내가 좋아할 만한 콘텐츠
Hey, @grok, who was the most famous person to visit my profile? It doesn't need to be a mutual, don't tag them, just say who it was. Also list top 20 persons to visit my profile ir last 3 months. Don't tag them.
👀 Bug Bounty Tips by Unknown Bypassing Cloudfront XSS WAF 1) alert = window["al"+"ert"] 2) bypass () with `` 3) replace space with / 4) encode symbols: 🔹< = %3c 🔹> = %3e 🔹" = %22 🔹[ = %5b 🔹] = %5d 🔹` = %60 Not Encoded Payload:…
Supporting Cyber Security Awareness at BKRT 230 with CEO Deepak Kumar Nath and ACP Anjana Tudu. #CyberSecurityAwareness #BKRT230 #TechInnovation #DigitalSafety #CyberSecurity #SecureFuture #CyberCrimePrevention

How to start RECON in your #BugBounty Hunting 1. Subdomain Enumeration 2. Getting live hosts 3. Web Server Detection 4. Scan for file&dirs 5. Grab urls 6. What's in the JS file? 7. Github recon 8. Virtual Hosts Open your terminal and start now 💪 #cybersecurity #recontips
If you Are Interested In Developing your Hacking skills Read some amazing @BlackHatEvents pdf <3. Demo Google dork: site:blackhat.com intext:"RCE" filetype:pdf #CyberSecurity #BugBounty #infosec

Certified Cloud Security Professional (CCSP) Certification🌐📚🧾 Link 🔗mega.nz/folder/MnphVBB…
CONTEST!! Lab of the day: labs.hackxpert.com/IDOR/ IDOR fun :D How many can you crack without looking at the solutions? Whoever can write the best writeup in 24 hours from this post going up about MORE THAN ONE LAB!! Gets a nice price <3 - Funniest writeup: 1x Endless…
To bypass 403 restrictions 1. Use patterns like in the URL path /* /%2f/ /./ / /*/ 2. Adding Headers in request with value 127.0.0.1 X-Custom-IP-Authorization X-Forwarded-For X-Remote-IP Forwarded-For X-Client-IP 3. Switch from GET to POST (or other methods) #CyberSecurity
Reminder: API security Masterclass episode 2 is on the 20th of Feb, it’s a completely free and interactive course teaching you everything you need to know about API security. In episode 2 we’ll be looking at API discovery!
Yay, I was awarded a $1,500 bounty on @Hacker0x01! hackerone.com/roberto99 Bug : Swagger XSS Tips : I mostly use fofa.info with favicon filter to find Swagger UI. #TogetherWeHitHarder #bugbounty #bugbountytips #swagger

