
你可能會喜歡
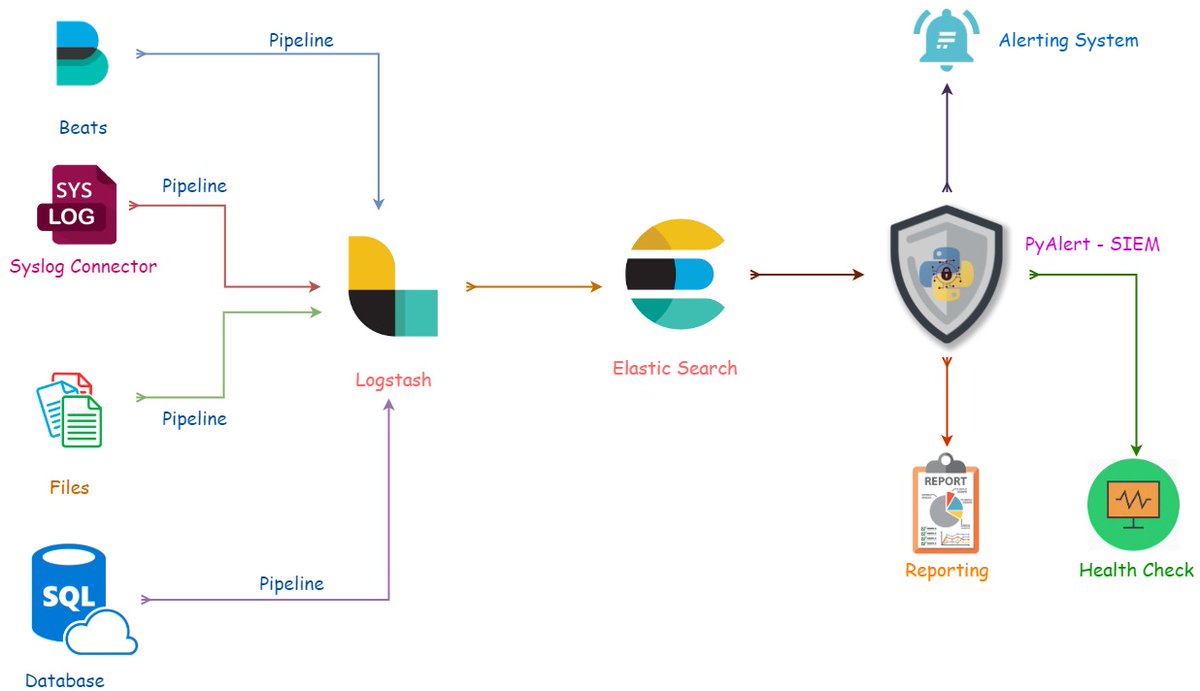
Introducing a new Security Incident and Event Management Tool designed using Python and ELK Stack. Features Offered: 1. Alerting 2. Reporting 3. Health Check visit: github.com/srinivas946/Py… #python #elk #elasticsearch #kibana #logstash #siem #secrity #cybersecurity #infosec
Learn Phishing Email Analysis to prevent Phishing Attacks. Topics Covered: 1. What are DNS Records ? 2. What is SPF and its limitations ? 3. What is DKIM and its limiations ? 4. What is DMARC ? visit : cybersecpy.in/phishing-email… #Phishing #cybersecurity #emails #Malware #Python

Learn about Advanced Persistent Threats. Topic : APT - 41 Concepts: Attack Life Cycle Targeted : Video Game Industry, Health Sector, Financially Motivated Activity and so on... visit: cybersecpy.in/2020/03/31/adv… #apt41 #cybercrime #cyberattacks #healthcare #videogameindustry
Learn how to interact with PowerPoint using Python. 1. Create Interactive Tables 2. Create Slides & Animations 3. Attach Multiple Images 4. Deal with Headings and Paragraphs visit: cybersecpy.in/interact-with-… #python #microsoft #microsoftoffice #PowerPoint #word #cybersecurity
Learn how to write Yara Rules for malware Analysis. Yara Rules are very easy to learn and write. 1. Learn how to use Meta Information 2. How many ways we can declare strings 3. How to use conditions Visit : cybersecpy.in/yara-rules-mal… #Python3 #Malware #cybersecurity #infosec

