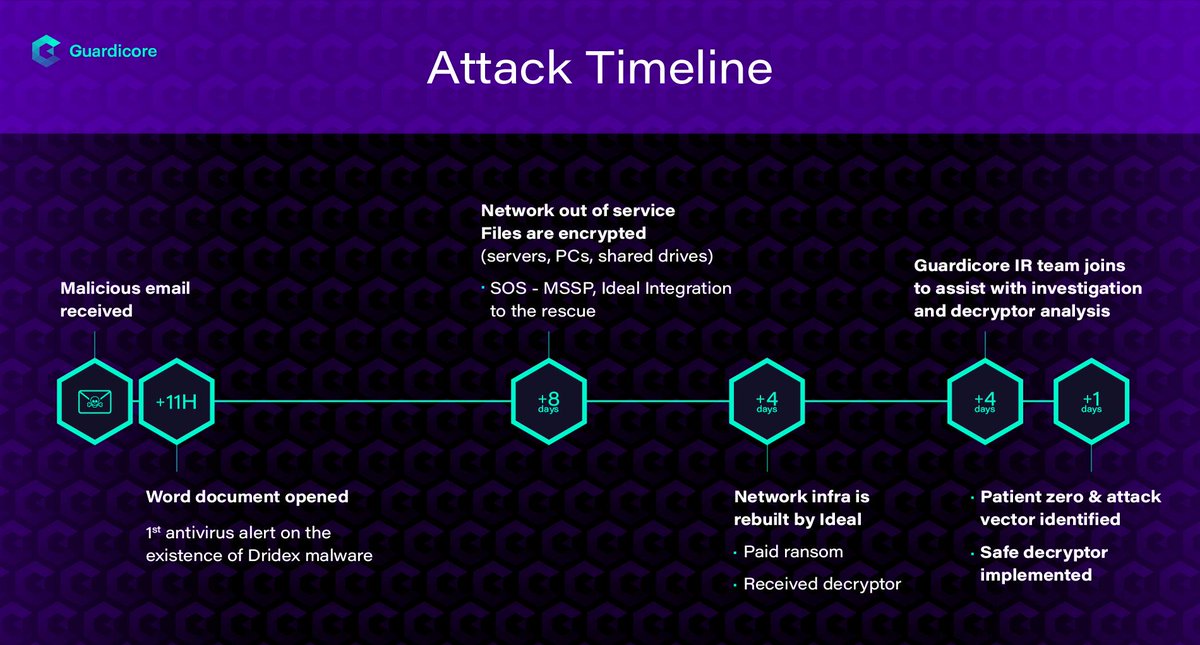
An investigation by @Guardicore's Labs team of a recent Cyber attack by #Dridex, incorporating an #IEncrypt #Ransomware variant. and we're also providing an #opensource decryptor. guardicore.com/2019/04/irespo… @ace__pace @OfriZiv
Ahora rumores apuntan a #iEncrypt a través de vulnerabilidad 0day en componente "Bonjour Updater" incluído en iTunes/iCloud para Windows. Tendría sentido si los usuarios pueden instalar iTunes porque tienen admin local. #Ransomware
No se ha revelado a qué familia pertenece el malware que atacó los sistemas de Everis, pero un estudio de VirusTotal indicó que el responsable podría ser el programa #BitPaymer/#IEncrypt. bit.ly/33ubEc3

Sicherheitsanalyse von Guardicore Labs @OphirHarpaz über eine neue #IEncrypt-Variante: Als Backups gegen #Ransomware nicht schützten buff.ly/2GcXcMq
Según los datos, el #ransomware que está afectando a la Universidad Santo Tomas 🇨🇱 podría ser una variante de #IEncrypt (aka #Bitpaymer). Extensión ".s4nt0t0m4s" Nota: !santo_tomas_readme.txt Recuerdan el caso Everis 🇪🇸 ? #Dridex -> Empire PowerShell -> IEncrypt 🚨
Según los datos, el #ransomware que está afectando a la Universidad Santo Tomas 🇨🇱 podría ser una variante de #IEncrypt (aka #Bitpaymer). Extensión ".s4nt0t0m4s" Nota: !santo_tomas_readme.txt Recuerdan el caso Everis 🇪🇸 ? #Dridex -> Empire PowerShell -> IEncrypt 🚨
The life of an Incident Responder, one minute I am enjoying my Friday, thinking about different beverages I will shortly be consuming. Then the call comes in......this time #IEncrypt ransomware, hundreds of machines and servers gone.

