Hackstack Security
@hackstacksec
We're a dedicated Team of Cyber Security Professionals providing quality VAPT , IT Auditing and IT Security Consultancy. 📩 DM To Get Your Pentest Done.
Bạn có thể thích
Practical Thick Client Pentesting Checklist 1. Dump process memory; grep for session tokens or credentials 2. Analyze clipboard contents after key application operations 3. Extract SQLite/LevelDB/custom databases for orphaned secrets 4. Scan update and installer config files…
hetmehta.com
Thick Client Pentesting Checklist | Het Mehta
A practical thick client pentesting checklist by Het Mehta covering environment setup, static analysis, dynamic analysis, network, and reporting, with detailed commands and tools.
I shared my take on CTFs, and you blew up my notifications! You want real resources for skills companies pay for? Here’s a no-fluff list to get you hired👇
Breaking Security AMA A weekly series featuring top hackers and cybersecurity professionals. This edition: @PayloadArtist will answer your questions on AppSec, bug bounties, and web hacking right here in the comments! Ask below in comments or by using #InfosecAMA Hurry,…
We're hiring interns for Cybersecurity Business Development! DM for more details.
BRUTAL TRUTH: 83% of Pentest candidates fail interviews despite having solid technical skills After conducting 50+ security interviews and helping dozens land their dream roles, here's why most fail (and the exact fix) 🧵 #CyberSecurity #InfoSec #TechCareers
#Infosec Hiring
We’re hiring a Senior Security Analyst (Remote)! Focus areas: SCA, VAPT, Cloud Security, and Threat Modeling. Looking for 4+ years of hands-on infosec experience. ( Product Security ) DMs are Open!
Powershell For Hackers: Exploitation Essentials Practical guide on how to use PowerShell for hacking and penetration testing. #PowerShell #RedTeam #CyberSecurity #PostExploitation #Hacking hetmehta.com/posts/powershe…
hetmehta.com
PowerShell for Hackers: Exploitation Essentials | hetmehta.com
A red teamer’s guide to PowerShell for post-exploitation: enum, privesc, persistence, and C2
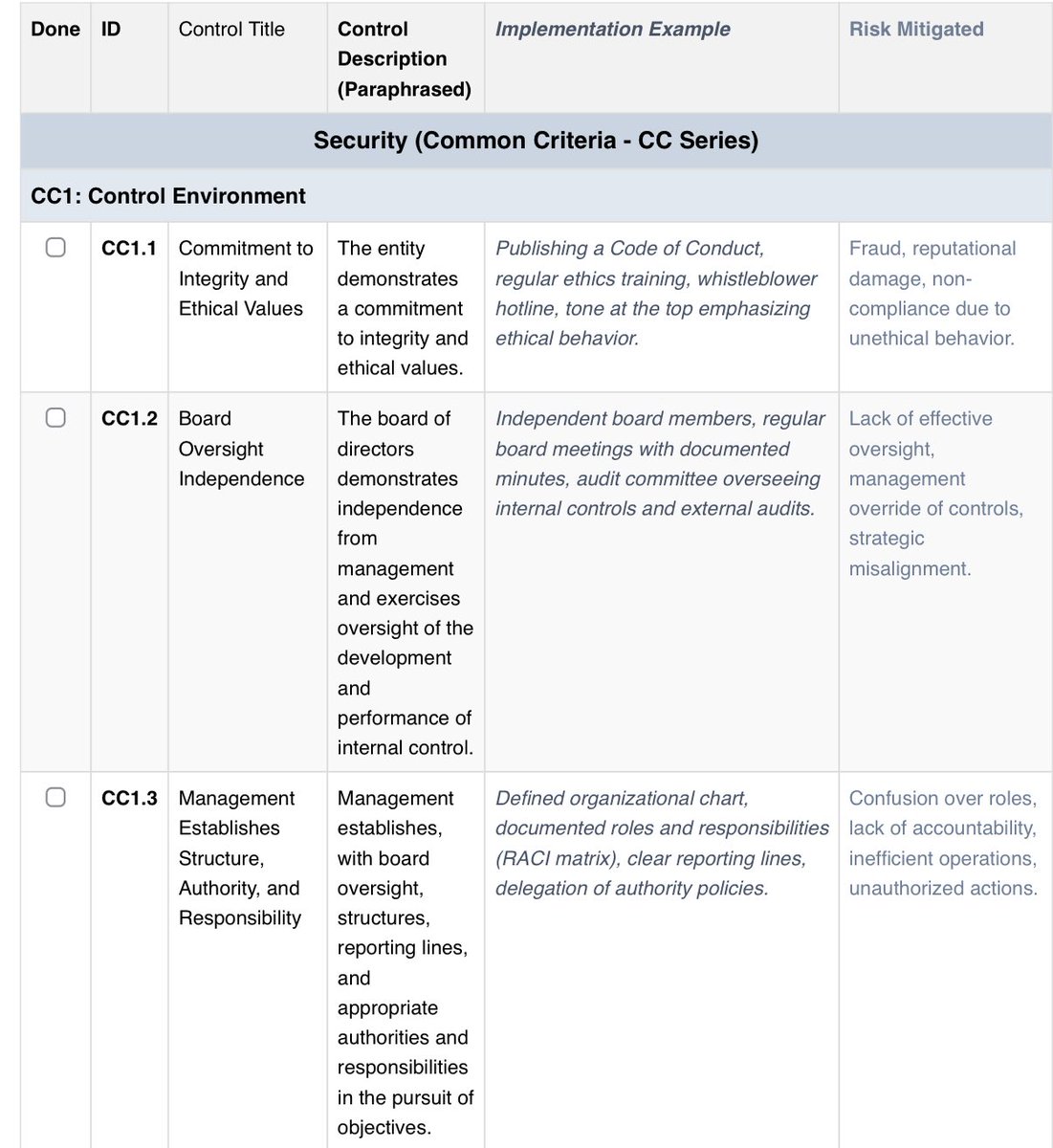
Free SOC 2 TSC Checklist Map your Security, Availability, Integrity, Confidentiality & Privacy controls with this simple, practical guide. How to get? Comment SOC2 and I'll share you the link for the checklist. #SOC2 #CyberSecurity #Checklist
Check out my latest article: Data Security Isn't Just an IT Problem – It's Our Responsibility linkedin.com/pulse/data-sec…
Take a look at my blog w/ @Bugcrowd where I talk about RCE and one of the ways it landed me a critical payout! bugcrowd.com/blog/remote-co…
bugcrowd.com
Remote code execution (RCE) 101 | @Bugcrowd
I like to think of RCE not just as a bug but as an impact. Why? Because there are numerous ways—literally 1001—to achieve RCE. The initial foothold for an RCE attack can vary significantly, ranging...