Learn how to Interact with Microsoft Office Services using Python. 1. Create Heading and Paragraphs 2. Attach Images of different types (jpg, png, gif etc..) 3. Create Tables with Multiple styles #Python3 #cybersecurity #Malware #infosec #Microsoft #Office365

YAML - Yet Ain't Markup Language -Learn how to Interact with YAML Files to Perform Read and Write Operations with different types of data. - Learn how to use YAML Files as configuration Files Vist: cybersecpy.in/python-yaml-fi… #Python #cybersecurity #yaml #programming #files
Learn how to use configuration file using python. Increase the flexibility of the program by adding configuration file where values can be changed dynamically. visit: cybersecpy.in/python-configu… #Python #pythontool #CyberSecurityBrief #cyber #informationsecurity

Identifying the Malware based on file-type not worthy always. To overcome this scenario, fingerprinting malware using cryptographic hash will provide better results in detection of malware. Visit: cybersecpy.in/fingerprinting… #Python #Malware #malwareanalysis #security #cybersecurity

In Malware Analysis, the first step of Identifying malware based on its file types, Most of the Malware are of types exe, dll, sys, com, ocx and so on. Create Your Own Tool for Identifying the File Types using Python. Visit: cybersecpy.in/identifying-fi… #Python #Malware #executive

Learn how Python handle csv files in real time scenarios. 1. Parse JSON Input and store in a csv file 2. Parse HTML Input and store in a csv file 3. Take Logs as Input and make a logic for pivot table 4. Visualize the data using csv file 5. Fetch Threat I…lnkd.in/fasRfvF
linkedin.com
#cybersecurity #informationsecurity #hacking #networksecurity #siem #threat #databreach #privacy...
Learn how Python handle csv files in real time scenarios. 1. Parse JSON Input and store in a csv file 2. Parse HTML Input and store in a csv file 3. Take Logs as Input and make a logic for pivot...
Comma Separated Value (CSV) - Handle CSV Files using Python and learn how to handle data using csv in real time scenarios of cybersecurity Automation field. Empower Your Knowledge by learning Python in CyberSecurity #cybersecurity…lnkd.in/fJwWYW2 lnkd.in/fT-VtFF
Learn how to work with Date-Times in Python with Real Time Scenarios explained well. Learn Cyber Security in Pythonic Way - # #cybersecurity #security #security #infosec #informationsecurity #cyberattack #networksecurity #d…lnkd.in/fqdsgQj lnkd.in/fX8QdwR
linkedin.com
#cybersecurity #security #security #infosec #informationsecurity #cyberattack #networksecurity...
Learn how to work with Date-Times in Python with Real Time Scenarios explained well. Learn Cyber Security in Pythonic Way - https://lnkd.in/fX8QdwR #cybersecurity #security #security #infosec...
Learn How Python is Evolving in Cybersecurity. A Python Path towards Cybersecurity, visit #security #infosec #informationsecurity #cybersecurity #pythonprogramming #python #learn #datasecurity cybersecpy.in
Learn How Python Evolved in Cyber Security. A Python Path towards CyberSecurity. visit cybersecpy.in

United States 趨勢
- 1. Canada 327K posts
- 2. Reagan 117K posts
- 3. #FanCashDropPromotion N/A
- 4. #PoetryInMotionLeeKnow 25.5K posts
- 5. Immigration 154K posts
- 6. #FridayVibes 5,514 posts
- 7. Good Friday 68.4K posts
- 8. #FursuitFriday 12.2K posts
- 9. U-Haul 10.2K posts
- 10. #FridayFeeling 3,014 posts
- 11. Cyrene 27.5K posts
- 12. Happy Friyay 1,736 posts
- 13. Inflation 105K posts
- 14. Halle 23.9K posts
- 15. Tren de Aragua 19.1K posts
- 16. 3% in September 6,112 posts
- 17. MADURO LOS TIENE LOCOS 1,645 posts
- 18. Leon Thomas 6,157 posts
- 19. Lover Girl 39.8K posts
- 20. New Edition 7,143 posts
Something went wrong.
Something went wrong.


























