你可能會喜歡
Yesterday I revisited the fundamentals of HTTP Requests. Today I explored another layer of web security: HTTP Security Headers: the guards against XSS, clickjacking, insecure redirects & data leaks. #Cybersecurity #WebSecurity
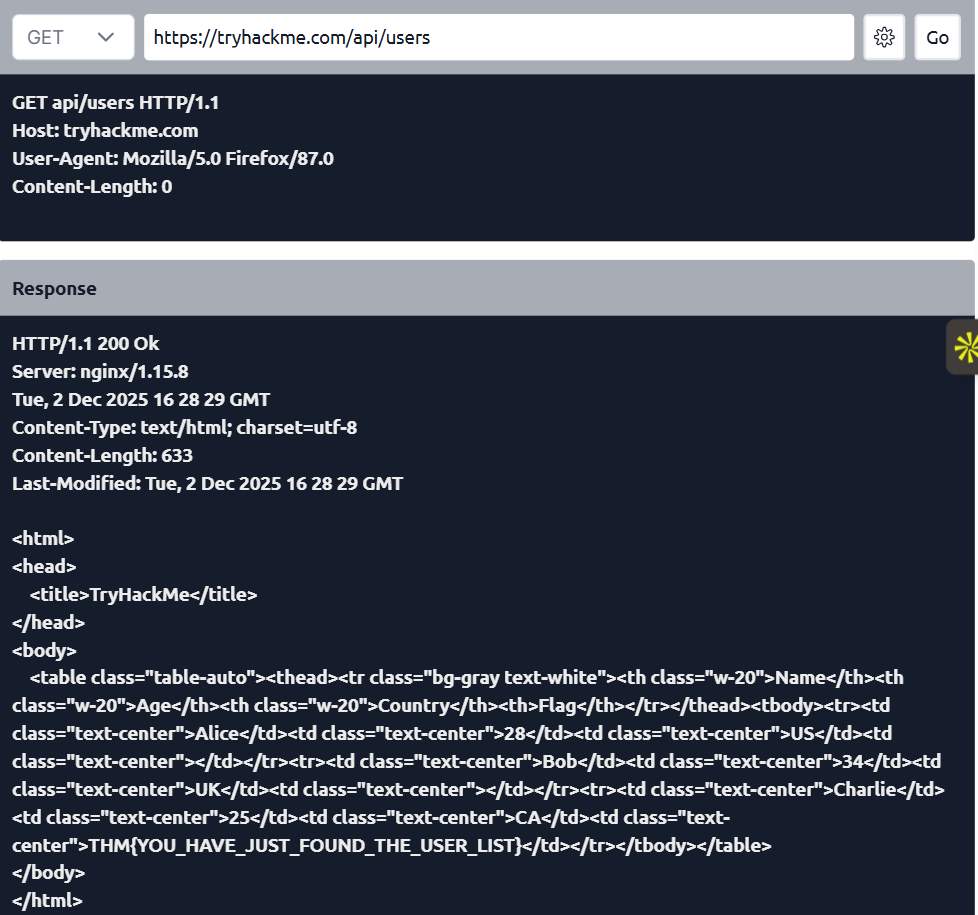
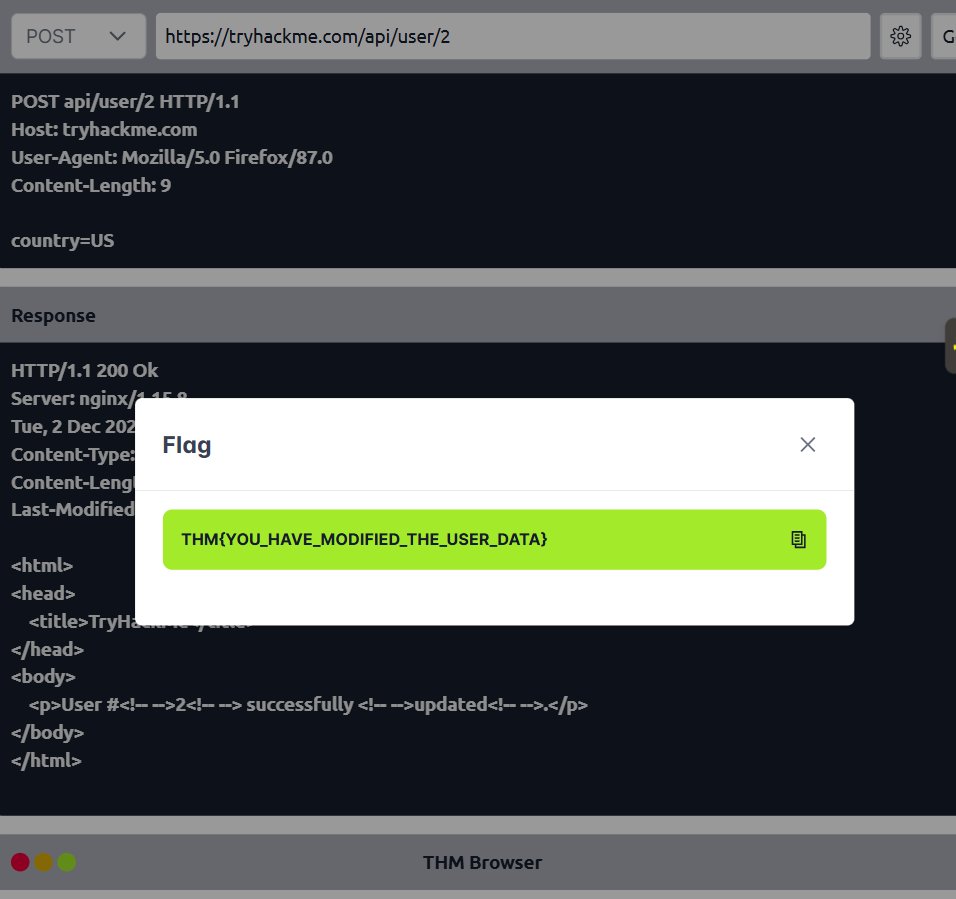
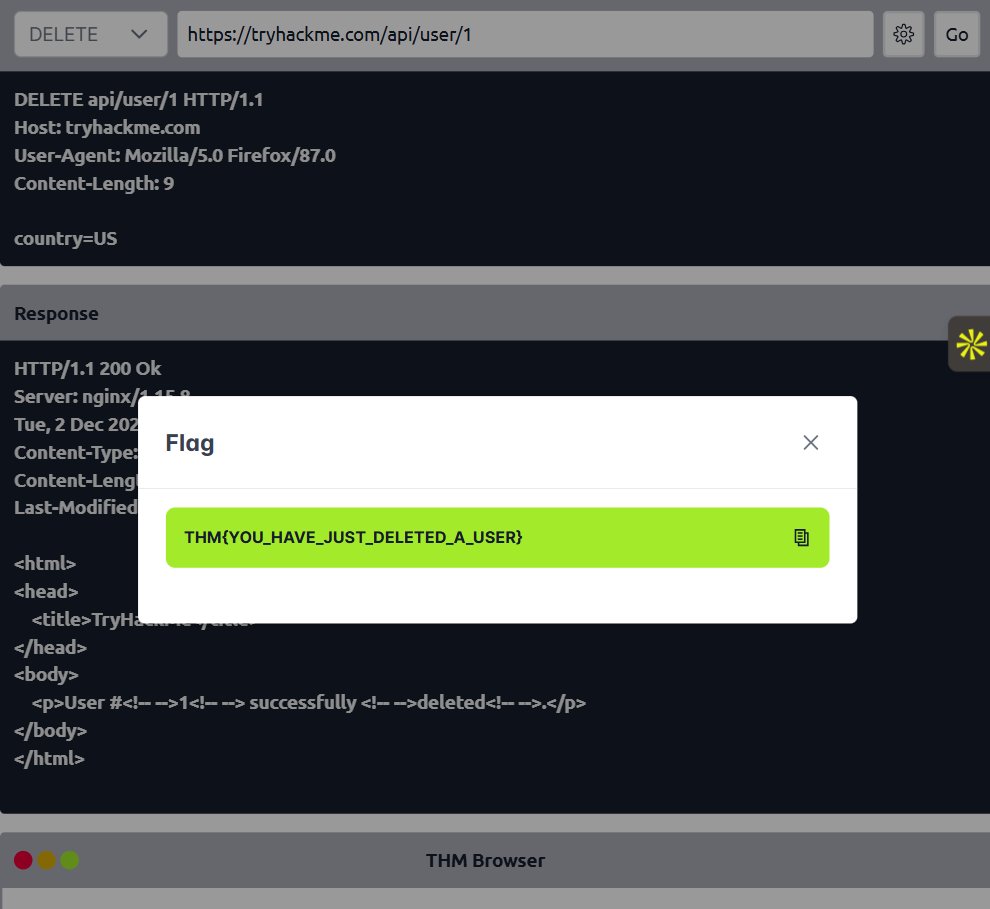
Yesterday, I revisited the foundations of HTTP Requests. Today, I shifted to the other side of the communication flow: HTTP Responses: how servers talk back to clients, and the subtle clues these messages give attackers. #TryHackMe #TechTwitter
Day 63 Hands-On Practical: Nmap scan types, OS & version discovery, port filtering, and outputs completed a pen test for a client, focused on active reconnaissance using Nmap. #Pentest #Nmap #VulnerabilityManagement #InfoSec
Day 62: Today I completed an authorized internal penetration test against an isolated lab environment designed to mirror a client’s legacy service stack. #CyberSecurity #VulnerabilityAssessment #HandsOnLearning
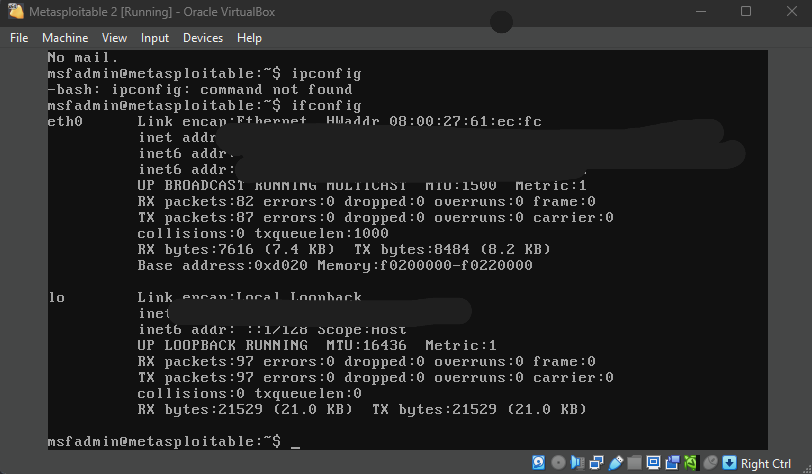
Day 61 of Learning: Today I explored two OSINT (Open-Source Intelligence) tools that highlight just how much information is available online if you know where to look. #CyberSecurity #OSINT #InfoSec #DigitalFootprint #LearningInPublic
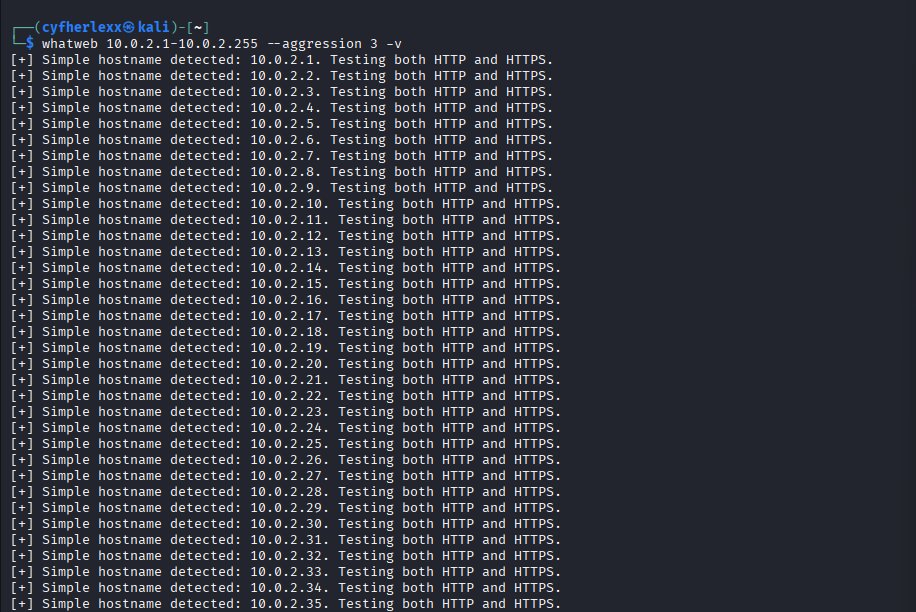
Day 59 of Learning: I explored WhatWeb (aggression level 3) in my lab environment to understand the depth of reconnaissance possible. Key findings included: 🔵 HTTP headers & server banners 🔵 TLS certificate details #Cybersecurity #WhatWeb #EthicalHacking #Infosec #WebSecurity

