Cube🧊
@cube0x8
💻 Vulnerability research, fuzzing, reverse engineering 🚐 Travelling the world with a van 🤘🏻 Metal music supporter
You might like
End of day 1: the mhackeroni kitchen is in full swing @defcon CTF - let's cook 🔥 Thanks for the support to 🥇 #7Layers - #DRIVESEC 🥈 @_revng - @KeylessTech - @WuerthPhoenix - @CNIT_TLC 🙌 #STACKBITS


Drop by everyone 🦥
I know it’d be a bloodbath, but I’d love to see a pwn2own category for so-called security appliances
Neat, Intel awarded a $5k bug bounty for this report! We donated it to local food bank @2ndharvest, just in time for Christmas! Thank you!! 🎅
New write-up on an Intel Ice Lake CPU vulnerability, we can effectively corrupt the RoB with redundant prefixes! 🔥 An updated microcode is available today for all affected products, cloud providers should patch ASAP. lock.cmpxchg8b.com/reptar.html
I turned a workshop on fuzzing with LibAFL into a blog post for you all, check it out: atredis.com/blog/2023/12/4…
Emulated full system snapshot fuzzing by Intel 👀 haunted.computer/@novafacing/11…
"How to Build a Fuzzing Corpus" introduces some of the basic theory behind using a seed corpus for fuzzing, and answers three key questions: what is a seed corpus, why are they useful, and how can we build one from scratch? blog.isosceles.com/how-to-build-a…
Our work on exploring new ways for efficient firmware fuzzing will be published at @USENIXSecurity 2023! With SAFIREFUZZ, we introduce near-native rehosting, drastically improving the performance of fuzzing embedded targets. Super happy about this work w @domenuk @nSinusR

* The 8 new fuzzers are: AFL+++, AFLrustrust, AFLsmart++, HasteFuzz, LearnPerfFuzz, LibAFL_libFuzzer , Pastis, and symsan. ** The 4 baseline fuzzers are: AFL, AFL++, HonggFuzz, and libFuzzer. They are evaluated by #FuzzBench from Google Open Source Security Team (GOSST).
The battle has started and will last exactly 23 hours, plus hours of post-battle victory assessment. 10k+ CPUs in Google cloud are roaring for this battle. The battle is the #SBFT23 fuzzing competition, and its winners will be crowned on 14 May 2023 in Melbourne, Australia.
Pleased to announce that the materials of Hypervisor 101 in Rust🦀is now public! A one-day long course taught at #gccsec, to quickly learn hardware-assisted virtualization technology and its application for high-performance fuzzing on Intel/AMD processors github.com/tandasat/Hyper…
LibAFL QEMU full-system mode is a thing! Check out the example that fuzz a small ARM FreeRTOS firmware at github.com/AFLplusplus/Li… Next step: fast memory and devices snapshots
Mgła live @ Principal Club Theater, Thessaloniki. This is quality black metal.

