내가 좋아할 만한 콘텐츠
The moment an occupation soldier attacked a Palestinian woman in Al-Aqsa Mosque this morning. #AlAqsaUnderAttack #Palestine
Link Hijacked, Account Impersonated. It's Broken Link Hijacking (BLH). #cybersecuritytips #cybersecurity #ethicalhacking #bugbounty #bugbountytips #WebSecurity #Pentesting

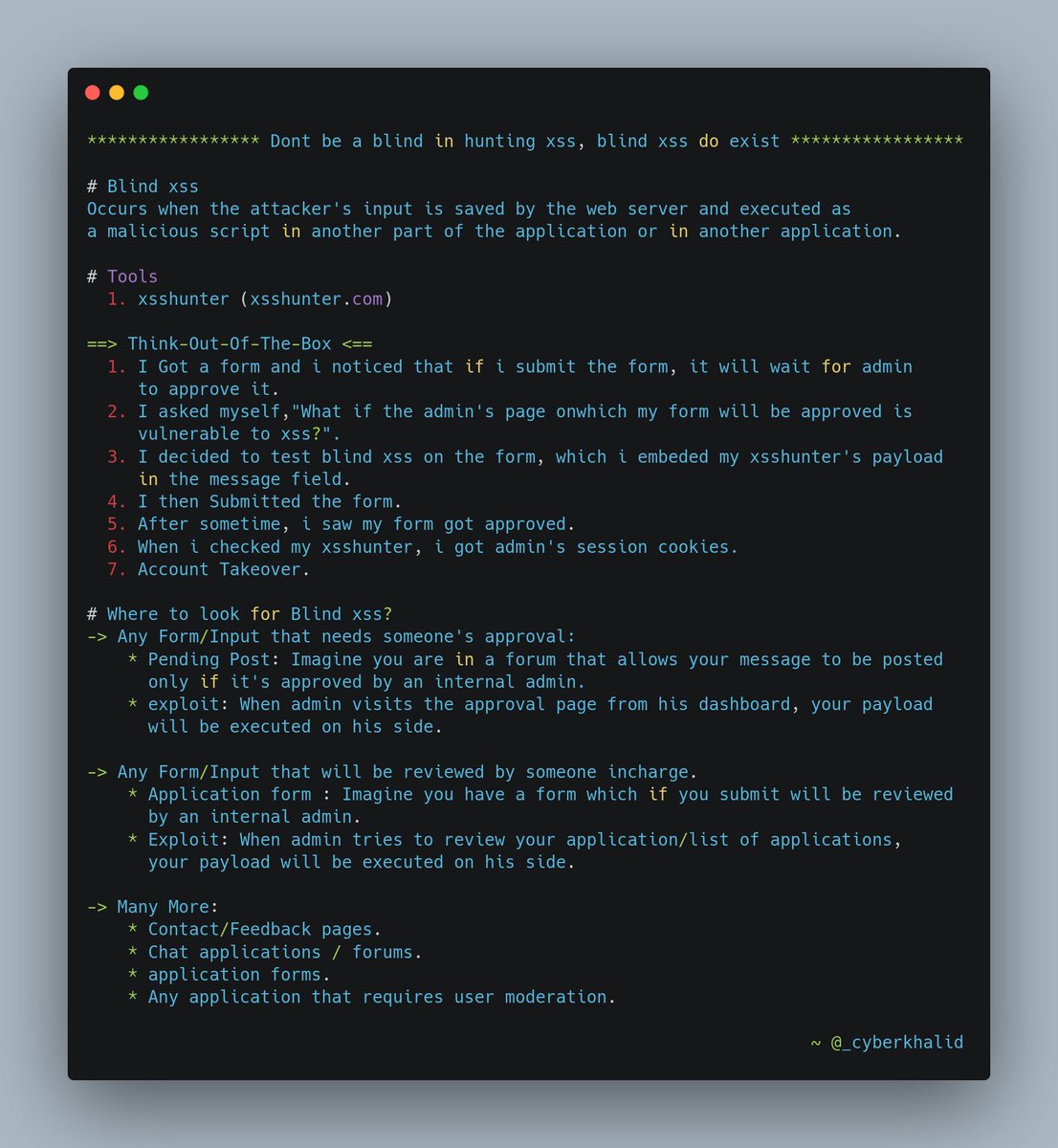
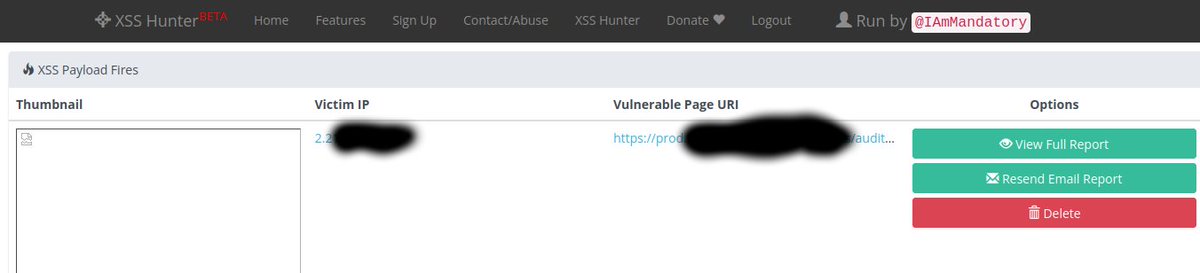
Blind XSS is kind of vulnerability that most hunters miss, This is my findings from hackerone public program inwhich I was able to takeover admin dashboard. Don't be a blind, blind XSS do exist #cybersecurity #bugbounty #infosec #infosecurity #Ethicalhacking #websecurity
#Ramadan Kareem! We wish you all an inspiring and rewarding month.

