#securitysoftwareengineering search results
Don't trade off agility or safety in cloud applications! Deliver confidently with DevSecOps—integrate security at every phase. Register now>>> reliance.systems/building-apps-… #DevSecOps #CloudSecurity #AgileDevelopment #SecureDeployment
#AIAgent #Security #Safety - A deep dive into AI agent safety and security frameworks, classification and mitigation medium.com/@sambeera/ai-a…
🚨 AI has redefined software risk — shaping how both attackers & defenders operate. Join @ap0x & @dalev for a breakdown of these shifting dynamics: bit.ly/4oqSV9T #AISecurity #SoftwareSupplyChainSecurity #AppSec
What if your devs could spot insecure code before it goes live? Or your cloud teams could lock down PHI before it leaks? That’s not wishful thinking. It’s role-based training. Get your teams breach-ready, not just audit-ready. Watch the full webinar to see how it’s done. 👉…

Technology that evolves compliance, not just supports it. Learn how aCSF transforms security from a checkbox to a strategic advantage: hubs.ly/Q03V-hRn0 #Cybersecurity #Compliance #CMMC #NISTCSF #ManagedIT #SystemsEngineering

Looking for a practical, evaluable framework for building and verifying software security from the ground up? We've got you covered. bit.ly/4pNNz9W

Website Authentication Made Simple with SafeLine ift.tt/iI6wjyC #systemweakness #cybersecurity #ethicalhacking
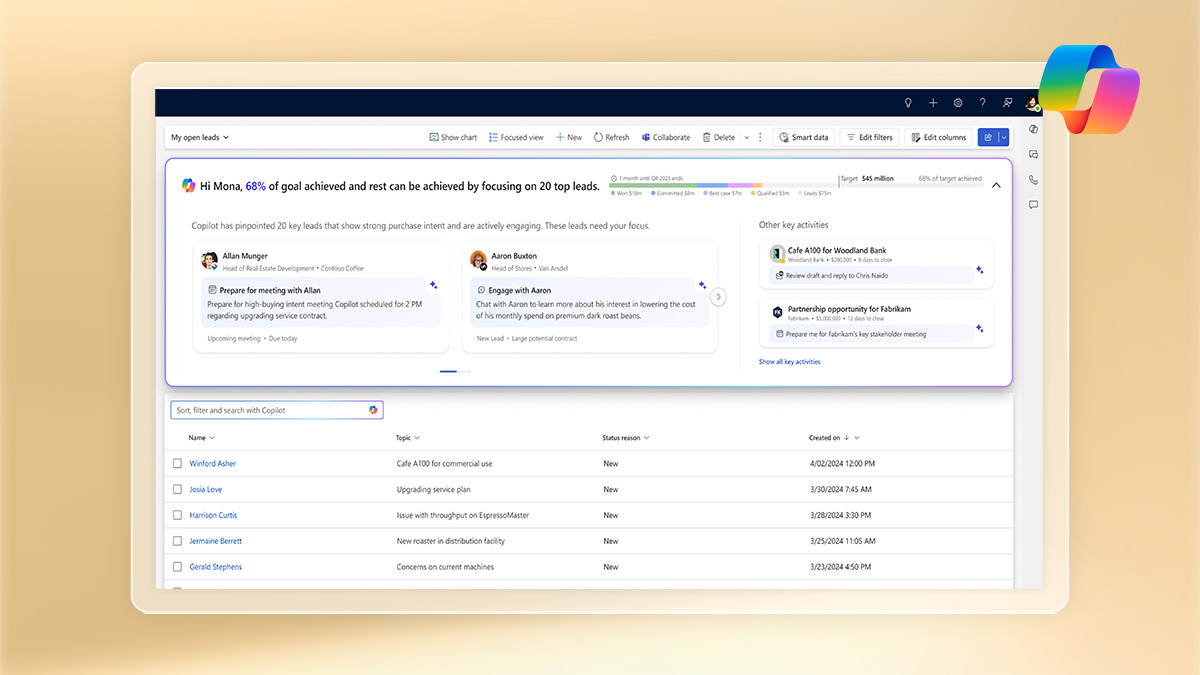
9/17: The security architecture: Data loss prevention protocols. Robust authentication systems. Maker-defined instructions establishing guardrails. Comprehensive governance features for IT administrators. Source: microsoft.com/en-us/dynamics… Organizations maintain control while…
If you are building or deploying #AI powered applications, this perspective is essential reading. 🔗 na2.hubs.ly/H02lf2S0 #agenticsecurity

