
strikoder
@Strikoder
Beginner pentester documenting my OSCP journey through HTB labs. Follow if you're learning too or exploring cybersecurity.
Best tweet ever!
i still don't get it. people get up in arms about tweets saying if you have never engineered you are not an engineer if you need the validity of some internet rando its time to grow up. if you need to be called an engineer or else you wont be able to succeed, grow up i was…
New HackTheBox video!!! Roundcube RCE (CVE-2025-49113) to foothold, then exploiting Below monitoring tool (CVE-2025-27591) symlink vulnerability for root. Watch on YT: youtu.be/Y2O0tlVgjo0 #HackTheBox #OSCP #CVE202549113 #CVE202527591 #Pentesting #Linux

New video: NetExec (nxc) - AD enumeration, hash dumping, and module demo (SMB/LDAP/WinRM/NTDS). Full walkthrough and timestamps here: youtu.be/JeZNcZhpTWI?si… #Pentesting #CyberSecurity #netexec #crackmapexec #pentestingtools

New episode for pentesters: a practical deep dive into Mimikatz, ticket/hash concepts, LSASS targets, and more Watch: youtu.be/XPxqZFaC0xE #Pentest #RedTeam #infosec #mimikatz #lsass #hashdump #credentialsdump

Hello guys! So in my prep for OSCP I noticed many machines have dozens of SUID and SGID binaries that may be exploitable or limited. Especially during the exam you might miss something under pressure. GitHub Link: github.com/strikoder/gtfo… #GTFOBins #SUID #GUID #gtfobinSUID
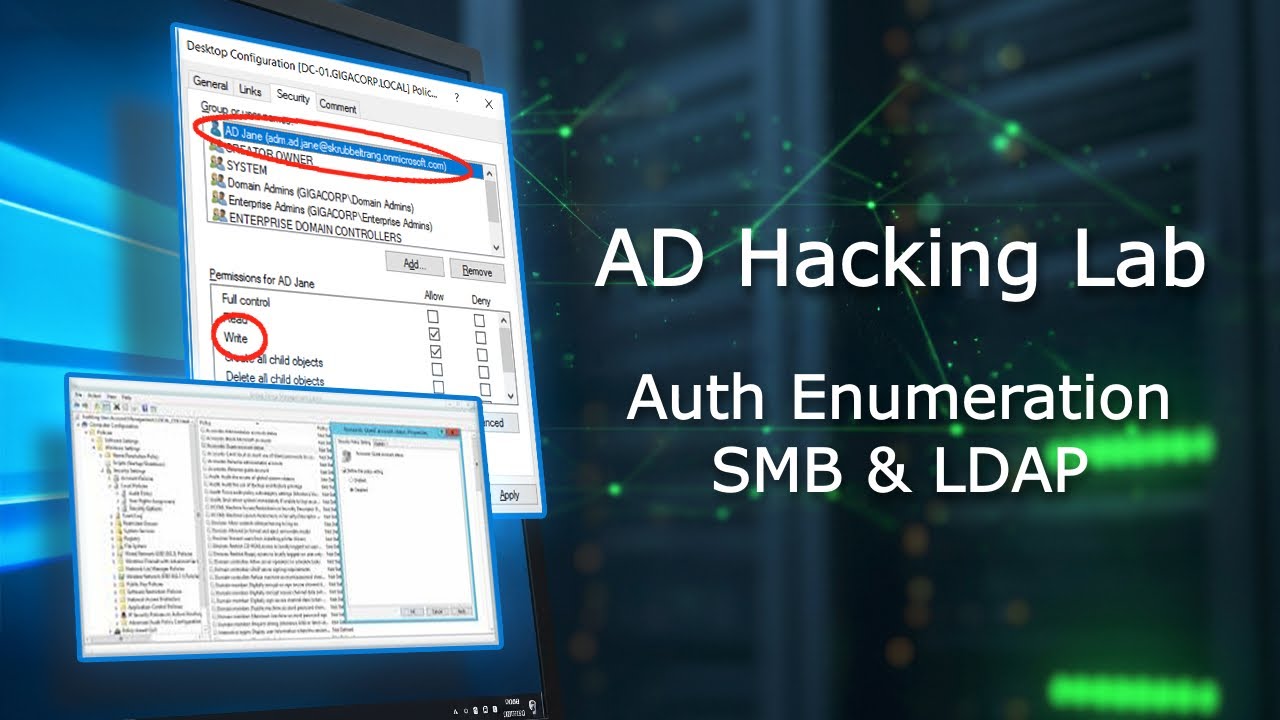
New video out: Authenticated SMB & LDAP enumeration in AD using custom OSCP-style scripts. Tools: rpcclient, netexec, ldapsearch Covers: Post-compromise recon, extracting users/groups/shares Watch here: youtu.be/kfxQRgKBfCI?si… #OSCP #ActiveDirectory #RedTeam #Pentest
youtube.com
YouTube
OSCP Scripts for SMB & LDAP Authenticated Enumeration | Enumerating...
Happy to drop my favorite video so far. In this one, I cover full Active Directory enumeration using BloodHound and its three main ingestors: - SharpHound - bloodhound-python - RustHound Link: youtu.be/en_v4wM6Dm4?si… #BloodHound #ActiveDirectory #OSCP #PT1 #PNPT #CyberSecurity
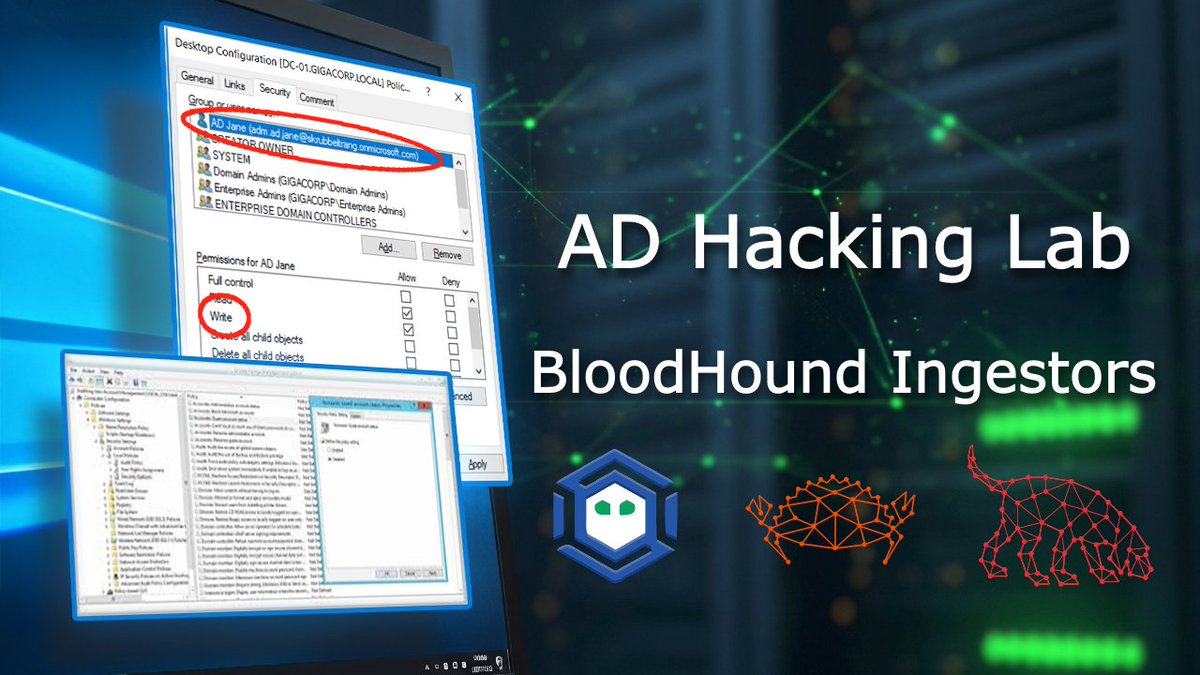
Just dropped a new Ep of my Active Directory Hacking Lab series! Focus: No-auth enumeration (Yeah, most of it’s useless without misconfigs, but you gotta check.) DNS → Kerberos → SMB → LDAP Watch: youtu.be/H0IHMjkkKkI?si… #OSCP #pentest #ActiveDirectory #AD #infosec

