Mahesh Bheema
@0xmahesh
Security Enthusiast | OSCP | OSWP | Null Hyderabad Chapter Lead
คุณอาจชื่นชอบ
The $5 Membership sale is now live! The sale lasts until July 17 23:59 UTC: account.shodan.io/billing/member
May meet registrations are open. Register before it's too late here nullhydmay2023.eventbrite.com. Date: May 27th Venue:@Servicenow #NullHyd @null0x00 @vhssunny1 @pavanw3b @badc0d3r @0xmahesh
April meet registrations are open. Register before it's too late. Date: April 22 Venue: @EPAMSystems nullhydapr2023.eventbrite.com #NullHyd @null0x00 @vhssunny1 @0xmahesh @badc0d3r @pavanw3b
🛠️ These are my go-to #DevSecOps tools at all stages of the DevSecOps lifecycle. These are all OSS (not paid tools) so you wont spend a $ buying them
In this video walkthrough, we break down the basic info of CVE-2023-23397 the zero-day, zero-touch vulnerability that was rated 9.8 on the #CVSS scale. Follow this thread as we detail the general exploitation routine of this #vulnerability. research.trendmicro.com/cve202323397
We've just published a quick write up on CVE-2023-23397, which allows a remote adversary to leak NetNTLMv2 hashes: mdsec.co.uk/2023/03/exploi… by @domchell

#NullHyd's March registrations are open. Reserve a seat before it's too late. nullhydmar2023.eventbrite.com @0xmahesh @vhssunny1 @pavanw3b
Automatically configure a vulnerable Active Directory network on AWS : - 6 VMs - 1 linux server with GLPI - 3 domains Perfect to share a vulnerable lab with other people #activedirectory #aws #pentest #ad #LordOfTheRings github.com/0xBallpoint/LO…
Mindmap upgrade version 2023_02 thx to @Jenaye_fr and @DaahtK for the help. Full quality here : orange-cyberdefense.github.io/ocd-mindmaps/i…

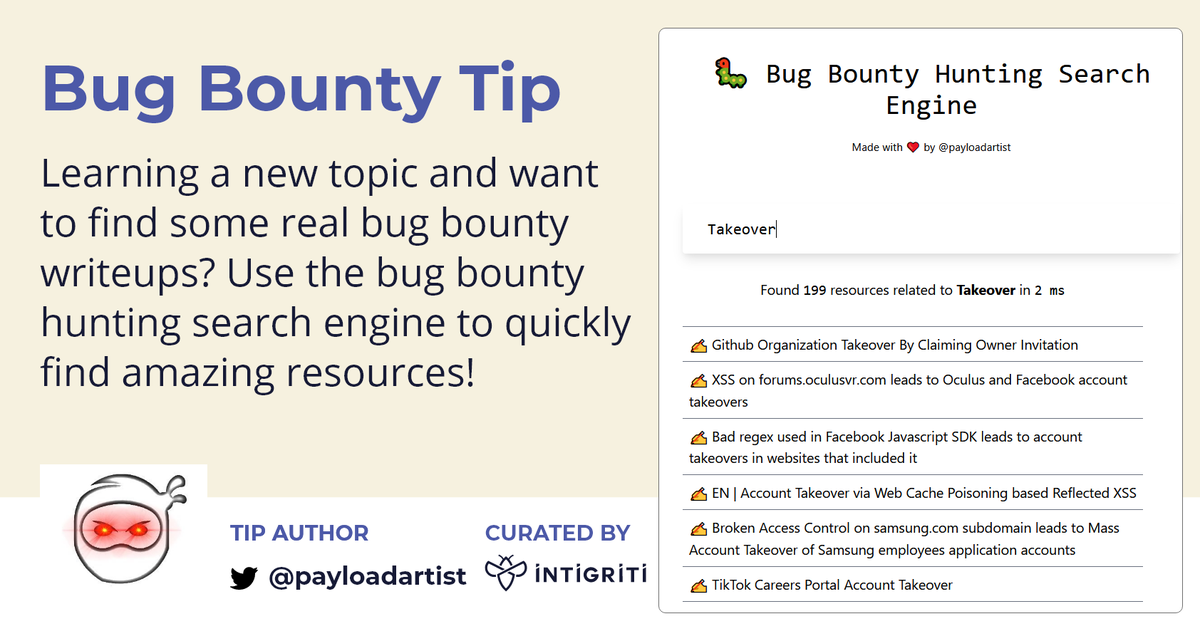
Learning from others is amazing, but how do you find the content you're looking for? @payloadartist solved that problem by creating the Bug Bounty Hunting Search Engine! hubs.li/Q01B0C100 #bugbounty #bugbountytips 👇
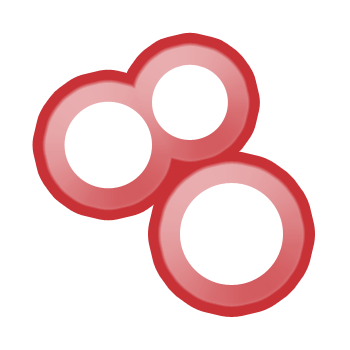
Accidental $70,000 Google Pixel Lock Screen Bypass >bugs.xdavidhu.me/google/2022/11… Video PoC: youtu.be/dSgSnYPgzT0 #TheSecureEdge #Hacking #Google #bugbounty #cybersecurity
After an unhealthy amount of hours put into this, I finally managed to get RCE on Cobalt Strike. I would recommend avoiding it for a while as CVE-2022-39197 is not sufficient.
The individual who breached Rockstar Games states they got initial access by social engineering an employee. They are currently on 4chan sharing material and chatting. boards.4channel.org/v/thread/61249…
We take the weekend off and Grand Theft Auto 6 material is leaked online from an alleged breach of Rockstar Games. Fun. The people on GTA forums, similar to Uber, believed it to be a hoax and mocked the leaker. gtaforums.com/topic/985481-g…
[BLOG] Fun post on how to combine evilginx by @mrgretzky and BITB by @mrd0x. rastamouse.me/evilginx-meet-…
I have compiled a list of Best Cybersecurity Youtube Channels, that talk about various topics related to cybersecurity. Do check it out 👇 Here is the link to the Github repository: github.com/Nickyie/Cybers… #Pentesting #CyberSec #cyberawarness #bugbounty #infosec #bugbounty
Some pics from @nullhyd July meet. Talks: News Bytes by Karan Cloud Security & S3 by @Aravind_JMA Cloud Security Zero to One by Ravi Teja Intro to Threat Hunting by @dmred1 Venue sponsor: @ServiceNow #nullHyd #InfoSec @null0x00