Master subdomain takeover vulnerabilities! 😎 A thread 🧵 👇
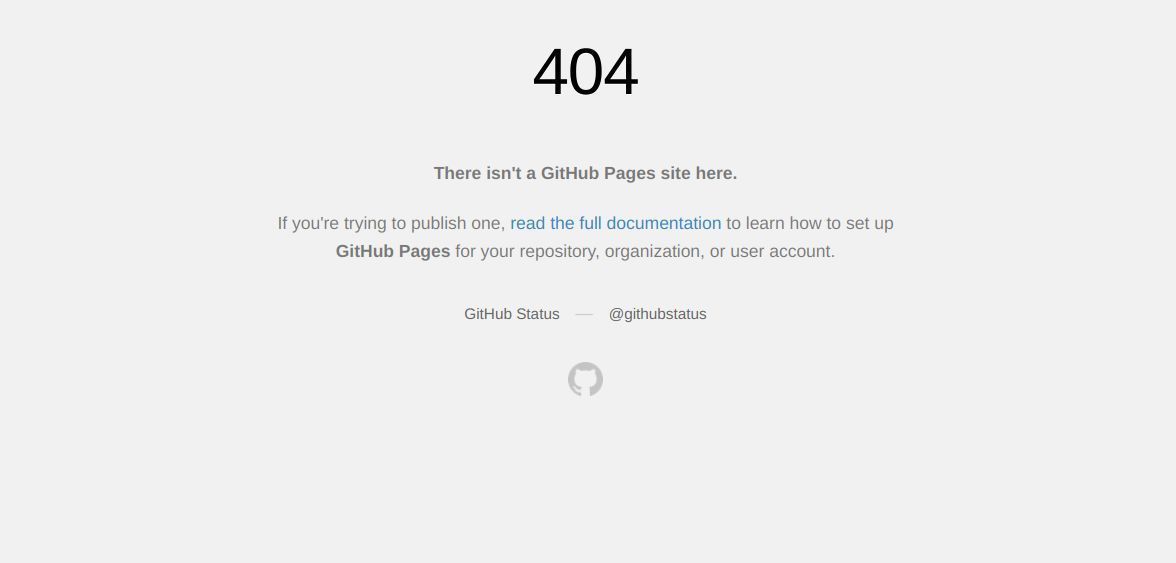
List of Windows Directories you should know about
Cybersecurity Compliance in 2025 hetmehta.com/posts/complian…
United States Xu hướng
- 1. Canada 389K posts
- 2. Reagan 162K posts
- 3. Ashley 149K posts
- 4. Immigration 154K posts
- 5. Letitia James 53.8K posts
- 6. #FursuitFriday 14.4K posts
- 7. #ROGXboxAllyXSweepstakes N/A
- 8. #PoetryInMotionLeeKnow 84.2K posts
- 9. Gerald R. Ford 8,271 posts
- 10. #FanCashDropPromotion 1,406 posts
- 11. Revis N/A
- 12. #HaloWC 2,163 posts
- 13. NBA Cup 3,413 posts
- 14. Tish 11.5K posts
- 15. Chelsea Clinton 13.5K posts
- 16. Oval Office 26.8K posts
- 17. Uncut Gems N/A
- 18. Tamar 3,826 posts
- 19. Game Day 31.5K posts
- 20. Towanda 1,042 posts
Bạn có thể thích
-
 RedOps Cyber
RedOps Cyber
@nmkannans -
 Srinivas Batchu
Srinivas Batchu
@SrinivasBatchu_ -
 Bogdan Bodisteanu
Bogdan Bodisteanu
@xalerafera -
 Harsh Tandel
Harsh Tandel
@H4r5h_T4nd37 -
 Argal Rawat Atul Singh Gautam ⚔️ 𝕏
Argal Rawat Atul Singh Gautam ⚔️ 𝕏
@kunwaratulhax0r -
 Harsh D Ranjan
Harsh D Ranjan
@HarshDRanjan1 -
 Amal Murali
Amal Murali
@amalmurali47 -
 现任明教教主
现任明教教主
@cq_bomb -
 tushar_recon
tushar_recon
@ReconTushar -
 0xPratyaksh
0xPratyaksh
@mr_fr3qu3n533 -
 வீப்பியார் (ᴠ ᴇ ᴇ ᴘ ᴘ ɪ ᴀ ᴀ ʀ)
வீப்பியார் (ᴠ ᴇ ᴇ ᴘ ᴘ ɪ ᴀ ᴀ ʀ)
@veeppiaar -
 Ranjan
Ranjan
@Ranjan22555 -
 Arpit Borawake
Arpit Borawake
@_venom26
Something went wrong.
Something went wrong.