#internalpentest search results
PeekABoo - Tool To Enable Remote Desktop On The Targeted Machine j.mp/2WFFeYR #InfrastructureTesting #InternalPentest #PeekABoo

"RT PeekABoo - Tool To Enable Remote Desktop On The Targeted Machine j.mp/2WFFeYR #InfrastructureTesting #InternalPentest #PeekABoo https://t.co/JqnrqhPT9o"

PeekABoo - Tool To Enable Remote Desktop On The Targeted Machine j.mp/2WFFeYR #InfrastructureTesting #InternalPentest #PeekABoo

So where to start? Well, pentesting comes in two forms: Internal and External pentests. This article will deal solely with internal testing. Keep reading: buff.ly/2W8U4eL #cybersecurity #internalpentest

PeekABoo - Tool To Enable Remote Desktop On The Targeted Machine j.mp/2WFFeYR #InfrastructureTesting #InternalPentest #PeekABoo #spectresecurity

PeekABoo - Tool To Enable Remote Desktop On The Targeted Machine j.mp/2WFFeYR #InfrastructureTesting #InternalPentest #PeekABoo

Difference Between Internal and External Penetration Testing Read Now: infosectrain.com/blog/differenc… #SecureYourPerimeter #InternalPenTest #ExternalPenTest #CyberSecTesting #cybersecurity #penetrationtesting #infosectrain #learntorise

PeekABoo - Tool To Enable Remote Desktop On The Targeted Machine j.mp/2WFFeYR #InfrastructureTesting #InternalPentest #PeekABoo

Getting ntlmv1/2 hash using .scf file onto the file share: 1337red.wordpress.com/using-a-scf-fi… #internalpentest #infosec #pentest
İç Network Penetrasyon (Sızma) Testi 📍rootcon.com.tr ☎️0216 561 76 96 #pentest #internalpentest #cybersecurity #zafiyet #bilgiguvenligi #agguvenligi #penetrationtest #güvenliktesti #veriguvenligi #network

The threat posed by hackers is persistent, and it is important to maintain a strong defense to protect your organization. Visit us today for all kind of cyber security services bit.ly/2FtRKUH #pentesting #VulnerabilityAssessments #InternalPenTest #ComplimentaryPenTest
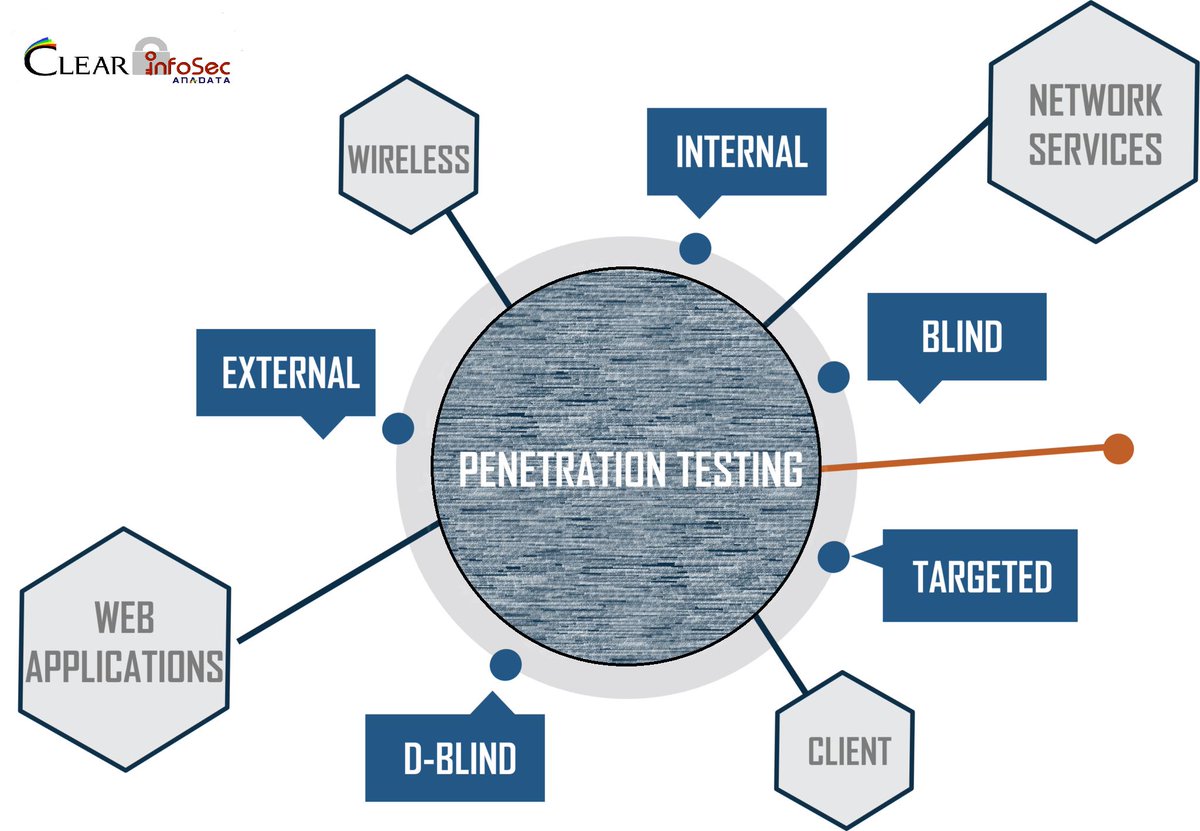
Both internal and external pen testing serve as valuable tools to assess network security. Several factors, including desired level of access, should be considered before implementing. READ ARTICLE: bit.ly/41zPG5s #InternalPenTest #ExternalPenTest #CyberSecurity
startup.info
Startup Info - Startups & Innovation Magazine
Startup Info is the leading entrepreneurs and innovation magazine devoted to shed light on the booming startup ecosystem worldwide.
Procdump dump lsass Defender: Threat detected! Sqldumper dump lsass Defender: Sure, go right ahead! btw dumping lsass with sqldumper.exe is not new, actually its quite old. lolbas-project.github.io/lolbas/OtherMS…


