#ret2libc Suchergebnisse
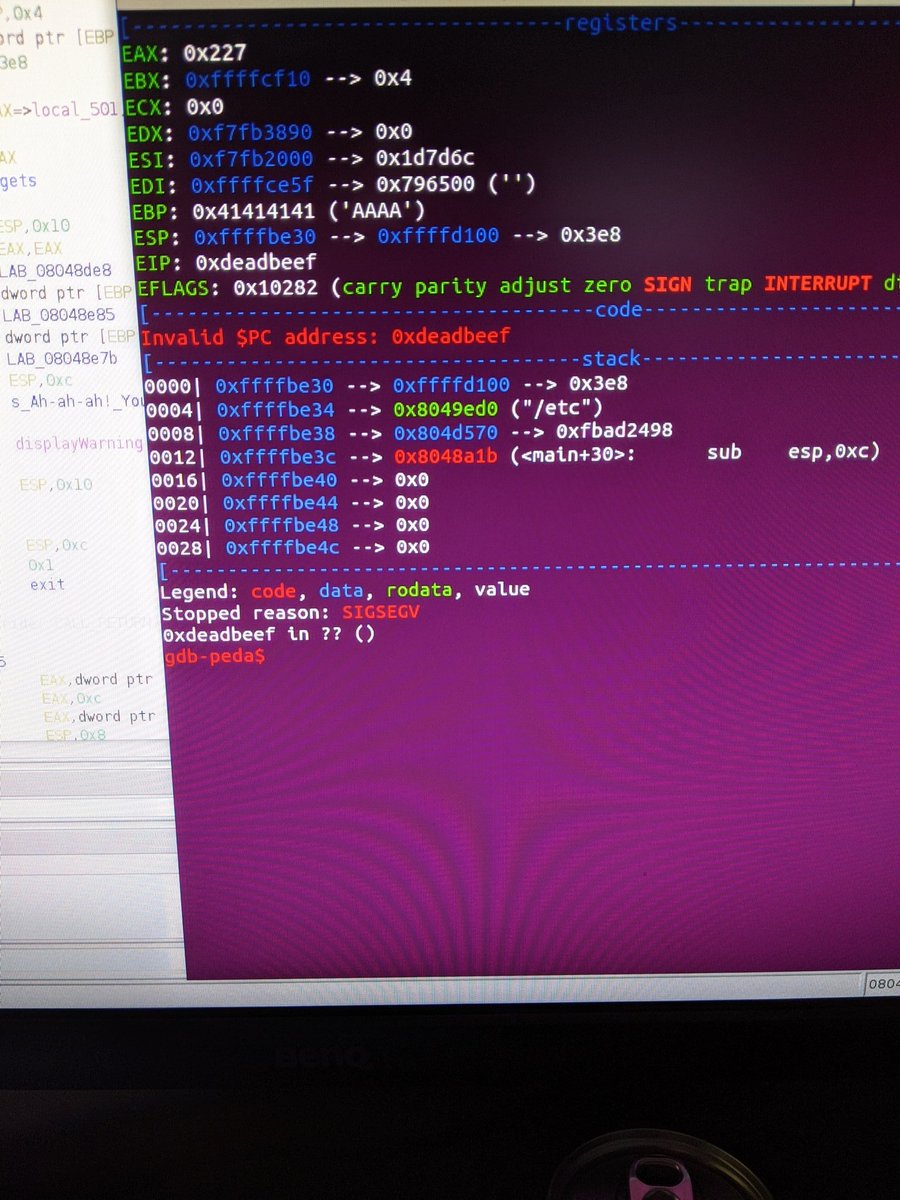
Holy sh** very nice tool ! Made the #Ret2libc manually on this box (pretty fun to craft btw) but this gadget finder just seems :
Learn exploit development in this guide on defeating a non-executable stack with #ret2libc. buff.ly/2Hl1Pln #hacking #security