Bug Bounty Hint If you have found that server is running PHP - you can try to test it for RCE vulnerability. Append following header to request: User-Agentt: zerodiumsystem("id") If PHP version is vulnerable - you will execute system("id") command on a server.
United States เทรนด์
- 1. Aaron Gordon 26.1K posts
- 2. Steph 62.6K posts
- 3. Jokic 23.1K posts
- 4. #criticalrolespoilers 12.9K posts
- 5. Halle 20.3K posts
- 6. Wentz 25.3K posts
- 7. Warriors 89K posts
- 8. Vikings 52.9K posts
- 9. #EAT_IT_UP_SPAGHETTI 234K posts
- 10. #DubNation 4,516 posts
- 11. Hobi 41.6K posts
- 12. #LOVERGIRL 17.9K posts
- 13. Cam Johnson 1,652 posts
- 14. Nuggets 26.4K posts
- 15. Chargers 58.1K posts
- 16. Megan 37.9K posts
- 17. Wardell 2,746 posts
- 18. Pacers 22.5K posts
- 19. Shai 25.9K posts
- 20. Will Richard 5,144 posts
คุณอาจชื่นชอบ
-
 Abhijeth D
Abhijeth D
@abhijeth -
 Riyaz Walikar
Riyaz Walikar
@riyazwalikar -
 Aseem Jakhar
Aseem Jakhar
@aseemjakhar -
 Akash Mahajan
Akash Mahajan
@makash -
 badc0d3r
badc0d3r
@badc0d3r -
 Mohammed A. Imran
Mohammed A. Imran
@secfigo -
 Srinivas Kotipalli
Srinivas Kotipalli
@srini0x00 -
 Himanshu Kumar Das
Himanshu Kumar Das
@mehimansu -
 Krishna Chaitanya T
Krishna Chaitanya T
@novogeek -
 Neelu Tripathy
Neelu Tripathy
@NeeluTripathy -
 AMol NAik
AMol NAik
@amolnaik4 -
 Abhisek Datta
Abhisek Datta
@abh1sek -
 Abhinav Mishra
Abhinav Mishra
@0ctac0der -
 N B Sri Harsha
N B Sri Harsha
@nbsriharsha -
 Subhash
Subhash
@pbssubhash
Something went wrong.
Something went wrong.























































































![hunter0x7's profile picture. [Hacker + lover of bash] I Don't know how to hack but i know how to pwnd!](https://pbs.twimg.com/profile_images/1176789748322643968/bEReriMR.jpg)