
你可能會喜歡
#flareon12 challenges 7 to 9 were pretty cool, even though 9 was pretty punitive. A bit too much math and not enough malware for my taste. Still hope they can keep the yearly burnout tradition alive in the future ;-)

La team @FlatNetworkOrg tfns.fr ctftime.org/team/87434/ The Flat Network Society TOP 5 Mondial CTFTime gagne des bons d'achats 🍖, des médailles de bronze gravées Barbhack, des bières édition limitée, un module #flipperzero Messenger

Given the recent events with VMPSoft DMCA'ing educational YouTube videos demonstrating how to unpack malware protected with VMProtect, we have decided to release a free to use unpacker which works for all versions of VMP 3.x including the most recent version. Simply sign…

After #flareon11 challenge 7, I got inspired to build tooling for #dotnet Native AOT reverse engineering. As such, I built a #Ghidra Analyzer that can automatically recover most .NET types, methods and frozen objects (e.g., strings). Blog:👉blog.washi.dev/posts/recoveri…

Excellent post on quick and dirty Lumma control flow deobfuscation using ghidralib and Python cert.pl/en/posts/2025/…
We released a few more video of Recon 2024. @oliverlavery @_revng @ergrelet @lauriewired @allthingsida @buherator youtube.com/@reconmtl recon.cx #reverseengineering #cybersecurity Have a good weekend!
PyGhidra (Python3 Ghidra) is official now!
⌛ This series will take you through installing WinDbg and configuring Binary Ninja to use the WinDbg engine to create and use TTD traces. It will also show you how to capture TTD traces and replay them in Binary Ninja 👇 buff.ly/3Q8jMJd
I have a banger #BinaryRefinery release for y'all. Version 0.8.2 adds support for InnoSetup extraction: Thanks to @malcat4ever for porting part of innoextract to Python, it served as the main template for my code. Many thanks also to @SquiblydooBlog who pointed this out to me.
RULECOMPILE - Undocumented Ghidra decompiler rule language. A blog post about how frustration with poor decompilation led me to dive deep into Ghidra's decompiler to discover (and reverse-engineer) - an obscure, undocumented DSL msm.lt/re/ghidra/rule… #reverseengineering #ghidra

🚀Excited to announce ghidralib - a library that makes #Ghidra scripts drastically shorter and easier to write. I've been using it daily for #reverseengineering and decided it’s time to share! Check it out: github.com/msm-code/ghidr… And the docs: msm-code.github.io/ghidralib/ #infosec

I recently added a new #BinaryRefinery tutorial: github.com/binref/refiner… This one follows the same steps as a very cool #MalCat blog article (thanks to @malcat4ever!)
Reversing virtualized binaries is no easy task. Our intern Jack took on exploring automated devirtualization techniques, and presents in our latest blog post an efficient, modular, taint-based approach that leverages LLVM IR: blog.thalium.re/posts/llvm-pow…
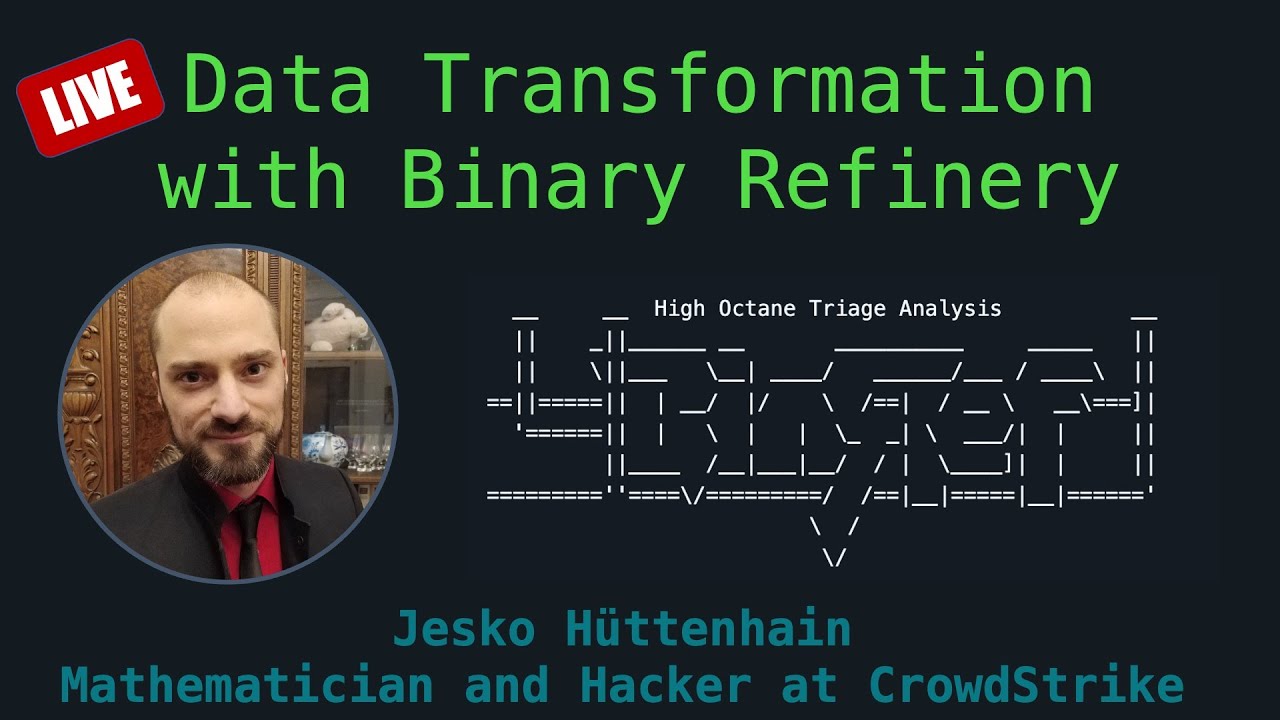
🎙️ Live streams resume tomorrow - Jesko Huttenhain (@huettenhain) joins us tomorrow at 11am CST to discuss data transformations with #BinaryRefinery! youtube.com/live/-B072w0qj…
youtube.com
YouTube
Explore Command-Line Driven Binary Transformations with Binary...
I just published my writeups for all challenges of #flareon11: 👉 washi1337.github.io/ctf-writeups/w… 👉 blog.washi.dev/posts/flareon1… Hope you like them as much as I liked writing them!