Finding Origin Ip behind waf using mail server #cybersecurity #cybersecuritytips #bugbountytips #bugbounty #infosec #infosecurity

Pic of the Day @johnjhacking #infosec #cybersecurity #cybersecuritytips #pentesting #oscp #informationsecurity #cissp #CyberSec

[HACKER TIP] If you are testing Open Redirect but there is a blacklisted character, you can test it with a chinese dot to bypass it or any other Unicode Character. example: redirect_to=////evil%E3%80%82com #bugbounty #hackertips #openredirect
![YogoshaOfficial's tweet image. [HACKER TIP] If you are testing Open Redirect but there is a blacklisted character, you can test it with a chinese dot to bypass it or any other Unicode Character.
example:
redirect_to=////evil%E3%80%82com
#bugbounty #hackertips #openredirect](https://pbs.twimg.com/media/FOI8-gOX0AYySFd.jpg)
Understand the logic thoroughly, then circumvent the logic accordingly. Be patient, be sophisticated, be ethical.
Top 30 React Projects for Beginners Thread🧵👇

OAuth 2.o bug bounty mindsets #cybersecurity #infosec #Pentesting #ethicalhacking

New Writeup - Circumventing Browser Security Mechanisms For SSRF. In this blog post we find our way around browser's mixed content policy to perform a SSRF against headless Chrome. Ft. @S1r1u5_ @iamnoooob @rootxharsh httpvoid.com/?p=Circumventi…

Managing #safety remains a vital task in #construction, but it’s a job that involves heavy record-keeping and constant training for success. How 3 construction companies use #tech to improve safety ✅👉 resources.industrydive.com/how-three-cons… #RINNO #deeprenovation @constructdive

How Server-Side request forgery(ssrf) works? #cybersecurity #infosec #infosecurity #ethicalhacking #Pentesting #CyberSec

Blind SSRF vulnerabilities arise when an application can be induced to issue a back-end HTTP request to a supplied URL, but the response from the back-end request is not returned in the application's front-end response. #cybersecurity #infosec #ethicalhacking #infosecurity
Nothing quite like a "Nice catch!" to make your day so much better 🥳

DLL hijacking is a method of injecting malicious code into an application by exploiting the way some Windows applications search and load Dynamic Link Libraries (DLL). #cybersecurity #CyberSec #infosec #infosecurity #Ethicalhacking #windows #redteam

PEASS-ng is a collection of tools that automates privilege escalation in linux, windows and Mac os #cybersecurity #Ethicalhacking #Pentesting #infosec #infosecurity #linux #windows #macOS #CyberSec github.com/carlospolop/PE…
Join on #IWD2022 for a powerful talk w/women leaders in #Web3! @BadBitch_Empire hosts @desfemmes @we3 @boysclubcrypto @wowpixiesNFT @wib @komerabi @shefi 👉👉 w/ @lisacarmenwang @lisabeyu @0xelan @leighcuen @maggie_love @manasilvora @parkerjayp @nftlily

Password reset poisoning is a technique whereby an attacker manipulates a vulnerable website into generating a password reset link pointing to a domain under their control. #cybersecurity #Ethicalhacking #Pentesting #infosecurity #CyberSec #WebSecurity

United States 트렌드
- 1. Prince Andrew 33.2K posts
- 2. $AMZN 50.2K posts
- 3. Ryan Clark 3,158 posts
- 4. Happy Halloween 316K posts
- 5. Sydney Sweeney 107K posts
- 6. Usha 34.3K posts
- 7. Andrew Mountbatten Windsor 7,548 posts
- 8. Rhule 5,664 posts
- 9. Heritage 46.3K posts
- 10. Somalia 59.3K posts
- 11. $AAPL 87.2K posts
- 12. Scream 7 45.9K posts
- 13. #Prop50VoteYes 6,925 posts
- 14. Royal Lodge 7,904 posts
- 15. Bill Kristol 1,951 posts
- 16. Necas 2,934 posts
- 17. Buckingham Palace 7,866 posts
- 18. Poot 16.4K posts
- 19. Mikko 2,841 posts
- 20. Happy Birthday Henry 2,462 posts
Something went wrong.
Something went wrong.






















































































