#ret2libc #BoF Nouvel article sur le retour à la libc, avec schémas et exemples ! blog.hackndo.com/retour-a-la-li…

w4l73r just owned system on Frolic ! hackthebox.eu via @hackthebox_eu Very nice #ret2libc privesc, loved it !
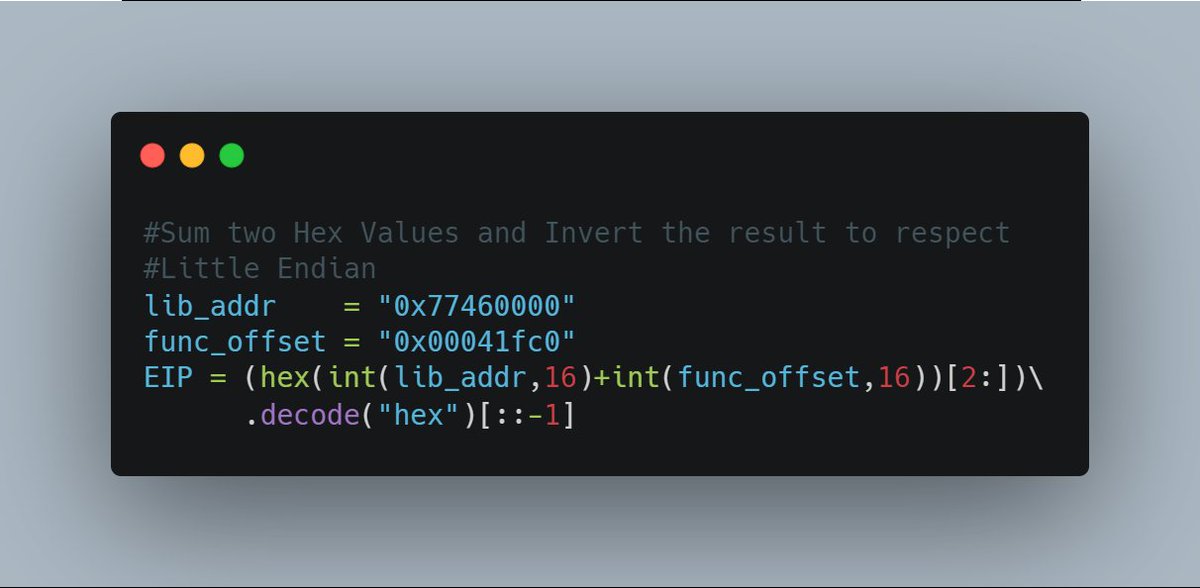
Learn exploit development in this guide on defeating a non-executable stack with #ret2libc. bit.ly/2IfRVCK #hacking #security

RT WonderHowTo "Learn exploit development in this guide on defeating a non-executable stack with #ret2libc. buff.ly/2Hl1Pln #hacking #security https://t.co/kyc6jgScaF"

Did you know the classic #ret2libc #exploitation technique frequently used on #x86 doesn't work on #ARM. But that doesn't stop you from using other techniques as we have #Ret2zp and #ROP. Learn about these and more from our book, ow.ly/dj0U30mOSz0 #IoT #ihackiot #Attify