Here's a little math problem about GRID 🤔 Multiple agentic capabilities available in one place Data sources across industries + Reasoning to bring it all together —————————————————————————— = The best answers you can ask for
Here's a little math problem about GRID 🤔 Multiple agentic capabilities available in one place Data sources across industries + Reasoning to bring it all together —————————————————————————— = The best answers you can ask for
I’ve officially completed the @CiscoNetAcad Ethical Hacker course and earned the certificate 🎉 It built a solid foundation in ethical hacking and offensive security. Excited to keep learning and growing in cybersecurity. #CyberSecurity #EthicalHacking #Cisco

Day 57: Post-Exploitation, Persistence & Evasion Today’s focus in my ethical hacking journey was on what happens after gaining access to a system: staying in, moving around, and avoiding detection. 🧵 #EthicalHacking #RedTeam
Day 56: Penetration Testing Tools & Exploit Code Analysis. ✍️ Today, I focused on understanding when, why, and how different tools are used across four major categories of a penetration test. #Cybersecurity #LearningInPublic
Day 55: Understanding Scripting Logic in Cybersecurity. Today was all about the fundamentals of scripting and how they tie directly into cybersecurity tasks like automation, analysis, and tool building. 🧵 #CyberSecurity #BlueDotLogs #Day55
Day 53–54 of My Cybersecurity Journey: From Vulnerability Discovery to Strategic Remediation During a pentest on a vulnerable DVWA server (10.6.6.13), I shifted focus from just scanning to what separates beginners from professionals: Let’s break it down. 👇🧵
