#secureprotocols search results
Unlock the strength of secure protocols with #TeleGuard! We ensure your messages are encrypted and only decipherable by the rightful recipient. Say goodbye to unwelcome access and hello to secure communication. Download now! #SecureProtocols #EndToEndEncryption

#TeleGuard is setting a new standard in data privacy. With continuous monitoring and updating of secure protocols, we address emerging vulnerabilities to keep your data safe. Download TeleGuard today and experience a new standard in data privacy. #DataPrivacy #SecureProtocols

Emerging protocols aim to reduce the trusted setup footprint or eliminate it entirely, boosting security and trustworthiness. #Trustless #SecureProtocols
7 featured participants in 7 days. Day 7. This is our last partner drop but we’re not done yet. Something fun is on the way. @eulerfinance 🧵
Using secure access protocols ensures that data transmitted over the network is encrypted, protecting it from interception or tampering. #SecureProtocols #DataSecurity #AccessControl

6/7 🔗 Technological Approach - Shido: Shido integrates advanced encryption techniques and secure protocols to maintain the integrity and confidentiality of data. It focuses on providing a robust security framework for blockchain applications. #Encryption #SecureProtocols
Day 7🚀 Secure your connections! When accessing any site, use Hypertext Transfer Protocol Secure (HTTPS) & Virtual Private Networks (VPNs) for encrypted protection. Keep your data safe & prevent cyber attacks. #Cybersecurity #SecureProtocols
Day 6🚀 Use a password manager! Generate & store complex passwords securely. Avoid using your name, birthday or common words as your password. Ensure it comprises uppercase & lowercase letters, numbers and special characters (X@vi3rP@ss!) #CyberSecurityAwareness
🟧Call for Papers🟧 Deadline: Jun. 14, 2024❄️ “Special Section on the Architectures, Protocols, and Applications for the Future Internet”🍷 IEICE Transactions on Information and Systems, Jun. 2025🍵 ieice.org/eng/s_issue/cf… #CallforPapers #Sensornetworking #secureprotocols

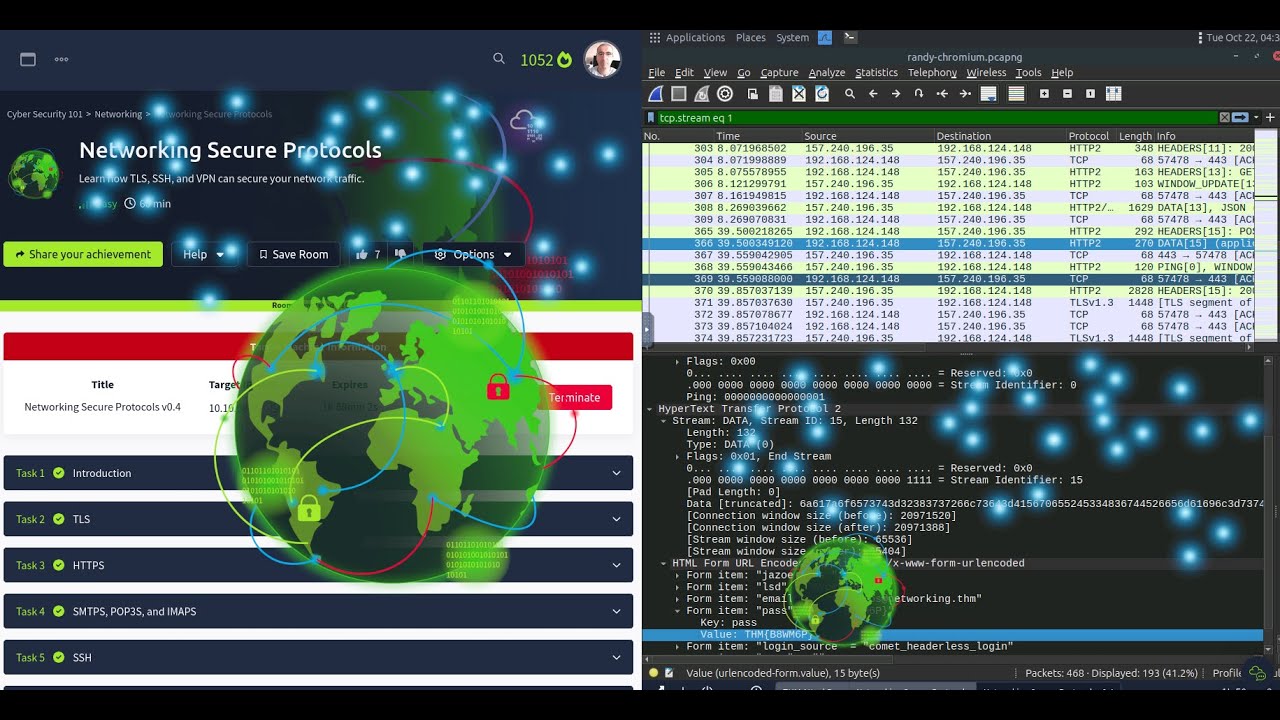
YouTube video walk through for TryHackMe room Networking Secure Protocols Learn how TLS, SSH, and VPN can secure your network traffic. Part of the new path: Cyber Security 101 youtube.com/watch?v=HJnoFo… #THMCyberSecurity101 #CyberSecurity101 #SecureProtocols #TLS #SSH #VPN…
youtube.com
YouTube
Networking Secure Protocols: TLS, SSH, and VPN in Cyber Security 101...
Giverep’s blockchain uses secure protocols—no vulnerabilities. #SecureProtocols @Giverep
Need to share confidential documents with clients? Want to receive files from your remote team? Thru’s secure file transfer ensures that your files remain protected every step of the way. Visit buff.ly/47fVHaO to learn more. #datasecurity #secureprotocols #filetransfer