All Skidz #LizardLands #sp00kypackets #ret2libc #realphantomraid
I am stuck at a reverse engineering task and I just don't get why my ret2libc attack wont work. When I use pwntools the exploit works, but if I write the payload to a file and pipe the contents of that file to the vulnerable program it doesnt work. Wth... #c #ret2libc
Today's @hackthebox_eu #Pwn challenge walkthrough is "PwnShop" 👀 See how #ROP gadgets can be used to pivot the stack and #ret2libc. Finally, we use some cool #PwnTools features to make life easy 🙂 #ctf #htb #hackthebox #bufferoverflow #infosec #tutorial youtube.com/watch?v=RNqJjO…
![_CryptoCat's tweet card. PwnShop [easy]: HackTheBox Pwn Challenge (ret2libc with stack pivot)](https://pbs.twimg.com/card_img/1993951016505491456/2I0a4zN5?format=jpg&name=orig)
youtube.com
YouTube
PwnShop [easy]: HackTheBox Pwn Challenge (ret2libc with stack pivot)
Ret2Libc Attack aidenpearce369.github.io/posts/ret2libc… Binary Exploitation #binaryexploitation #ret2libc #libc #linux #linuxsecurity #expdev #reversing #osed #eXDS
Tricks for successful exploitation of buffer overflow outside gdb lnkd.in/fStcFed #bof #ret2libc #gdb lnkd.in/fUTzhN5
🚨 New Writeup Alert! 🚨 "HTB: Cyber Apocalypse 2024 — Pet Companion" by Szigecsán Dávid is now live on IW! Check it out here: infosecwriteups.com/b9c289efc448 #pwn #pwntools #ret2libc #security #assembly
Video writeup for `teufel` pwnable from the #32c3ctf - #ROP #ret2libc youtube.com/watch?v=wDosab…
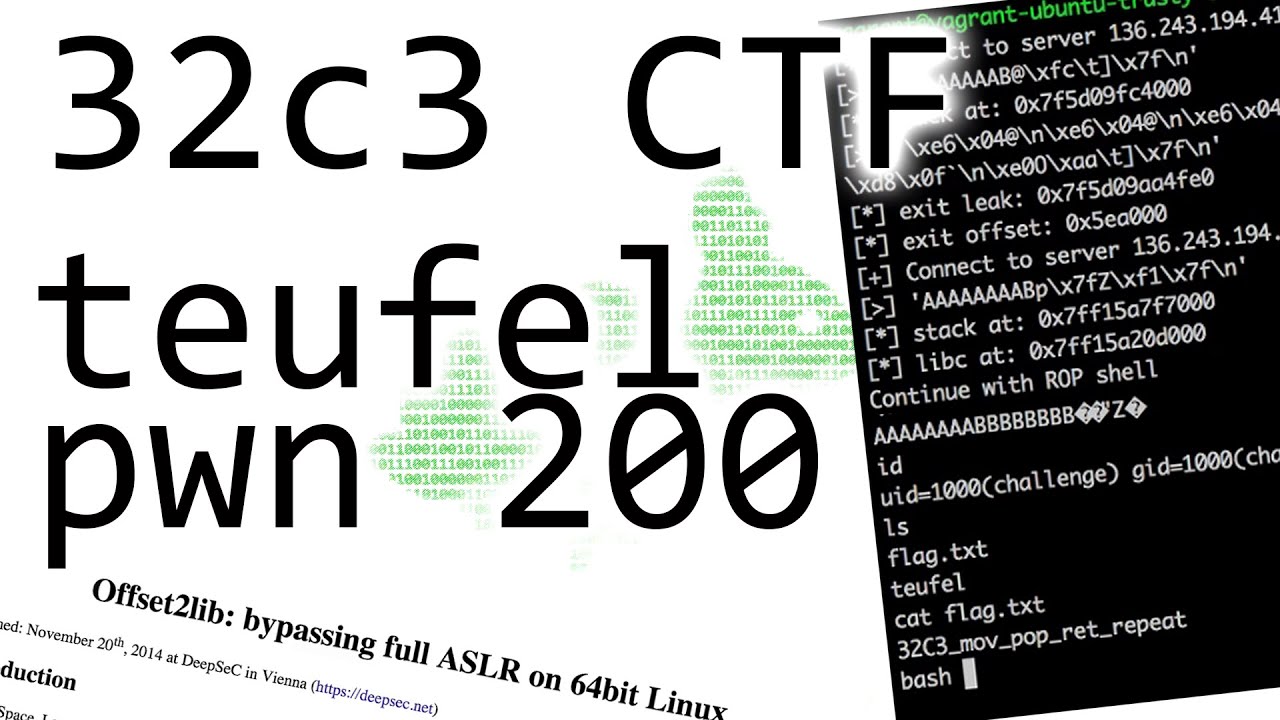
youtube.com
YouTube
ROP with a very small stack - 32C3CTF teufel (pwnable 200)
How to leak Libc addresses from GOT on a remote machine to exploit unknown libc and bypass ASLR on 64 bit. #binary_exploitation #ret2libc #hacking ret2rop.com/2020/04/got-ad…
🚨 New Writeup Alert! 🚨 "HTB: Cyber Apocalypse 2024 — Pet Companion" by Szigecsán Dávid is now live on IW! Check it out here: infosecwriteups.com/b9c289efc448 #pwn #pwntools #ret2libc #security #assembly
I am stuck at a reverse engineering task and I just don't get why my ret2libc attack wont work. When I use pwntools the exploit works, but if I write the payload to a file and pipe the contents of that file to the vulnerable program it doesnt work. Wth... #c #ret2libc
Ret2Libc Attack aidenpearce369.github.io/posts/ret2libc… Binary Exploitation #binaryexploitation #ret2libc #libc #linux #linuxsecurity #expdev #reversing #osed #eXDS
Today's @hackthebox_eu #Pwn walkthrough is "Ropme". Rated "hard" but actually easier than many of the "easy" challenges 😅 Classic #bufferoverflow; leak GOT address then #ret2libc 🙂 #ctf #htb #hackthebox #infosec #tutorial youtube.com/watch?v=AaKLMc…
Today's @hackthebox_eu #Pwn challenge walkthrough is "PwnShop" 👀 See how #ROP gadgets can be used to pivot the stack and #ret2libc. Finally, we use some cool #PwnTools features to make life easy 🙂 #ctf #htb #hackthebox #bufferoverflow #infosec #tutorial youtube.com/watch?v=RNqJjO…
![_CryptoCat's tweet card. PwnShop [easy]: HackTheBox Pwn Challenge (ret2libc with stack pivot)](https://pbs.twimg.com/card_img/1993951016505491456/2I0a4zN5?format=jpg&name=orig)
youtube.com
YouTube
PwnShop [easy]: HackTheBox Pwn Challenge (ret2libc with stack pivot)
Stepping it up with today's @hackthebox_eu #Pwn chall, "Shooting Star" 🌠 We'll use a #ROP chain to leak a GOT function address and #ret2libc. Finally, we look at #PwnTools automation and how to deal with different libc versions 🙂#ctf #htb #bof #infosec youtube.com/watch?v=Bvd9xn…
youtube.com
YouTube
Shooting Star [easy]: HackTheBox Pwn Challenge (ret2libc)
How to leak Libc addresses from GOT on a remote machine to exploit unknown libc and bypass ASLR on 64 bit. #binary_exploitation #ret2libc #hacking ret2rop.com/2020/04/got-ad…
Holy sh** very nice tool ! Made the #Ret2libc manually on this box (pretty fun to craft btw) but this gadget finder just seems :
w4l73r just owned system on Frolic ! hackthebox.eu via @hackthebox_eu Very nice #ret2libc privesc, loved it !

