Animalware
@ReEnElec
Reverse engineer, hardware developer and Amiga fan boy
คุณอาจชื่นชอบ
We’re seeing a clear trend: attackers are bypassing the endpoint entirely. Not just avoiding traditional EDR-monitored systems by pivoting to embedded and edge devices, but now also operating purely in the cloud. No shell, no malware, no persistence on the endpoint. Just an OAuth…
.@Volexity #threatintel: Multiple Russian threat actors are using Signal, WhatsApp & a compromised Ukrainian gov email address to impersonate EU officials. These phishing attacks abuse 1st-party Microsoft Entra apps + OAuth to compromise targets. volexity.com/blog/2025/04/2… #dfir
🚨NEW: Elon Musk has called Senator Mark Kelly (D-AZ) a “traitor” after visiting Ukraine this weekend. Kelly is a 25-year U.S. Navy pilot veteran and retired astronaut. RETWEET if you stand with @CaptMarkKelly against Elon Musk’s unpatriotic attacks!

A specialized build of `curl` that mimics the behavior of browsers like Chrome,Firefox, and Safari to avoid anti-bot measures in web scraping and automated HTTP requests

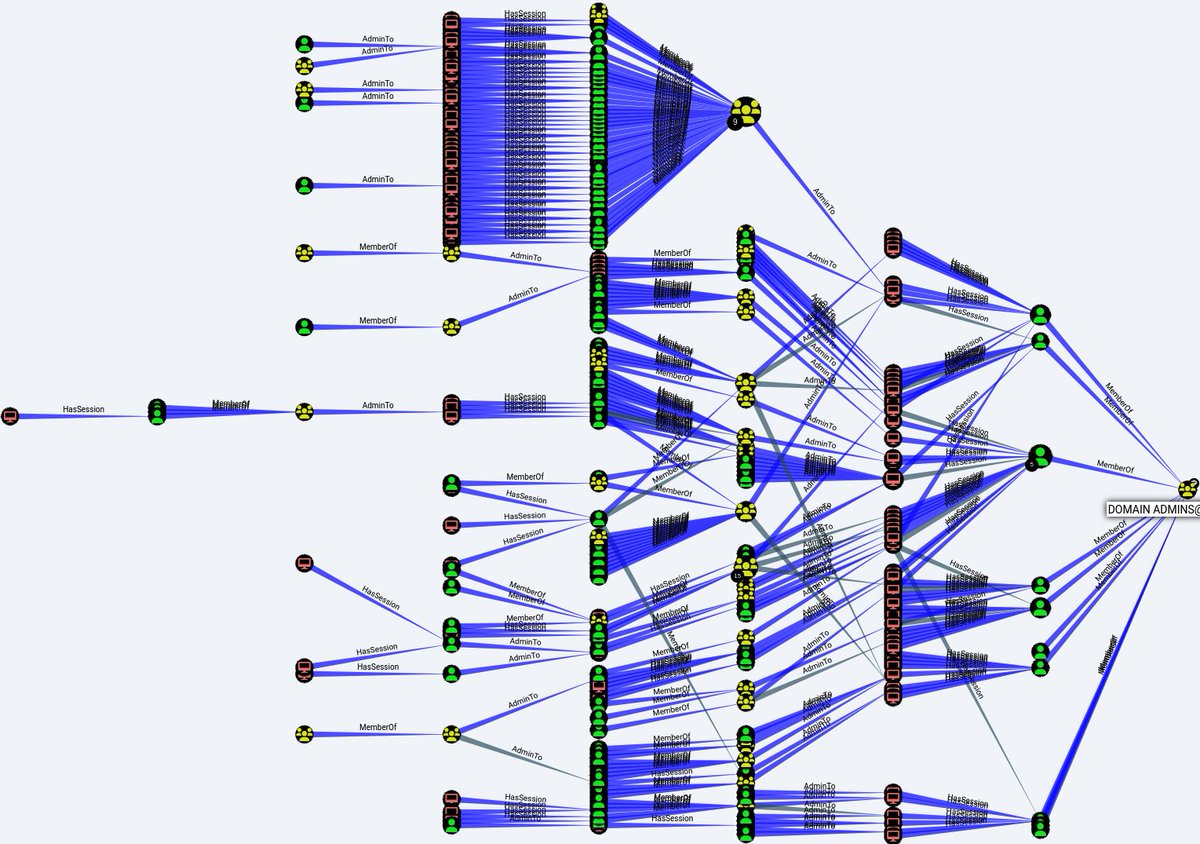
Just released SCCMHound! A BloodHound collector for SCCM. SCCMHound allows both attackers and defenders to construct BloodHound datasets using the vast amount of information that is stored/retrievable through SCCM. Feel free to take it for a spin! github.com/CrowdStrike/sc…
onedrive.exe (phoneactivate.exe #lolbin) side-loads tampered sppc.dll which in turn loads onedrive.dll and decrypts it with RC4 systemfunction033 and hardcoded key. The decrypted payload appears to be related to #havoc (h/t @embee_research @elasticseclabs) with the mentioned C2.