6/10: ⚙️ Trusted Setup: Zcash, like its predecessors, requires a trusted setup phase for generating zk-SNARKs. Careful execution and secure destruction of parameters are crucial to prevent potential vulnerabilities. #SecureProtocols
I'm looking for a #NetworkSystemsEngineer who knows #secureprotocols and #networkprotocols goo.gl/mhAnJG #jobs
🔒 TLC's ascendancy on Coindcx! Protect your digital assets with Trillioner Wallet's secure protocols! 💳🛡️ #TLC #SecureProtocols
Our focus is on enhancing asset transfer integrity and mitigating vulnerabilities to ensure a secure and efficient distributed ecosystem. #BlockchainInteroperability #SecureProtocols #SmartContracts
Interested in data security, particularly in cloud databases? Check out this article, “SecBerg: Secure and Practical Iceberg Queries in Cloud” by S. Zhang, S. Ray, @RongxingLu, Y. Guan, Y. Zheng, & J. Shao ieeexplore.ieee.org/abstract/docum… #IcebergQuery #CloudServices #SecureProtocols
⚔️ Dive into the realm of secure protocols like a knight of the digital round table! Essential for CompTIA Security+ (SY0-601) exam success! 🛡️ #CyberSecurity #CompTIA #SecureProtocols blog.alphaprep.net/the-art-of-arm…
Wrapped up: Networking Secure Protocols! This is built on all the previous rooms and now includes encryption, tunneling, and secure communications. #CyberSecurity #Networking #SecureProtocols tryhackme.com/room/networkin… #tryhackme via @realtryhackme
Apple loses bid to undo $440 million judgment in VirnetX patent case #VPN #SecureProtocols reut.rs/2svWLox
Let's ensure we create a document that sets a new standard for clarity, practicality, and impact within the cross-chain space. #CrossChainCollaboration #Web3Whitepaper #SecureProtocols
Emerging protocols aim to reduce the trusted setup footprint or eliminate it entirely, boosting security and trustworthiness. #Trustless #SecureProtocols
7 featured participants in 7 days. Day 7. This is our last partner drop but we’re not done yet. Something fun is on the way. @eulerfinance 🧵
Day 7🚀 Secure your connections! When accessing any site, use Hypertext Transfer Protocol Secure (HTTPS) & Virtual Private Networks (VPNs) for encrypted protection. Keep your data safe & prevent cyber attacks. #Cybersecurity #SecureProtocols
Day 6🚀 Use a password manager! Generate & store complex passwords securely. Avoid using your name, birthday or common words as your password. Ensure it comprises uppercase & lowercase letters, numbers and special characters (X@vi3rP@ss!) #CyberSecurityAwareness
Giverep’s blockchain uses secure protocols—no vulnerabilities. #SecureProtocols @Giverep
Wrapped up: Networking Secure Protocols! This is built on all the previous rooms and now includes encryption, tunneling, and secure communications. #CyberSecurity #Networking #SecureProtocols tryhackme.com/room/networkin… #tryhackme via @realtryhackme
Using secure access protocols ensures that data transmitted over the network is encrypted, protecting it from interception or tampering. #SecureProtocols #DataSecurity #AccessControl

