내가 좋아할 만한 콘텐츠
All good things must come to an end - will now be at bsky.app/profile/rajsam…
Our latest @metasploit weekly wrap up details a new module for an unauthenticated remote code execution bug in NetAlertX (CVE-2024-46506 plus more... rapid7.com/blog/post/2025… #infosec #cybersecurity
Our weekly @metasploit wrap-up details a module which exploits CVE-2018-15745, an unauthenticated directory traversal leading to file disclosure in Argus Surveillance DVR 4.0.0.0. rapid7.com/blog/post/2025… #infosec #cybersecurity
Our latest @metasploit weekly wrap up details a new exploit module for Craft CMS, when the attacker can use malicious FTP server to gain remote code execution rapid7.com/blog/post/2025… #infosec #cybersecurity
Our latest @Rapid7 analysis details the 2024 #ransomware landscape. Included are the 10 most prolific ransomware groups in 2024, ranked by the number of posts on leak sites. rapid7.com/blog/post/2025… #infosec #cybersecurity H/T @ChristiaanBeek
Our latest @metasploit weekly wrap-up includes a new module for exploiting CVE-2024-51092, an authenticated command injection in LibreNMS. It allows the attacker to run system commands and gain remote code execution (RCE) rapid7.com/blog/post/2025… #infosec #cybersecurity
Our latest @metasploit weekly wrap-up includes an exploit module for CVE-2024-55956, an unauthenticated file write vulnerability affecting Cleo LexiCom, VLTrader, and Harmony versions 5.8.0.23 and below. rapid7.com/blog/post/2025… #infosec #cybersecurity
Our latest @rapid7 analysis details CVE-2024-55591, an authentication bypass vulnerability in FortiOS and FortiProxy rapid7.com/blog/post/2025… #infosec #0day
Our latest @metasploit weekly wrap up includes multiple new modules including an exploit module for an unauthenticated arbitrary file read vulnerability, tracked as CVE-2024-45309, which affects OneDev versions <= 11.0.8. rapid7.com/blog/post/2025… #infosec #cybersecurity
Our latest @rapid7 advisory details CVE-2025-0282: Ivanti Connect Secure zero-day which has been exploited in the wild. More details here: rapid7.com/blog/post/2025… #infosec #cybersecurity
rapid7.com
CVE-2025-0282: Ivanti Connect Secure Zero-Day Exploited in the Wild | Rapid7 Blog
CVE-2025-0282: Ivanti Connect Secure Zero-Day Exploited in the Wild | Rapid7 Blog
Our @metasploit 2024 wrap-up details the most notable improvements and modules including expanded support for Active Directory Certificate Services AD CS attacks. More details here: rapid7.com/blog/post/2025… #infosec
My latest article is now published on @SCmagazineUK detailing the challenges in dealing with a #ransomware attack, and technical and ethical challenges this poses: insight.scmagazineuk.com/ransomware-rea… #malware #cybersecurity
Our technical analysis now available @AttackerKb on CVE-2024-53677, a flawed upload logic vuln in Apache Struts 2 which permits an attacker to override internal file upload variables in apps using Apache Struts 2 File Upload Interceptor. attackerkb.com/topics/YfjepZ7… H/T @the_emmons