The powershell script also copies phoneactivate.exe in the temp folder as onedrive.exe, which leverages DLL sideloading and generates traffic to 47,84,196,148:443. Possible new Lolbin? I have not found any information about this.


Erik and @jonasl’s Network Fingerprinting talk is now online. It covers #JA4 and #JARM by @4A4133, @lcamtuf’s #p0f and @xnih’s Satori. Thanks to @netnod for having us! youtu.be/1_VbYp4Zyno

youtube.com
YouTube
Network Fingerprinting - Erik Hjelmvik and Jonas Lejon
"Swiss-army tool for scraping and extracting data from online assets, made for hackers"

Give this a look, it’s called GHOSTS, it allows you to simulate/automate different types of user traffic/activities. Normally used cybersecurity testing, it might work for what you need. github.com/cmu-sei/GHOSTS
As I’m building out my ISE lab, it got me thinking. How do you simulate having users and devices on your network? Is there something that emulates an iPhone, Android, printer etc. so you can play around with profiling?
Whenever I’m checking RDP logs and wonder if a full GUI was obtained, I often refer back to this excellent article by Ponder The Bits on RDP event log tracking: ponderthebits.com/2018/02/window…
I know quite some people within my followers that are representing their tooling(s)/platform/organization related to infosec/threat hunting. Lets use this post to “advertise” the purpose of your tooling/platform usage so others can possibly hop in the train to learn new things!
📝 Just published a quick blog post: "Unintentional Evasion: Investigating How CMD Fragmentation Hampers Detection & Response" A recent investigation prompted me to share some quick thoughts on the topic of command line omission and fragmentation in Windows CMD, which can…
Mandiant released CAPA Explorer, a UI to explore CAPA results! This is pretty cool, well done @williballenthin and all! 👏 👉 mandiant.github.io/capa/explorer#… #malware #infosec #malware

I've open-sourced my Docker #honeypot logs from the past few years. The honeypot emulated a publicly accessible Docker instance (no SSL or auth) and logged requests. github.com/silascutler/do…


Hello defenders 🎯 So excited to release second blog about #AiTM Hunting! This time, I wrote about using #KQL hunting queries to detect AiTM activity in a Unified Security Operations Platform. I co-authored this blog with Arjun Trivedi🚀🚀🚀 ✔️Blog : techcommunity.microsoft.com/t5/microsoft-s…
Great talk from Jessica Wilson on open-source #DFIR tools and workflows! - "Forensic Flows, but make them better" youtu.be/oiPumjLLpKk?si…
🚀Introducing OpenRelik: Open-source platform for digital forensic investigations. Modular workflows, collaboration, central artifact repository and easily extendable to support new tools in a clean, easy to use interface. openrelik.org
When we respond to large scale compromise, we regularly see the same kinds of configuration issues across Entra ID. If you want some insight to what we see in real world compromises, I put together an overview here - microsoft.com/en-us/security…
Super excited to finally release a project I have been working on for the last few months! 🎊🎊 Introducing the REx: Rule Explorer project and Detection Engineering Threat Report (DETR) 🎉🎉 br0k3nlab.com/posts/2024/07/… If you found LoFP from lolol.farm useful, this…
I've just resolved all broken API endpoints in DefenderHarvester. Most endpoints were changed on the backend, the downside of tapping into unofficial API's I guess :D Also, added an option to retrieve all configured suppression rules. github.com/olafhartong/De…

The video of my #RSAC talk is out. Anyone interested in #ThreatHunting will want to check out it! "I Screwed Up Threat Hunting a Decade Ago, and Now We're Fixing it With PEAK" buff.ly/3zrKSWJ

United States เทรนด์
- 1. New York 23.6K posts
- 2. New York 23.6K posts
- 3. Virginia 534K posts
- 4. Texas 226K posts
- 5. Prop 50 186K posts
- 6. #DWTS 41.2K posts
- 7. Clippers 9,683 posts
- 8. Cuomo 416K posts
- 9. TURN THE VOLUME UP 21.9K posts
- 10. Van Jones 2,512 posts
- 11. Ty Lue 1,006 posts
- 12. Harden 10K posts
- 13. Jay Jones 103K posts
- 14. Bulls 37.1K posts
- 15. #Election2025 16.5K posts
- 16. Sixers 13.1K posts
- 17. WOKE IS BACK 38.9K posts
- 18. Isaiah Joe N/A
- 19. #questpit 5,952 posts
- 20. Eugene Debs 3,191 posts
Something went wrong.
Something went wrong.