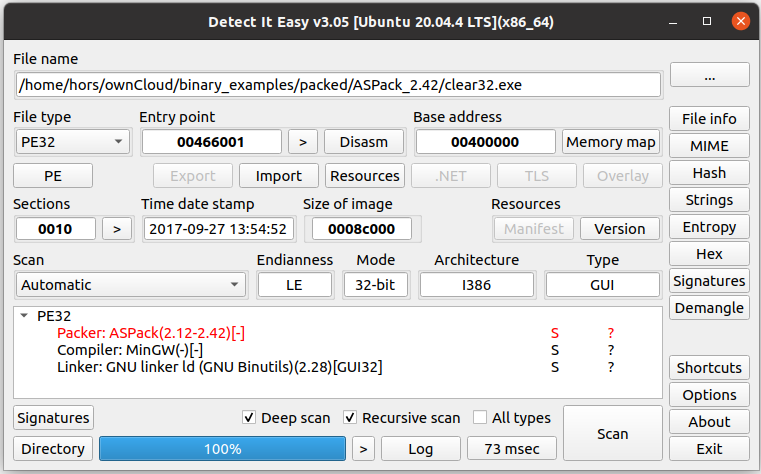
Detect It Easy, or abbreviated "DIE" is a program for determining types of files. 3.06 github.com/horsicq/Detect… #hacker #infosec #malware #hacking #programming #reversing #opensource #linux #linuxsecurity #unix #macos #detectiteasy #die #android #cybersecurity #detectiteasy
I just released the source code of Paracosme: a zero-click remote memory corruption exploit I demonstrated at Pwn2Own 2022 Miami 🐛🐜🪲 github.com/0vercl0k/parac…
LibAFL has now a dedicated paper! We discuss its design and show some experiments comparing compelling approaches. It will appear at CCS '22 this fall. Amazing collab with @domenuk @DongjiaZ @balzarot Preprint at s3.eurecom.fr/docs/ccs22_fio…
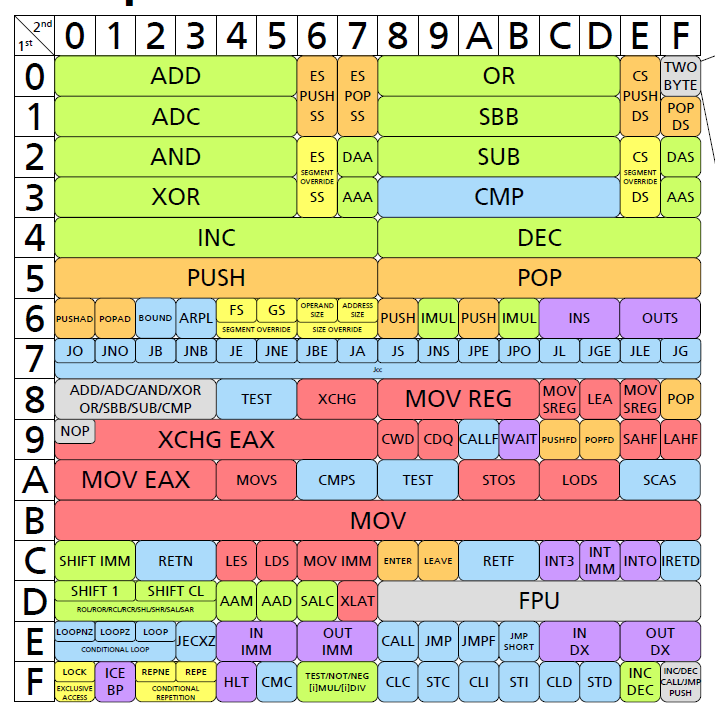
I've just discovered this amazing document showing super clearly the relation between the opcode and the instruction 🤯 pnx.tf/files/x86_opco…
I am very excited to announce that our talk: New Memory Forensics Techniques to Defeat Device Monitoring Malware was accepted at @BlackHatEvents Vegas! blackhat.com/us-22/briefing… @Volexity @volatility @nolaforensix @LSUCCT @lsuresearch #BHUSA #DFIR
So uh, NVIDIA apparently just… open-sourced their Linux GPU drivers under a dual MIT/GPL licence. ※ For Ampere and Turing only, at least for now…? developer.nvidia.com/blog/nvidia-re… github.com/NVIDIA/open-gp… … Is the world finally coming to an end?
United States Trends
- 1. Chiefs 97.8K posts
- 2. Branch 27.7K posts
- 3. Mahomes 29.7K posts
- 4. #TNABoundForGlory 48.3K posts
- 5. #LoveCabin N/A
- 6. LaPorta 9,847 posts
- 7. Goff 13.2K posts
- 8. Bryce Miller 4,097 posts
- 9. #OnePride 6,226 posts
- 10. Kelce 15.2K posts
- 11. #DETvsKC 4,758 posts
- 12. Butker 8,237 posts
- 13. Dan Campbell 3,027 posts
- 14. #LaGranjaVIP 38.3K posts
- 15. Mariners 46.8K posts
- 16. Pacheco 4,755 posts
- 17. Gibbs 5,467 posts
- 18. Baker 53K posts
- 19. Collinsworth 2,857 posts
- 20. Tyquan Thornton 1,199 posts
You might like
-
 JsQ4Kn0wledge
JsQ4Kn0wledge
@JsQForKnowledge -
 Piotr Bania
Piotr Bania
@PiotrBania -
 Andrea Fioraldi
Andrea Fioraldi
@andreafioraldi -
 Andrea Palazzo
Andrea Palazzo
@cogitoergor00t -
 VictorV
VictorV
@vv474172261 -
 sqrtrev
sqrtrev
@sqrtrev -
 GMO Flatt Security Inc.
GMO Flatt Security Inc.
@flatt_sec_en -
 [email protected]
[email protected]
@daviddiaul -
 brymko
brymko
@brymko -
 3ndG4me
3ndG4me
@3ndG4me_ -
 b0ring
b0ring
@dnpushme -
 babush
babush
@pmontesel -
 avboy1337
avboy1337
@avboy1337 -
 Fabio Pagani
Fabio Pagani
@pagabuc
Something went wrong.
Something went wrong.