Now available on @AttackerKb is our @Rapid7 technical analysis of#Cleo CVE-2024-55956 - H/T @stephenfewer this is a new vuln, not a patch bypass of CVE-2024-50623. IoCs included here: attackerkb.com/topics/geR0H8d… #infosec
Our latest @metasploit weekly wrap-up details RCEs for Moodle e-Learning platform, Primefaces, WordPress Really Simple SSL and CyberPanel along with two modules to change password through LDAP and SMB. rapid7.com/blog/post/2024… #infosec
Our latest @rapid7 analysis into a payload from the recent Cleo file transfer vuln reveals an encoded Java Archive payload. Note that this isn’t necessarily the only payload that has or will be deployed rapid7.com/blog/post/2024… H/T @ChristiaanBeek #cybersecurity

Our latest Rapid7 analysis details Widespread exploitation of Cleo file transfer software (CVE-2024-50623) - with links to detection/mitigation guidance included: rapid7.com/blog/post/2024… #infosec #cybersecurity
rapid7.com
Widespread Exploitation of Cleo File Transfer Software | Rapid7 Blog
Widespread Exploitation of Cleo File Transfer Software | Rapid7 Blog
Our latest @metasploit weekly wrap-up details a number of new modules, including "an exploit module for a CRLF injection vulnerability in Ivanti Connect Secure to achieve remote code execution" rapid7.com/blog/post/2024… #infosec #cybersecurity
Our latest @rapid7 analysis details does a deep dive into the latest Black Basta #ransomware campaign which drops Zbot, DarkGate, and Custom #Malware - included are IoCs, MITRE techniques and content coverage: rapid7.com/blog/post/2024… #infosec #cybersecurity
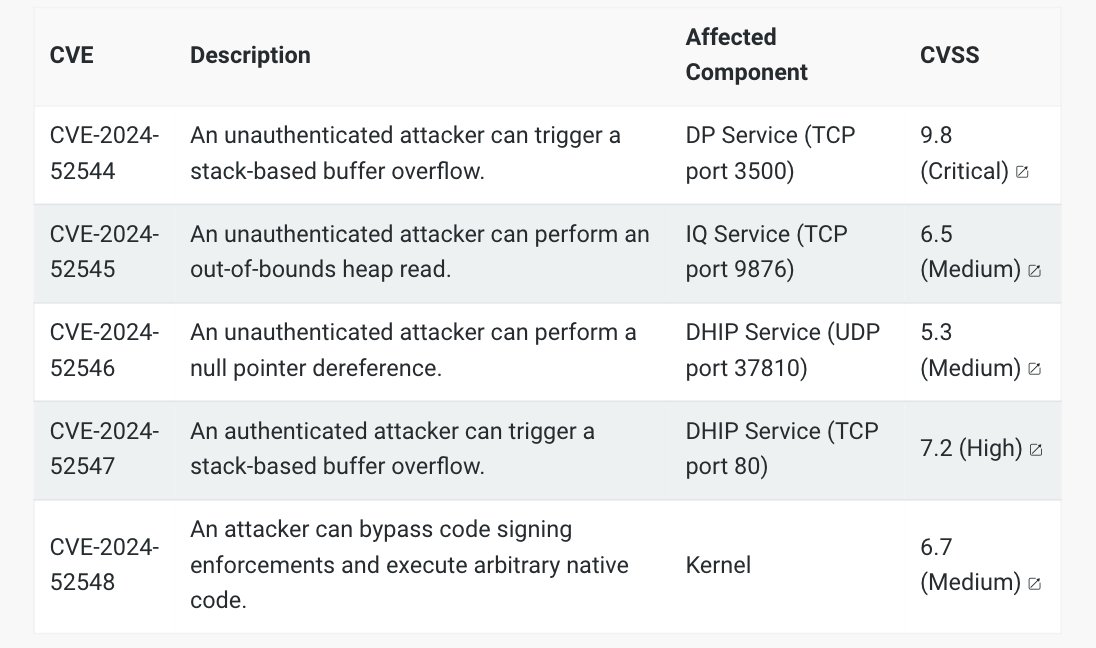
Our latest @rapid7 analysis details multiple vulnerabilities in the Lorex 2K Indoor Wi-Fi Security Camera, consisting of five distinct vulnerabilities, which operate together in two phases to achieve unauthenticated RCE rapid7.com/blog/post/2024… #cybersecurity H/T @stephenfewer
United States 트렌드
- 1. Chiefs 89.7K posts
- 2. Brian Branch 4,309 posts
- 3. #TNABoundForGlory 44.1K posts
- 4. Mahomes 26K posts
- 5. #LoveCabin N/A
- 6. LaPorta 9,610 posts
- 7. Goff 12.7K posts
- 8. Bryce Miller 3,782 posts
- 9. #OnePride 6,068 posts
- 10. Kelce 14.2K posts
- 11. Butker 8,069 posts
- 12. #DETvsKC 4,501 posts
- 13. #ALCS 10K posts
- 14. Mariners 45K posts
- 15. Gibbs 5,469 posts
- 16. Dan Campbell 2,399 posts
- 17. Baker 51.6K posts
- 18. Pacheco 4,661 posts
- 19. Collinsworth 2,634 posts
- 20. Tyquan Thornton 1,164 posts
내가 좋아할 만한 콘텐츠
-
 SANS ICS
SANS ICS
@SANSICS -
 Eyal Estrin ☁️
Eyal Estrin ☁️
@eyalestrin -
 Infosecurity Europe
Infosecurity Europe
@Infosecurity -
 Gregory Hale
Gregory Hale
@isssource -
 BUFFERZONE Security
BUFFERZONE Security
@BufferZoneSec -
Security4all
@security4all -
 Marco (Marc) Ayala
Marco (Marc) Ayala
@ICS_SCADA -
 Nitroxis Sprl
Nitroxis Sprl
@nitroxis_sprl -
 Paul Coggin
Paul Coggin
@PaulCoggin -
 Darren Argyle
Darren Argyle
@D_Argyle -
 Frumious Scadateer
Frumious Scadateer
@scadateer
Something went wrong.
Something went wrong.