This still one variant of #IEncrypt #Ransomware id-ransomware.blogspot.com/2018/11/iencry… A little later, I will add this as an update to the main article. Thanks!
Thnks !!! Not Tor address because are different versions =) And here we go again, company "Grupo Thermotek" affected by #iEncrypt (aka #BitPaymer) ransomware: Ext: grupothermot3k Note: .grupothermot3k_readme Maybe via fake browser update, filename: GoogleUpdate.exe

Watch Out Windows Users! #Cybercriminals behind #BitPaymer & #iEncrypt #ransomwareattacks found exploiting zero-day vulnerability affecting a little-known component that comes bundled with Apple's iTunes & iCloud for Windows to evade antivirus det. thehackernews.com/2019/10/apple-…

No se ha revelado a qué familia pertenece el malware que atacó los sistemas de Everis, pero un estudio de VirusTotal indicó que el responsable podría ser el programa #BitPaymer/#IEncrypt. bit.ly/33ubEc3

#BitPaymer / #IEncrypt #Ransomware 🆕Extension ".0riz0n" = "Orizon GmbH company"🧐 "The ransom note include the victim’s name, and the file extension appended to encrypted files is also custom to use a representation of the victim’s name" MD5: 34441b7389336a401f4a9acb79172e40

#BitPaymer/ #IEncrypt utiliza un cargador completamente personalizado el día del ataque, generalmente solo 2-3 horas antes. En donde el nombre de la compañía se utiliza como ext y en la nota de rescate, por ej: - Extensión: .3v3r1s = #Everis MD5: 5176924a0fc528db77e9ff2b3afa432b

Seems be a custom #IEncrypt ransomware sample targeting the US company CMS Nextech. extension_file : cmsnwned extension_readme : cmsnwned_readme cc @demonslay335 @VK_Intel @JAMESWT_MHT @James_inthe_box


Hi @demonslay335, would be possible to decrypt files affected by #BitPaymer #iEncrypt through id-ransomware.malwarehunterteam.com/index.php?
#BitPaymer #iEncrypt: - La infiltración inicial generalmente se obtiene a través de correos electrónicos de phishing que entregan #Dridex - Obtienen las credenciales AD, y durante el fin de semana implementan el ransomware en la red ya comprometida.
Múltiples incidentes por #Ransomware en España #iEncrypt a través de vulnerabilidad 0day en "Bonjour Updater" incluído en iTunes/iCloud para Windows/Mac Os. Si tenéis un iPad iPhone borrar ese programa si no queréis quedaros son archivos. @HardwareSfera @elchapuzas
Ahora rumores apuntan a #iEncrypt a través de vulnerabilidad 0day en componente "Bonjour Updater" incluído en iTunes/iCloud para Windows. Tendría sentido si los usuarios pueden instalar iTunes porque tienen admin local. #Ransomware
Múltiples incidentes por #Ransomware en España 🇪🇸 empresas como Everis, Accenture, La Ser y KPMG afectadas. Posible #iEncrypt a través de vulnerabilidad 0day en componentet "Bonjour Updater" incluído en iTunes/iCloud para Windows. Parcha ya!!!

Múltiples incidentes por #Ransomware en España 🇪🇸 empresas como Everis, Accenture, La Ser y KPMG afectadas. Posible #iEncrypt a través de vulnerabilidad 0day en componentet "Bonjour Updater" incluído en iTunes/iCloud para Windows. Parcha ya!!!

#IEncrypt #Ransomware submitted to ID Ransomware with email addresses "[email protected]" and "[email protected]"

#BitPaymer / #IEncrypt #Ransomware 🆕Extension ".0riz0n" = "Orizon GmbH company"🧐 "The ransom note include the victim’s name, and the file extension appended to encrypted files is also custom to use a representation of the victim’s name" MD5: 34441b7389336a401f4a9acb79172e40

Wake the fuck up!!! The future’s safe as the Australian housing market, and reality is already providing the painful pin to the largest housing bubble humanities ever witnessed. Take the red pill. #IEncrypt #SurveillanceSingularity
#BitPaymer/ #IEncrypt utiliza un cargador completamente personalizado el día del ataque, generalmente solo 2-3 horas antes. En donde el nombre de la compañía se utiliza como ext y en la nota de rescate, por ej: - Extensión: .3v3r1s = #Everis MD5: 5176924a0fc528db77e9ff2b3afa432b

#BitPaymer #iEncrypt: - La infiltración inicial generalmente se obtiene a través de correos electrónicos de phishing que entregan #Dridex - Obtienen las credenciales AD, y durante el fin de semana implementan el ransomware en la red ya comprometida.

