_D4Z3N_
@_D4z3n_
Malware Researcher 🙈
你可能會喜歡
#AllYourTorrentsBelongToUs #malware #torrent All Your Torrents Belong To Us reversingminds-blog.logdown.com/posts/7821320-…

#GhostFrame is responsible for over 1M #phishing attacks using stealthy iframes. This highlights the need for smarter defenses and ongoing training. See how Barracuda’s research team is helping your business stay safe. blog.barracuda.com/2025/12/04/thr… #BarracudaONEplatform

Evade behavioral analysis by executing malicious code within trusted Microsoft call stacks, patchless hooking library IAT/EAT github.com/hwbp/LazyHook
Attention malware analysts 💻 Our latest blog post delves into Time Travel Debugging (TTD). We introduce the basics of WinDbg and TTD to help you start incorporating TTD into your analysis. 📄: bit.ly/441J3vS

#RONINGLOADER -> PPL abuse, the new hotness.

#ElasticSecurityLabs uncovers #RONINGLOADER, a multi-stage loader utilizing signed drivers, PPL abuse, CI Policies, and other evasion techniques to deliver #DragonBreath's gh0st RAT variant. Check it out at ela.st/roningloader

🚨BREAKING: We uncovered LANDFALL — a commercial-grade Android spyware exploiting a now-patched Samsung zero-day (CVE-2025-21042) through weaponized DNG images sent via WhatsApp, enabling zero-click compromise of Samsung Galaxy devices. 1/ unit42.paloaltonetworks.com/landfall-is-ne…
Microsoft Incident Response – Detection and Response Team (DART) uncovered SesameOp, a new backdoor that uses the OpenAI Assistants API for C2. DART shared the findings with OpenAI, who identified and disabled an API key and associated account. msft.it/6012tGbpm SesameOp…
A new approach to static analysis with AI that turns days of research into hours. No MCP or live IDA required. Using GPT-5, we completely cracked XLoader v8, one of the most challenging malware families to analyze. #XLoader #MalwareAnalysis #AI research.checkpoint.com/2025/generativ…
This article explores a novel attack technique that combines Ghost SPNs and Kerberos reflection to elevate privileges on SMB servers, highlighting a critical gap in traditional detection methods. It details how attackers can exploit stale or misconfigured Service Principal Names…
new ppl here for malware content, check out my github page. c2, process injections, syscall libraries, etc... varying levels, as i've shared materials along my whole journey. lots new to drop still github.com/teach2breach
Great research from Mandiant, learned a lot from their analysis. cloud.google.com/blog/topics/th… Found more trojanized JavaScripts communicating with the same transaction hash. Sometimes it’s shocking how well DPRK actors understand blockchain mechanics and weaponize them.…
We first introduced the term “Premier Pass” during my talk at @pivot_con — describing a trend of advanced collaboration among China-aligned APT groups like Earth Estries & Earth Naga. Today, we published a blog post that explores the concept in depth. trendmicro.com/en_us/research…
#ESETresearch discovered a new wave of the well-known 🇰🇵 Lazarus campaign Operation DreamJob, now targeting the drone industry. @pkalnai @alexis_rapin welivesecurity.com/en/eset-resear… 1/9
#ElasticSecurityLabs joins forces with @tamusystem and discloses TOLLBOOTH, an IIS module used for SEO abuse that relies on publicly exposed ASP. NET machine keys: go.es.io/3L68p57
Unit 42 shares a step-by-step guide to cloud incident response. Learn how cloud investigations differ from traditional incidents, focusing on identities, misconfigurations and service interactions. bit.ly/46JEbxn

Elastic Security Labs introduces nightMARE, a versatile Python library for malware analysis, featuring static analysis tools and configuration extractors for various malware families, now available in version 0.16. #MalwareAnalysis #PythonLibrary elastic.co/security-labs/…
Unit 42 recently responded to a ransomware incident involving BlackSuit at a manufacturing client. This event illustrates how a single compromised VPN credential, obtained through a vishing attack, can lead to significant operational impact. bit.ly/42DUrO3