Day 52 of My Cybersecurity Journey – The Power of Reporting: Let’s talk about something that separates script kiddies from professionals. How we report findings after a penetration test. It’s not just what you find - it’s how you communicate it.🧵👇 #CyberSecurityJourney
Day 50 – 51 of My Cybersecurity Journey: Post-Exploitation, Persistence & Lateral Movement. Happy New Month, everyone! 🫂 Initial access is the start. The real challenge begins with maintaining control, moving across systems, and avoiding detection. Let’s break it down. 🧵👇
Day 49 of My Cybersecurity Journey: Post-Exploitation, Footholds & Persistence After gaining access to a system, what comes next? Today, I explored how attackers maintain access after a successful compromise. Here's what I learned: 👇🧵 #CyberSecurity #EthicalHacking #InfoSec
Day 48 of My Cybersecurity Journey Today’s focus was on IoT protocols. Let’s break it down 👇 #Cybersecurity #IoTSecurity #Day48
Day 47 of #CybersecurityJourney Exploring Attacks on Mobile & IoT Systems Today’s focus: how attackers compromise the systems we carry in our pockets and the "smart" devices around us. Let’s break it down 👇🧵 #Cybersecurity #MobileSecurity #IoTSecurity #EthicalHacking
Day 46: Cont'd – Cloud, Mobile & IoT Security. Today’s deep dive into offensive cloud security techniques was packed. Here's what I explored, practiced, and documented 👇🧵 #CyberSecurity #CloudSecurity #EthicalHacking