Seems be a custom #IEncrypt ransomware sample targeting the US company CMS Nextech. extension_file : cmsnwned extension_readme : cmsnwned_readme cc @demonslay335 @VK_Intel @JAMESWT_MHT @James_inthe_box


Is it just a dream? Nineteen Eighty-Four was meant to just be a movie... But as the cold hard boot is pressed against our faces, and the Encryption Access bill is signed with bi-partisan support, a small piece of me, and a large part of liberty & freedom dies #iEncrypt #Australia

Thnks !!! Not Tor address because are different versions =) And here we go again, company "Grupo Thermotek" affected by #iEncrypt (aka #BitPaymer) ransomware: Ext: grupothermot3k Note: .grupothermot3k_readme Maybe via fake browser update, filename: GoogleUpdate.exe

The future is now, it’s digital, it’s unstoppable and it’s fully end-2-end encrypted. The states ability to control information is an analogue monolith, a 2400 baud modem operating in a gigabit digital-fibre connected world. They never stood a chance. #iEncrypt $BTC

Update of #IEncrypt #Ransomware id-ransomware.blogspot.com/2018/11/iencry… Extension: .n3xtpharma Note: original_filename.n3xtpharma_readme Sample: autoexec.bat.n3xtpharma_readme Email: [email protected], [email protected] Thanks to @Emm_ADC_Soft

Account With #AdminPrivileges Abused To Install #BitPaymer (#iEncrypt) #Ransomware Via #PsExec - bit.ly/2InBo2N-Ttx @TrendMicro ➡️ #Organizations #CyberRisks #CyberThreats #PowerShell #InfoSec #SecurityBreach #CyberAttacks #EndpointSecurity #Backdoor #CyberSecurity

The life of an Incident Responder, one minute I am enjoying my Friday, thinking about different beverages I will shortly be consuming. Then the call comes in......this time #IEncrypt ransomware, hundreds of machines and servers gone.

An investigation by @Guardicore's Labs team of a recent Cyber attack by #Dridex, incorporating an #IEncrypt #Ransomware variant. and we're also providing an #opensource decryptor. guardicore.com/2019/04/irespo… @ace__pace @OfriZiv

Sicherheitsanalyse von Guardicore Labs @OphirHarpaz über eine neue #IEncrypt-Variante: Als Backups gegen #Ransomware nicht schützten buff.ly/2GcXcMq

Watch Out Windows Users! #Cybercriminals behind #BitPaymer & #iEncrypt #ransomwareattacks found exploiting zero-day vulnerability affecting a little-known component that comes bundled with Apple's iTunes & iCloud for Windows to evade antivirus det. thehackernews.com/2019/10/apple-…

No se ha revelado a qué familia pertenece el malware que atacó los sistemas de Everis, pero un estudio de VirusTotal indicó que el responsable podría ser el programa #BitPaymer/#IEncrypt. bit.ly/33ubEc3

#ICYMI @Guardicore Labs superstars @OphirHarpaz & Danielle Kuznets reveal research focused on a strain of #Dridex and #IEncrypt #Ransomware. They created a safe decryptor that helped a customer to recover from the attack. bit.ly/2GcPmlH
Something went wrong.
Something went wrong.
United States Trends
- 1. #FaithFreedomNigeria 1,242 posts
- 2. Zeraora 5,767 posts
- 3. Peggy 25.6K posts
- 4. Good Wednesday 31.4K posts
- 5. #wednesdaymotivation 6,716 posts
- 6. #LosVolvieronAEngañar 1,614 posts
- 7. Hump Day 14.8K posts
- 8. Dearborn 315K posts
- 9. #Wednesdayvibe 2,203 posts
- 10. #MissUniverse 19.6K posts
- 11. Berseria N/A
- 12. Luxray N/A
- 13. Cory Mills 16.6K posts
- 14. Jessica Tisch N/A
- 15. Happy Hump 9,499 posts
- 16. Semrush N/A
- 17. $NVDA 41.5K posts
- 18. For God 225K posts
- 19. $TGT 4,669 posts
- 20. Gettysburg Address N/A