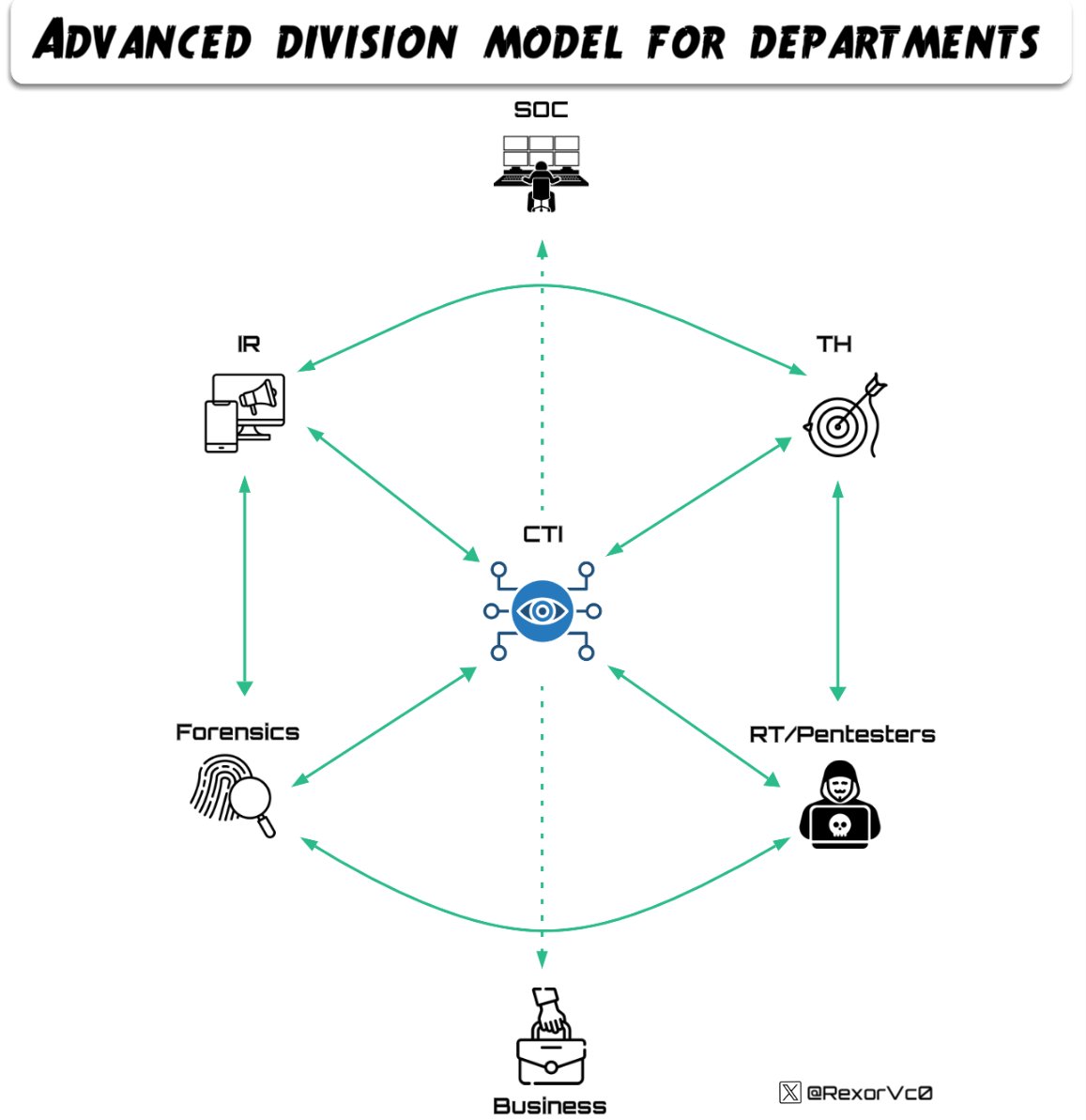
📡New blog about my talk "CTI: The Dark Cloak" where we explore how #intel teams collaborate to tackle real #TA 🕵️♂️ We analyze threats from #CTI, assisting other teams such as #TH and #DFIR, extracting max value from every piece of info 🔗Blogpost: rexorvc0.com #RE



Unit 42 presents a proof of concept on indirect prompt injection in AI agents. This method can store malicious instructions in an agent's memory, affecting future interactions. bit.ly/3L2ppcs
We at @emproofsecurity open-sourced a free firmware reverse engineering workshop for self-study. Topics: ELF analysis, cracking, malware triage, embedded-Linux, bare-metal, crypto-key extraction, anti-analysis. Docker setup and solutions included. github.com/emproof-com/wo…
🚀 We are proud to announce the availability of Threatray Release v2.1, bringing an exciting set of additions and improvements to the platform. 🤝 We’ve partnered with @nextronsystems, a pioneer in YARA and Sigma rule detection, to bring their industry-leading detection…

United States 趨勢
- 1. Lakers 44.7K posts
- 2. Spurs 36.5K posts
- 3. JUNGKOOK FOR CHANEL BEAUTY 36.7K posts
- 4. Doug Dimmadome 9,881 posts
- 5. Godzilla 20.7K posts
- 6. Michigan 123K posts
- 7. Marcus Smart 2,194 posts
- 8. Wemby 5,428 posts
- 9. Dolly Parton 2,720 posts
- 10. Sherrone Moore 63.6K posts
- 11. #Survivor49 5,224 posts
- 12. Jim Ward 10.1K posts
- 13. Erika 178K posts
- 14. PETA 26.2K posts
- 15. Gainax 4,323 posts
- 16. #PorVida 1,513 posts
- 17. TOP CALL 10.1K posts
- 18. Stephon Castle 3,785 posts
- 19. #AEWDynamite 27K posts
- 20. Gabe Vincent 1,170 posts
你可能會喜歡
-
 Steve YARA Synapse Miller
Steve YARA Synapse Miller
@stvemillertime -
 Valthek
Valthek
@ValthekOn -
 CAPE Sandbox
CAPE Sandbox
@CapeSandbox -
 sysopfb
sysopfb
@sysopfb -
 S2
S2
@sisoma2 -
 Itay Cohen 🌱
Itay Cohen 🌱
@megabeets_ -
 Evilcry_
Evilcry_
@Blackmond_ -
 Herbie Zimmerman
Herbie Zimmerman
@HerbieZimmerman -
 J.A.R.V.I.S
J.A.R.V.I.S
@peppermalware -
 Philippe Lagadec
Philippe Lagadec
@decalage2 -
 Catch all the Malwa
Catch all the Malwa
@MalwareCantFly -
 Drunk Binary
Drunk Binary
@DrunkBinary -
 Antelox
Antelox
@Antelox -
 sean
sean
@seanmw -
 Farenain
Farenain
@Farenain
Something went wrong.
Something went wrong.