Let's ensure we create a document that sets a new standard for clarity, practicality, and impact within the cross-chain space. #CrossChainCollaboration #Web3Whitepaper #SecureProtocols
YouTube video walk through for TryHackMe room Networking Secure Protocols Learn how TLS, SSH, and VPN can secure your network traffic. Part of the new path: Cyber Security 101 youtube.com/watch?v=HJnoFo… #THMCyberSecurity101 #CyberSecurity101 #SecureProtocols #TLS #SSH #VPN…

youtube.com
YouTube
Networking Secure Protocols: TLS, SSH, and VPN in Cyber Security 101...
6/7 🔗 Technological Approach - Shido: Shido integrates advanced encryption techniques and secure protocols to maintain the integrity and confidentiality of data. It focuses on providing a robust security framework for blockchain applications. #Encryption #SecureProtocols
🟧Call for Papers🟧 Deadline: Jun. 14, 2024❄️ “Special Section on the Architectures, Protocols, and Applications for the Future Internet”🍷 IEICE Transactions on Information and Systems, Jun. 2025🍵 ieice.org/eng/s_issue/cf… #CallforPapers #Sensornetworking #secureprotocols

⚔️ Dive into the realm of secure protocols like a knight of the digital round table! Essential for CompTIA Security+ (SY0-601) exam success! 🛡️ #CyberSecurity #CompTIA #SecureProtocols blog.alphaprep.net/the-art-of-arm…
🔒 TLC's ascendancy on Coindcx! Protect your digital assets with Trillioner Wallet's secure protocols! 💳🛡️ #TLC #SecureProtocols
#TeleGuard is setting a new standard in data privacy. With continuous monitoring and updating of secure protocols, we address emerging vulnerabilities to keep your data safe. Download TeleGuard today and experience a new standard in data privacy. #DataPrivacy #SecureProtocols

Unlock the strength of secure protocols with #TeleGuard! We ensure your messages are encrypted and only decipherable by the rightful recipient. Say goodbye to unwelcome access and hello to secure communication. Download now! #SecureProtocols #EndToEndEncryption

Need to share confidential documents with clients? Want to receive files from your remote team? Thru’s secure file transfer ensures that your files remain protected every step of the way. Visit buff.ly/47fVHaO to learn more. #datasecurity #secureprotocols #filetransfer

6/10: ⚙️ Trusted Setup: Zcash, like its predecessors, requires a trusted setup phase for generating zk-SNARKs. Careful execution and secure destruction of parameters are crucial to prevent potential vulnerabilities. #SecureProtocols
#TeleGuard is setting a new standard in data privacy. With continuous monitoring and updating of secure protocols, we address emerging vulnerabilities to keep your data safe. Download TeleGuard today and experience a new standard in data privacy. #DataPrivacy #SecureProtocols

Unlock the strength of secure protocols with #TeleGuard! We ensure your messages are encrypted and only decipherable by the rightful recipient. Say goodbye to unwelcome access and hello to secure communication. Download now! #SecureProtocols #EndToEndEncryption

Using secure access protocols ensures that data transmitted over the network is encrypted, protecting it from interception or tampering. #SecureProtocols #DataSecurity #AccessControl

Need to share confidential documents with clients? Want to receive files from your remote team? Thru’s secure file transfer ensures that your files remain protected every step of the way. Visit buff.ly/47fVHaO to learn more. #datasecurity #secureprotocols #filetransfer

🟧Call for Papers🟧 Deadline: Jun. 14, 2024❄️ “Special Section on the Architectures, Protocols, and Applications for the Future Internet”🍷 IEICE Transactions on Information and Systems, Jun. 2025🍵 ieice.org/eng/s_issue/cf… #CallforPapers #Sensornetworking #secureprotocols

Something went wrong.
Something went wrong.
United States Trends
- 1. Lakers 68K posts
- 2. Luka 51K posts
- 3. Marcus Smart 6,651 posts
- 4. Rockets 56.2K posts
- 5. #DWTS 44.8K posts
- 6. Shai 31.2K posts
- 7. Sengun 23K posts
- 8. Double OT 5,696 posts
- 9. Ayton 9,487 posts
- 10. Reed Sheppard 5,831 posts
- 11. Warriors 78.4K posts
- 12. Draymond 6,223 posts
- 13. Kevin Durant 23.3K posts
- 14. Chris Webber 1,682 posts
- 15. Chet 17.4K posts
- 16. Kuminga 6,584 posts
- 17. Caruso 5,144 posts
- 18. #LakeShow 5,613 posts
- 19. Elaine 21K posts
- 20. Curry 29.9K posts