Services as Software: - SOC Services as Software - Virtual CISO Services as Software Check link to my article in first comment. Bookmark and come back later if not available or browse it here: linkedin.com/in/francescofa…. All-in-one from the #TrustEverybodyButCutTheCards archives…
🤖 Scaling secure software in the age of AI takes more than tools. It takes turning AI-driven intelligence into real action. Join Dustin Lehr as he explores how AI, training, and dev engagement can be leveraged together. 🔗 ow.ly/8WEz50XAF9e #ai #aisecurity #aicode

2/ Our Framework covers essential security areas: - Proper key management for ENS ownership - Secure resolver configuration best practices - Subdomain delegation security protocols - Record update and maintenance procedures - Integration security patterns for developers 💡 Pro…
Even with Application Security Posture Management platforms, many teams fall into the same cycle: detect, fix, repeat. Visibility is only half the battle 🥊 You also need to address people-driven factors behind insecure code. Learn how to close the gap 👇blog.secureflag.com/2025/12/02/hum…
Security as an Engineering Discipline, Not a Marketing Claim 🛡️🖥️ Security at scale isn’t achieved by adding noise to your validator set or producing dense whitepapers. It’s achieved by designing systems with consistent behaviour under stress. Devve’s security model is built…
🎥 New Video Drop: Behind the Scenes of OWASP FIASSE — The Securable Framework Youtube Link - youtu.be/82ZvPtFqT84?si… #OWASP #FIASSE #SecurableSoftware #AppSec #SecureByDesign #SoftwareEngineering #AIAppSec #AIInSoftware #ShiftLeft #DevSecOps #OWASPProjects @owasp

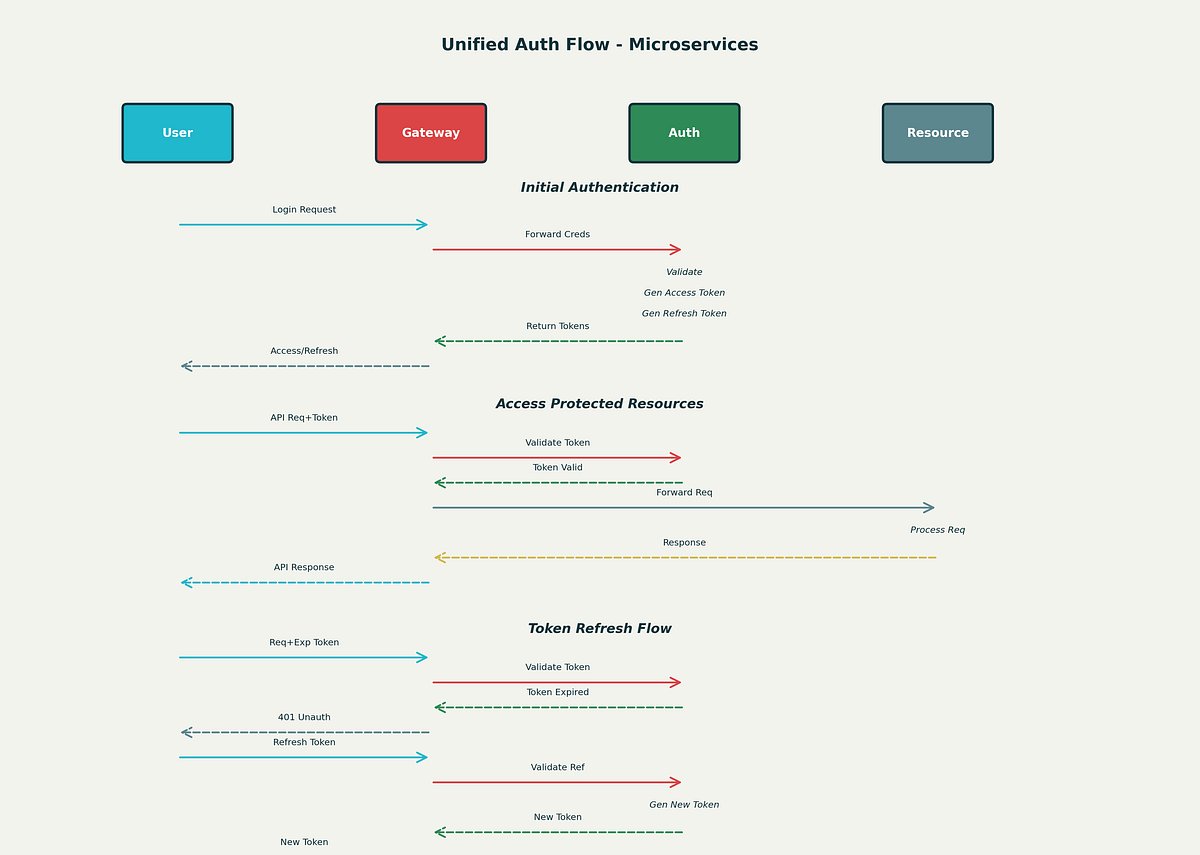