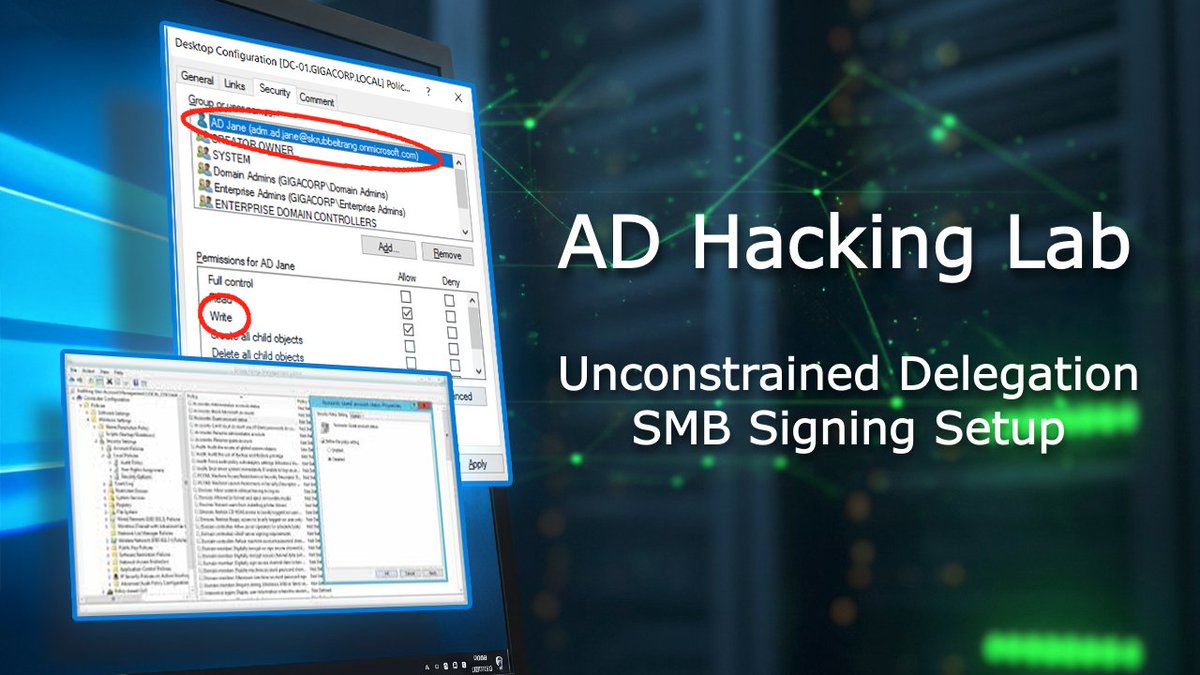
Preparing the LAB machines – Unconstrained Delegation & SMB signing setup. Install Wise Care, disable SMB signing on clients, add pentest\local_admin, enable TrustedForDelegation on LAB-FINANCE. YT Link: youtu.be/GexheVVwtI8?si… #ActiveDirectory #pentesting #AD
HackTheBox - Cap Walkthrough | IDOR, pcap, getcap. Bulk download enumeration from, FTP/SSH access, then local privilege paths with `getcap`. Watch: youtu.be/AuwYzh-vI_4 #pcap #getcap #IDOR #massdownload
HackTheBox – Cicada Walkthrough | DEV, SMB, WinRM, hive-dump. Access DEV SMB to recover creds. evil-winrm for interactive shell. Export HKLM\SYSTEM and HKLM\SAM to desktop. Run secretsdump and reuse hashes with psexec. Watch: youtu.be/qER4mbvXucE #wirnm #smb #hivedump