Day 45: Cloud, Mobile & IoT Security Today, I explored one of the most important areas in cybersecurity: Cloud Security with a focus on how attackers exploit cloud infrastructure. Let’s break it down 👇 #CyberSecurity #EthicalHacking #CloudSecurity
United States 趨勢
- 1. Chris Paul 15.6K posts
- 2. #SpotifyWrapped 14.8K posts
- 3. Clippers 24.3K posts
- 4. Good Wednesday 28.2K posts
- 5. #NSD26 4,673 posts
- 6. #WednesdayMotivation 3,273 posts
- 7. Happy Hump 6,216 posts
- 8. Hump Day 9,424 posts
- 9. FELIX LV VISIONARY SEOUL 25.8K posts
- 10. National Signing Day 2,886 posts
- 11. #FELIXxLouisVuitton 29.1K posts
- 12. TOP CALL 10.1K posts
- 13. Nashville 31K posts
- 14. #PutThatInYourPipe N/A
- 15. The BIGGЕST 296K posts
- 16. jungkook 263K posts
- 17. Elden Campbell N/A
- 18. Somalians 86.5K posts
- 19. Somalis 100K posts
- 20. Market Focus 4,621 posts
你可能會喜歡
-
 Bluemool Limited
Bluemool Limited
@bluemoolltd -
 JustParkwell
JustParkwell
@JustParkwell -
 Femi for HOR Eti Osa Campaign Office
Femi for HOR Eti Osa Campaign Office
@Femi4HOR -
 Tobiah 🙂↔️
Tobiah 🙂↔️
@TobiahRims -
 traderkareem
traderkareem
@A_dkareem -
 Thayaw
Thayaw
@Sphinxtee -
 Everything Kids Online
Everything Kids Online
@everythingkidss -
 卍
卍
@not0jay -
 0xRaphael🍊,💊
0xRaphael🍊,💊
@official_Lagwaa -
 Veeki Estate And Properties Limited
Veeki Estate And Properties Limited
@veekiestate -
 satimaClemz
satimaClemz
@ClemzSatima -
 Aderemi Azeez
Aderemi Azeez
@raycre8tives -
 Opoobo
Opoobo
@opoobo
Something went wrong.
Something went wrong.













































































