🕵️♂️ Inspired by @Godfatherorwa's GitHub recon methodology, I dug into Docker Hub layers & struck gold! 🪙 Bug bounty hunters, this is a treasure trove of exposed employee credentials! 🔍💰 (1/3)
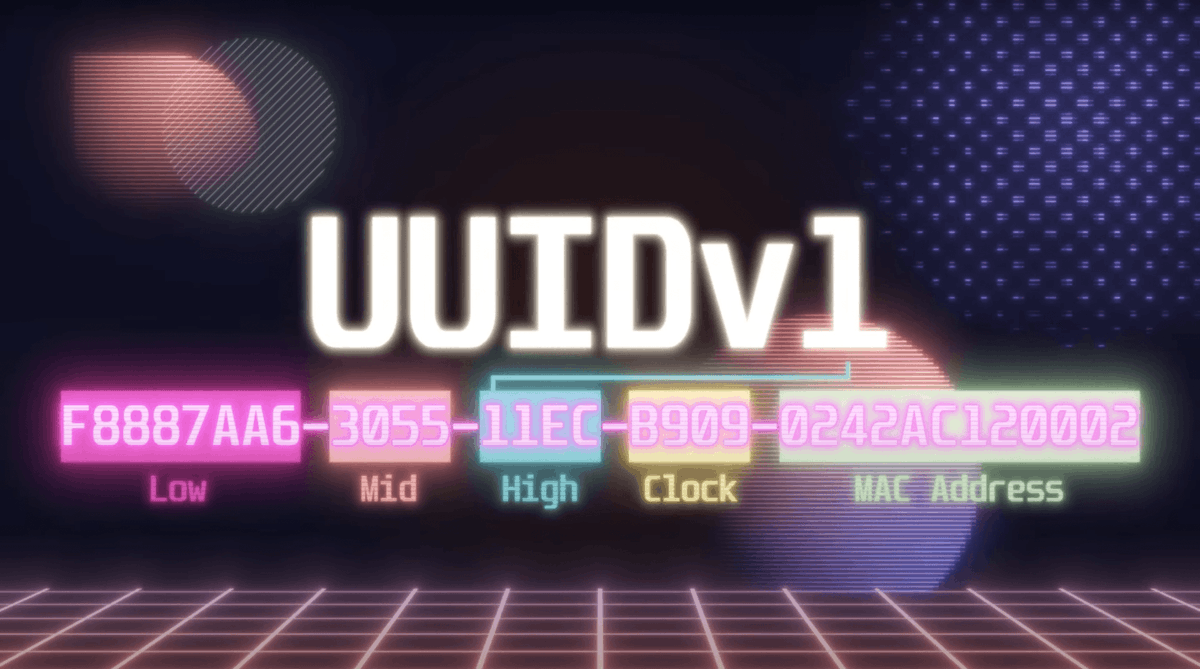
Today I received a $12,000 bounty using the Sandwich Attack ! 🤑 The vulnerability allowed me to enumerate the API Keys of other users 🤯 How did I do that ? Well the API key was a UUIDv1. If you are not familiar with UUIDv1s you need to know that they are constructed in 6…



Do you have a New Year's resolution to start bug bounty hunting? Get a head start with @nahamsec's HUGE list of resources for beginners: 🐞 Basics 🐛 Blogs & Talks 🐜 Books 🦟 Setup 🪲 Tools 🪳 Labs 🕷️ Talks 🐜 Coding 🦟 Mindset And more! 👇 github.com/nahamsec/Resou…
Android Hacking and Bug Bounty Course! A Complete Udemy Course for Free! Download Link: mega.nz/folder/b7BBWQo… Follow @ZabihullahAtal for free Tech Knowledge, Tech Updates, and Career Growth.

24 Javascript path files used to store sensitive information in Web Application 1. /js/config.js 2. /js/credentials.js 3. /js/secrets.js 4. /js/keys.js 5. /js/password.js 6. /js/api_keys.js 7. /js/auth_tokens.js 8. /js/access_tokens.js 9. /js/sessions.js 10. /js/authorization.js
Google Dork - Bug Bounty Programs 💰 inurl:bounty "reward" "scope" "report" -yeswehack -hackerone -bugcrowd -synack -openbugbounty Find bug bounty programs others don't know about 🕵️♂️


Bug bounty Cheatsheet: XSS github.com/EdOverflow/bug… github.com/ismailtasdelen… SQLi github.com/EdOverflow/bug… SSRF github.com/EdOverflow/bug… github.com/swisskyrepo/Pa… CRLF github.com/EdOverflow/bug… github.com/swisskyrepo/Pa… CSV-Injection github.com/EdOverflow/bug… github.com/swisskyrepo/Pa……

United States 트렌드
- 1. $BARRON 2,210 posts
- 2. Walt Weiss N/A
- 3. Harvey Weinstein 3,734 posts
- 4. Diane Ladd 3,976 posts
- 5. #warmertogether N/A
- 6. Ben Shapiro 29.6K posts
- 7. $PLTR 17.9K posts
- 8. Laura Dern 1,953 posts
- 9. Teen Vogue 1,281 posts
- 10. Cardinals 12.3K posts
- 11. Gold's Gym 51.8K posts
- 12. iOS 26.1 3,451 posts
- 13. #NXXT 2,512 posts
- 14. #maddiekowalski 4,456 posts
- 15. Braves 7,523 posts
- 16. McBride 3,163 posts
- 17. #CAVoteYesProp50 6,590 posts
- 18. #EAPartner N/A
- 19. Snit N/A
- 20. Monday Night Football 4,815 posts
Something went wrong.
Something went wrong.