youtube.com
YouTube
HackTheBox – Cicada Walkthrough | SMB & WinRM auth, hive-dump
HackTheBox Servmon Walkthrough | NVMS-1000, NSClient++, port-forwarding. NVMS-1000 path traversal, SSH as Nadine, SSH local port-forwarding to reach NSClient++, transfer nc.exe and run EDB-46802 for privilege escalation. Watch: youtu.be/L576cQ3mQU4 #HackTheBox #HTB #pentesting

Timelapse (HTB) walkthrough: PFX crack, WinRM cert auth attempt, LAPS escalation to root. Watch: youtu.be/DmP292z1Gks tldr: zip2john, pfx2john, OpenSSL PFX→PEM, evil-winrm cert auth, certutil download, Invoke-ConPtyShell, LAPS→TRX. #HTB #Timelapse #Windows

New HackTheBox walkthrough: SecNotes I cover multiple attack paths: - Password reset flaw - SQLi login bypass - SSRF via contact form - PHP webshell + nc.exe - Abusing WSL for a reverse shell - Privilege escalation with Impacket Watch here: youtu.be/gCfnjLkgShA #HackTheBox
youtube.com
YouTube
HackTheBox – Secnotes Walkthrough | SQLi, WSL
New HackTheBox walkthrough: Access In this one, I go through: - FTP enumeration - Dumping an MDB database - Extracting a PST file - Telnet exploitation - Multiple privilege escalation methods Full video here: youtu.be/H5HNbhIzVco #hackthebox #oscp #ethicalhacking

Just dropped a new HackTheBox walkthrough: Jeeves (Windows, Medium): - Jenkins RCE on port 50000 - Cracking a KeePass KDBX database with keepass2john - Extracting creds with kpcli - Pass-the-Hash attack using psexec for full Admin access 🎥 Watch here: youtu.be/qGhsmC3hZdM?si…