Do you know "PowerShell Direct"? ✅If you're local and Hyper-V admin, VM runs locally and you have valid credentials for it: you can execute PowerShell commands in the VM and copy files! No need for network access, nor having PowerShell Remoting enabled 😉 docs.microsoft.com/en-us/virtuali…


Difference Between Internal and External Penetration Testing Read Now: infosectrain.com/blog/differenc… #SecureYourPerimeter #InternalPenTest #ExternalPenTest #CyberSecTesting #cybersecurity #penetrationtesting #infosectrain #learntorise

Both internal and external pen testing serve as valuable tools to assess network security. Several factors, including desired level of access, should be considered before implementing. READ ARTICLE: bit.ly/41zPG5s #InternalPenTest #ExternalPenTest #CyberSecurity
startup.info
Startup Info - Startups & Innovation Magazine
Startup Info is the leading entrepreneurs and innovation magazine devoted to shed light on the booming startup ecosystem worldwide.
So where to start? Well, pentesting comes in two forms: Internal and External pentests. This article will deal solely with internal testing. Keep reading: buff.ly/2W8U4eL #cybersecurity #internalpentest

So where to start? Well, pentesting comes in two forms: Internal and External pentests. This article will deal solely with internal testing. Keep reading: buff.ly/3xjW0ip #cybersecurity #internalpentest

The threat posed by hackers is persistent, and it is important to maintain a strong defense to protect your organization. Visit us today for all kind of cyber security services bit.ly/2FtRKUH #pentesting #VulnerabilityAssessments #InternalPenTest #ComplimentaryPenTest

PeekABoo - Tool To Enable Remote Desktop On The Targeted Machine j.mp/2WFFeYR #InfrastructureTesting #InternalPentest #PeekABoo

PeekABoo - Tool To Enable Remote Desktop On The Targeted Machine j.mp/2WFFeYR #InfrastructureTesting #InternalPentest #PeekABoo #spectresecurity

PeekABoo - Tool To Enable Remote Desktop On The Targeted Machine j.mp/2WFFeYR #InfrastructureTesting #InternalPentest #PeekABoo

PeekABoo - Tool To Enable Remote Desktop On The Targeted Machine j.mp/2WFFeYR #InfrastructureTesting #InternalPentest #PeekABoo

"RT PeekABoo - Tool To Enable Remote Desktop On The Targeted Machine j.mp/2WFFeYR #InfrastructureTesting #InternalPentest #PeekABoo https://t.co/JqnrqhPT9o"

PeekABoo - Tool To Enable Remote Desktop On The Targeted Machine j.mp/2WFFeYR #InfrastructureTesting #InternalPentest #PeekABoo

"RT PeekABoo - Tool To Enable Remote Desktop On The Targeted Machine j.mp/2WFFeYR #InfrastructureTesting #InternalPentest #PeekABoo https://t.co/JqnrqhPT9o"

PeekABoo - Tool To Enable Remote Desktop On The Targeted Machine j.mp/2WFFeYR #InfrastructureTesting #InternalPentest #PeekABoo

PeekABoo - Tool To Enable Remote Desktop On The Targeted Machine j.mp/2WFFeYR #InfrastructureTesting #InternalPentest #PeekABoo #spectresecurity

PeekABoo - Tool To Enable Remote Desktop On The Targeted Machine j.mp/2WFFeYR #InfrastructureTesting #InternalPentest #PeekABoo

So where to start? Well, pentesting comes in two forms: Internal and External pentests. This article will deal solely with internal testing. Keep reading: buff.ly/2W8U4eL #cybersecurity #internalpentest

PeekABoo - Tool To Enable Remote Desktop On The Targeted Machine j.mp/2WFFeYR #InfrastructureTesting #InternalPentest #PeekABoo

Difference Between Internal and External Penetration Testing Read Now: infosectrain.com/blog/differenc… #SecureYourPerimeter #InternalPenTest #ExternalPenTest #CyberSecTesting #cybersecurity #penetrationtesting #infosectrain #learntorise

İç Network Penetrasyon (Sızma) Testi 📍rootcon.com.tr ☎️0216 561 76 96 #pentest #internalpentest #cybersecurity #zafiyet #bilgiguvenligi #agguvenligi #penetrationtest #güvenliktesti #veriguvenligi #network

The threat posed by hackers is persistent, and it is important to maintain a strong defense to protect your organization. Visit us today for all kind of cyber security services bit.ly/2FtRKUH #pentesting #VulnerabilityAssessments #InternalPenTest #ComplimentaryPenTest

Something went wrong.
Something went wrong.
United States Trends
- 1. Araujo 101K posts
- 2. Estevao 77.3K posts
- 3. Ferran 53K posts
- 4. Chelsea 408K posts
- 5. Barcelona 301K posts
- 6. Rashford 20.4K posts
- 7. Yamal 77.6K posts
- 8. Cucurella 35K posts
- 9. Kounde 24.6K posts
- 10. Godzilla 22.6K posts
- 11. #CHEBAR 9,702 posts
- 12. #AskTems 3,829 posts
- 13. Rush Hour 4 15.7K posts
- 14. Sonny Gray 8,480 posts
- 15. Flick 25.7K posts
- 16. Happy Thanksgiving 22.9K posts
- 17. Enzo 42.5K posts
- 18. Balde 8,312 posts
- 19. Raising Arizona 1,299 posts
- 20. Caicedo 20.2K posts
