#flareon11 challenge 10 - almost blackbox vm solves: github.com/matthw/ctf/tre… / sorry @_marklech_ i didnt put more effort into it after the serpentine burnout, was a good one tho :)
My Windows User Space Emulator is now open source. Feel free to check out out ⬇️ github.com/momo5502/emula…
United States 趨勢
- 1. Branch 35.4K posts
- 2. Chiefs 110K posts
- 3. Red Cross 46.4K posts
- 4. Mahomes 34.2K posts
- 5. #LaGranjaVIP 79.1K posts
- 6. Binance DEX 5,084 posts
- 7. Rod Wave 1,519 posts
- 8. #TNABoundForGlory 58K posts
- 9. #LoveCabin 1,295 posts
- 10. Air Force One 50.6K posts
- 11. Bryce Miller 4,556 posts
- 12. Eitan Mor 12.8K posts
- 13. Alon Ohel 12.8K posts
- 14. #OnePride 6,447 posts
- 15. LaPorta 11.5K posts
- 16. Tel Aviv 54.3K posts
- 17. Dan Campbell 4,015 posts
- 18. Kelce 16.8K posts
- 19. Goff 13.8K posts
- 20. Omri Miran 13.1K posts
你可能會喜歡
-
 rev.ng
rev.ng
@_revng -
 Alice Climent
Alice Climent
@AliceCliment -
 Jiří Vinopal
Jiří Vinopal
@vinopaljiri -
 Ankit Anubhav
Ankit Anubhav
@ankit_anubhav -
 Hors
Hors
@horsicq -
 Invictus Incident Response
Invictus Incident Response
@InvictusIR -
 irfan_eternal
irfan_eternal
@irfan_eternal -
 Steve Eckels
Steve Eckels
@stevemk14ebr -
 4rchib4ld
4rchib4ld
@4rchib4ld -
 Moritz
Moritz
@m_r_tz -
 S3cur3Th1sSh1t
S3cur3Th1sSh1t
@ShitSecure -
 Br3akp0int
Br3akp0int
@tccontre18 -
 Gameel Ali 🤘
Gameel Ali 🤘
@MalGamy12 -
 Christopher Peacock
Christopher Peacock
@SecurePeacock -
 [email protected]
[email protected]
@pieceofsummer
Something went wrong.
Something went wrong.


































































![ReversingWithMe's profile picture. Object File Analysis, Programming Scientist.
I use [lol, haha, :), !] to deal with Poe's Law.
Reserve right to be wrong sometimes.](https://pbs.twimg.com/profile_images/1599224946038779904/DqxmcYpo.jpg)












