youtube.com
YouTube
HackTheBox Jeeves Walkthrough | Jenkins RCE, KeePass (KDBX) Looting,...
HackTheBox Support Walkthrough is live: - Running Windows .exe on Linux with Mono - LDAP info - AddComputer for machine account creation - Resource-Based Constrained Delegation (RBCD) - Pass The Ticket Video: youtu.be/QEXostYrmN4?si… #ActiveDirectory #Pentesting #CyberSecurity
youtube.com
YouTube
HackTheBox Support Walkthrough | Mono EXE, LDAP info, RBCD, Pass The...
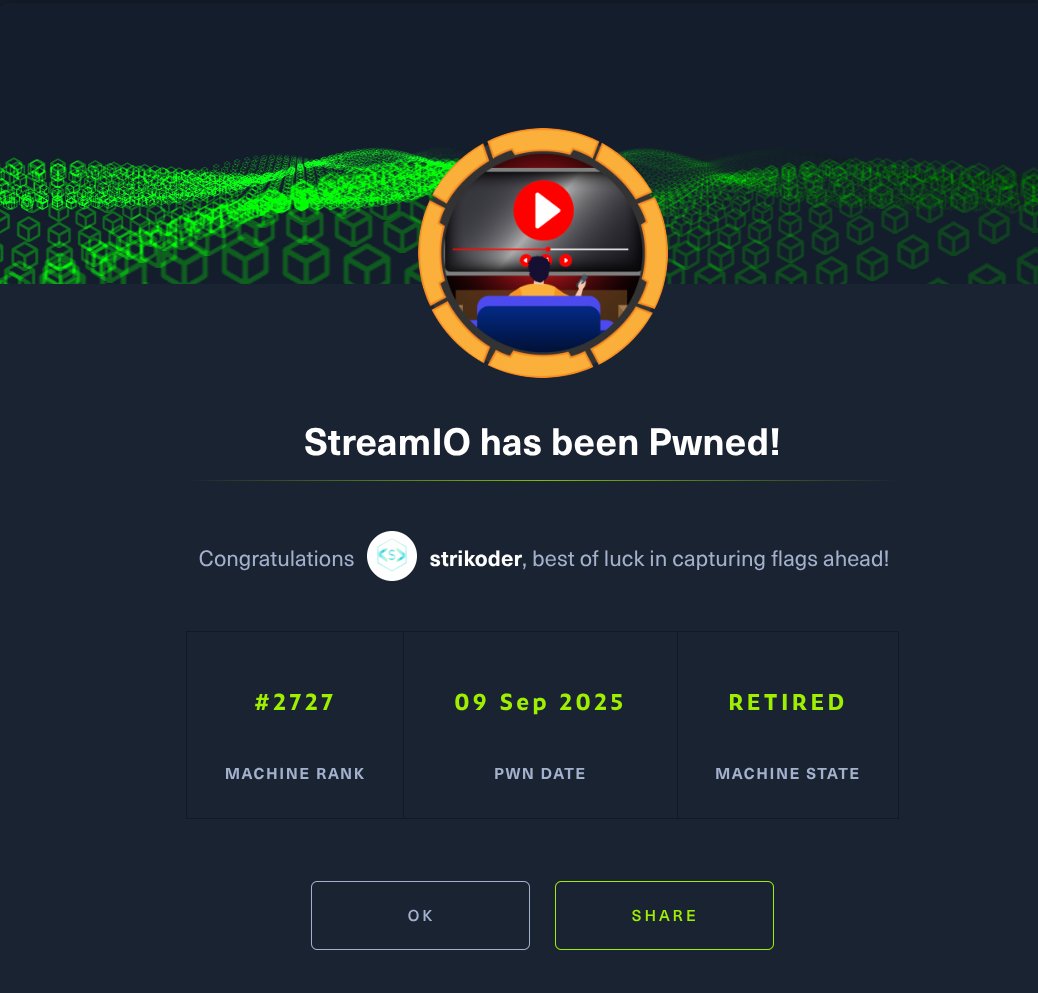
Tried #HTB StreamIO (on the TJ Null OSCP list). Only ~2000 ppl solved it, and now I see why. You need: SQLi, LFI, MSSQL, reverse shells, Firefox creds, BloodHound, and ReadLAPS abuse. Recorded a 2h walkthrough xD youtu.be/JgHjbwW-RhI?si… #OSCP #Pentesting #HTB
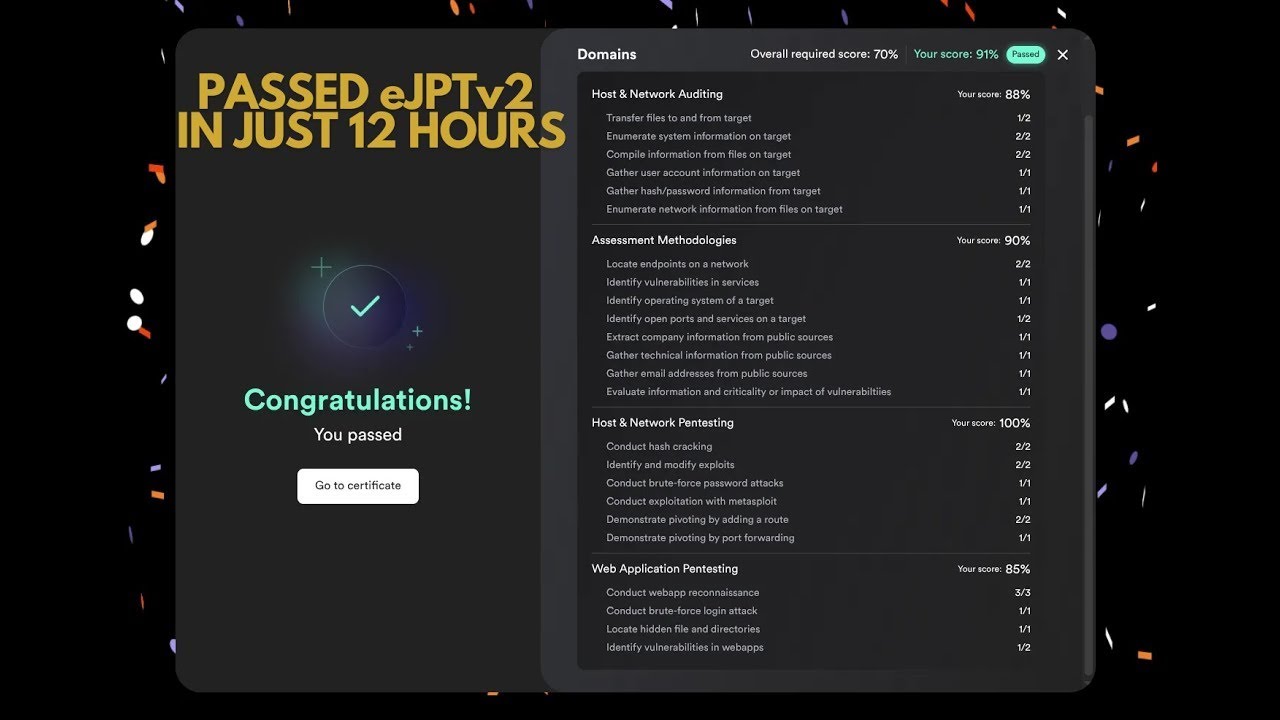
Passed #eJPT in 12 hours (3 wrong answers, stuck 6h on 1 box). Made a video breaking down my study progress, tools, mistakes, what I wish I knew before the exam + a roadmap to prep for eJPT/OSCP. Watch here: youtu.be/15AVH1IT2rM #ejpt #oscp #cybersecurity #pentesting
youtube.com
YouTube