Unified Security Authentication Design for Microservices: A Deep Dive into Modern Architecture… ift.tt/1mYMloA #coding #programming #development #softwaredevelopment #engineering
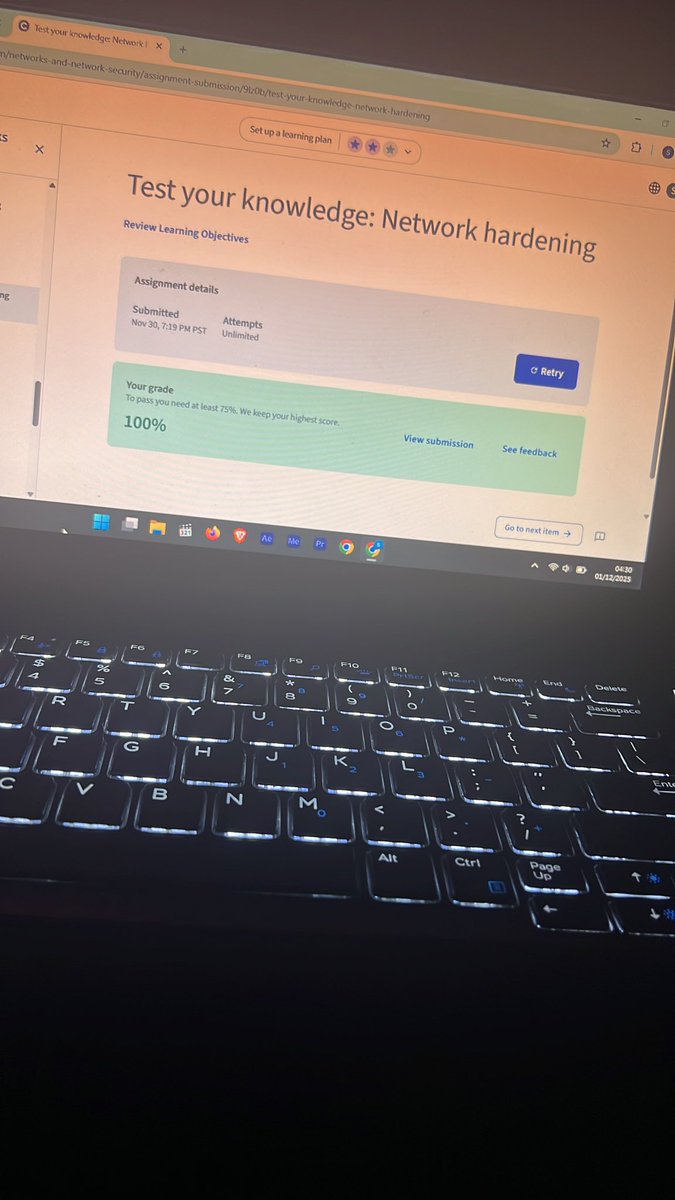
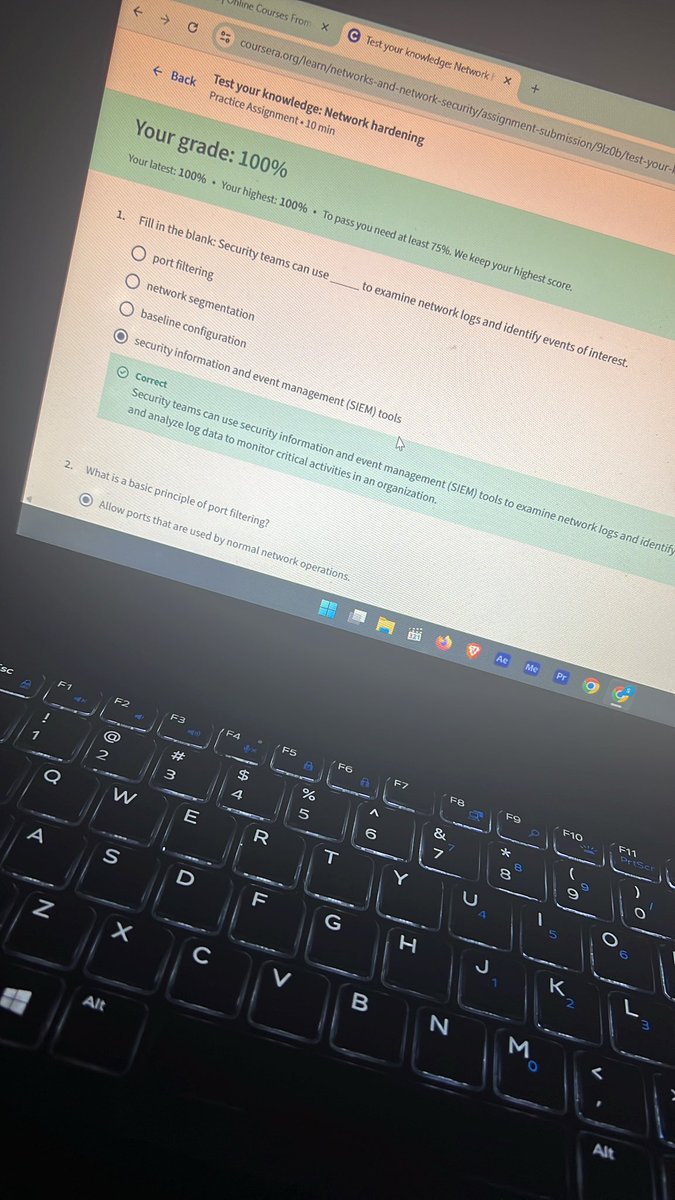
Day 9: Revisiting my previous Coursera course. Today, I strengthened my knowledge on how OS & network hardening work together — from applying security configurations to using firewalls, IDS/IPS, and SIEM tools to monitor threats. #CyberSecurity #networking @OnijeC @segoslavia
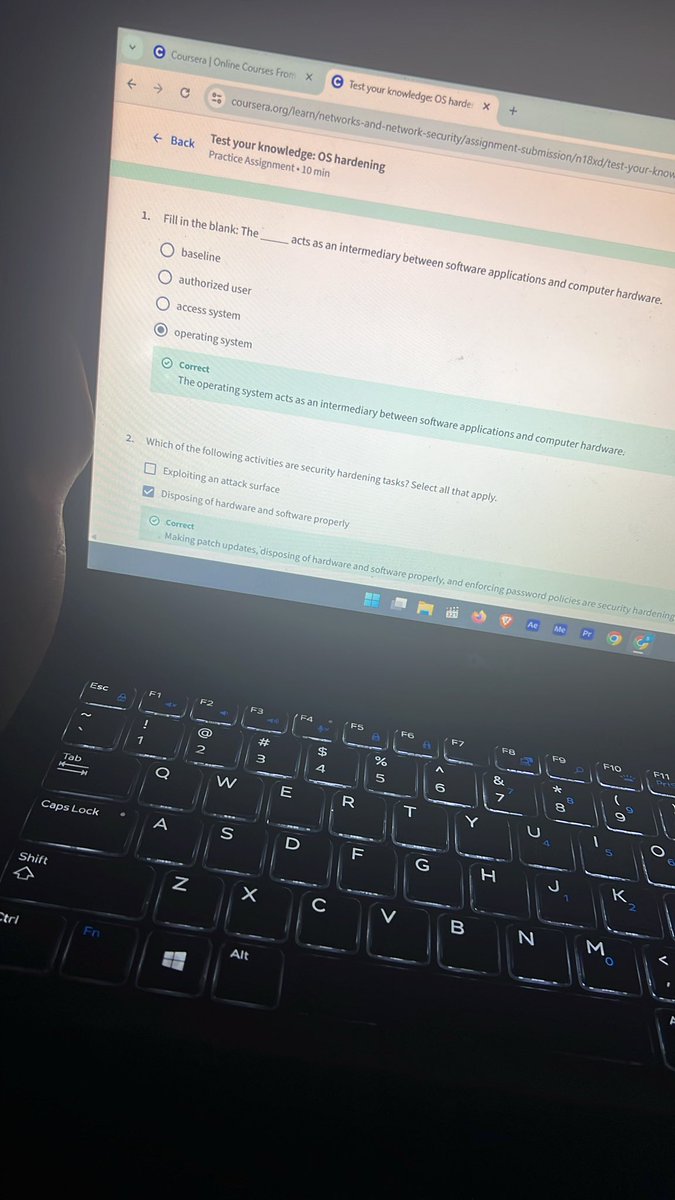
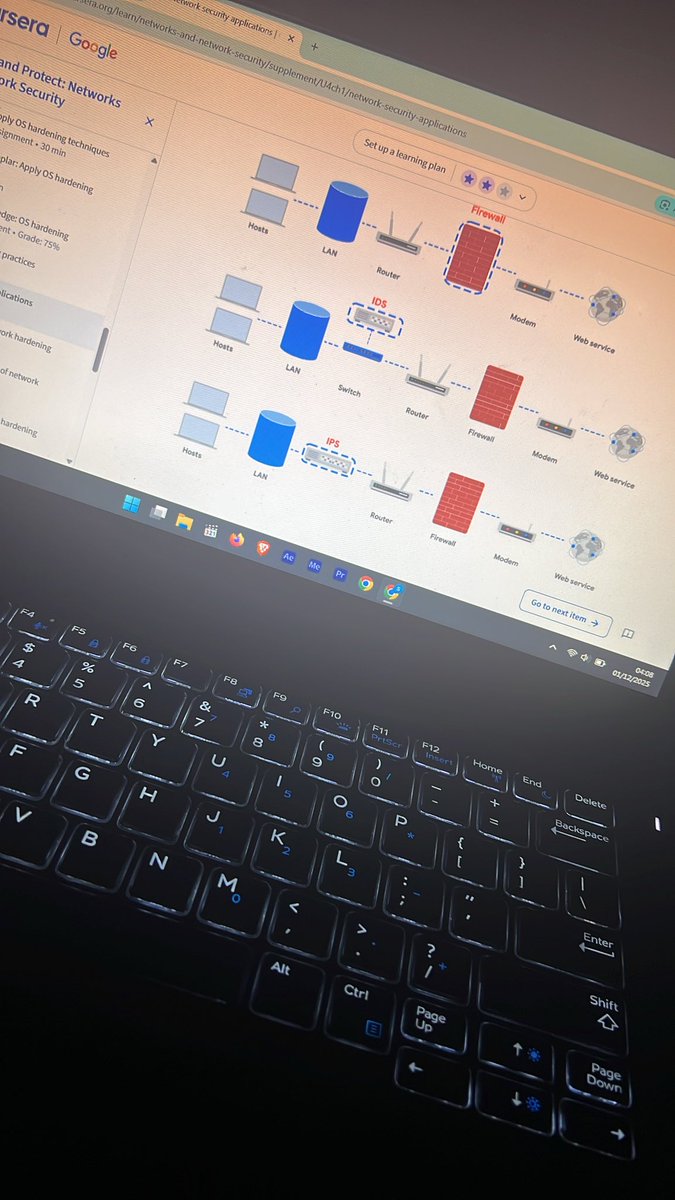
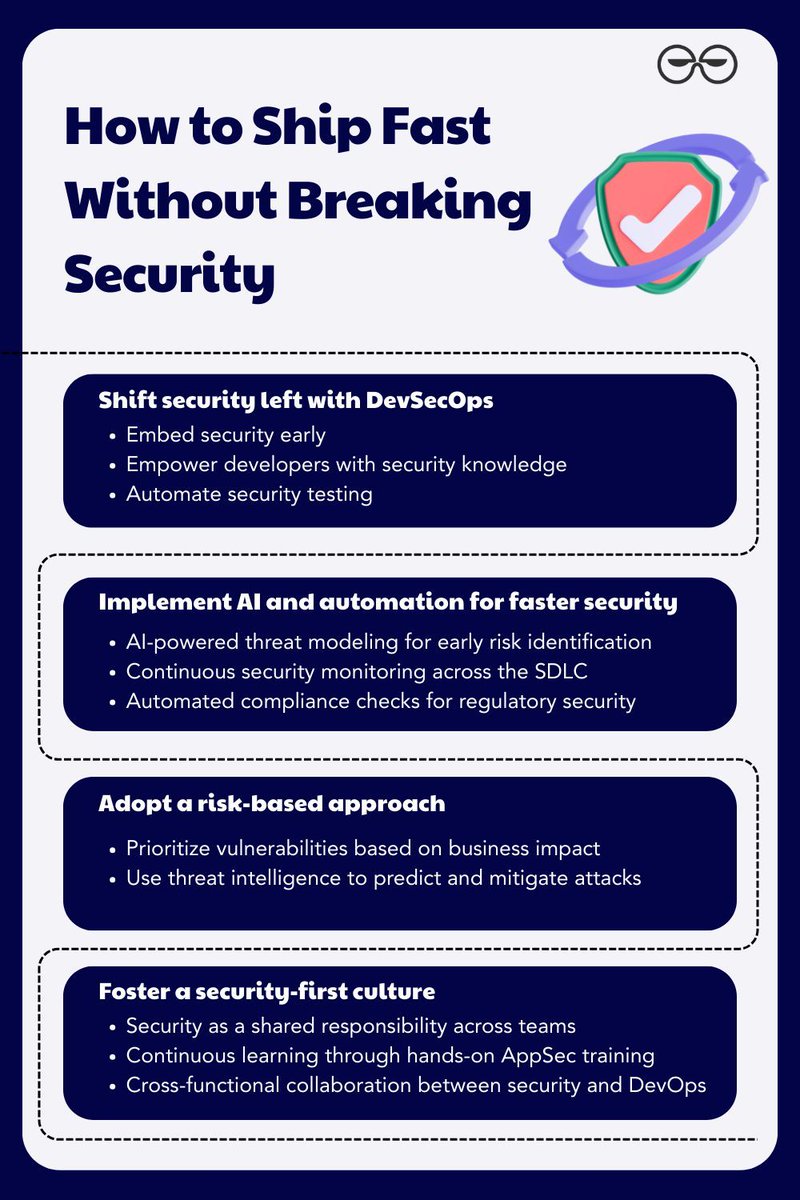
There’s no excuse to not prioritize security from Day 1 of the SDLC. If you’re serious about moving fast and staying secure, you need a process where security isn’t an afterthought, it’s built into every commit, every pipeline, every sprint. So how do you build that in without…
IoT makes life smarter — but also riskier. Weak passwords, outdated firmware, insecure networks & API flaws can expose your entire system. Stay protected with the right practices. 👉 Read more: snsin.com/9-common-iot-s… #IoTSecurity #CyberSecurity #SNS #TechSafety #StaySecure

Something went wrong.
Something went wrong.
United States Trends
- 1. Good Thursday 30.9K posts
- 2. #thursdayvibes 1,966 posts
- 3. Merry Christmas 68.9K posts
- 4. Happy Friday Eve N/A
- 5. #JASPER_TouchMV 252K posts
- 6. #NationalCookieDay N/A
- 7. JASPER COMEBACK TOUCH 165K posts
- 8. #ThursdayThoughts 1,472 posts
- 9. Hilux 8,875 posts
- 10. #thursdaymotivation 2,384 posts
- 11. DataHaven 11.7K posts
- 12. Toyota 29.2K posts
- 13. Earl Campbell 2,482 posts
- 14. Omar 189K posts
- 15. Colbert 4,561 posts
- 16. The Grinch 10.9K posts
- 17. Prince Harry 9,510 posts
- 18. Halle Berry 4,344 posts
- 19. Happy Birthday Dan 1,782 posts
- 20. USPS 7,714 posts