Interested in learning how to use Return-to-Zero-Protection (#ret2zp) as an alternative, which overcomes all the limitation of #ret2libc as applied to ARM #systems ? Read our #blog NOW >>>> ow.ly/FTdM30nhVFj #ARMexploitation #x86 #ARMarchitecture #ihackiot #Attify
Learn the details of Return to Zero Protection technique on #ARM processor with our blog here >>>> ow.ly/JuHi30n19Tx #ARMexploitation #ret2libc #ARMbinaries #ihackiot #Attify
Learn why Return-to-Libc ( #ret2libc ) technique fails on ARM processor with our blog here >>> ow.ly/TuqP30naoQu #ARM #x86exploitation #ret2zp #ihackiot #Attify
"RT RT attifyme: Interested in learning how to use Return-to-Zero-Protection (#ret2zp) as an alternative, which overcomes all the limitation of #ret2libc as applied to ARM #systems ? Read our #blog NOW >>>> ow.ly/FTdM30nhVFj #ARMexploitation #x86 #ARMarchitecture #ihack…
Holy sh** very nice tool ! Made the #Ret2libc manually on this box (pretty fun to craft btw) but this gadget finder just seems :
#ret2libc #BoF Nouvel article sur le retour à la libc, avec schémas et exemples ! blog.hackndo.com/retour-a-la-li…

w4l73r just owned system on Frolic ! hackthebox.eu via @hackthebox_eu Very nice #ret2libc privesc, loved it !

Learn exploit development in this guide on defeating a non-executable stack with #ret2libc. bit.ly/2IfRVCK #hacking #security

Learn exploit development in this guide on defeating a non-executable stack with #ret2libc. buff.ly/2Hl1Pln #hacking #security

Did you know the classic #ret2libc #exploitation technique frequently used on #x86 doesn't work on #ARM. But that doesn't stop you from using other techniques as we have #Ret2zp and #ROP. Learn about these and more from our book, ow.ly/dj0U30mOSz0 #IoT #ihackiot #Attify

RT WonderHowTo "Learn exploit development in this guide on defeating a non-executable stack with #ret2libc. buff.ly/2Hl1Pln #hacking #security https://t.co/kyc6jgScaF"

Something went wrong.
Something went wrong.
United States Trends
- 1. Ravens 57.4K posts
- 2. Lamar 46K posts
- 3. Bengals 51.3K posts
- 4. #heatedrivalry 11.2K posts
- 5. ilya 14.5K posts
- 6. shane 17K posts
- 7. Joe Burrow 20.5K posts
- 8. Zay Flowers 4,102 posts
- 9. Cowboys 92.7K posts
- 10. Chiefs 108K posts
- 11. Hudson 11.4K posts
- 12. #WhoDey 3,669 posts
- 13. Derrick Henry 4,424 posts
- 14. Perine 1,581 posts
- 15. #hrspoilers 1,477 posts
- 16. connor storrie 1,781 posts
- 17. Harbaugh 3,114 posts
- 18. Sarah Beckstrom 212K posts
- 19. Zac Taylor 2,610 posts
- 20. AFC North 2,316 posts