eJPT Certification Review | My Study Progress, Exam Experience, and...
Just dropped a new video on solving Chatterbox (Medium, Windows) from HackTheBox 👇 youtube.com/watch?v=-ZEye2… Highlights: Exploiting vulnerable Chatterbox service Abusing ICACLS to grab root #HackTheBox #Meduim_Box #Pentesting

New series launched: Active Directory Attacks Step-by-step labs for OSCP, PNPT, CPTS prep. First episode is out now. Watch here: youtu.be/BJPQnL6ZOWA #OSCP #Active_Directory

United States Trends
- 1. #GMMTV2026 1.23M posts
- 2. MILKLOVE BORN TO SHINE 232K posts
- 3. Good Tuesday 23.1K posts
- 4. WILLIAMEST MAGIC VIBES 31.8K posts
- 5. TOP CALL 9,420 posts
- 6. #WWERaw 78.8K posts
- 7. Barcelona 151K posts
- 8. Moe Odum N/A
- 9. AI Alert 8,186 posts
- 10. Brock 42.5K posts
- 11. Purdy 28.6K posts
- 12. Alan Dershowitz 2,896 posts
- 13. Bryce 21.4K posts
- 14. Keegan Murray 1,568 posts
- 15. Dialyn 8,170 posts
- 16. Check Analyze 2,432 posts
- 17. Token Signal 8,660 posts
- 18. Market Focus 4,710 posts
- 19. Timberwolves 3,956 posts
- 20. Barca 79.7K posts
Something went wrong.
Something went wrong.















































